The Extensible Authentication Protocol (EAP) as defined in IETF RFC 2284 provides support for many authentication methods.EAP was originally adopted for use with PPP, since been redefined in IETF RFC 3748 for use with 802.1X port base access control. Below shows the EAP packet format.

There are 4 different type of EAP packets & identify by the “Code” octet of EAP header.
Code=1 Request
Code=2 Response
Code=3 Success
Code=4 Failure
Most of the time EAP messages are encapsulated in EAP over LAN(EAPOL) frames. There are 5 different major types of EAPOL messages
1. Type 0 – EAP Packets (encapsulated EAP frame)
2. Type 1 – EAPOL-Start (optional frame that supplicant can use to start EAP Proces)
3. Type 2 – EAPOL-Logoff (this frame terminate an EAP session & shut virtuall ports)
4. Type 3 – EAPOL-Key (used to exchange dynamic keying info,eg 4way-handshake)
5. Type 4 – EAPOL-Encapsulated-ASF-Alert (used to send alerts such as SNMP traps to virtual ports)
Below shows the generic EAP frame exchange (Page 140 of Official CWSP Study Guide)
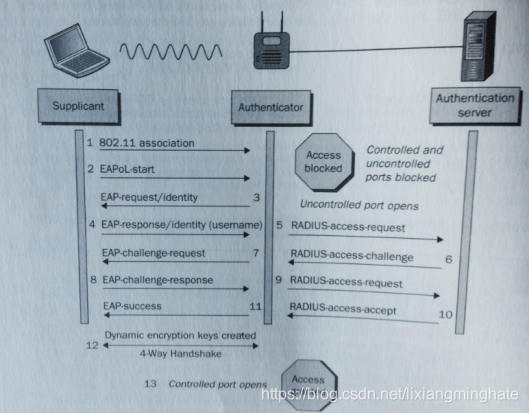
Authenticator maintains two virtual ports (uncontrolled & control port). When open “uncontrolled port” allows EAP authentication traffic to pass through. The control port blocks all other traffic until the supplicant has authenticated.When control port is open, upper layer (3-7) traffic can pass through. Here is the flow of frame exchange.
1. Supplicant associate with BSS, both controlled & uncontrolled ports are blocked on the authenticator.
2. Supplicant initiate the EAP process by sending EAPOL-Start frame (optional frame & may or may not be used by different type of EAP)
3. Authenticator send EAP-Request frame.
4. Supplicant send EAP-Response frame with identity in clear text. Then uncontrolled port open to allow EAP traffic through.
5. Authenticator encapsulate EAP response frame in RADIUS packet & forwards it to authentication server(AS).
6. AS looks at supplicant’s name & check again user database & then send a password challenge.
7. Authenticator send the password challenge to the supplicant in a EAP frame.
8. Supplicant send EAP-challenge response by hashing password using hash algorithm (like MS-CHAPv2)
9. Authenticator forwards the challenge response in a RADIUS packet to AS.
10. AS runs an identical hash & see if response is correct. AS will send “Success” or “Failure”
11. Authenticator forwards AS message to supplicant in “EAP-Success” frame or “EAP-Failure” frame.
12. 4-Way handshake (if EAP-Success) between Authenticator & Supplicant occurs
13. Once 4 way-handshake is completed, the controlled port is unblocked & supplicant is authorized to use network resources.
Here is a snapshot of a wireless frame capture when EAP authentication in uesd. You will see the EAP-Request(frame 113), EAP-Response (frame 115), EAP-Success (fram 157) which are type -0 EAP packets. Also you can see type-3 EAPOL-Key messages (frame 159,161,163 & 165)
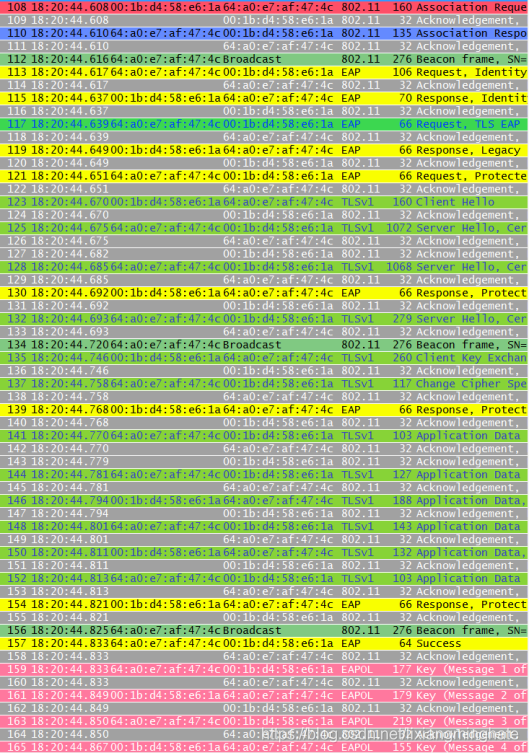
Here is some more details on different type of EAP packets in the above capture.
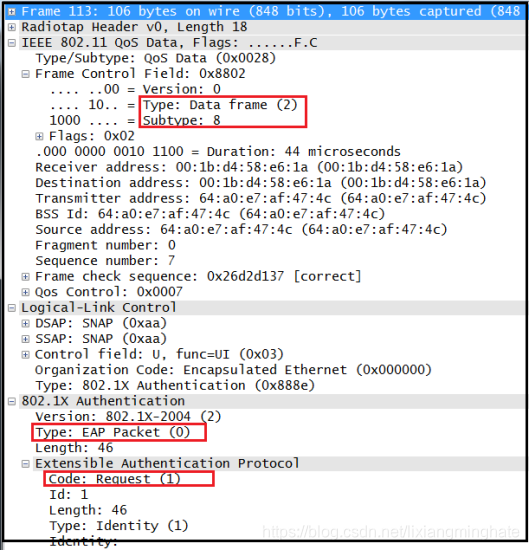
EAP-Request (frame 113 in the above).Note that Type 0 EAP packet type is “0” & Code is 1 (ie EAP-Request)
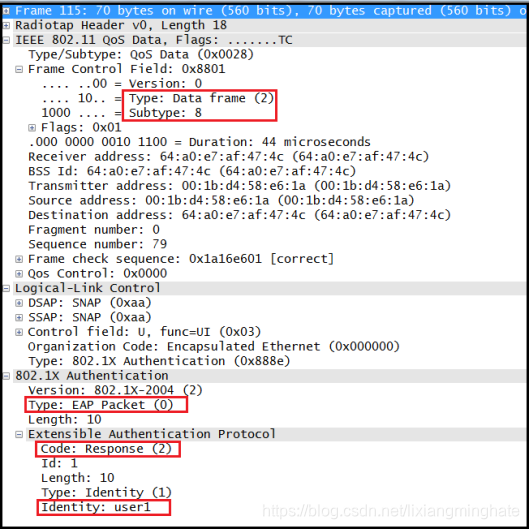
Here is an EAP-Response frame(115 in the above).Note that Type 0 EAP packet type is “0” & Code is 2 indicating it is a EAP-Reseponse frame. Also note the Identity is sent as cleartext (user1 in this capture).
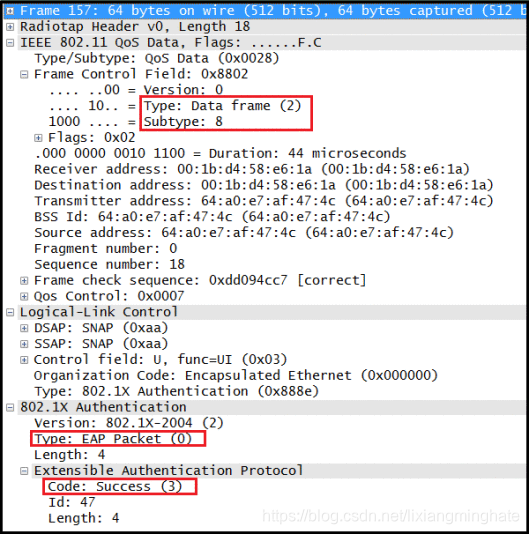
Here is the “EAP-Success” frame(no 157). Note that EAP packet type 0 indicating it is normal EAP frame & Code is set to 3 indicating it is a EAP-Success frame.
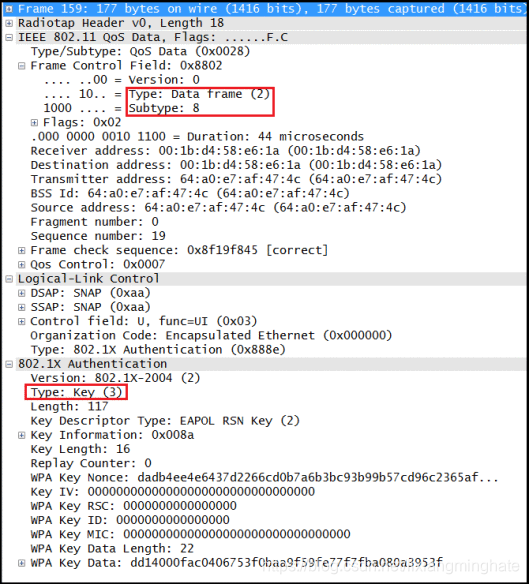
Here is an “EAPOL-Key” exchange frame (no 159). Note that EAP packet type 3 indicating it is a EAPOL-Key exchange frame.
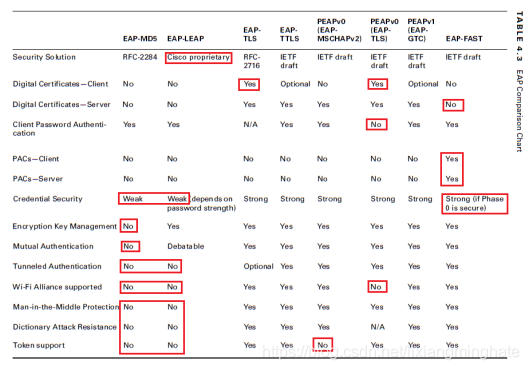
There are many different types of EAP authentication methods & some of them are less secure compare to others.As you saw abouve, supplicant identity sending as cleartext is security risk & some EAP methods use encrypted tunnel to make it more secure. Here are the different types of EAP
1. EAP-MD5 (weak)
2. EAP-LEAP (weak)
3. EAP-PEAP (2 phase tunneled)
4. EAP-TTLS (2 phase tunneled)
5. EAP-TLS (client & server side certs)
6. EAP-FAST (2 phase tunneled)
Here is a quick comparison of these EAP methods (page 157 of CWSP Study Guide)
Reference
1. CWSP Official Study Guide– CH4.
后记:
请注意这篇文章作者所描述的场景:如图二所示,无线网中存在Supplicant-Authenticator-Authenticator Server(Authenticator Server是单独的服务,没有集成在Authenticator中)。至少我在捕获无线数据包时没有发现EAPOL.type==0这类包




 本文深入解析了EAP(Extensible Authentication Protocol)的工作原理,包括其在802.1X和PPP中的应用,EAP包格式,以及与RADIUS、AS服务器的交互流程。文章还探讨了多种EAP认证方法的安全性比较。
本文深入解析了EAP(Extensible Authentication Protocol)的工作原理,包括其在802.1X和PPP中的应用,EAP包格式,以及与RADIUS、AS服务器的交互流程。文章还探讨了多种EAP认证方法的安全性比较。
















 637
637

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








