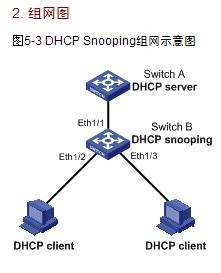
1. 组网需求
Switch B通过以太网端口Ethernet1/1连接到DHCP服务器,通过以太网端口Ethernet1/2、Ethernet1/3连接到DHCP客户端。要求:
l
与DHCP服务器相连的端口可以转发DHCP服务器的响应报文,而其他端口不转发DHCP服务器的响应报文。
l
记录DHCP-REQUEST和信任端口收到的DHCP-ACK广播报文中DHCP客户端IP地址及MAC地址的绑定关系。
配置步骤
# 使能DHCP Snooping功能。
<SwitchB> system-view
[SwitchB] dhcp-snooping
# 配置Ethernet1/1端口为信任端口。
[SwitchB] interface ethernet 1/1
[SwitchB-Ethernet1/1] dhcp-snooping trust
[SwitchB-Ethernet1/1] quit
支持Option 82配置举例
1. 组网需求l
Switch B上使能DHCP Snooping功能,并支持Option 82功能;
l
对包含Option 82的请求报文的处理策略为replace;
l
在Ethernet1/2上配置Ciruict ID填充内容为company001,Remote ID填充内容为device001;
l
在Ethernet1/3上配置以verbose模式填充Option 82,接入节点标识为sysname,填充格式为ASCII格式。
l
Switch B将添加Option 82的DHCP请求报文转发给DHCP服务器Switch A,使得DHCP客户端可以获取到IP地址。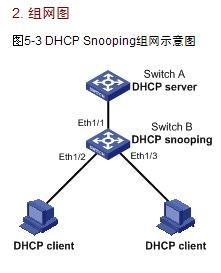
3. 配置步骤# 使能DHCP Snooping功能。
<SwitchB> system-view
[SwitchB] dhcp-snooping
# 配置Ethernet1/1端口为信任端口。
[SwitchB] interface ethernet 1/1
[SwitchB-Ethernet1/1] dhcp-snooping trust
[SwitchB-Ethernet1/1] quit
# 在Ethernet1/2上配置DHCP Snooping支持Option 82功能。
[SwitchB] interface ethernet 1/2
[SwitchB-Ethernet1/2] dhcp-snooping information enable
[SwitchB-Ethernet1/2] dhcp-snooping information strategy replace
[SwitchB-Ethernet1/2] dhcp-snooping information circuit-id string company001
[SwitchB-Ethernet1/2] dhcp-snooping information remote-id string device001
[SwitchB-Ethernet1/2] quit
# 在端口Ethernet1/3上配置DHCP Snooping支持Option 82功能。
[SwitchB] interface ethernet 1/3
[SwitchB-Ethernet1/3] dhcp-snooping information enable
[SwitchB-Ethernet1/3] dhcp-snooping information strategy replace
[SwitchB-Ethernet1/3] dhcp-snooping information format verbose node-identifier sysname
[SwitchB-Ethernet1/3] dhcp-snooping information circuit-id format-type ascii
[SwitchB-Ethernet1/3] dhcp-snooping information remote-id format-type ascii
转载于:https://www.cnblogs.com/bethal/p/5800670.html




















 1万+
1万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








