一 ICMP协议简介
ICMP(internet control message protocol)是面向无连接、不可靠的、基于网络层的消息控制协议,它可以传输数据报错信息、网络状况信息、主机状况信息等。
1.ICMP数据封装
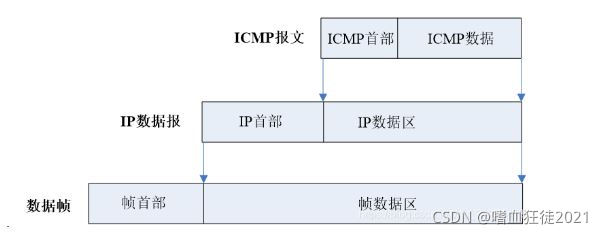
ICMP报文是使用IP数据报来封装和发送的,携带ICMP报文的IP数据报完全像其他类型数据的数据报那样在网络中被转发,没有额外的可靠性和优先级,由于IP数据报本身被放在底层物理数据帧中进行发送,因此,ICMP报文本身也可能丢失或者出现传输错误。
2.ICMP报文类型
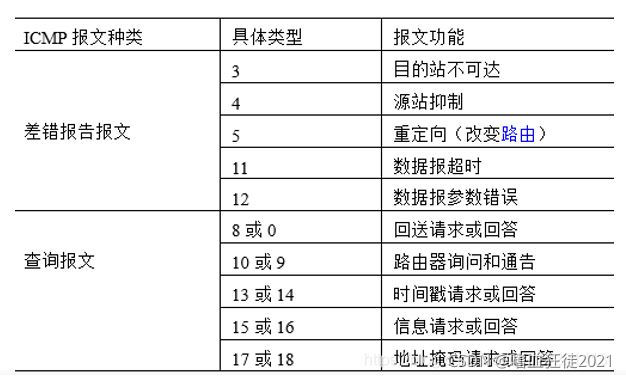
ICMP报文可以分为两大类:ICMP差错报告报文和ICMP查询报文。差错报告报文主要用来向IP数据报源主机返回一个差错报告信息,查询报文用于一台主机向另一台主机查询特定的信息,通常查询报文是成对出现的,即源主机发起一个查询报文,在目的主机收到该报文后,会按照查询报文约定的格式为源主机返回一个应答报文。
注意, ICMP差错报文并不能纠正差错,它只是简单地报告差错。
二 使用snort规则检测ping不可达事件
ping命令是使用ICMP协议,现在需要制定snort规则,对ping不可达事件进行告警,具体snort规则如下:
include classification.config
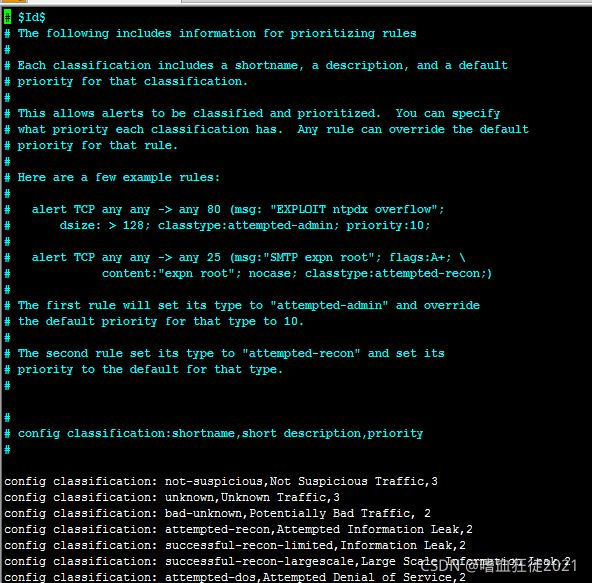
alert icmp any any -> any any (msg:"ICMP Destination Unreachable."; itype:3; icode:1; sid:48511; rev:4;)1.classification.config是在snort配置文件,具体如下所示:
2.itype是icmp类型,表明Destination unreachable
3.icode是icmp相关代码,表明Host unreachable
4.使用命令抓包:
 利用Snort规则检测和防御ICMP攻击与异常:从ping不可达到复杂网络探测
利用Snort规则检测和防御ICMP攻击与异常:从ping不可达到复杂网络探测





 本文介绍了ICMP协议的基础概念,重点讲解了如何使用Snort规则检测ping不可达事件,并展示了针对不同类型ICMP报文的高级检测规则,包括恶意扫描、网络探测和安全威胁。通过实例演示,读者将了解如何设置和应用这些规则以增强网络安全防护。
本文介绍了ICMP协议的基础概念,重点讲解了如何使用Snort规则检测ping不可达事件,并展示了针对不同类型ICMP报文的高级检测规则,包括恶意扫描、网络探测和安全威胁。通过实例演示,读者将了解如何设置和应用这些规则以增强网络安全防护。
 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章

















 5617
5617

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








