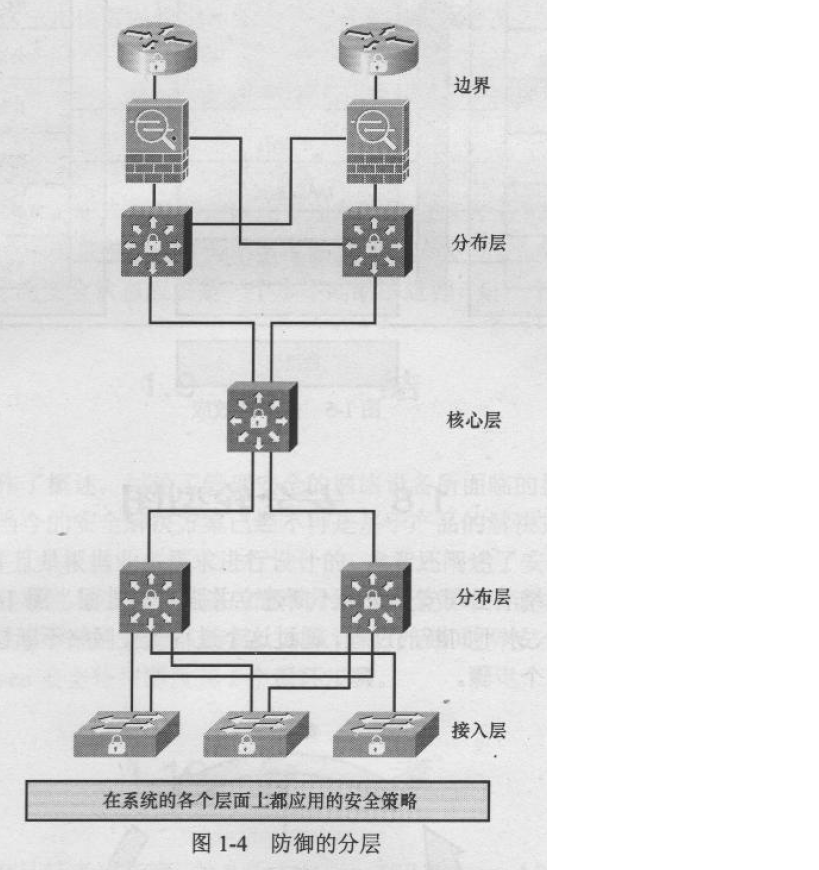
A layered approach requires implementing security solutions at different spectrums of the network. Another similar concept is islands of security. To implement islands of security, do not restrict your thinking to perimeter security. Do not depend on just one method for your security. You should, instead, have layers of protection—perimeter, distribution, core, and access layer.
This layered approach is related to the technology of an environment and the complexity of each of the technologies at each layer. The complexity comes from different protocols, applications, hardware, and security mechanisms that work at one or more of the seven layers in the OSI model. Just as there are different levels within an environment, different types of attacks can occur at each level and would require respective countermeasures.
转载于:https://blog.51cto.com/weber213/495579







 本文探讨了在网络的不同层面实施安全措施的重要性。介绍了分层安全的概念及其实施方式,包括边界的保护、分布层、核心层和接入层的安全措施。文章强调了在开放系统互连(OSI)模型的各层上应用不同技术和安全机制的必要性。
本文探讨了在网络的不同层面实施安全措施的重要性。介绍了分层安全的概念及其实施方式,包括边界的保护、分布层、核心层和接入层的安全措施。文章强调了在开放系统互连(OSI)模型的各层上应用不同技术和安全机制的必要性。
















 448
448

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








