5.3 命名ACL
实验目的:
1、掌握命名ACL的基本编写。
2、理解命名ACL的基本特性。
3、理解命名ACL和编号ACL的区别。
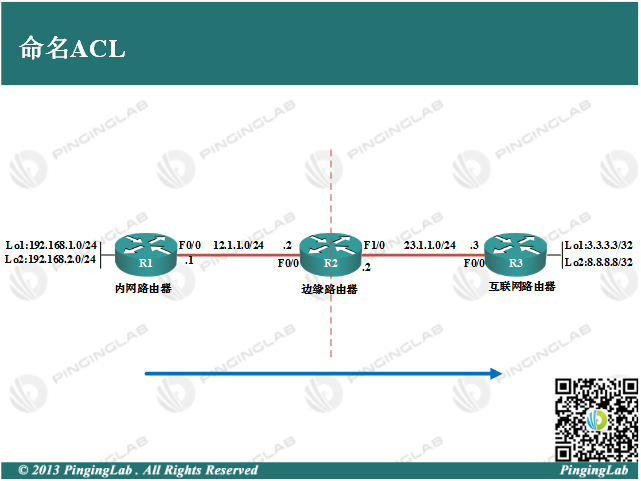
实验拓扑:
实验步骤:
1、依据图中拓扑,配置各个路由器的IP地址,并部署静态路由保证全网连通,配置如下:
R1上
R1(config)#ip route 23.1.1.0 255.255.255.0 12.1.1.2
R1(config)#ip route 3.3.3.3 255.255.255.255 12.1.1.2
R1(config)#ip route 8.8.8.8 255.255.255.255 12.1.1.2
R2上
R2(config)#ip route 192.168.1.0 255.255.255.0 12.1.1.1
R2(config)#ip route 192.168.2.0 255.255.255.0 12.1.1.1
R2(config)#ip route 3.3.3.3 255.255.255.255 23.1.1.3
R2(config)#ip route 8.8.8.8 255.255.255.255 23.1.1.3
R3上
R3(config)#ip route 12.1.1.0 255.255.255.0 23.1.1.2
R3(config)#ip route 192.168.1.0 255.255.255.0 23.1.1.2
R3(config)#ip route 192.168.2.0 255.255.255.0 23.1.1.2
测试连通性,如下:
R1#ping 3.3.3.3 source 192.168.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 40/40/40 ms
R1#ping 8.8.8.8 source 192.168.2.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
Packet sent with a source address of 192.168.2.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 36/43/56 ms
可以看到,内网与外网通信没有问题。
2、在R2上部署基于命名的标准ACL,使得内网网段192.168.1.0/24不能访问外网,其他都能访问,配置如下:
R2(config)#ip access-list standard DENYVLAN10
R2(config-std-nacl)#deny 192.168.1.0 0.0.0.255
R2(config-std-nacl)#permit any
R2(config-std-nacl)#exit
R2(config)#int f0/0
R2(config-if)#ip access-group DENYVLAN10 in
R2(config-if)#exit
测试ACL的效果,让内网路由器R1访问外网路由器R3,如下:
R1#ping 3.3.3.3 source 192.168.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
UUUUU
Success rate is 0 percent (0/5)
R1#ping 8.8.8.8 source 192.168.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
UUUUU
Success rate is 0 percent (0/5)
R1#ping 3.3.3.3 source 192.168.2.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds:
Packet sent with a source address of 192.168.2.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 16/38/64 ms
R1#ping 8.8.8.8 source 192.168.2.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
Packet sent with a source address of 192.168.2.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 20/38/48 ms
从上面很明显的看出,内网网段192.168.1.0/24无法访问外网,其他网段可以。
3、在R2上部署命名拓展ACL,使得内网网段192.168.1.0/24不能访问外网主机3.3.3.3的23号端口,192.168.2.0/24网段不能Ping通8.8.8.8,配置如下:
R2上
R2(config)#ip access-list extended DENYSERVICE
R2(config-ext-nacl)#deny tcp 192.168.1.0 0.0.0.255 host 3.3.3.3 eq 23
R2(config-ext-nacl)#deny icmp 192.168.2.0 0.0.0.255 host 8.8.8.8
R2(config-ext-nacl)#permit ip any any
R2(config-ext-nacl)#exit
R2(config)#int f0/0
R2(config-if)#ip access-group DENYSERVICE in
R3上
R3(config)#line vty 0 15
R3(config-line)#no login
R3(config-line)#exit
测试命名拓展ACL,如下:
R1#telnet 3.3.3.3 /source-interface lo1
Trying 3.3.3.3 ...
% Destination unreachable; gateway or host down
R1#telnet 3.3.3.3
Trying 3.3.3.3 ... Open
R3>exit
可以看到,R1本地环回地址192.168.1.1无法远程访问3.3.3.3,其他地址则可以。
R1#ping 8.8.8.8
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 36/40/44 ms
R1#ping 8.8.8.8 source loopback 2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
Packet sent with a source address of 192.168.2.1
UUUUU
Success rate is 0 percent (0/5)
此时192.168.2.0网段无法Ping通8.8.8.8,但是其他网段可以。
4、管理命名ACL
①查看ACL状态
R2#show ip access-lists
Extended IP access list DENYSERVICE
10 deny tcp 192.168.1.0 0.0.0.255 host 3.3.3.3 eq telnet (3 matches)
20 deny icmp 192.168.2.0 0.0.0.255 host 8.8.8.8 (15 matches)
30 permit ip any any (20 matches)
②删除ACL语句
R2(config)#ip access-list extended DENYSERVICE
R2(config-ext-nacl)#no 10
③查看ACL状态
R2#show ip access-lists
Extended IP access list DENYSERVICE
20 deny icmp 192.168.2.0 0.0.0.255 host 8.8.8.8 (15 matches)
30 permit ip any any (20 matches)
④插入ACL语句
R2(config)#ip access-list extended DENYSERVICE
R2(config-ext-nacl)#25 deny tcp 192.168.1.0 0.0.0.255 host 3.3.3.3 eq telnet
⑤查看ACL状态
Extended IP access list DENYSERVICE
20 deny icmp 192.168.2.0 0.0.0.255 host 8.8.8.8 (15 matches)
25 deny tcp 192.168.1.0 0.0.0.255 host 3.3.3.3 eq telnet
30 permit ip any any (20 matches)
从上面实验可以看到,基于命名的标准和拓展ACL,语法上与基于编号的ACL没有任何区别,只不过是将编号换成名字罢了,即便如此,命名ACL在管理方面更加人性化。此实验完成。
==========================================
PingingLab·高品质IT教育提供商
CCIE 实验室·IT项目实战·高端人才定制
深圳拼客信息科技有限公司·广州大学城外环西路站
新浪微博:@拼客科技PingingLab @PingingLab-陈鑫杰
PingingLab微信公众号:pinginglab
PingingLab技术交流群:240920680
转载于:https://blog.51cto.com/chenxinjie/1274479





















 240
240

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








