javascript防注入代码,过滤关键字! 其实没啥用,就是学下正则表达式,比如upupdatedate,过滤掉update还有update.
没啥意思.
js版的防范SQL注入式攻击代码:

 代码
代码
<
script language
=
"
javascript
"
>
<!--
var url = location.search;
var re = / ^\?(.*)(select%20|insert%20|delete%20from%20|count\(|drop%
20table | update % 20truncate % 20 | asc\( | mid\( | char \( | xp_cmdshell | exec %
20master | net % 20localgroup % 20administrators | \ " |:|net%20user|\|%20or%20)(.*)
$/gi;
var e = re.test(url);
if(e) {
alert( " 地址中含有非法字符~ " );
location.href= " error.asp " ;
}
//-->
</script>
<!--
var url = location.search;
var re = / ^\?(.*)(select%20|insert%20|delete%20from%20|count\(|drop%
20table | update % 20truncate % 20 | asc\( | mid\( | char \( | xp_cmdshell | exec %
20master | net % 20localgroup % 20administrators | \ " |:|net%20user|\|%20or%20)(.*)
$/gi;
var e = re.test(url);
if(e) {
alert( " 地址中含有非法字符~ " );
location.href= " error.asp " ;
}
//-->
</script>
规则中的%20是javascript的URL编码,是空格的意思.
可以看看document.write(escape(' '));输入的就是%20
alert(decodeURIComponent('%20')); 输出的是空格
假设我们输入http://www.xxx.com/?id=select *
就会报如下错误:
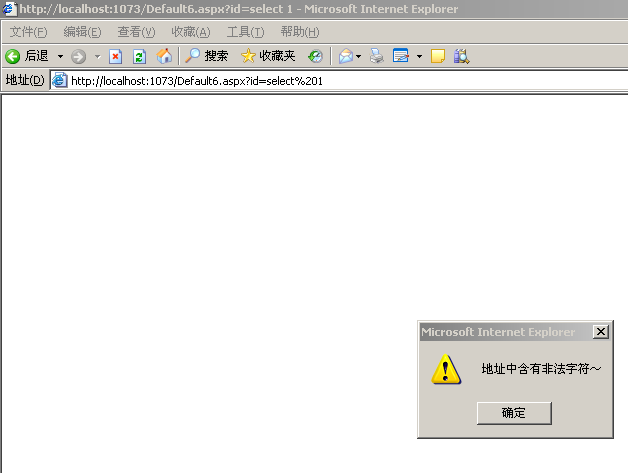
如果直接输入http://www.xx.com/?id=select -->select后价格空格键
并不会过滤,因为地址栏中会去掉末尾的空格.




 本文介绍了一种使用JavaScript进行前端SQL注入防护的方法,通过正则表达式匹配并过滤潜在的恶意字符串来保护应用程序的安全。
本文介绍了一种使用JavaScript进行前端SQL注入防护的方法,通过正则表达式匹配并过滤潜在的恶意字符串来保护应用程序的安全。

















 349
349

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








