在日常工作中曾经遇到过添加各种各种读取属性,文件节点无权限。setenforce 0 之后,操作正常的,就可以确认为selinux权限问题了,下面记录曾经遇到过的权限问题
1. 最简单的一类就是按照万能公式缺什么,加什么权限。加完权限,编译也没报错,替换后也解决问题的
type=1400 audit(1698809417.118:102): avc: denied { read write } for comm="HwBinder:245_1" name="wake_lock" dev="sysfs" ino=4980 scontext=u:r:tvhalserver:s0 tcontext=u:object_r:sysfs_wake_lock:s0 tclass=file permissive=1
type=1400 audit(1698809417.118:103): avc: denied { open } for comm="HwBinder:245_1" path="/sys/power/wake_lock" dev="sysfs" ino=4980 scontext=u:r:tvhalserver:s0 tcontext=u:object_r:sysfs_wake_lock:s0 tclass=file permissive=1
语法:rule_name source_type target_type : class perm_set**
万能公式:
缺少什么权限:{ read write open}权限
谁缺少权限:scontext=u:r:tvhalserver:s0
对谁缺少权限:tcontext=u:object_r:sysfs_wake_lock:s0
什么类型:tclass=file
+++ b/sepolicy/tvhalserver.te
@@ -183,4 +183,9 @@ allow tvhalserver hal_tv_earc_default:binder { call };
allow tvhalserver hal_tv_earc_default:file { getattr };
allow tvhalserver userdata_file:dir { search read open getattr remove_name };
allow tvhalserver userdata_file:file { write ioctl lock };
+allow tvhalserver sysfs_wake_lock:file { open read write };
2.1 dac_override 添加权限后,编译出现never allow 的。比如下面这个
type=1400 audit(1698809417.118:101): avc: denied { dac_override } for comm="HwBinder:245_1" capability=1 scontext=u:r:tvhalserver:s0 tcontext=u:r:tvhalserver:s0 tclass=capability permissive=1
+++ b/sepolicy/tvhalserver.te
@@ -190,4 +190,6 @@ allow tvhalserver powerctl_prop:property_service { set };
allow tvhalserver hal_power_default:dir { search };
+allow tvhalserver tvhalserver:capability { dac_override };
编译的时候会出现nerverallow 报错:
libsepol.report_failure: neverallow on line 342 of system/sepolicy/private/domain.te (or line 40681 of policy.conf) violated by allow tvhalserver tvhalserver:capability { dac_override };
libsepol.check_assertions: 1 neverallow failures occurred
看来遇到dac_override权限问题时,不能直接 allow XXX {dac_override} 这种形式来修复
因为tvhalserver 操作了节点 /sys/power/wake_lock 出现的错误。
wakelock 的owner 为radio, group 为wake_lock,而tvhalserver属于root 的。由于发生了跨用户访问发生了该权限问题
参考 https://blog.youkuaiyun.com/jbhand/article/details/109776691
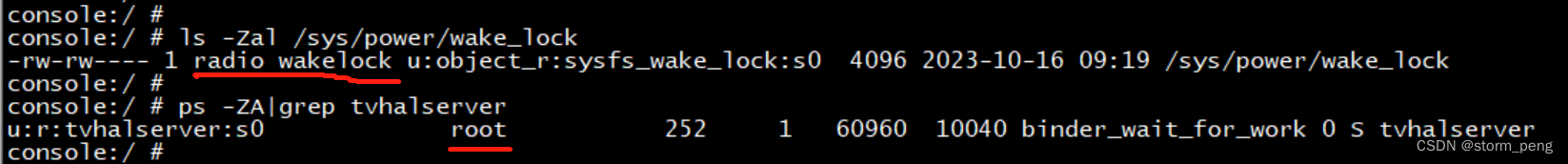 在tvhalserver 启动所在的.rc 文件group 那里添加wakelock。修改如下:
在tvhalserver 启动所在的.rc 文件group 那里添加wakelock。修改如下:
+++ b/tvhalserver/android/vendor.xxxxx.hardware.tvhalserver@1.0.rc
@@ -3,5 +3,5 @@ on early-boot
service tvhalserver /vendor/bin/hw/tvhalserver
interface vendor.xxxxx.hardware.tvhalserver@1.0::ITvhalServer default
class hal
- group system root media audio
+ group system root media audio wakelock
user root
2.2. 下面这个是另外一个修改,也出现了dac_override 权限报错。修改方法类似
type=1400 audit(1698826891.472:2122): avc: denied { dac_override } for comm="HwBinder:289_1" capability=1 scontext=u:r:system_control:s0 tcontext=u:r:system_control:s0 tclass=capability permissive=1
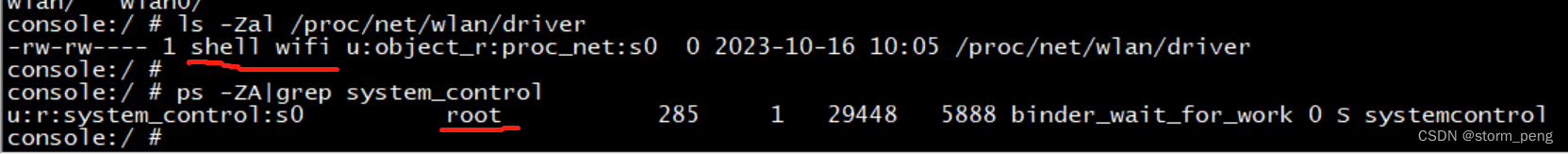
+++ b/frameworks/services/systemcontrol/systemcontrol.rc
@@ -9,6 +9,6 @@ on post-fs-data
service system_control /vendor/bin/systemcontrol
user root
- group system root media audio
+ group system root media audio wifi
3. 对vendor_default_prop 加 setprop 权限neverallow,需要在xxx_contexts修改tcontext 名字
需要设置一个属性,运行报错如下
type=1107 audit(1698317251.320:13): uid=0 auid=4294967295 ses=4294967295 subj=u:r:init:s0 msg='avc: denied { set } for property=persist.vendor.aml.tv.lightnumber pid=243 uid=0 gid=1000 scontext=u:r:tvhalserver:s0 tcontext=u:object_r:vendor_default_prop:s0 tclass=property_service permissive=1'
+++ b/sepolicy/property_contexts
@@ -19,6 +19,7 @@ persist.vendor.bt_suspend u:object_r:vendor_platform_prop:s0
persist.vendor.wifibt_drv_path u:object_r:vendor_platform_prop:s0
+persist.vendor.aml.tv.lightnumber u:object_r:vendor_default_prop:s0
diff --git a/sepolicy/tvhalserver.te b/sepolicy/tvhalserver.te
index 3c48998..daf9bd1 100644
--- a/sepolicy/tvhalserver.te
+++ b/sepolicy/tvhalserver.te
@@ -35,6 +35,7 @@ get_prop(tvhalserver, vendor_media_prop)
get_prop(tvhalserver, vendor_tv_prop)
set_prop(tvhalserver, vendor_tv_prop)
get_prop(tvhalserver, vendor_default_prop)
+set_prop(tvhalserver, vendor_default_prop)
@@ -189,3 +190,4 @@ allow tvhalserver powerctl_prop:property_service { set };
allow tvhalserver sysfs_wake_lock:file { open read write };
+allow tvhalserver vendor_default_prop:property_service { set };
加上上面的权限后,又出现了neverallow 报错了
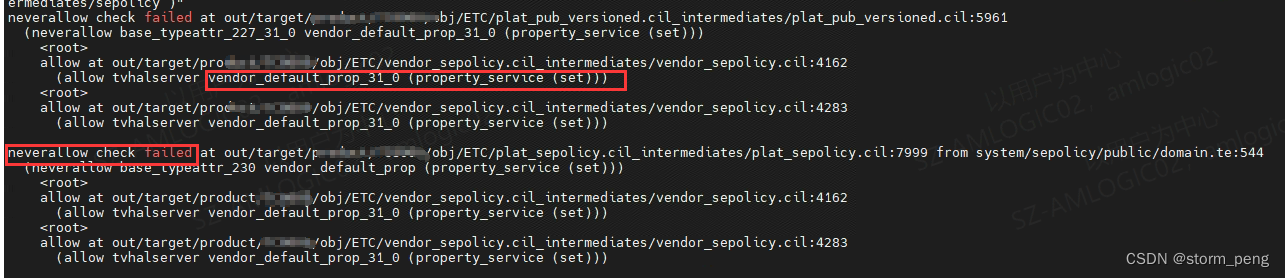
从上图看,在检查neverallow 时,在system\sepolicy\public\domain.te 544行 拦截报错了。除了init, vendor_init,其他的所有进程都不允许对vendor_default_prop 执行property_set 的操作
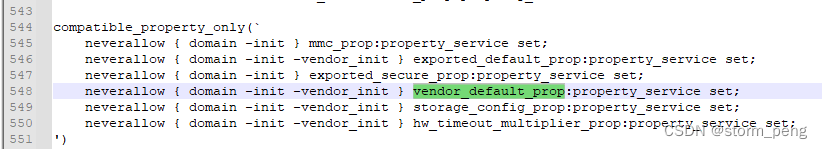
参考https://blog.51cto.com/u_15127527/4402759
既然不允许对vendor_default_prop 执行property_set,那就针对要设置的属性,换个名字。
1)在property.te 定义vendor_light_prop
2)property_contexts 里把要设的属性,和新名字vendor_light_prop关联起来
3)在tvhalserver.te 添加权限
这样修改完毕,编译就没有错误了
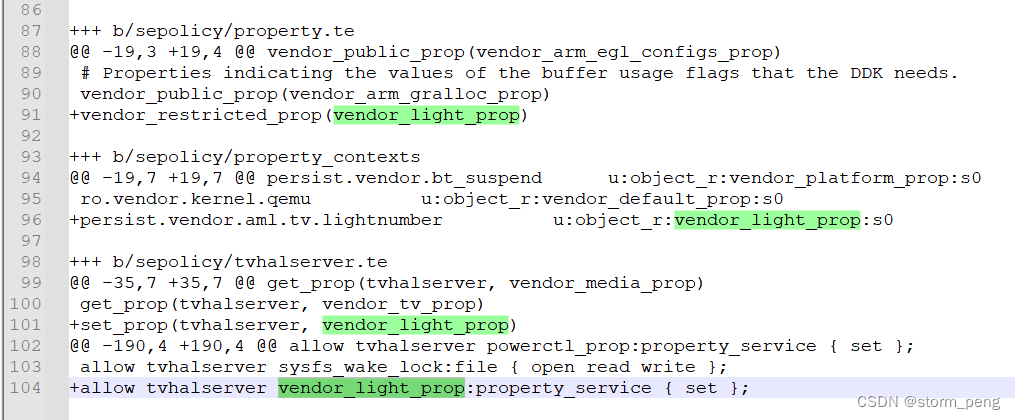
更新运行的时候,在getprop 时出现的hal_light_default 对 vendor_light_prop 没有 read, open, getattr, map权限。这个按照万能公式直接添加后就没问题了
type=1400 audit(0.0:18): avc: denied { read } for name="u:object_r:vendor_light_prop:s0" dev="tmpfs" ino=321 scontext=u:r:hal_light_default:s0 tcontext=u:object_r:vendor_light_prop:s0 tclass=file permissive=1
type=1400 audit(0.0:19): avc: denied { open } for path="/dev/__properties__/u:object_r:vendor_light_prop:s0" dev="tmpfs" ino=321 scontext=u:r:hal_light_default:s0 tcontext=u:object_r:vendor_light_prop:s0 tclass=file permissive=1
type=1400 audit(0.0:20): avc: denied { getattr } for path="/dev/__properties__/u:object_r:vendor_light_prop:s0" dev="tmpfs" ino=321 scontext=u:r:hal_light_default:s0 tcontext=u:object_r:vendor_light_prop:s0 tclass=file permissive=1
type=1400 audit(0.0:21): avc: denied { map } for path="/dev/__properties__/u:object_r:vendor_light_prop:s0" dev="tmpfs" ino=321 scontext=u:r:hal_light_default:s0 tcontext=u:object_r:vendor_light_prop:s0 tclass=file permissive=1
修改如下:
+++ b/sepolicy/hal_light_default.te
@@ -4,4 +4,5 @@ allow hal_light_default tvhalserver_hwservice:hwservice_manager find;
allow hal_light_default sysfs_display:dir search;
+allow hal_light_default vendor_light_prop:file { read map open getattr };4. 操作虚拟文件节点,出现权限错误后,按万能公式添加权限,编译出现neverallow,不能在file_contexts 改名,而是要在genfs_contexts 这里面改名,加权限
场景:客户的app 应用需要在他的APP 里,读取系统文件节点,但运行的时候,获取不到需要的值。setenforce 0之后,运行时出现下面报错
type=1400 audit(0.0:618): avc: denied { read } for name="life_time" dev="sysfs" ino=259311 scontext=u:r:system_app:s0 tcontext=u:object_r:sysfs:s0 tclass=file permissive=1
type=1400 audit(0.0:619): avc: denied { open } for path="/sys/devices/platform/soc/fe08c000.mmc/mmc_host/mmc0/mmc0:0001/life_time" dev="sysfs" ino=259311 scontext=u:r:system_app:s0 tcontext=u:object_r:sysfs:s0 tclass=file permissive=1
type=1400 audit(0.0:620): avc: denied { getattr }for path="/sys/devices/platform/soc/fe08c000.mmc/mmc_host/mmc0/mmc0:0001/life_time" dev="sysfs" ino=259311 scontext=u:r:system_app:s0 tcontext=u:object_r:sysfs:s0 tclass=file permissive=1
按常规在system_app.te 添加权限,
allow system_app sysfs:file { open read getattr };
编译出现nerverallow
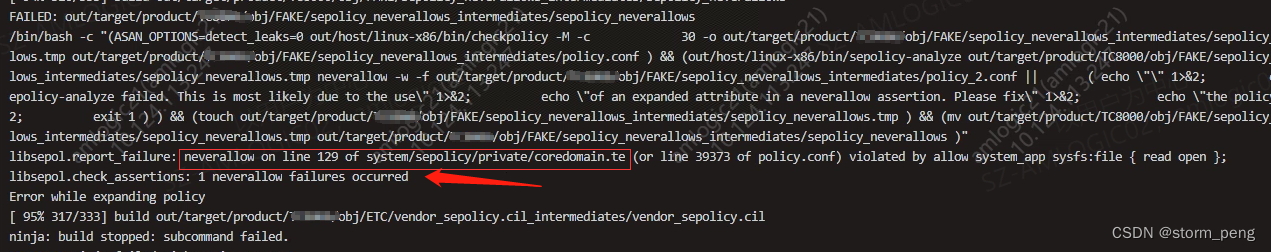
coredomain.te不允许对sysfs 有读写权限
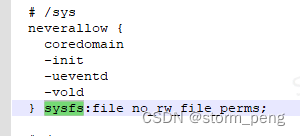
按照3 的方法,修改 scontexts 的role 名称
diff --git a/sepolicy/file.te b/sepolicy/file.te
index 79c767d..64c0f22 100755
--- a/sepolicy/file.te
+++ b/sepolicy/file.te
@@ -100,6 +100,7 @@ type sysfs_mm, fs_type, sysfs_type;
type aml_debugfs, fs_type, debugfs_type;
type sysfs_dmc, fs_type, sysfs_type;
+type sysfs_devices_block, fs_type, sysfs_type;
diff --git a/sepolicy/file_contexts b/sepolicy/file_contexts
index d03c1a0..5acd658
--- a/sepolicy/file_contexts
+++ b/sepolicy/file_contexts
@@ -312,6 +312,7 @@
/sys/devices/platform/soc/[0-9a-z]*\.sdio/mmc_host/mmc[0-9]/mmc[0-9]:000[0-9]/mmc[0-9]:000[0-9]:[0-9]/net/ap[0-1](/.*)? u:object_r:sysfs_net:s0
+/sys/devices/platform/soc/[0-9a-z]*\.mmc/mmc_host/mmc[0-9]/mmc[0-9]:000[0-9](/.*)? u:object_r:sysfs_devices_block:s0
diff --git a/sepolicy/system_app.te b/sepolicy/system_app.te
index 05ef9e1..7896b92
--- a/sepolicy/system_app.te
+++ b/sepolicy/system_app.te
@@ -106,4 +106,4 @@ allow system_app video_block_device:dir { open read search getattr };
allow system_app video_block_device:file { getattr open read };
allow system_app data_vendor_tcl_file:file { getattr read };
+#allow system_app sysfs_devices_block:file { open read getattr };
ls -z /sys/devices/platform/soc/fe08c000.mmc/mmc_host/mmc0/mmc0:0001/life_time
名字依然没变过来

后来搜到一个例子:https://cpu52.com/archives/298.html
在sepolicy/genfs_contexts 按下面修改之后
+++ b/sepolicy/genfs_contexts
@@ -14,5 +14,5 @@ genfscon sysfs /class/astream u:object_r:sysfs_astream:s0
genfscon sysfs /devices/virtual/astream/astream-dev u:object_r:sysfs_astream:s0
+genfscon sysfs /devices/platform/soc/fe08c000.mmc/mmc_host/mmc0/mmc0:0001 u:object_r:sysfs_devices_block:s0
再ls -z /sys/devices/platform/soc/fe08c000.mmc/mmc_host/mmc0/mmc0:0001/life_time 名字就变过来了
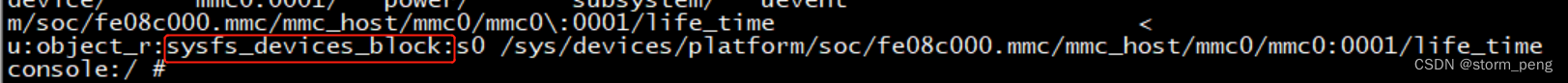
接下来加上权限运行就没有问题了
diff --git a/sepolicy/system_app.te b/sepolicy/system_app.te
index ec84588..67e0a6d 100755
--- a/sepolicy/system_app.te
+++ b/sepolicy/system_app.te
@@ -106,3 +106,4 @@ allow system_app video_block_device:dir { open read search getattr };
allow system_app video_block_device:file { getattr open read };
+allow system_app sysfs_devices_block:file { open read getattr };




















 3433
3433

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








