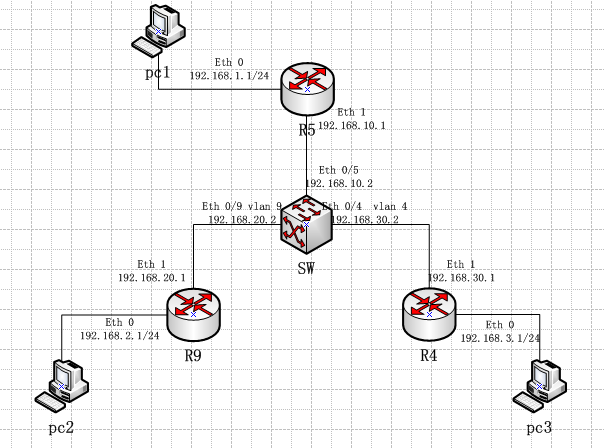
SW配置
[SW]vlan 5
[SW-vlan5]port e 0/5
[SW-vlan5]vlan 9
[SW-vlan9]port e 0/9
[SW-vlan9]vlan 4
[SW-vlan4]port e 0/4
[SW-vlan4]inter vlan 5
[SW-Vlan-interface5]ip ad 192.168.10.2 255.255.255.0
[SW-Vlan-interface5]inter vlan 9
[SW-Vlan-interface9]ip ad 192.168.20.2 255.255.255.0
[SW-Vlan-interface9]inter vlan 4
[SW-Vlan-interface4]ip ad 192.168.30.3 255.255.255.0
R5配置
配置ip地址与静态路由
[R5]inter eth 0
[R5-Ethernet0]ip ad 192.168.1.1 24
%01:03:09: Line protocol ip on the interface Ethernet0 is UP
[R5-Ethernet0]inter e 1
[R5-Ethernet1]ip ad 192.168.10.1 24
R5]ip rou 0.0.0.0 0 192.168.10.2
配置acl
[R5]acl 3000
[R5-acl-3000]rule per ip sou 192.168.1.0 0.0.0.255 des 192.168.2.0 0.0.0.255
Rule has been added to normal packet-filtering rules
[R5-acl-3000]rule per ip sou 192.168.1.0 0.0.0.255 des 192.168.3.0 0.0.0.255
Rule has been added to normal packet-filtering rules
[R5-acl-3000]rule deny ip sou any des any
Rule has been added to normal packet-filtering rules
配置IPsec proposal
R5]ipsec proposal zhangchaojie
[R5-ipsec-proposal-zhangchaojie] encapsulation-mode tunnel
[R5-ipsec-proposal-zhangchaojie]tran esp-new
[R5-ipsec-proposal-zhangchaojie]es authentication-algorithm md5-hmac-96
[R5-ipsec-proposal-zhangchaojie]es encryption-algorithm des
配置IPsec policy
[R5]ipsec policy ?
STRING<1-15> ipsec policy name.
[R5]ipsec policy zhangchaojie ?
INTEGER<0-10000> ipsec policy sequence number.
[R5]ipsec policy zhangchaojie 1 ?
<cr> if this ipsec policy has been created
isakmp indicaties that IKE will be used to establish the IPSec SA
manual indicaties that IKE will NOT be used to establish the IPSec SA
[R5]ipsec policy zhangchaojie 1 ma
[R5-ipsec-policy-zhangchaojie-1]proposal zhangchaojie
[R5-ipsec-policy-zhangchaojie-1]security acl 3000
[R5-ipsec-policy-zhangchaojie-1]sa inbound esp spi 345
[R5-ipsec-policy-zhangchaojie-1]sa outbound esp spi 678
[R5-ipsec-policy-zhangchaojie-1]sa inbound esp string zhangchaojie
[R5-ipsec-policy-zhangchaojie-1]sa outbound esp string hanyu
[R5-ipsec-policy-zhangchaojie-1]tunnel local 192.168.10.1
[R5-ipsec-policy-zhangchaojie-1]tunnel remote 192.168.20.1
[R5]ipsec policy zhangchaojie 2 ma
[R5-ipsec-policy-zhangchaojie-2]proposal zhangchaojie
[R5-ipsec-policy-zhangchaojie-2]secu acl 3000
[R5-ipsec-policy-zhangchaojie-2]sa inbound esp spi 456
[R5-ipsec-policy-zhangchaojie-2]sa outbound esp spi 789
[R5-ipsec-policy-zhangchaojie-2]sa inbound esp string zhangchaojie
[R5-ipsec-policy-zhangchaojie-2]sa outbound esp string hanyu
[R5-ipsec-policy-zhangchaojie-2]tunnel local 192.168.10.1
[R5-ipsec-policy-zhangchaojie-2]tunnel remote 192.168.30.1
应用IPsec policy
[R5-ipsec-policy-zhangchaojie-2]quit
[R5]inter e 1
[R5-Ethernet1]ipsec ?
policy Apply ipsec policy to interface
[R5-Ethernet1]ipsec policy ?
STRING<1-15> ipsec policy name.
[R5-Ethernet1]ipsec policy zhangchaojie
R9配置
配置ip地址与静态路由
[R9]inter e 1
[R9-Ethernet1]ip ad 192.168.20.1 24
[R9-Ethernet1]inter e 0
[R9-Ethernet0]ip ad 192.168.2.1 24
[R9]ip route 0.0.0.0 0 192.168.20.2
配置acl
[R9]acl 3000
[R9-acl-3000]rule per ip sou 192.168.2.0 0.0.0.255 des 192.168.1.0 0.0.0.255
[R9-acl-3000]rule deny ip sou any des any
配置IPsec proposal
[R9-acl-3000]ipsec pro hanyu
[R9-ipsec-proposal-hanyu]en tun
[R9-ipsec-proposal-hanyu]tran es
[R9-ipsec-proposal-hanyu]es au md5
[R9-ipsec-proposal-hanyu]es en des
配置IPsec policy
[R9]ipsec policy hanyu 1 ma
[R9-ipsec-policy-hanyu-1] pro hanyu
[R9-ipsec-policy-hanyu-1]sec acl 3000
[R9-ipsec-policy-hanyu-1]sa inbound esp spi 678
[R9-ipsec-policy-hanyu-1]sa out esp spi 345
[R9-ipsec-policy-hanyu-1]sa inbound esp string hanyu
[R9-ipsec-policy-hanyu-1]sa out esp string zhangchaojie
[R9-ipsec-policy-hanyu-1]tunn local 192.168.20.1
[R9-ipsec-policy-hanyu-1]tun re 192.168.10.1
应用ipsec policy
[R9]inter e 1
[R9-Ethernet1]ipsec policy hanyu
R4配置
配置ip地址与静态路由
[R4]inter e 1
[R4-Ethernet1]ip ad 192.168.30.1 24
[R4-Ethernet1]
%02:03:56: Line protocol ip on the interface Ethernet1 is UPinter e 0
[R4-Ethernet0]ip ad 192.168.3.1 24
[R4-Ethernet0]quit
[R4]ip rou 0.0.0.0 0 192.168.30.2
配置acl
[R4]acl 3000
[R4-acl-3000]rule per ip sou 192.168.30.0 0.0.0.255 des 192.168.1.0 0.0.0.255
Rule has been added to normal packet-filtering rules
[R4-acl-3000]rule deny ip sou any des any
Rule has been added to normal packet-filtering rules
配置IPsec proposal
[R4]ipsec pro hanyu
[R4-ipsec-proposal-hanyu]en tu
[R4-ipsec-proposal-hanyu]tran es
[R4-ipsec-proposal-hanyu]es au md
[R4-ipsec-proposal-hanyu]es en des
配置IPsec policy
[R4]ipsec policy hanyu 1 m
[R4-ipsec-policy-hanyu-1]pro hanyu
[R4-ipsec-policy-hanyu-1]sec acl 3000
[R4-ipsec-policy-hanyu-1]sa inbound esp spi 789
[R4-ipsec-policy-hanyu-1]sa outbound esp spi 456
[R4-ipsec-policy-hanyu-1]sa inbound esp string hanyu
[R4-ipsec-policy-hanyu-1]sa outbound esp string zhangchaojie
[R4-ipsec-policy-hanyu-1]tun local 192.168.30.1
[R4-ipsec-policy-hanyu-1]tun re 192.168.10.1
应用IPsec policy
[R4]inter e 1
[R4-Ethernet1]ipsec policy hanyu
转载于:https://blog.51cto.com/dchanyu/817967







 本文详细介绍了网络交换机SW及路由器R5、R9、R4的配置过程,包括VLAN划分、IP地址分配、静态路由设置、ACL规则定义及IPsec策略配置等。重点展示了如何通过IPsec实现安全隧道,保障不同网络间数据传输的安全。
本文详细介绍了网络交换机SW及路由器R5、R9、R4的配置过程,包括VLAN划分、IP地址分配、静态路由设置、ACL规则定义及IPsec策略配置等。重点展示了如何通过IPsec实现安全隧道,保障不同网络间数据传输的安全。
















 1312
1312

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








