实验五、GRE over IPSec
一、实验拓朴:
二、实验目的:
1、 所有流量通过GRE封装
2、 所有流量被IPSec保护
3、 实现路由协议数据只被GRE封装,用户业务数据被IPSec所保护
三、实验配置:
(1)、实现单播通信
RT1#
interface Tunnel1 //设置tunnel通道
ip address 1.1.1.1 255.255.255.0
tunnel source 202.103.96.112 //定义tunnel源地址
tunnel destination 202.103.95.112 //定义tunnel目标地址
keepalive 20 3 //定义keepalive机制
!
interface Ethernet0/0
ip address 202.103.96.112 255.255.255.0
half-duplex
!
ip route 0.0.0.0 0.0.0.0 202.103.96.111
ip route 192.168.2.0 255.255.255.0 tunnel1 //定义细化路由,GRE是基于路由的***
!
access-list 101 permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255 //定义感兴趣流量(多余配置,便于后面的实现)
!
RT2如RT1所配
(2)、ospf over GRE,且ospf 流量只被GRE封装,用户业务数据被IPSec保护
RT1#
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key cisco address 202.103.95.112
!
crypto ipsec transform-set cisco esp-3des esp-md5-hmac
mode transport
!
crypto map cisco 10 ipsec-isakmp
set peer 202.103.95.112
set transform-set cisco
match address 101
!
interface Loopback0
ip address 192.168.1.1 255.255.255.0
!
interface Tunnel1
ip address 1.1.1.1 255.255.255.0
tunnel source 202.103.96.112
tunnel destination 202.103.95.112
crypto map cisco
!
interface Ethernet0/0
ip address 202.103.96.112 255.255.255.0
half-duplex
!
router ospf 1
router-id 1.1.1.3
log-adjacency-changes
passive-interface Ethernet0/0
network 1.1.1.1 0.0.0.0 area 0
network 192.168.1.0 0.0.0.255 area 0
!
ip route 0.0.0.0 0.0.0.0 202.103.96.111
!
access-list 101 permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
!
如果所有流量均被IPSec所保护的话,感兴趣流量应定义为:
access-list 101 permit ip host 202.103.96.112 host 202.103.95.112
并将map应用于出站口
RT2如RT1配置
四、实验调试:
RT1#show ip route
C 202.103.96.0/24 is directly connected, Ethernet0/0
1.0.0.0/24 is subnetted, 1 subnets
C 1.1.1.0 is directly connected, Tunnel1
C 192.168.1.0/24 is directly connected, Loopback0
S 192.168.2.0/24 is directly connected, Tunnel1
S* 0.0.0.0/0 [1/0] via 202.103.96.111
RT1#show ip route
C 202.103.96.0/24 is directly connected, Ethernet0/0
1.0.0.0/24 is subnetted, 1 subnets
C 1.1.1.0 is directly connected, Tunnel1
C 192.168.1.0/24 is directly connected, Loopback0
192.168.2.0/32 is subnetted, 1 subnets
O 192.168.2.1 [110/11112] via 1.1.1.2, 00:02:47, Tunnel1
S* 0.0.0.0/0 [1/0] via 202.103.96.111
RT1#
五、数据包分析:
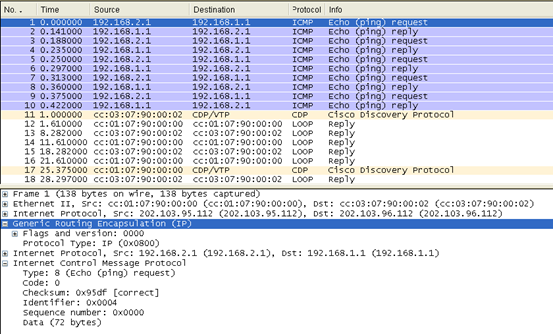
(1)、单播通信
所有的流量均被GRE封装,此处用的icmp协议,报文格式为:
| 新IP头(协议号47) | GRE头 | 原IP头 | 上层协议头 | Data |
新ip头:S:202.103.95.112 D:202.103.96.112
原ip头: S:192.168.2.1 D:192.168.1.1
上层协议头为:icmp 类型为8,代码为0 的请求报文
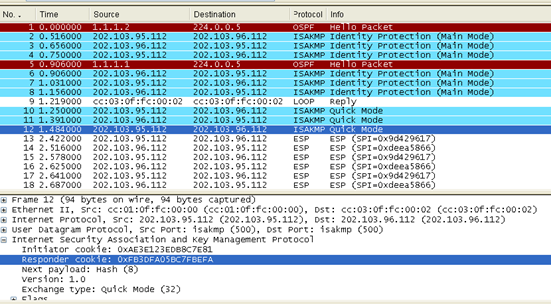
(2)、ospf流量只被GRE封装,用户业务数据被IPSec所保护
业务数据均通过udp传输,封装isakmp头部
报文格式为:
| IP头 | UDP 头 | isakmp头 | Data |
IP头为set peer的地址:S:202.103.95.112 D:202.103.96.112
UDP源目端口均为500
Ospf协议数据均被GRE封装传输
封装一个新的ip头以及一个GRE头,实际的ip封装在内部,源ip为1.1.1.2,目标ip为224.0.0.5
转载于:https://blog.51cto.com/liaoyuanchen/1194664




 本文介绍了一个关于GREoverIPSec的实验,详细说明了实验拓扑、目的、配置步骤及调试过程。实验中实现了所有流量通过GRE封装并由IPSec保护,同时确保路由协议数据仅被GRE封装,而用户业务数据则受到IPSec保护。
本文介绍了一个关于GREoverIPSec的实验,详细说明了实验拓扑、目的、配置步骤及调试过程。实验中实现了所有流量通过GRE封装并由IPSec保护,同时确保路由协议数据仅被GRE封装,而用户业务数据则受到IPSec保护。


















 1074
1074

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








