环境:
| hostname | 角色 | release | IP | Iptables and firewalld |
| server1 | Master | rhel6.5 | 172.25.37.1/24 | Disabled |
| server2 | Web1 | rhel6.5 | 172.25.37.2/24 | Disabled |
| server3 | Web2 | rhel6.5 | 172.25.37.3/24 | Disbaled |
| server4 | BackUp | rhel6.5 | 172.25.37.4/24 | Disavled |
【1】在server2和server3上面安装httpd服务。
[root@server2 ~]# yum install -y httpd
[root@server2 ~]# /etc/init.d/httpd start
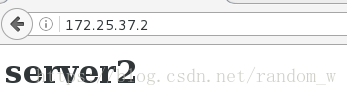
[root@server2 ~]# echo "<h1> server2 </h1>" > /var/www/html/index.html
测试:
[root@server3 ~]# yum install -y httpd
[root@server3 ~]# /etc/init.d/httpd start
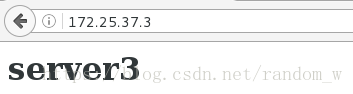
[root@server3 ~]# echo "<h1> server3 </h1>" > /var/www/html/index.html
测试:
【2】在server2和server3上面禁用arp对虚拟IP的响应
[root@server2 ~]# yum install -y arptables_jf
[root@server2 ~]# arptables -A IN -d 172.25.37.100 -j DROP
[root@server2 ~]# arptables -A OUT -s 172.25.37.100 -j mangle --mangle-ip-s 172.25.37.2
[root@server2 ~]# /etc/init.d/arptables_jf save
Saving current rules to /etc/sysconfig/arptables: [ OK ]
[root@server2 ~]# ip addr add 172.25.37.100 dev eth0
[root@server3 ~]# yum install -y arptables_jf
[root@server3 ~]# arptables -A IN -d 172.25.37.100 -j DROP
[root@server3 ~]# arptables -A OUT -s 172.25.37.100 -j mangle --mangle-ip-s 172.25.37.3
[root@server3 ~]# /etc/init.d/arptables_jf save
Saving current rules to /etc/sysconfig/arptables: [ OK ]
[root@server3 ~]# ip addr add 172.25.37.100 dev eth0
【3】在server1上面安装keepalived和ipvsadm
[root@server1 ~]# yum install -y keepalived ipvsadm
[root@server1 ~]# cat /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
root@localhost
}
notification_email_from root@localhost
smtp_server 127.0.0.1
smtp_connect_timeout 30
router_id LVS_DEVEL
}
vrrp_instance VI_1 {
state MASTER
interface eth0
virtual_router_id 51
priority 150
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
172.25.37.100
}
}
virtual_server 172.25.37.100 80 {
delay_loop 6
lb_algo rr
lb_kind DR
nat_mask 255.255.255.0
persistence_timeout 50
protocol TCP
real_server 172.25.37.2 80 {
weight 1
TCP_CHECK {
connect_port 80
connect_timeout 3
nb_get_retry 3
delay_before_retry 3
}
}
real_server 172.25.37.3 80 {
weight 1
TCP_CHECK {
connect_port 80
connect_timeout 3
nb_get_retry 3
delay_before_retry 3
}
}
}[root@server1 ~]# /etc/init.d/keepalived start
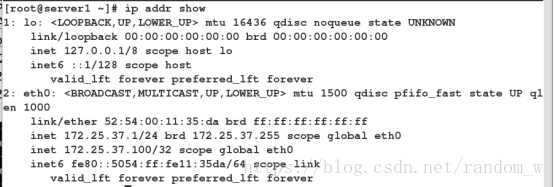
[root@server1 ~]# ipvsadm -Ln
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 172.25.37.100:80 rr persistent 50
-> 172.25.37.2:80 Route 1 0 0
-> 172.25.37.3:80 Route 1 0 0
测试:
关于不能在同一台主机实现轮询参考博客:
https://blog.youkuaiyun.com/xqj198404/article/details/52103465
【4】在server4进行与server1相同操作
注:server4的keepalived配置文件要将MASTER改为BACKUP,priority的值改为小于150的一个值。
开启keepalived
测试高可用:
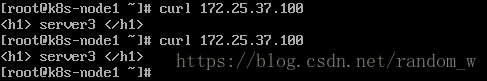
[root@random rhel6.5]# curl 172.25.37.100
<h1> server3 </h1>
将master关闭模拟故障:
[root@server1 ~]# /etc/init.d/keepalived stop
再次访问,访问正常:
[root@random rhel6.5]# curl 172.25.37.100
<h1> server3 </h1>
在server4上面可以查看到ipvs信息。
[root@server4 ~]# ipvsadm -Ln
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 172.25.37.100:80 rr persistent 50
-> 172.25.37.2:80 Route 1 0 0
-> 172.25.37.3:80 Route 1 0 2
在server1上面看不到任何信息:
[root@server1 ~]# ipvsadm -Ln
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn




 本文详细介绍了如何在RHEL 6.5环境下搭建基于Keepalived和IPVS的高可用负载均衡系统。包括HTTP服务安装、ARP响应禁用、Keepalived及IPVS配置等步骤,并通过实际案例演示了故障转移的过程。
本文详细介绍了如何在RHEL 6.5环境下搭建基于Keepalived和IPVS的高可用负载均衡系统。包括HTTP服务安装、ARP响应禁用、Keepalived及IPVS配置等步骤,并通过实际案例演示了故障转移的过程。
















 949
949

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








