漏洞列表
| 漏洞类型 | 复现 |
|---|---|
| 任意文件上传 | √ |
| 配置文件覆盖 | √ |
| 任意文件上传2 | √ |
| 跨站脚本漏洞 | √ |
| 任意文件删除 | √ |
| 任意文件下载 | √ |
| sql注入 | √ |
复现漏洞
任意文件上传1
漏洞成因
展示位置:
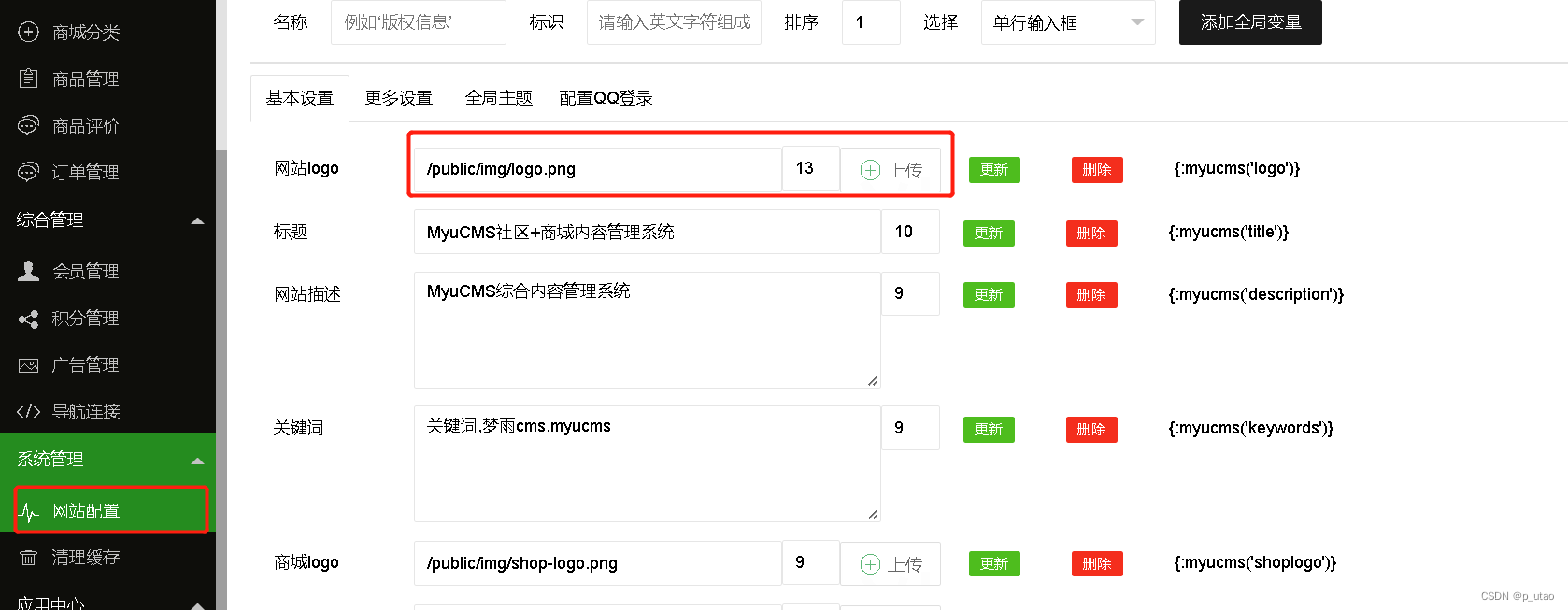
代码位置:
myucms-v2.1.1022\application\admin\controller\Upload.php
public function upfile()
{
if (!session('userid') || !session('username')) {
$this->error('亲!请登录',url('bbs/login/index'));
} else {
return json($this->model->upfile('files'));
}
}
这里会判断是否登录,没有登录会跳转到登录界面,登录则会调用model->upfile
public function upfile($type,$filename = 'file',$is_water = false){
if (config('web.qiniuopen') == 1) {
$driverConfig = array('secrectKey' => config('web.secrectKey'), 'accessKey' => config('web.accessKey'), 'domain' => config('web.domain'), 'bucket' => config('web.bucket'));
$setting = array('rootPath' => './', 'saveName' => array('uniqid', ''), 'hash' => true);
$setting['exts'] = explode(',', config('web.WEB_RXT'));
$setting['maxSize'] = 50 * 1024 * 1024;
$File = $_FILES['file'];
$Upload = new Upload($setting, 'Qiniu', $driverConfig);
$info = $Upload->uploadOne($File);
if ($info) {
$data['sha1'] = $info['sha1'];
$data['md5'] = $info['md5'];
$data['create_time'] = time();
$data['uid'] = session('userid');
$data['download'] = 0;
$data['size'] = $info['size'];
$data['name'] = $info['name'];
$data['ext'] = $info['ext'];
$data['savepath'] = $info['url'];
$data['savename'] = $info['savename'];
$data['mime'] = $info['type'];
$map['md5'] = $info['md5'];
$mmn = Db::name('file')->where($map)->find();
if (empty($mmn)) {
Db::name('file')->insert($data);
$res = Db::name('file')->getLastInsID();
if ($res > 0) {
return array('code' => 200, 'msg' => '上传成功', 'hasscore' => 0, 'ext' => $data['ext'], 'id' => $res, 'headpath' => $data['savepath'],'path' => $data['savepath'], 'md5' => $data['md5'], 'savename' => $data['savename'], 'filename' => $data['name'], 'info' => $info);
} else {
return array('code' => 0, 'msg' => '上传失败');
}
} else {
return array('code' => 200, 'msg' => '上传成功', 'hasscore' => 1, 'ext' => $mmn['ext'], 'id' => $mmn['id'], 'headpath' => $data['savepath'],'path' => $mmn['savepath'], 'md5' => $mmn['md5'], 'savename' => $mmn['savename'], 'filename' => $mmn['name'], 'info' => $mmn);
}
} else {
return array('code' => 0, 'msg' => $Upload->getError());
}
} else {
$file = request()->file($filename);
$md5 = $file->hash('md5');
$n = Db::name('file')->where('md5', $md5)->find();
if (empty($n)) {
$info = $file->validate(['size' => 50 * 1024 * 1024, 'ext' => config('web.WEB_RXT')])->move(ROOT_PATH . DS . 'uploads');
if ($info) {
$path = DS . 'uploads' . DS . $info->




 本文详细分析了一个名为myucms的CMS系统的多个安全漏洞,包括任意文件上传、配置文件覆盖、SQL注入、跨站脚本(XSS)和文件操作漏洞。通过复现这些漏洞,揭示了系统在文件验证、用户输入过滤和数据库交互等方面的安全缺陷,提醒开发者关注并加强系统安全防护。
本文详细分析了一个名为myucms的CMS系统的多个安全漏洞,包括任意文件上传、配置文件覆盖、SQL注入、跨站脚本(XSS)和文件操作漏洞。通过复现这些漏洞,揭示了系统在文件验证、用户输入过滤和数据库交互等方面的安全缺陷,提醒开发者关注并加强系统安全防护。
 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章

















 2432
2432


 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?







