实验目的与要求:
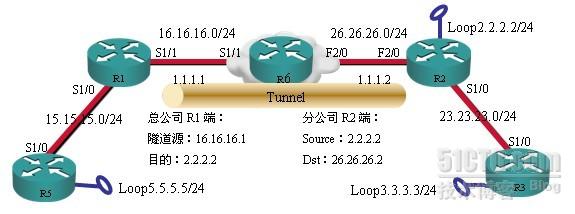
R1为总公司出口路由,R6模拟外网,起DHCP,R2模拟分公司网络出口,动态获取IP,R2利用环回口发起×××会话(因为外网接口是动态获取的IP,R1的GRE隧道没法指定destination,就指向R2的loop接口)。
分公司接入端为动态地址就使用Dynamic P2P GRE over ipsec来实现×××,但是流量必须由动态的一段发起才能建立***。
实验配置要点:
R5和R3需要简单配置ip地址和静态路由,R6需要配置ip地址和dhcp即可。
R1总公司配置:
crypto isakmp policy 1 //IKE策略
encr 3des
authentication pre-share
hash sha
group 2
crypto isakmp key gezi123 address 0.0.0.0 0.0.0.0 //定义psk密钥,对端允许所有地址
crypto ipsec transform-set myset esp-3des esp-sha-hmac //转换集,可以工作在transport模式
crypto dynamic-map dmap 10
set transform-set myset
crypto map mymap local-address Serial1/1 //和静态P2P GRE over ipsec的唯一区别
crypto map mymap 1 ipsec-isakmp dynamic dmap
interface Tunnel1 //创建GRE隧道
ip address 1.1.1.1 255.255.255.0
tunnel source 16.16.16.1
tunnel destination 2.2.2.2 //目的地址指向对端换回口,因为对端接口ip是动态的(不固定)。
speed auto
interface Serial1/0
ip address 15.15.15.1 255.255.255.0
clock rate 64000
interface Serial1/1
ip address 16.16.16.1 255.255.255.0
clock rate 64000
crypto map mymap
router ospf 1
log-adjacency-changes
//需要将tunnel口的ip也宣告进ospf,否则不能建立邻居关系
network 1.1.1.0 0.0.0.255 area 0
network 15.15.15.0 0.0.0.255 area 0
ip route 0.0.0.0 0.0.0.0 16.16.16.6
//指定到tunnel destination的静态路由,不指定的话建立的ospf邻居关系不稳定,up和down状态之间一直切换。
ip route 2.2.2.2 255.255.255.255 16.16.16.6
R2分公司的配置:
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp key gezi123 address 16.16.16.1
crypto ipsec transform-set myset esp-3des esp-sha-hmac
crypto map mymap local-address FastEthernet2/0
crypto map mymap 1 ipsec-isakmp
set peer 16.16.16.1
set transform-set myset
match address 100
interface Loopback0
ip address 2.2.2.2 255.255.255.0
interface Tunnel1
ip address 1.1.1.2 255.255.255.0
tunnel source Loopback0
tunnel destination 16.16.16.1
interface Serial1/0
ip address 23.23.23.2 255.255.255.0
clock rate 64000
interface FastEthernet2/0
ip address dhcp //该端口地址是由dhcp服务器动态分分配的地址
crypto map mymap
router ospf 1
log-adjacency-changes
network 1.1.1.0 0.0.0.255 area 0
network 23.23.23.0 0.0.0.255 area 0
ip route 0.0.0.0 0.0.0.0 26.26.26.6
access-list 100 permit gre host 2.2.2.2 host 16.16.16.1 //感兴趣流量是从loop0发起的
实验验证:
r2#sh crypto isakmp sa
dst src state conn-id slot status
16.16.16.1 26.26.26.10 QM_IDLE 7 0 ACTIVE
r2#sh crypto ipsec sa
interface: FastEthernet2/0
Crypto map tag: mymap, local addr 26.26.26.10
protected vrf: (none)
local ident (addr/mask/prot/port): (2.2.2.2/255.255.255.255/47/0) //本地源地址
remote ident (addr/mask/prot/port): (16.16.16.1/255.255.255.255/47/0) //远端目的地址
current_peer 16.16.16.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 226, #pkts encrypt: 226, #pkts digest: 226
#pkts decaps: 185, #pkts decrypt: 185, #pkts verify: 185
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 44, #recv errors 0
local crypto endpt.: 26.26.26.10, remote crypto endpt.: 16.16.16.1 //真实的出口地址
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0
current outbound spi: 0xD931AE00(3643911680)
inbound esp sas:
spi: 0xB70B3F53(3070967635)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2001, flow_id: SW:1, crypto map: mymap
sa timing: remaining key lifetime (k/sec): (4569885/2758)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xD931AE00(3643911680)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2002, flow_id: SW:2, crypto map: mymap
sa timing: remaining key lifetime (k/sec): (4569885/2758)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
查看NAT:
r2#sh ip nat translations
Pro Inside global Inside local Outside local Outside global
icmp 26.26.26.10:11 3.3.3.3:11 6.6.6.6:11 6.6.6.6:11
icmp 26.26.26.10:12 23.23.23.3:12 6.6.6.6:12 6.6.6.6:12
icmp 26.26.26.10:14 23.23.23.3:14 6.6.6.6:14 6.6.6.6:14
实验总结:
此方案虽然可以使用路由协议和NAT,但是致命的缺点就是只能是点对点建立×××。对于多个分公司的接入就束手无策了。
转载于:https://blog.51cto.com/xiaomeng/775022







 本文介绍了一种通过动态P2P GRE over IPsec实现总公司与分公司间安全通信的方法。实验中,R1作为总公司出口路由器,R6模拟外网并提供DHCP服务,R2作为分公司出口路由器,其IP地址动态获取。配置中,R1创建了指向R2环回接口的GRE隧道,并使用IPSec进行加密。分公司端R2则通过DHCP获取IP地址,并发起×××连接。
本文介绍了一种通过动态P2P GRE over IPsec实现总公司与分公司间安全通信的方法。实验中,R1作为总公司出口路由器,R6模拟外网并提供DHCP服务,R2作为分公司出口路由器,其IP地址动态获取。配置中,R1创建了指向R2环回接口的GRE隧道,并使用IPSec进行加密。分公司端R2则通过DHCP获取IP地址,并发起×××连接。
















 645
645

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








