CrackMe160-002
爆破思路
同001,从调用堆栈找到关键函数,进入
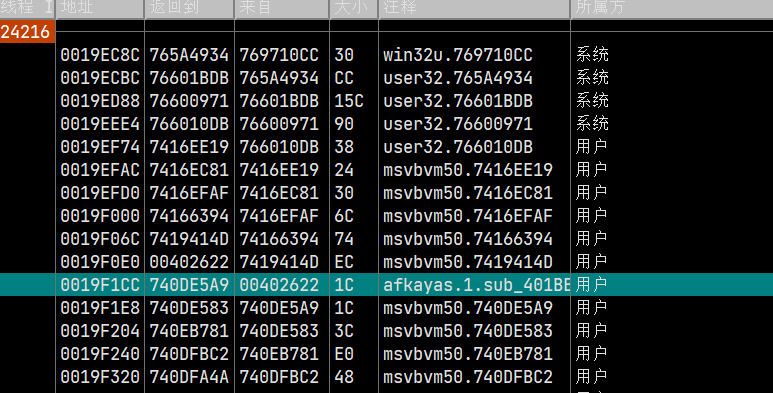
稍微向上翻一下即可看到字符串(字符串前面的L说明该字符串是由Unicode编码)
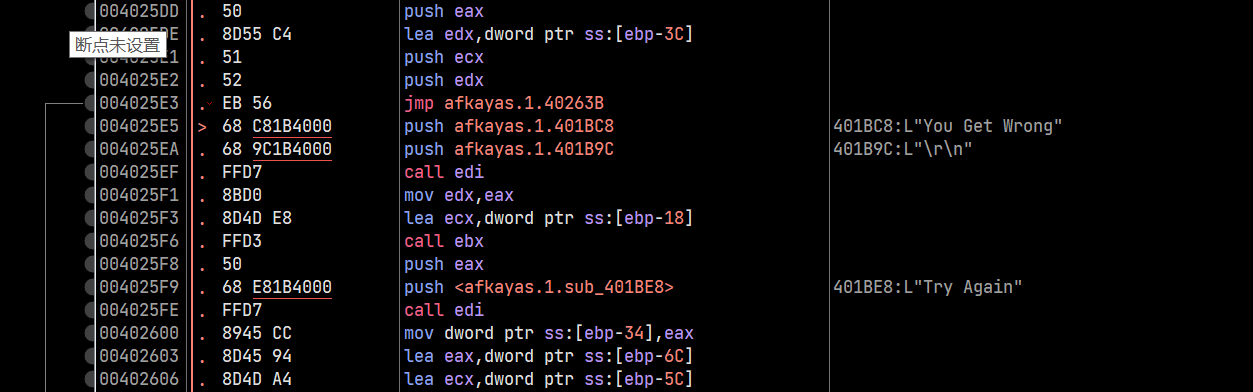
在转储中右键->十六进制->拓展ASCII 即可查看Unicode
有点偏题了。。那么按照001的思路这里可以同样的爆破,就不赘述了,把重头戏还是放在序列生成比较好
序列生成
老样子,这里断点打到判断之前,不过并没有发现类似cmp这样的指令,于是乎我考虑断点再段前面一些
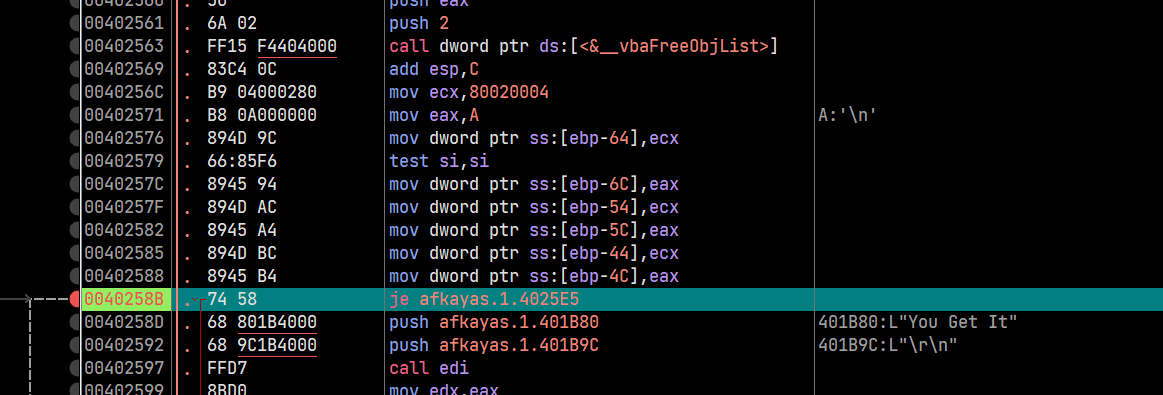
00402310 | 55 | push ebp |
00402311 | 8BEC | mov ebp,esp |
00402313 | 83EC 0C | sub esp,C |
00402316 | 68 26104000 | push <JMP.&__vbaExceptHandler> |
0040231B | 64:A1 00000000 | mov eax,dword ptr fs:[0] |
00402321 | 50 | push eax |
00402322 | 64:8925 00000000 | mov dword ptr fs:[0],esp |
00402329 | 81EC B0000000 | sub esp,B0 |
0040232F | 53 | push ebx |
00402330 | 56 | push esi |
00402331 | 8B75 08 | mov esi,dword ptr ss:[ebp+8] |
00402334 | 57 | push edi |
00402335 | 8BC6 | mov eax,esi |
00402337 | 83E6 FE | and esi,FFFFFFFE |
0040233A | 8965 F4 | mov dword ptr ss:[ebp-C],esp |
0040233D | 83E0 01 | and eax,1 |
00402340 | 8B1E | mov ebx,dword ptr ds:[esi] |
00402342 | C745 F8 08104000 | mov dword ptr ss:[ebp-8],afkayas.1.401008 |
00402349 | 56 | push esi |
0040234A | 8945 FC | mov dword ptr ss:[ebp-4],eax |
0040234D | 8975 08 | mov dword ptr ss:[ebp+8],esi |
00402350 | FF53 04 | call dword ptr ds:[ebx+4] |
00402353 | 8B83 10030000 | mov eax,dword ptr ds:[ebx+310] |
00402359 | 33FF | xor edi,edi |
0040235B | 56 | push esi |
0040235C | 897D E8 | mov dword ptr ss:[ebp-18],edi |
0040235F | 897D E4 | mov dword ptr ss:[ebp-1C],edi |
00402362 | 897D E0 | mov dword ptr ss:[ebp-20],edi |
00402365 | 897D DC | mov dword ptr ss:[ebp-24],edi |
00402368 | 897D D8 | mov dword ptr ss:[ebp-28],edi |
0040236B | 897D D4 | mov dword ptr ss:[ebp-2C],edi |
0040236E | 897D C4 | mov dword ptr ss:[ebp-3C],edi |
00402371 | 897D B4 | mov dword ptr ss:[ebp-4C],edi |
00402374 | 897D A4 | mov dword ptr ss:[ebp-5C],edi |
00402377 | 897D 94 | mov dword ptr ss:[ebp-6C],edi |
0040237A | 8985 40FFFFFF | mov dword ptr ss:[ebp-C0],eax |
00402380 | FFD0 | call eax |
00402382 | 8D4D D4 | lea





 博客详细分析了CrackMe160-002程序的序列生成过程,从汇编代码层面探讨了如何通过Name字段生成特定的序列,并解释了涉及的函数如vbaLenBstr、imul、rtcAnsiValueBstr和vbaStrI4的作用。最后,揭示了程序通过比较用户输入的Serial与生成序列来验证的逻辑。
博客详细分析了CrackMe160-002程序的序列生成过程,从汇编代码层面探讨了如何通过Name字段生成特定的序列,并解释了涉及的函数如vbaLenBstr、imul、rtcAnsiValueBstr和vbaStrI4的作用。最后,揭示了程序通过比较用户输入的Serial与生成序列来验证的逻辑。
 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章

















 234
234

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








