bool IsRooted() {
const char* paths[] = {
"/system/app/Superuser.apk",
"/sbin/su",
"/system/bin/su",
"/system/xbin/su",
"/data/local/xbin/su",
"/data/local/bin/su",
"/system/sd/xbin/su",
"/system/bin/failsafe/su",
"/data/local/su",
"/su/bin/su"
};
for (const auto& path : paths) {
if (access(path, F_OK) == 0)
return true;
}
return false;
}
// ========================
// Check Running Processes for Suspicious Names
// ========================
bool IsProcessSuspicious() {
DIR* proc = opendir("/proc");
if (!proc) return false;
struct dirent* ent;
while ((ent = readdir(proc)) != nullptr) {
if (ent->d_type != DT_DIR) continue;
std::string pid = ent->d_name;
if (!std::all_of(pid.begin(), pid.end(), ::isdigit))
continue;
std::string cmdlinePath = "/proc/" + pid + "/cmdline";
std::ifstream cmdFile(cmdlinePath, std::ios::binary);
std::string line;
if (std::getline(cmdFile, line, '\0')) { // cmdline is null-terminated
std::transform(line.begin(), line.end(), line.begin(), ::tolower);
static const std::vector<std::string> suspiciousNames = {
"frida-server", "frida", "gg", "gameguardian",
"termux", "canary", "httpcanary", "su", "magisk",
"sqlite", "tcpdump", "xposed", "substrate", "lsposed"
};
for (const auto& name : suspiciousNames) {
if (line.find(name) != std::string::npos) {
closedir(proc);
LOGI("Suspicious process detected: %s (PID: %s)", line.c_str(), pid.c_str());
return true;
}
}
}
cmdFile.close();
}
closedir(proc);
return false;
}
// ========================
// Check for known tool binaries on disk
// ========================
bool HasToolBinary() {
const std::vector<std::string> toolPaths = {
"/data/local/tmp/frida-server",
"/data/data/com.termux/",
"/storage/emulated/0/Download/gg",
"/data/local/tmp/gg",
"/data/local/tmp/magisk",
"/system/bin/frida-server",
"/system/xbin/su",
"/data/local/tmp/su",
"/data/local/tmp/scrcpy"
};
for (const auto& path : toolPaths) {
if (access(path.c_str(), F_OK) == 0) {
LOGI("Malicious binary detected at: %s", path.c_str());
return true;
}
}
return false;
}
// ========================
// Root & Package Detection with Crash
// ========================
void RootAndToolCheck() {
uintptr_t UE4Base = GetModuleBase("libUE4.so"); // Change if your target is different (e.g. libil2cpp.so)
if (!UE4Base) {
LOGE("Cannot perform detection: libUE4.so not loaded yet or missing.");
return;
}
// Apply offset to get function pointer
uintptr_t CMessageBoxExt_address = UE4Base + 0x7d88bb4; // ⚠️ Ensure this offset matches your build!
auto CMessageBoxExt = reinterpret_cast<int(*)(int, const char16_t*, const char16_t*)>(CMessageBoxExt_address);
std::vector<std::string> dangerousTools = {
"com.topjohnwu.magisk",
"com.noshufou.android.su",
"eu.chainfire.supersu",
"com.koushikdutta.rommanager",
"com.dimonvideo.luckypatcher",
"com.chelpus.lackypatch",
"com.termux",
"org.kali.nethunter",
"com.guoshi.httpcanary",
"catch_.me_.if_.you_.can_", // GameGuardian
"com.frida.server",
"re.frida.server",
"org.mozilla.fenix", // Firefox Canary
"com.jakting.rns", // Root Navigation
"com.ghidra", "com.jadx", "com.bin.mt", "com.mt.helper"
};
std::string detectedTool;
for (const auto& pkg : dangerousTools) {
if (IsPackageInstalled(pkg.c_str())) {
detectedTool = pkg;
break;
}
}
if (IsRooted() && detectedTool.empty()) {
detectedTool = "ROOT ACCESS DETECTED";
}
if (!detectedTool.empty()) {
std::u16string msg = u"RAT INJECTING BECAUSE YOU TRYING TO CRACK OR DUMP\nTool: ";
msg += convertToUtf16(detectedTool).c_str();
msg += u"\nPehle delete kar warna teri details leak";
CMessageBoxExt(0, msg.c_str(), u"warning !! mat panga le");
// Trigger crash (simulate anti-cheat kill)
__builtin_trap(); // Safer than *(int*)0 = 0;
}
}
// ======================== Add all packages if detect it crash the game
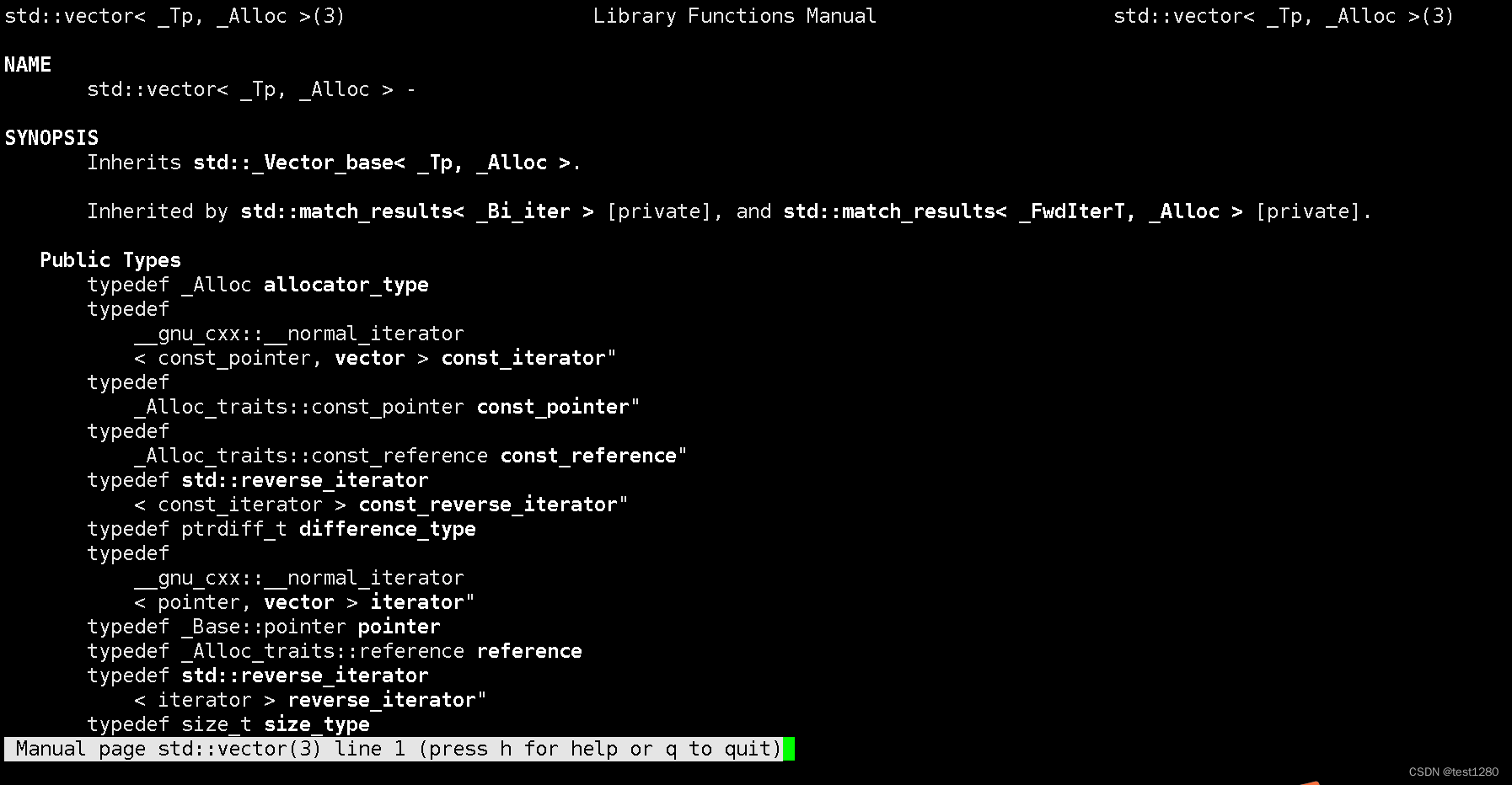





 博客围绕Linux系统中出现的‘No manual entry for std::vector’报错展开,介绍了解决该报错的方法,并对解决结果进行验证,还给出了参考链接。
博客围绕Linux系统中出现的‘No manual entry for std::vector’报错展开,介绍了解决该报错的方法,并对解决结果进行验证,还给出了参考链接。
















 8012
8012

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








