
标准中注册的声明:
iss:jwt签发者
sub:jwt所面向的用户
aud:接收jwt的一方
exp:jwt的过期时间,这个过期时间必须要大于签发时间
nbf:定义在什么时间之前,该jwt都是不可用的
iat:jwt的签发时间
jti:jwt的唯一身份标识,主要用来作为一次性的token,从而回避重放攻击。
以上是转发别的博客
1.导入jwt包
![]()
2.staup 设置
//启用api认证
services.AddAuthentication(JwtBearerDefaults.AuthenticationScheme).AddJwtBearer(
option =>
{
var secretByte = Encoding.UTF8.GetBytes(_configuration["Authentication:SecretKey"]);
option.TokenValidationParameters = new TokenValidationParameters()
{
//只有我们的接口后端的发出的接口才能访问
ValidateIssuer = true,
ValidIssuer = _configuration["Authentication:Issuer"],
//验证token的持有者
ValidateAudience = true,
ValidAudience = _configuration["Authentication:Audience"],
//验证token是否过期
ValidateLifetime = true,
//token私钥传入进来进行加密
IssuerSigningKey = new SymmetricSecurityKey(secretByte)
};
}
);
app.UseAuthentication();//认证
app.UseAuthorization();//授权
3.配置appsetting.json
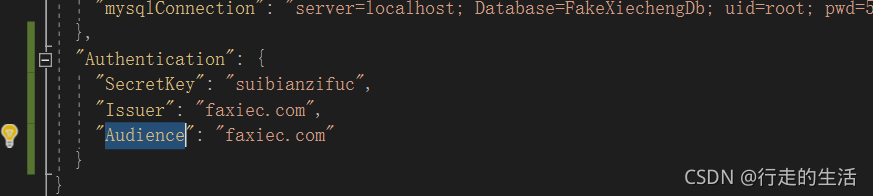
4. 在控制器编码
using System;
using System.Collections.Generic;
using System.Linq;
using System.Threading.Tasks;
using Microsoft.AspNetCore.Authorization;
using Microsoft.AspNetCore.Http;
using Microsoft.AspNetCore.Mvc;
using FakeXiecheng.API.Dtos;
using Microsoft.IdentityModel.Tokens;
using System.Security.Claims;
using System.IdentityModel.Tokens.Jwt;
using Microsoft.Extensions.Configuration;
using System.Text;
namespace FakeXiecheng.API.Controllers
{
[Route("auth")]
[ApiController]
public class AuthenticateController : ControllerBase
{
//读取json的
private readonly IConfiguration _configuration;
public AuthenticateController(IConfiguration configuration)
{
_configuration = configuration;
}
//任何人都可以访问
[AllowAnonymous]
[HttpPost("login")]
public IActionResult Login([FromBody] LoginDto loginDto)
{
//1. 验证用户名密码
//2. 创建jwt
//header
var singingAlgorithm = SecurityAlgorithms.HmacSha256;
//payload
var claims = new[] {
//sub
new Claim(JwtRegisteredClaimNames.Sub,"fake_user_id")
};
//signiture
var secretByte = Encoding.UTF8.GetBytes(_configuration["Authentication:SecretKey"]);
var signingkey = new SymmetricSecurityKey(secretByte);
var singingCredentials = new SigningCredentials(signingkey,singingAlgorithm);
var token = new JwtSecurityToken(
issuer:_configuration["Authentication:Issuer"],
audience: _configuration["Authentication:Audience"],
claims,
notBefore:DateTime.UtcNow,
expires:DateTime.UtcNow.AddDays(1),
singingCredentials
);
//输出token字符串
var tokenStr = new JwtSecurityTokenHandler().WriteToken(token);
//3.返回200 OK +jwt
return Ok(tokenStr);
}
}
}
5. 在需要验证的控制器加上
[Authorize(AuthenticationSchemes = "Bearer")]
验证 jwt是否成功,在该控制的方法上请求看返回的结果是否成功、





 本文详细介绍了如何使用JWT(JSON Web Token)进行API认证和授权。首先,通过配置设置启用API认证,然后在appsettings.json中设置密钥。在控制器中创建登录接口,验证用户输入并生成JWT,最后在需要验证的控制器上添加授权标签 `[Authorize(AuthenticationSchemes = Bearer)]`,确保请求包含有效的JWT。
本文详细介绍了如何使用JWT(JSON Web Token)进行API认证和授权。首先,通过配置设置启用API认证,然后在appsettings.json中设置密钥。在控制器中创建登录接口,验证用户输入并生成JWT,最后在需要验证的控制器上添加授权标签 `[Authorize(AuthenticationSchemes = Bearer)]`,确保请求包含有效的JWT。
















 4607
4607

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








