内核文档(Address Space Layout Randomization):
- Documentation for /proc/sys/kernel/ — The Linux Kernel documentation
- https://www.kernel.org/doc/Documentation/sysctl/kernel.txt
- 3.15.1 Address Space Layout Randomization (oracle.com)
randomize_va_space
This option can be used to select the type of process address space randomization that is used in the system, for architectures that support this feature.
| 0 | Turn the process address space randomization off. This is the default for architectures that do not support this feature anyways, and kernels that are booted with the “norandmaps” parameter. |
| 1 | Make the addresses of mmap base, stack and VDSO page randomized. This, among other things, implies that shared libraries will be loaded to random addresses. Also for PIE-linked binaries, the location of code start is randomized. This is the default if the CONFIG_COMPAT_BRK option is enabled. |
| 2 | Additionally enable heap randomization. This is the default if There are a few legacy applications out there (such as some ancient versions of libc.so.5 from 1996) that assume that brk area starts just after the end of the code+bss. These applications break when start of the brk area is randomized. There are however no known non-legacy applications that would be broken this way, so for most systems it is safe to choose full randomization. Systems with ancient and/or broken binaries should be configured with |
地址空间布局随机化默认是开启的,开启了之后进程的虚拟地址空间布局就不再是默认布局,vm_area_struct链接成的结构大概就是这样的:
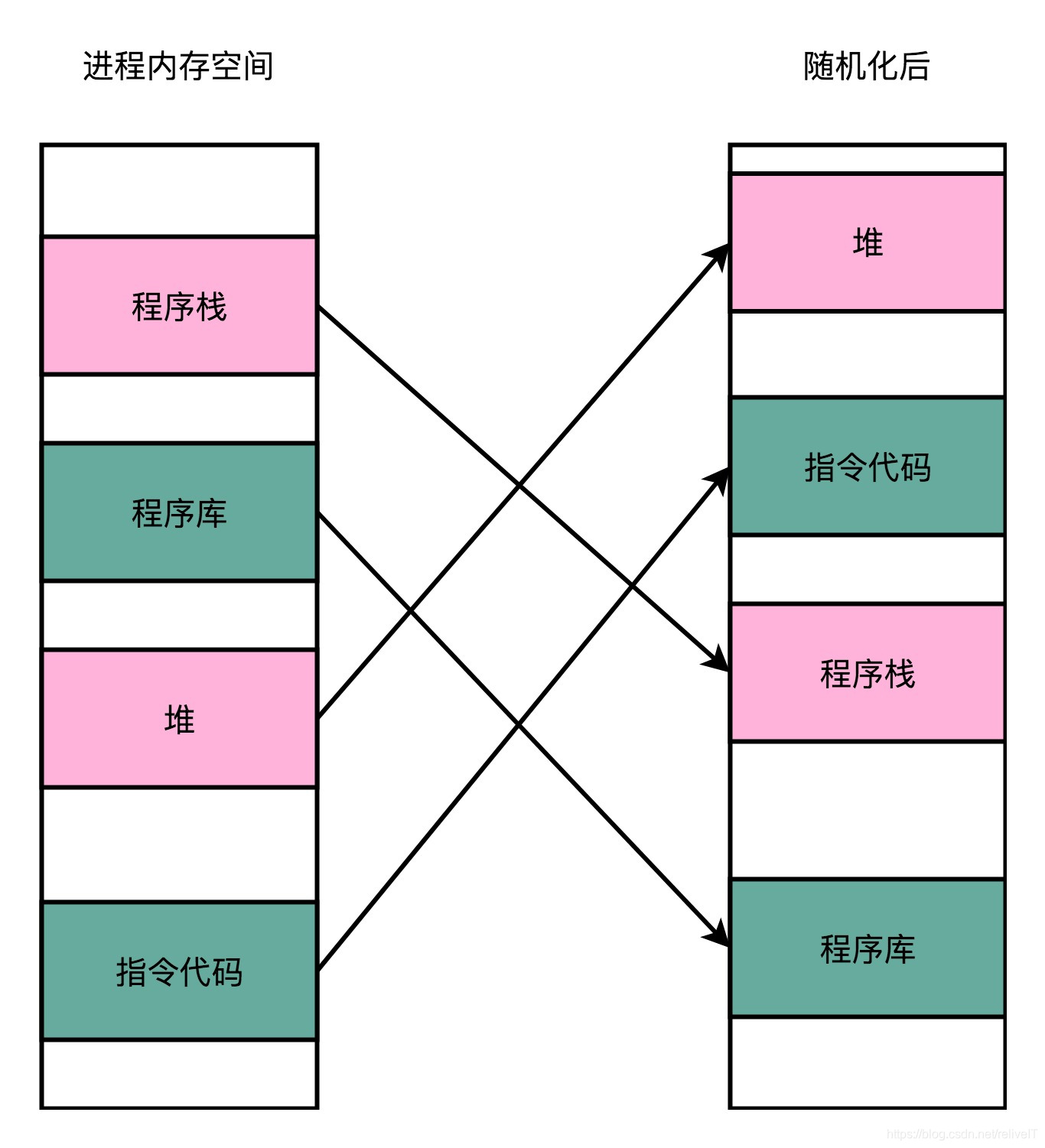
GNU Linux中修改ASLR的方法:
You can change the setting temporarily by writing a new value to , for example: /proc/sys/kernel/randomize_va_space
# echo value > /proc/sys/kernel/randomize_va_spaceTo change the value permanently, add the setting to , for example: /etc/sysctl.conf
kernel.randomize_va_space = valueand run the sysctl -p command.
If you change the value of , you should test your application stack to ensure that it is compatible with the new setting. randomize_va_space
If necessary, you can disable ASLR for a specific program and its child processes by using the following command:
% setarch `uname -m` -R program [args ...]







 本文介绍了Linux内核中的Address Space Layout Randomization(ASLR)技术,包括其作用和默认设置。通过调整/proc/sys/kernel/randomize_va_space,用户可以临时或永久改变ASLR的级别。为确保应用程序兼容性,更改设置后应进行测试。若需禁用特定程序的ASLR,可使用特定命令。
本文介绍了Linux内核中的Address Space Layout Randomization(ASLR)技术,包括其作用和默认设置。通过调整/proc/sys/kernel/randomize_va_space,用户可以临时或永久改变ASLR的级别。为确保应用程序兼容性,更改设置后应进行测试。若需禁用特定程序的ASLR,可使用特定命令。

















 613
613

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








