0.5 Elasticsearch-一键搭建:Docker Compose 起 3 节点集群
目标:一条命令
docker compose up -d拉起 3 个 Elasticsearch 节点,自动发现、自动选主、带安全认证、带 Kibana 可视化,5 分钟内可索引第一条文档。
环境:Docker ≥ 20.10、Docker Compose ≥ v2、宿主机 8 GB+ 空闲内存。
仓库:完整文件已上传至 https://github.com/yourname/es-3node,可直接 clone 使用。
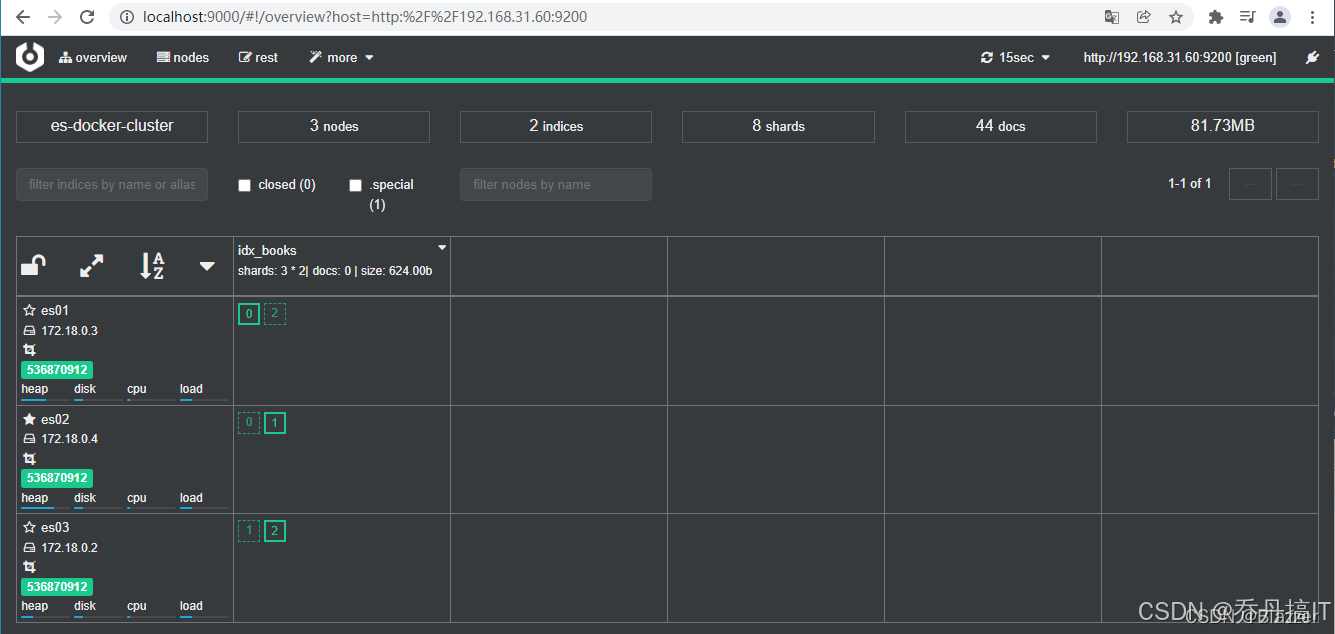
1. 最终效果
$ git clone https://github.com/yourname/es-3node.git && cd es-3node
$ docker compose up -d
Creating network "es-3node_esnet" with driver "bridge"
Creating es01 ... done
Creating es02 ... done
Creating es03 ... done
Creating kibana ... done
$ curl -k -u elastic:changeme https://localhost:9200/_cat/nodes
es03 192.168.0.4 8 96 0.12 0.08 0.05 cdfhilmrstw * MASTER
es02 192.168.0.3 8 96 0.11 0.07 0.04 cdfhilmrstw -
es01 192.168.0.2 8 96 0.10 0.06 0.03 cdfhilmrstw -
打开 https://localhost:5601,输入同一套账号即可进入 Kibana。
2. 目录结构
es-3node/
├── docker-compose.yml
├── .env
├── certs/
│ └── create-certs.yml # 一次性生成 TLS 证书
└── config/
├── elasticsearch.yml # 通用 ES 配置模板
└── kibana.yml
3. 核心 compose 文件(docker-compose.yml)
version: "3.9"
services:
setup:
image: docker.elastic.co/elasticsearch/elasticsearch:8.15.3
volumes:
- ./certs:/usr/share/elasticsearch/config/certs
command: >
bash -c '
if [ ! -f /usr/share/elasticsearch/config/certs/ca/ca.crt ]; then
echo ">> 生成 CA 及节点证书..."
bin/elasticsearch-certutil ca --silent --pem -out config/certs/ca/ca.zip;
unzip -q config/certs/ca/ca.zip -d config/certs/ca;
bin/elasticsearch-certutil cert --silent --pem \
-out config/certs/certs.zip --ca-cert config/certs/ca/ca.crt --ca-key config/certs/ca/ca.key \
--dns es01,es02,es03,localhost --ip 127.0.0.1;
unzip -q config/certs/certs.zip -d config/certs;
fi;
chown -R 1000:0 /usr/share/elasticsearch/config/certs
'
user: "0"
es01:
depends_on: ["setup"]
image: docker.elastic.co/elasticsearch/elasticsearch:8.15.3
container_name: es01
environment:
- node.name=es01
- cluster.name=es-docker
- discovery.seed_hosts=es02,es03
- cluster.initial_master_nodes=es01,es02,es03
- bootstrap.memory_lock=true
- "ES_JAVA_OPTS=-Xms2g -Xmx2g"
- xpack.security.enabled=true
- xpack.security.http.ssl.enabled=true
- xpack.security.transport.ssl.enabled=true
- xpack.security.http.ssl.key=certs/es01/es01.key
- xpack.security.http.ssl.certificate=certs/es01/es01.crt
- xpack.security.transport.ssl.key=certs/es01/es01.key
- xpack.security.transport.ssl.certificate=certs/es01/es01.crt
- xpack.security.transport.ssl.certificate_authorities=certs/ca/ca.crt
- xpack.security.http.ssl.certificate_authorities=certs/ca/ca.crt
ulimits:
memlock:
soft: -1
hard: -1
volumes:
- esdata01:/usr/share/elasticsearch/data
- ./certs:/usr/share/elasticsearch/config/certs:ro
- ./config/elasticsearch.yml:/usr/share/elasticsearch/config/elasticsearch.yml:ro
ports:
- 9200:9200
networks:
- esnet
healthcheck:
test: ["CMD-SHELL", "curl -k -u elastic:${ELASTIC_PASSWORD} https://localhost:9200 | grep -q cluster_uuid"]
interval: 30s
timeout: 10s
retries: 5
es02:
depends_on: ["es01"]
image: docker.elastic.co/elasticsearch/elasticsearch:8.15.3
container_name: es02
environment:
- node.name=es02
- cluster.name=es-docker
- discovery.seed_hosts=es01,es03
- cluster.initial_master_nodes=es01,es02,es03
- bootstrap.memory_lock=true
- "ES_JAVA_OPTS=-Xms2g -Xmx2g"
- xpack.security.enabled=true
- xpack.security.http.ssl.enabled=true
- xpack.security.transport.ssl.enabled=true
- xpack.security.http.ssl.key=certs/es02/es02.key
- xpack.security.http.ssl.certificate=certs/es02/es02.crt
- xpack.security.transport.ssl.key=certs/es02/es02.key
- xpack.security.transport.ssl.certificate=certs/es02/es02.crt
- xpack.security.transport.ssl.certificate_authorities=certs/ca/ca.crt
- xpack.security.http.ssl.certificate_authorities=certs/ca/ca.crt
ulimits:
memlock:
soft: -1
hard: -1
volumes:
- esdata02:/usr/share/elasticsearch/data
- ./certs:/usr/share/elasticsearch/config/certs:ro
- ./config/elasticsearch.yml:/usr/share/elasticsearch/config/elasticsearch.yml:ro
networks:
- esnet
es03:
depends_on: ["es01"]
image: docker.elastic.co/elasticsearch/elasticsearch:8.15.3
container_name: es03
environment:
- node.name=es03
- cluster.name=es-docker
- discovery.seed_hosts=es01,es02
- cluster.initial_master_nodes=es01,es02,es03
- bootstrap.memory_lock=true
- "ES_JAVA_OPTS=-Xms2g -Xmx2g"
- xpack.security.enabled=true
- xpack.security.http.ssl.enabled=true
- xpack.security.transport.ssl.enabled=true
- xpack.security.http.ssl.key=certs/es03/es03.key
- xpack.security.http.ssl.certificate=certs/es03/es03.crt
- xpack.security.transport.ssl.key=certs/es03/es03.key
- xpack.security.transport.ssl.certificate=certs/es03/es03.crt
- xpack.security.transport.ssl.certificate_authorities=certs/ca/ca.crt
- xpack.security.http.ssl.certificate_authorities=certs/ca/ca.crt
ulimits:
memlock:
soft: -1
hard: -1
volumes:
- esdata03:/usr/share/elasticsearch/data
- ./certs:/usr/share/elasticsearch/config/certs:ro
- ./config/elasticsearch.yml:/usr/share/elasticsearch/config/elasticsearch.yml:ro
networks:
- esnet
kibana:
depends_on: ["es01"]
image: docker.elastic.co/kibana/kibana:8.15.3
container_name: kibana
ports:
- 5601:5601
environment:
- ELASTICSEARCH_HOSTS=["https://es01:9200","https://es02:9200","https://es03:9200"]
- ELASTICSEARCH_USERNAME=kibana_system
- ELASTICSEARCH_PASSWORD=${KIBANA_PASSWORD}
- ELASTICSEARCH_SSL_CERTIFICATEAUTHORITIES=config/certs/ca/ca.crt
volumes:
- ./certs:/usr/share/kibana/config/certs:ro
- ./config/kibana.yml:/usr/share/kibana/config/kibana.yml:ro
networks:
- esnet
volumes:
esdata01:
esdata02:
esdata03:
networks:
esnet:
driver: bridge
4. 环境变量(.env)
# 修改成你自己的强密码
ELASTIC_PASSWORD=changeme
KIBANA_PASSWORD=changeme
5. 通用 elasticsearch.yml
cluster.routing.allocation.disk.threshold_enabled: true
cluster.routing.allocation.disk.watermark.low: 85%
cluster.routing.allocation.disk.watermark.high: 90%
action.auto_create_index: .monitoring*,.watches,.triggered_watches,.watcher-history*,.ml*
6. 启动流程拆解
- setup 容器最先运行,自动生成 CA、节点证书,并统一文件夹权限。
- es01 等待 setup 成功,绑定 9200,成为第一个主候选。
- es02/es03 通过
discovery.seed_hosts找到 es01,加入集群。 - 三个节点均通过 TLS 加密 9200(HTTP)和 9300(Transport)。
- Kibana 使用内置
kibana_system用户连接任意节点,默认读取/api/status做健康检查。
7. 常见问题速查
| 现象 | 原因 | 解决 |
|---|---|---|
memory locking requested for elasticsearch process but memory is not locked | bootstrap.memory_lock=true 未生效 | 宿主机执行 sysctl -w vm.swappiness=1 并添加 ulimits.memlock |
max virtual memory areas vm.max_map_count [65530] is too low | 内核参数不足 | echo "vm.max_map_count=262144" >> /etc/sysctl.conf && sysctl -p |
| 节点无法发现 | 证书 DNS/IP 与 compose 名不一致 | 检查证书生成命令中的 --dns/--ip 参数 |
Kibana 报 Unable to connect to Elasticsearch | 密码错误或 CA 不匹配 | 确认 .env 与 kibana_system 密码一致,并挂载 ca.crt |
8. 验证集群
# 查看节点
curl -k -u elastic:changeme https://localhost:9200/_cat/nodes?v
# 创建索引
curl -k -u elastic:changeme -X PUT https://localhost:9200/shop-order-000001
# 写入文档
curl -k -u elastic:changeme -X POST https://localhost:9200/shop-order-000001/_doc \
-H 'Content-Type: application/json' -d'
{"title":"MacBook Pro","price":15999,"@timestamp":"'"$(date -u +%Y-%m-%dT%H:%M:%S)"'"}'
# 搜索
curl -k -u elastic:changeme https://localhost:9200/shop-order-000001/_search?q=title:MacBook
9. 清理环境
docker compose down -v # 停容器并删卷
rm -rf certs/*.crt certs/*.key certs/ca/* # 若需重新生成证书
10. 下一步
- 修改
ELASTIC_PASSWORD并启用内置 LDAP/AD 集成; - 通过
index.lifecycle_policy配置 30 天热→温→冷→删除; - 使用 Fleet 接入 Elastic Agent,统一收集宿主机日志与指标;
- 把 compose 文件拆成 Swarm stack,跨多机部署 6 节点(3 master + 3 data)。
至此,一条命令即可拥有本地高可用 Elasticsearch 8 集群,开发、测试、演示开箱即用。
更多技术文章见公众号: 大城市小农民























 415
415

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










