转:https://hackernoon.com/exploiting-electron-rce-in-exodus-wallet-d9e6db13c374
Exploiting Electron RCE in Exodus wallet
While browsing Twitter I’ve noticed ElectronJS remote code execution vulnerability in protocol handler. That sounds severe. As stated in official description, for application to be vulnerable is enough to register itself as default handler for some protocol. I had one application based on Electron installed on my laptop that I was looking into some time ago — Exodus cryptocurrencies wallet. I knew that it registers itself as a handler for exodus:// URI scheme.
Since no details about vulnerability were presented on the official blog post, I went straight to electron Github looking for recent commits. The following commit was a fix for vulnerability. Biggest change was a newly created file command_line_args.cc which implements few check for command line arguments.
Basically, the code checks command line arguments against a blacklist. Based on that, it can be assumed that it is possible to inject command line arguments via URI handler. Electron based applications are basically bunch of Javascript and HTML files rendered by Chromium for front-end and nodejs for back-end. And Chromium and nodejs is bundled inside main executable file. Those strings of blacklist in fix commit is command line switches for Chromium and nodejs. Seems that to exploit vulnerability we only need to find command line option in Chromium or nodejs that allows to spawn additional process.
To test if it is really possible to inject arguments to Exodus.exe via protocol I created HTML file:
<!doctype html>
<script>
window.location = 'exodus://aaaaaaaaa --aaaaa='
</script>
Exodus wallet was launched with the following arguments.
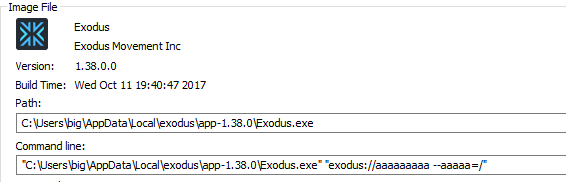
Payload was wrapped with double quotes. Nevertheless, double quote was not filtered out or sanitized before passing as command line arguments. The following allowed to inject additional command line switch.
<!doctype html>
<script>
window.location = 'exodus://aaaaaaaaa" --aaaaa=bbbb'
</script>
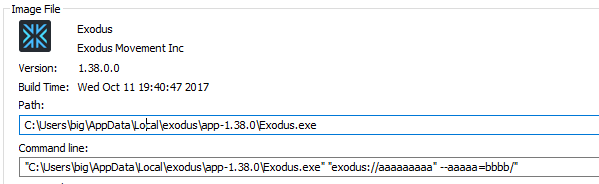
For remote code execution it is needed to find nice Chromium command line switch that allows to execute additional command. I found page containing nicely summarized list of Chromium command line switches. gpu-launcher looked promising.
— gpu-launcher Extra command line options for launching the GPU process (normally used for debugging). Use like renderer-cmd-prefix.
Time to try it.
<!doctype html>
<script>
window.location = 'exodus://aaaaaaaaa" --gpu-launcher="cmd" --aaaaa='
</script>

Exodus wallet was quick to release an update, it was released shortly after announcement of vulnerability. Also, it does a good job by pushing an update for end users by displaying messages, nevertheless update is not automatic and user still has to confirm an update. Anyway, there is ton of desktop applications based on Electron, so better check if any app running on your machine is based on Electron and make sure it is patched.




 本文介绍了一种针对基于Electron的应用程序Exodus钱包的远程代码执行漏洞利用方法。通过注册默认URI处理程序并注入命令行参数,可以实现对目标应用的攻击。文章详细展示了如何构造payload,并成功触发漏洞。
本文介绍了一种针对基于Electron的应用程序Exodus钱包的远程代码执行漏洞利用方法。通过注册默认URI处理程序并注入命令行参数,可以实现对目标应用的攻击。文章详细展示了如何构造payload,并成功触发漏洞。

















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








