结构目录
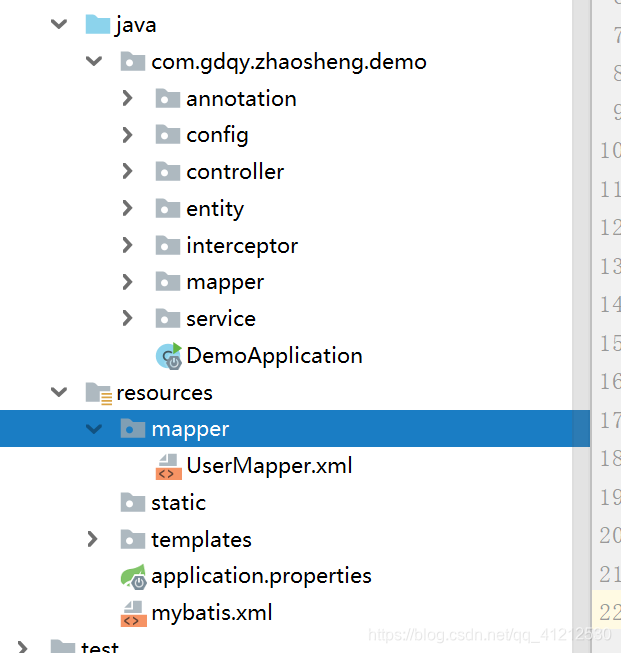
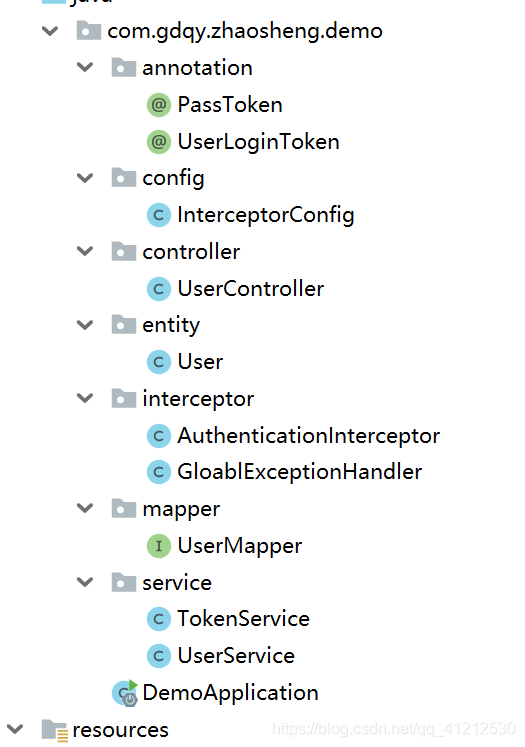
一 annotation包
package com.gdqy.zhaosheng.demo.annotation;
import java.lang.annotation.ElementType;
import java.lang.annotation.Retention;
import java.lang.annotation.RetentionPolicy;
import java.lang.annotation.Target;
@Target({ElementType.METHOD, ElementType.TYPE})
@Retention(RetentionPolicy.RUNTIME)
public @interface PassToken {
boolean required() default true;
}
二 config包,拦截请求
package com.gdqy.zhaosheng.demo.config;
import com.gdqy.zhaosheng.demo.interceptor.AuthenticationInterceptor;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.web.servlet.config.annotation.InterceptorRegistry;
import org.springframework.web.servlet.config.annotation.WebMvcConfigurer;
@Configuration
public class InterceptorConfig implements WebMvcConfigurer {
@Override
public void addInterceptors(InterceptorRegistry registry) {
registry.addInterceptor(authenticationInterceptor())
.addPathPatterns("/**"); // 拦截所有请求,通过判断是否有 @LoginRequired 注解 决定是否需要登录
}
@Bean
public AuthenticationInterceptor authenticationInterceptor() {
return new AuthenticationInterceptor();
}
}
三 interceptor包有两个类
第一个,AuthenticationInterceptor类,主要是验证token
package com.gdqy.zhaosheng.demo.interceptor;
import com.auth0.jwt.JWT;
import com.auth0.jwt.JWTVerifier;
import com.auth0.jwt.algorithms.Algorithm;
import com.auth0.jwt.exceptions.JWTDecodeException;
import com.auth0.jwt.exceptions.JWTVerificationException;
import com.gdqy.zhaosheng.demo.annotation.PassToken;
import com.gdqy.zhaosheng.demo.annotation.UserLoginToken;
import com.gdqy.zhaosheng.demo.entity.User;
import com.gdqy.zhaosheng.demo.service.UserService;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.web.method.HandlerMethod;
import org.springframework.web.servlet.HandlerInterceptor;
import org.springframework.web.servlet.ModelAndView;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import java.lang.reflect.Method;
/**
* @author jinbin
* @date 2018-07-08 20:41
*/
public class AuthenticationInterceptor implements HandlerInterceptor {
@Autowired
UserService userService;
@Override
public boolean preHandle(HttpServletRequest httpServletRequest, HttpServletResponse httpServletResponse, Object object) throws Exception {
String token = httpServletRequest.getHeader("token");// 从 http 请求头中取出 token
// 如果不是映射到方法直接通过
if(!(object instanceof HandlerMethod)){
return true;
}
HandlerMethod handlerMethod=(HandlerMethod)object;
Method method=handlerMethod.getMethod();
//检查是否有passtoken注释,有则跳过认证
if (method.isAnnotationPresent(PassToken.class)) {
PassToken passToken = method.getAnnotation(PassToken.class);
if (passToken.required()) {
return true;
}
}
//检查有没有需要用户权限的注解
if (method.isAnnotationPresent(UserLoginToken.class)) {
UserLoginToken userLoginToken = method.getAnnotation(UserLoginToken.class);
if (userLoginToken.required()) {
// 执行认证
if (token == null) {
throw new RuntimeException("无token,请重新登录");
}
// 获取 token 中的 user id
String userId;
try {
userId = JWT.decode(token).getAudience().get(0);
} catch (JWTDecodeException j) {
throw new RuntimeException("401");
}
User user = userService.findUserById(userId);
if (user == null) {
throw new RuntimeException("用户不存在,请重新登录");
}
// 验证 token
JWTVerifier jwtVerifier = JWT.require(Algorithm.HMAC256(user.getPassword())).build();
try {
jwtVerifier.verify(token);
} catch (JWTVerificationException e) {
throw new RuntimeException("401");
}
return true;
}
}
return true;
}
@Override
public void postHandle(HttpServletRequest httpServletRequest, HttpServletResponse httpServletResponse, Object o, ModelAndView modelAndView) throws Exception {
}
@Override
public void afterCompletion(HttpServletRequest httpServletRequest, HttpServletResponse httpServletResponse, Object o, Exception e) throws Exception {
}
}
第二个是,GloablExceptionHandler类提示返回服务器出错
package com.gdqy.zhaosheng.demo.interceptor;
import com.alibaba.fastjson.JSONObject;
import org.springframework.web.bind.annotation.ControllerAdvice;
import org.springframework.web.bind.annotation.ExceptionHandler;
import org.springframework.web.bind.annotation.ResponseBody;
@ControllerAdvice
public class GloablExceptionHandler {
@ResponseBody
@ExceptionHandler(Exception.class)
public Object handleException(Exception e) {
String msg = e.getMessage();
if (msg == null || msg.equals("")) {
msg = "服务器出错";
}
JSONObject jsonObject = new JSONObject();
jsonObject.put("message", msg);
return jsonObject;
}
}
四 mapper包
package com.gdqy.zhaosheng.demo.mapper;
import com.gdqy.zhaosheng.demo.entity.User;
import org.apache.ibatis.annotations.Param;
public interface UserMapper {
User findByUsername(@Param("username") String username);
User findUserById(@Param("Id") String Id);
}
五 service包有两个类
第一个TokenService,封装token
package com.gdqy.zhaosheng.demo.service;
import com.auth0.jwt.JWT;
import com.auth0.jwt.algorithms.Algorithm;
import com.gdqy.zhaosheng.demo.entity.User;
import org.springframework.stereotype.Service;
@Service("TokenService")
public class TokenService {
public String getToken(User user) {
String token="";
token= JWT.create().withAudience(user.getId())// 将 user id 保存到 token 里面
.sign(Algorithm.HMAC256(user.getPassword()));// 以 password 作为 token 的密钥
return token;
}
}
第二个UserService
package com.gdqy.zhaosheng.demo.service;
import com.gdqy.zhaosheng.demo.entity.User;
import com.gdqy.zhaosheng.demo.mapper.UserMapper;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.stereotype.Service;
@Service("UserService")
public class UserService {
@Autowired
UserMapper userMapper;
public User findByUsername(User user){
return userMapper.findByUsername(user.getUsername());
}
public User findUserById(String userId) {
return userMapper.findUserById(userId);
}
}
DemoApplication 在启动程序记得添加
package com.gdqy.zhaosheng.demo;
import org.mybatis.spring.annotation.MapperScan;
import org.springframework.boot.SpringApplication;
import org.springframework.boot.autoconfigure.SpringBootApplication;
@SpringBootApplication
@MapperScan("com.gdqy.zhaosheng.demo.mapper")//写你mapper接口所在的路径
public class DemoApplication {
public static void main(String[] args) {
SpringApplication.run(DemoApplication.class, args);
}
}
六 resources下的包
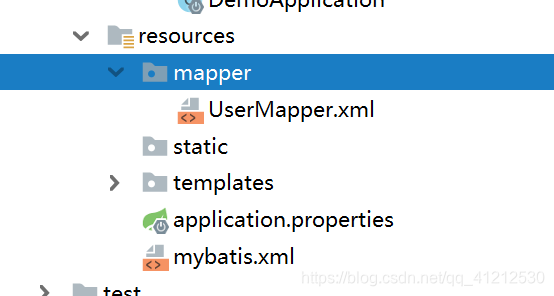
UserMapper.xml
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE mapper PUBLIC "-//mybatis.org//DTD Mapper 3.0//EN" "http://mybatis.org/dtd/mybatis-3-mapper.dtd" >
<mapper namespace="com.gdqy.zhaosheng.demo.mapper.UserMapper">
<select id="findByUsername" resultType="com.gdqy.zhaosheng.demo.entity.User">
SELECT * FROM user
where
username=#{username}
</select>
<select id="findUserById" resultType="com.gdqy.zhaosheng.demo.entity.User">
SELECT * FROM user
where
id=#{Id}
</select>
</mapper>
application.properties
server.port=6379
spring.datasource.url=jdbc:mysql://127.0.0.1:3306/booksystem?serverTimezone=UTC
spring.datasource.username=root
spring.datasource.password=123456
spring.datasource.driver-class-name=com.mysql.jdbc.Driver
spring.datasource.max-idle=10
server.tomcat.uri-encoding=UTF-8
spring.datasource.type=com.alibaba.druid.pool.DruidDataSource
#指定全局配置文件
mybatis.config-location=classpath:mybatis.xml
#指定sql文件
mybatis.mapperLocations=classpath:mapper/*.xml
mybatis.xml
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE configuration PUBLIC "-//mybatis.org//DTD Config 3.0//EN" "http://mybatis.org/dtd/mybatis-3-config.dtd">
<configuration>
<settings>
<setting name="logImpl" value="SLF4J"/>
<!-- 开启驼峰命名转换 Table(create_time) -> Entity(createTime) -->
<setting name="mapUnderscoreToCamelCase" value="true" />
</settings>
</configuration>
附上sql语句
SET NAMES utf8mb4;
SET FOREIGN_KEY_CHECKS = 0;
-- ----------------------------
-- Table structure for user
-- ----------------------------
DROP TABLE IF EXISTS `user`;
CREATE TABLE `user` (
`id` int(45) NOT NULL,
`username` varchar(255) CHARACTER SET utf8mb4 COLLATE utf8mb4_general_ci NULL DEFAULT NULL,
`password` varchar(255) CHARACTER SET utf8mb4 COLLATE utf8mb4_general_ci NULL DEFAULT NULL,
PRIMARY KEY (`id`) USING BTREE
) ENGINE = InnoDB CHARACTER SET = utf8mb4 COLLATE = utf8mb4_general_ci ROW_FORMAT = Dynamic;
-- ----------------------------
-- Records of user
-- ----------------------------
INSERT INTO `user` VALUES (1, '张三', '123456');
SET FOREIGN_KEY_CHECKS = 1;
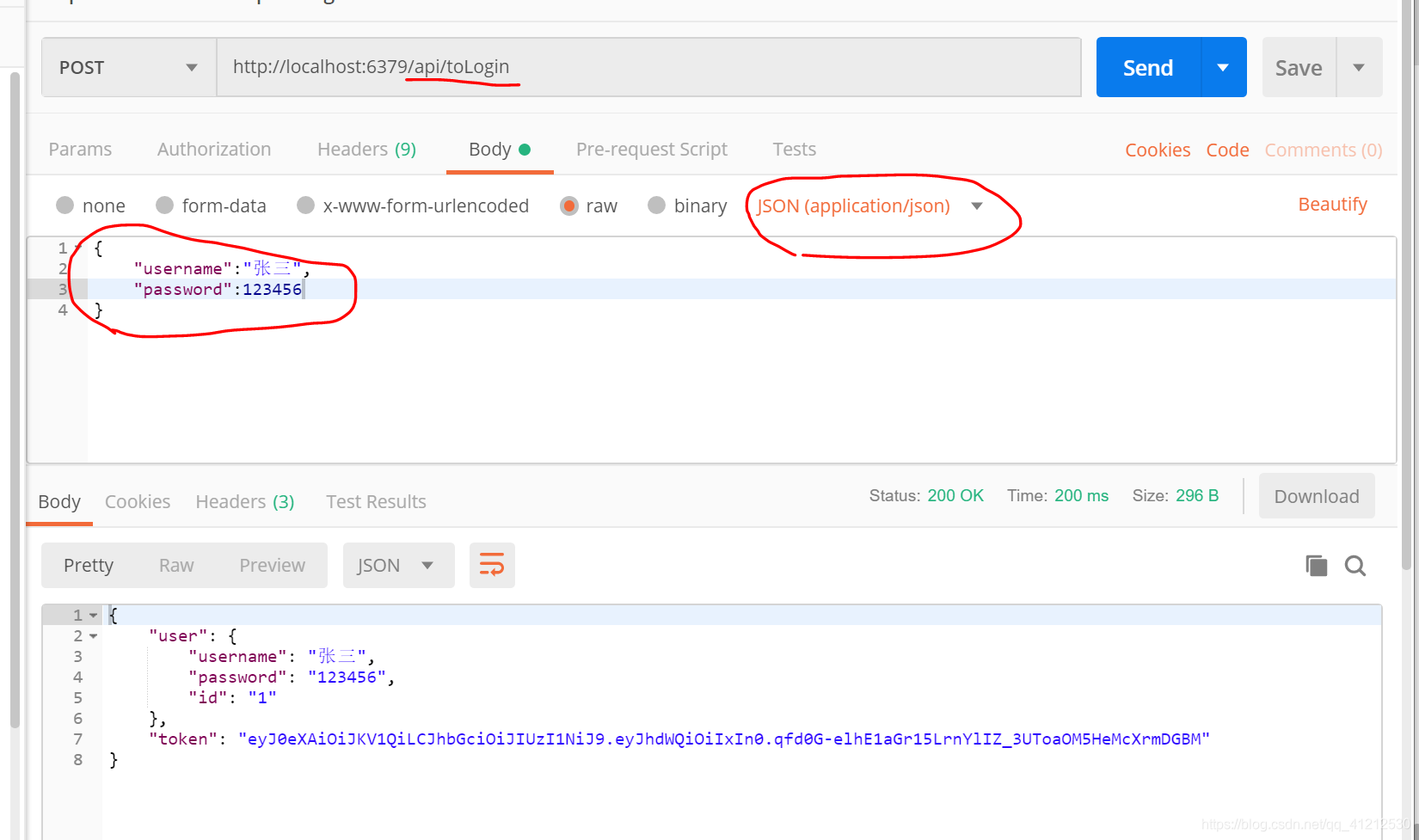
请求方式 我用的是postman接口测试工具





 本文介绍了一种基于JWT的用户认证方案,并通过Spring Boot实现了请求的拦截与验证流程。主要内容包括自定义注解、配置类、拦截器的实现及数据库操作。
本文介绍了一种基于JWT的用户认证方案,并通过Spring Boot实现了请求的拦截与验证流程。主要内容包括自定义注解、配置类、拦截器的实现及数据库操作。
















 1万+
1万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








