一、通过dropbear为目标系统提供ssh远程连接服务
1、编译安装dropbear
[root@localhost ~]# tar xf dropbear-2013.58.tar.bz2 [root@localhost ~]# cd dropbear-2013.58 [root@localhost dropbear-2013.58]# ./configure [root@localhost dropbear-2013.58]# make PROGRAMS="dropbear dbclient dropbearkey scp" [root@localhost dropbear-2013.58]# make PROGRAMS="dropbear dbclient dropbearkey scp" install
2、将dropbear移植至目标系统
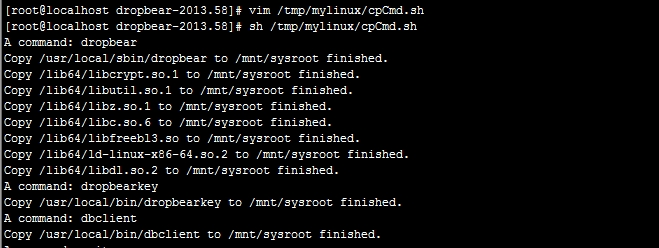
宿主机上使用此脚本移植dropbear,cpCmd.sh脚本内容如下:
#!/bin/bash
#
declare -i DebugLevel=0
Target=/mnt/sysroot
[ -d $Target ] || mkdir $Target &> /dev/null
read -p "A command: " Command
while [ $Command != 'q' -a $Command != 'Q' ]; do
Command=`which $Command | grep -v "^alias" | grep -o "[^[:space:]]*"`
[ $DebugLevel -eq 1 ] && echo $Command
ComDir=${Command%/*}
[ $DebugLevel -eq 1 ] && echo $ComDir
[ -d ${Target}${ComDir} ] || mkdir -p ${Target}${ComDir}
[ ! -f ${Target}${Command} ] && cp $Command ${Target}${Command} && echo "Copy $Command to $Target finished."
for Lib in `ldd $Command | grep -o "[^[:space:]]*/lib[^[:space:]]*"`; do
LibDir=${Lib%/*}
[ $DebugLevel -eq 1 ] && echo $LibDir
[ -d ${Target}${LibDir} ] || mkdir -p ${Target}${LibDir}
[ ! -f ${Target}${Lib} ] && cp $Lib ${Target}${Lib} && echo "Copy $Lib to $Target finished."
done
read -p "A command: " Command
done
接下来运行此脚本,分别输入dropbear、dropbearkey和dbclient、bash、ss即可;这些命令会被存储于目标系统的/usr/local/sbin或/usr/local/bin目录中。
3、为远程登录的用户提供伪终端设备文件
编辑/etc/fstab文件添加如下内容
devpts /dev/pts devpts defaults 0 0
4、为目标系统的dropbear生成主机密钥
默认情况下,dropbear到/etc/dropbear目录中查找使用的rsa格式主机密钥(默认名称为dropbear_rsa_host_key)和dss格式的主机密钥(默认名称为dropbear_dss_host_key)。其中,rsa格式可使用不同长度的密钥,但dss格式只使用1024位的密钥。
[root@localhost dropbear-2013.58]# mkdir /mnt/sysroot/etc/dropbear [root@localhost dropbear-2013.58]# dropbearkey -t rsa -f /mnt/sysroot/etc/dropbear/dropbear_rsa_host_key -s 2048 [root@localhost dropbear-2013.58]# dropbearkey -t dss -f /mnt/sysroot/etc/dropbear/dropbear_dss_host_key
5、定义安全shell
dropbear默认情况下仅允许其默认shell出现在/etc/shells文件中的用户远程登录
[root@localhost dropbear-2013.58]# vim /mnt/sysroot/etc/shells //添加下面内容 /bin/sh /bin/ash /bin/hush /bin/bash /sbin/nologin
6、为目标主机提供网络服务转换机制
在宿主机上使用默认选项编译的dropbear将依赖nsswitch实现用户名称解析,因此,还需要为目标主机提供nss相关的库文件及配置文件。
[root@localhost ~]# vim /mnt/sysroot/etc/nsswitch.conf //添加下面内容 passwd: files shadow: files group: files hosts: files dns //复制所需要的库文件: [root@localhost ~]# mkdir /mnt/sysroot/usr/lib64 [root@localhost ~]# cp -d /lib64/libnss_files* /mnt/sysroot/lib64/ [root@localhost ~]# cp -d /usr/lib64/libnss3.so /usr/lib64/libnss_files.so /mnt/sysroot/usr/lib64/
7、创建dropbear的服务脚本
为了dropbear服务脚本正常工作,把这些复制到目标机上
[root@localhost ~]# mkdir -pv /mnt/sysroot/var/lock/subsys [root@localhost ~]# cp /sbin/consoletype /mnt/sysroot/sbin/
①、创建脚本
[root@localhost ~]# mkdir -pv /mnt/sysroot/etc/rc.d/init.d
[root@www sysroot]# vim /mnt/sysroot/etc/rc.d/init.d/dropbear
//
//脚本内容如下:
#!/bin/bash
#
# description: dropbear ssh daemon
# chkconfig: 2345 66 33
#
dsskey=/etc/dropbear/dropbear_dss_host_key
rsakey=/etc/dropbear/dropbear_rsa_host_key
lockfile=/var/lock/subsys/dropbear
pidfile=/var/run/dropbear.pid
dropbear=/usr/local/sbin/dropbear
dropbearkey=/usr/local/bin/dropbearkey
[ -r /etc/rc.d/init.d/functions ] && . /etc/rc.d/init.d/functions
[ -r /etc/sysconfig/dropbear ] && . /etc/sysconfig/dropbear
keysize=${keysize:-1024}
port=${port:-22}
gendsskey() {
[ -d /etc/dropbear ] || mkdir /etc/dropbear
echo -n "Starting generate the dss key: "
$dropbearkey -t dss -f $dsskey &> /dev/null
RETVAL=$?
if [ $RETVAL -eq 0 ]; then
success
echo
return 0
else
failure
echo
return 1
fi
}
genrsakey() {
[ -d /etc/dropbear ] || mkdir /etc/dropbear
echo -n "Starting generate the rsa key: "
$dropbearkey -t rsa -s $keysize -f $rsakey &> /dev/null
RETVAL=$?
if [ $RETVAL -eq 0 ]; then
success
echo
return 0
else
failure
echo
return 1
fi
}
start() {
[ -e $dsskey ] || gendsskey
[ -e $rsakey ] || genrsakey
if [ -e $lockfile ]; then
echo -n "dropbear daemon is already running: "
success
echo
exit 0
fi
echo -n "Starting dropbear: "
daemon --pidfile="$pidfile" $dropbear -p $port -d $dsskey -r $rsakey
RETVAL=$?
echo
if [ $RETVAL -eq 0 ]; then
touch $lockfile
return 0
else
rm -f $lockfile $pidfile
return 1
fi
}
stop() {
if [ ! -e $lockfile ]; then
echo -n "dropbear service is stopped: "
success
echo
exit 1
fi
echo -n "Stopping dropbear daemon: "
killproc dropbear
RETVAL=$?
echo
if [ $RETVAL -eq 0 ]; then
rm -f $lockfile $pidfile
return 0
else
return 1
fi
}
status() {
if [ -e $lockfile ]; then
echo "dropbear is running..."
else
echo "dropbear is stopped..."
fi
}
usage() {
echo "Usage: dropbear {start|stop|restart|status|gendsskey|genrsakey}"
}
case $1 in
start)
start ;;
stop)
stop ;;
restart)
stop
start
;;
status)
status
;;
gendsskey)
gendsskey
;;
genrsakey)
genrsakey
;;
*)
usage
;;
esac
②、给dropbea执行权限
[root@localhost ~]# chmod +x /mnt/sysroot/etc/rc.d/init.d/dropbear [root@localhost ~]# cp /etc/rc.d/init.d/functions /mnt/sysroot/etc/rc.d/init.d/ //复制dropber调用的functions脚本至目标机
③、创建规范化开机启动、关机停止服务、
[root@localhost ~]# cd /mnt/sysroot/etc/rc.d/ [root@localhost rc.d]# ln -sv init.d/dropbear dropbear.start //创建dropbear启动脚本链接 [root@localhost rc.d]# ln -sv init.d/dropbear dropbear.stop //创建dropbear停止脚本链接
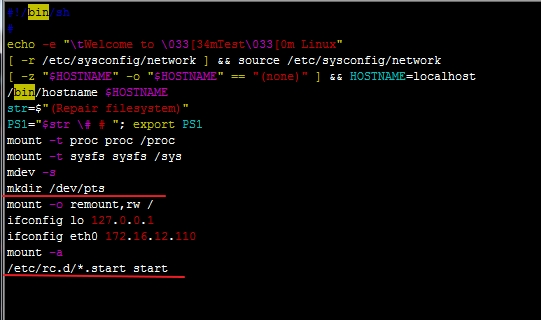
[root@localhost rc.d]# vim rc.sysinit
添加下图红线划的内容:
④、创建关机时的服务脚本rc.sysdown
[root@localhost ~]# vim /mnt/sysroot/etc/rc.d/rc.sysdown //添加下面内容 #!/bin/sh # sync sleep 2 sync /etc/rc.d/*.stop stop /bin/umount -a -r poweroff [root@localhost ~]# chmod +x /mnt/sysroot/etc/rc.d/rc.sysdown //给此脚本执行权限
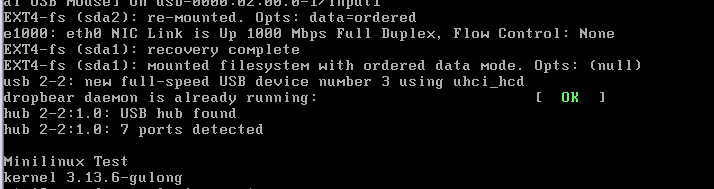
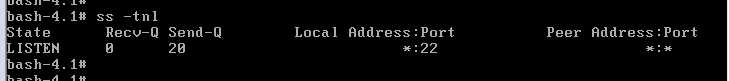
8、重启目标机,测试远程ssh登录
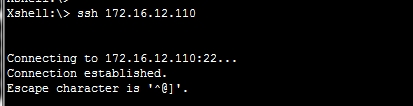
使用Xshell远程登录:
登录成功!
二、通过nginx提供web服务
1、编译安装nginx
[root@localhost ~]# tar xf nginx-1.4.2.tar.gz [root@localhost ~]# cd nginx-1.4.2 [root@localhost nginx-1.4.2]# ./configure --prefix=/usr/local --conf-path=/etc/nginx/nginx.conf --error-log-path=/var/log/nginx/error.log --http-log-path=/var/log/nginx/access.log --user=nginx --group=nginx --without-pcre --without-http_rewrite_module --without-http_geo_module --without-http_uwsgi_module --without-http_fastcgi_module --without-http_scgi_module --without-http_memcached_module [root@localhost nginx-1.4.2]# make && make install
创建nginx用户
groupadd -r nginx useradd -r -g nginx nginx
2、移植nginx至目标系统
[root@localhost ~]# sh /tmp/mylinux/cpCmd.sh A command: nginx Copy /usr/local/sbin/nginx to /mnt/sysroot finished. Copy /lib64/libpthread.so.0 to /mnt/sysroot finished. Copy /usr/lib64/libcrypto.so.10 to /mnt/sysroot finished. A command: q
3、移植配置文件至目标系统
[root@localhost ~]# mkdir /mnt/sysroot/etc/nginx/ [root@localhost ~]# mkdir /mnt/sysroot/var/log/nginx [root@localhost ~]# mkdir /mnt/sysroot/usr/local/html [root@localhost ~]# mkdir /mnt/sysroot/usr/local/logs [root@localhost ~]# cp /etc/nginx/* /mnt/sysroot/etc/nginx/
4、复制nginx用户信息
[root@localhost ~]# grep "^nginx" /etc/passwd >> /mnt/sysroot/etc/passwd [root@localhost ~]# grep "^nginx" /etc/group >> /mnt/sysroot/etc/group [root@localhost ~]# grep "^nginx" /etc/shadow >> /mnt/sysroot/etc/shadow
5、创建测试页面
[root@localhost ~]# ls /usr/local/html/* /usr/local/html/50x.html /usr/local/html/index.html [root@localhost ~]# cp /usr/local/html/* /mnt/sysroot/usr/local/html/
6、测试
启动目标主机,然后使用如下命令启动nginx,即可通过浏览器测试访问。
/usr/local/nginx
在浏览器中输入目标机IP,测试
转载于:https://blog.51cto.com/lemidi/1391307




 本文介绍如何使用Dropbear为目标系统提供SSH远程连接服务,并通过Nginx搭建Web服务。包括Dropbear与Nginx的编译安装、配置文件移植、服务脚本创建等步骤。
本文介绍如何使用Dropbear为目标系统提供SSH远程连接服务,并通过Nginx搭建Web服务。包括Dropbear与Nginx的编译安装、配置文件移植、服务脚本创建等步骤。
















 489
489

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








