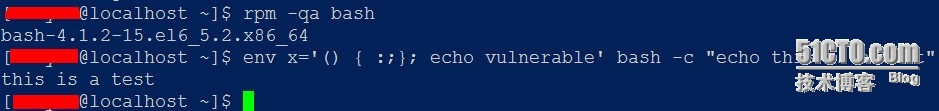
RedHat和CentOS 检查bash漏洞方法,如果显示下面提示,说明存在漏洞
|
1
2
3
|
# env x='() { :;}; echo vulnerable' bash -c "echo this is a test"
vulnerable
this is a
test
|
具体修补方法,不用指定bash版本,因为系统自己会识别的
|
1
2
3
|
yum update
bash
-y
/sbin/ldconfig
rpm -qa
bash
|
打完补丁后,下面示例
centos 5.5系统
|
1
2
|
# rpm -qa bash
bash
-3.2-33.el5.1
|
centos 6.4系统
|
1
2
|
# rpm -qa bash
bash
-4.1.2-15.el6_5.1.x86_64
|
打完补丁后执行,如果是下面的提示,说明漏洞已经修复
|
1
2
3
4
|
# env x='() { :;}; echo vulnerable' bash -c "echo this is a test"
bash
: warning: x: ignoring
function
definition attempt
bash
: error importing
function
definition
for
`x'
this is a
test
|
RedHat漏洞说明 https://access.redhat.com/articles/1200223
CentOS修复方式 http://lists.centos.org/pipermail/centos/2014-September/146099.html
不过现在网上有另一种说法,即使打补丁,不过还可以绕过去,那么
如果php-fpm用www用户运行的话,需要检查/etc/passwd 下是不是可以登录的/bin/bash
www:x:80:80::/home/www:/bin/bash
如果是,那么需要执行
|
1
2
3
|
# chsh www -s /sbin/nologin
Changing shell
for
www.
Shell changed.
|
现在php-fpm的用户www为www:x:80:80::/home/www:/sbin/nologin,可以阻止用此用户登录到后台
如果没有进行上面的更新升级,可以进行如下做一步到位的补丁修复,直接将bash更新为bash-4.1.2-15.el6_5.2.X86_64(CentOS6系列):
再次升级为bash-4.1.2-15.el6_5.2.x86_64
由于昨天打的补丁还可以绕过去,所以今天再次升级,这次升级的版本为
bash-4.1.2-15.el6_5.2.x86_64(CentOS 6)
https://rhn.redhat.com/errata/RHSA-2014-1306.html# Red Hat Enterprise Linux Server (v. 6)
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
|
# yum update bash
Loaded plugins: fastestmirror
Loading mirror speeds from cached hostfile
* base: mirrors.skyshe.cn
* extras: mirrors.skyshe.cn
* updates: mirrors.skyshe.cn
Setting up Update Process
Resolving Dependencies
--> Running transaction check
---> Package
bash
.x86_64 0:4.1.2-15.el6_5.1 will be updated
---> Package
bash
.x86_64 0:4.1.2-15.el6_5.2 will be an update
--> Finished Dependency Resolution
Dependencies Resolved
=====================================================================================
Package Arch Version Repository Size
=====================================================================================
Updating:
bash
x86_64 4.1.2-15.el6_5.2 updates 905 k
Transaction Summary
=====================================================================================
Upgrade 1 Package(s)
Total download size: 905 k
Is this ok [y
/N
]: y
Downloading Packages:
bash
-4.1.2-15.el6_5.2.x86_64.rpm | 905 kB 01:22
Running rpm_check_debug
Running Transaction Test
Transaction Test Succeeded
Running Transaction
Updating :
bash
-4.1.2-15.el6_5.2.x86_64 1
/2
Cleanup :
bash
-4.1.2-15.el6_5.1.x86_64 2
/2
Verifying :
bash
-4.1.2-15.el6_5.2.x86_64 1
/2
Verifying :
bash
-4.1.2-15.el6_5.1.x86_64 2
/2
Updated:
bash
.x86_64 0:4.1.2-15.el6_5.2
Complete!
|
如果显示的版本依然是bash-4.1.2-15.el6_5.1.x86_64,那么清空yum缓存后再更新,至此,漏洞修复完善,可以安心
|
1
2
3
4
5
6
7
8
9
|
# yum clean all
# yum makecache #这两步一般不用
# yum update bash
# /sbin/ldconfig
# rpm -qa bash
bash
-4.1.2-15.el6_5.2.x86_64
# env x='() { :;}; echo vulnerable' bash -c "echo this is a test"
this is a
test
#现在说明漏洞已修复
|







 本文介绍如何检查并修复RedHat和CentOS系统中的Bash漏洞,包括具体的修补步骤、验证方法及额外的安全措施。
本文介绍如何检查并修复RedHat和CentOS系统中的Bash漏洞,包括具体的修补步骤、验证方法及额外的安全措施。

















 2万+
2万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








