简介
你问我Js逆向是什么?请看:👇👇👇
分析
网站:aHR0cHM6Ly9tYXRjaC55dWFucmVueHVlLmNvbS9tYXRjaC8x(base64解密)
-
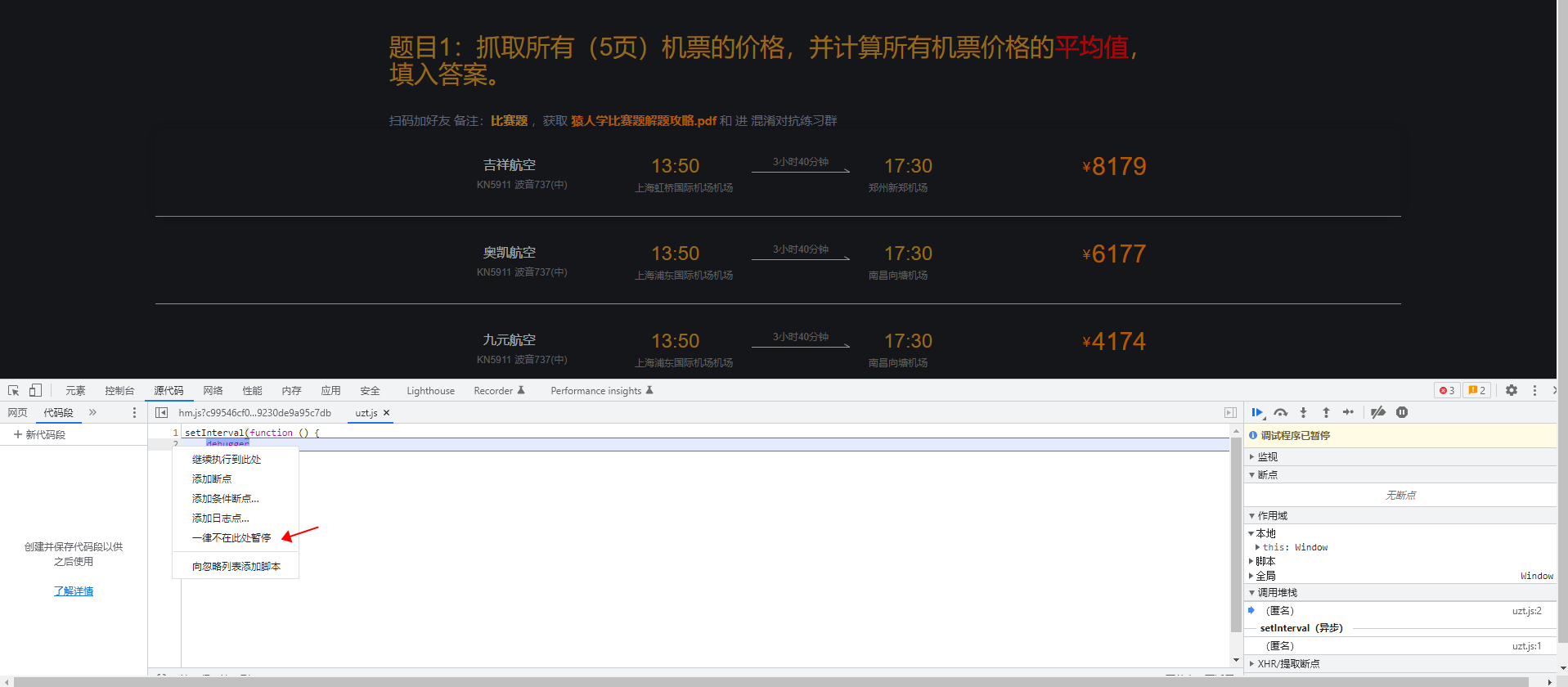
打开调式,发现弹出无限Debug,有几种跳过方法就不过多说明,我这里采用最简单的方法直接在debug行号下右键,点击不在此处暂停,就能跳过debug
-
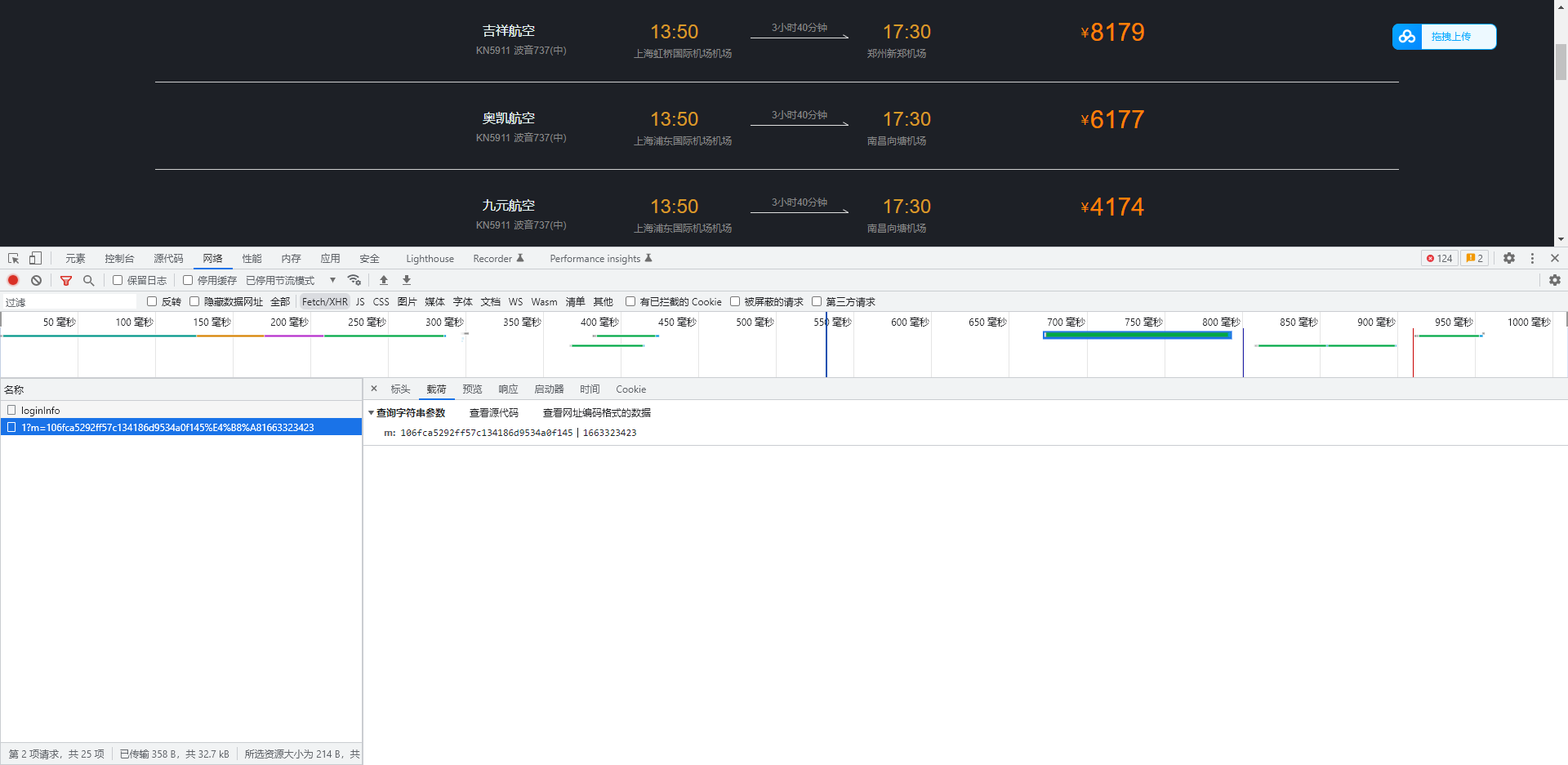
跳过之后刷新一下页面,找到数据接口,有一个m参数,毫无疑问,我们需要逆向的就是它了
-
全局搜索m,可惜找不到,从题目标题大概可以确定代码都混淆过了
-
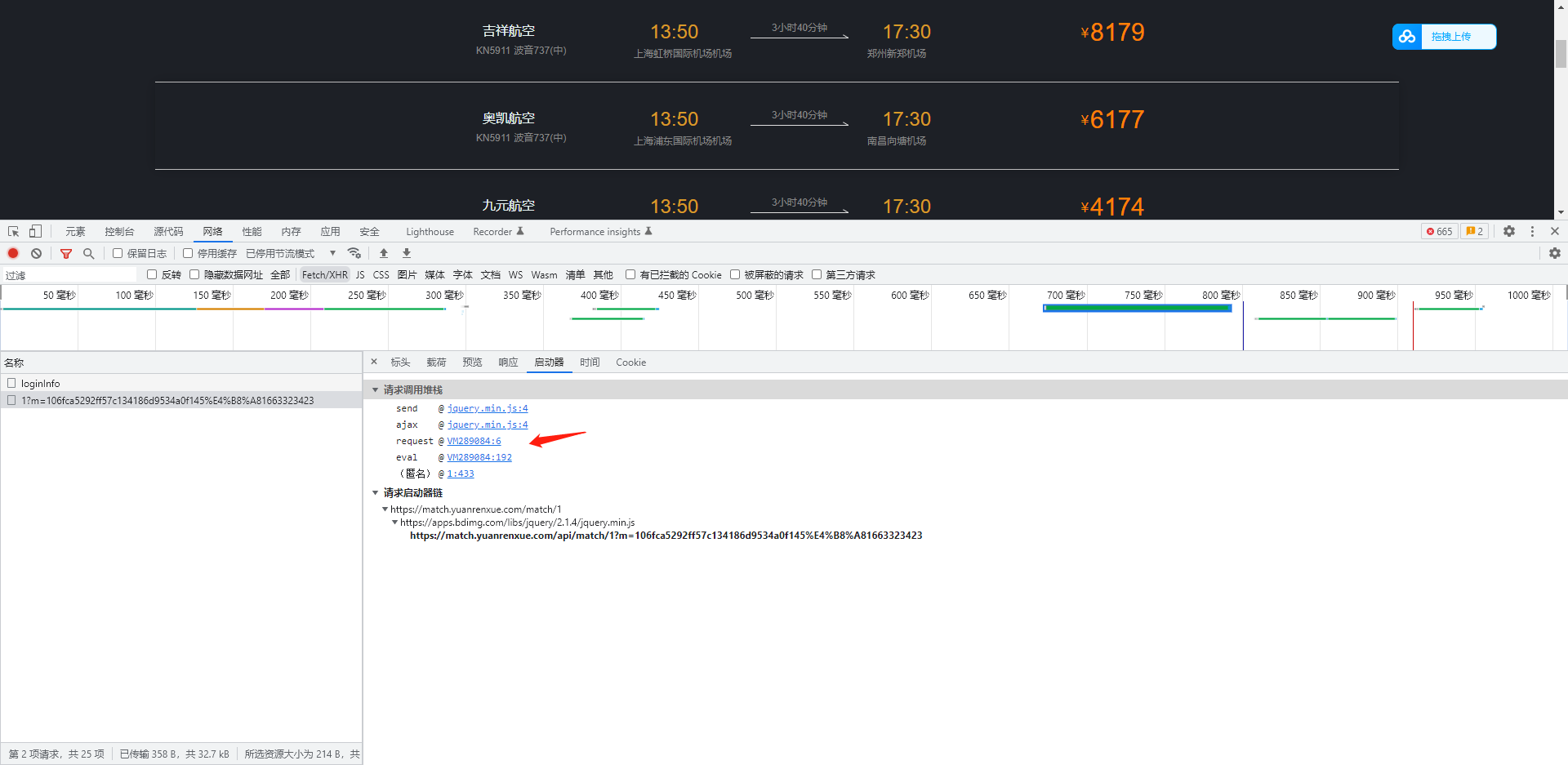
我们直接在启动堆栈里面找调用的js,前两个都是jquery,所以我们直接从第三个开始入手
-
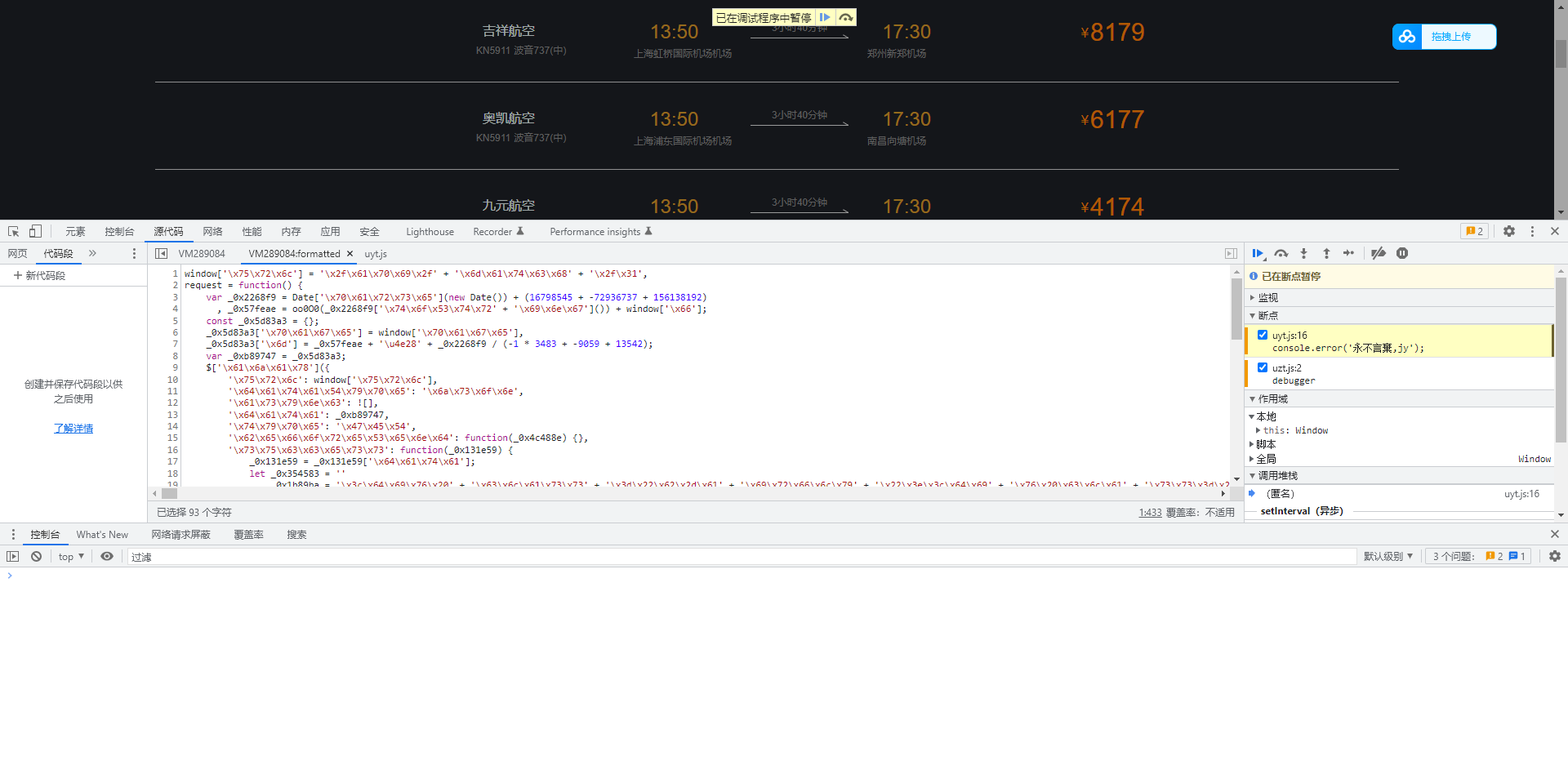
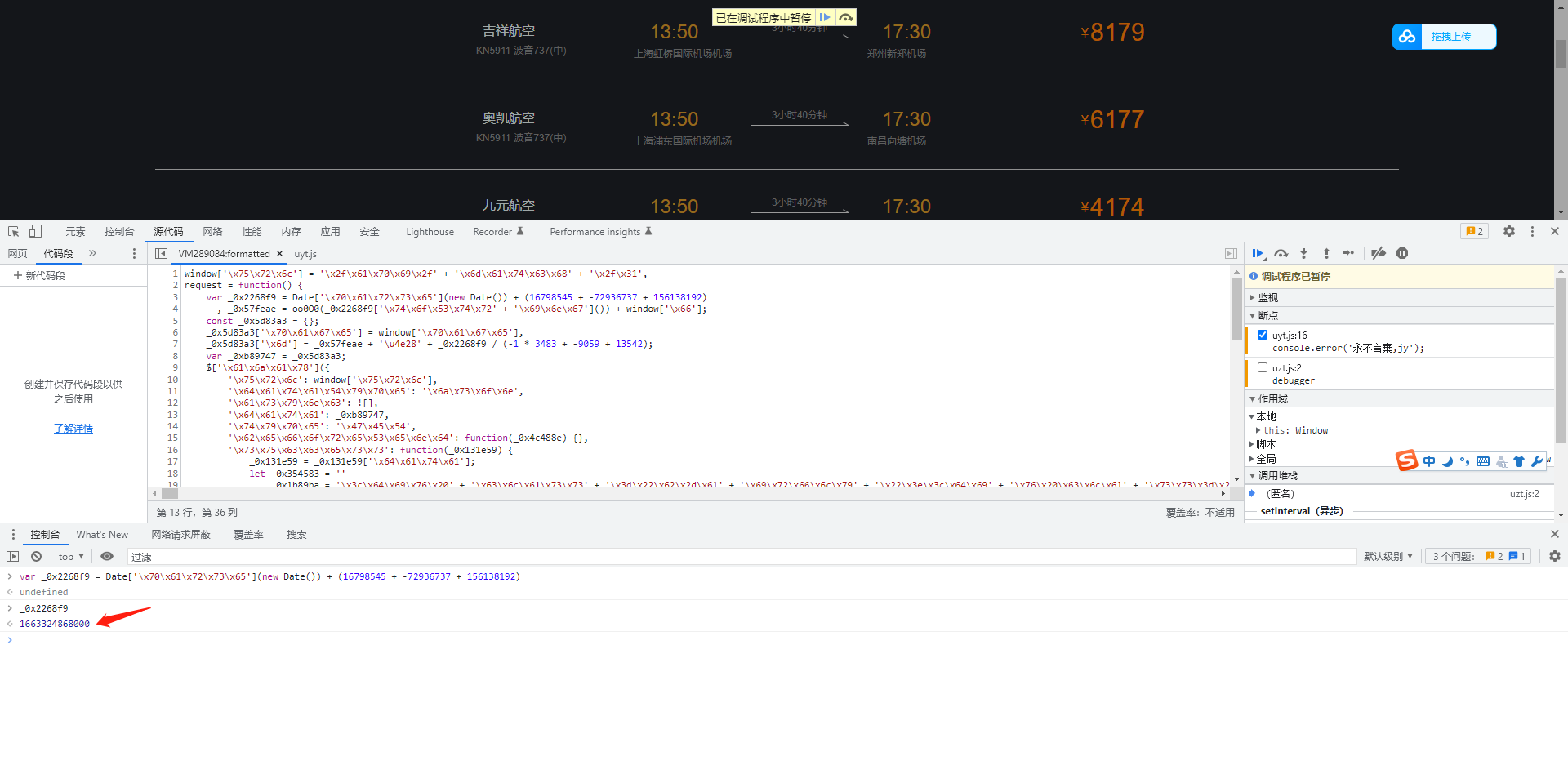
确实是混淆,我们在控制台打印一下_0x2268f9,看看这是个啥玩意
-
打开控制台,又一个debug,老样子行号右键,一律跳过!

-
跳过之后,继续打印,结果是一个时间戳
-
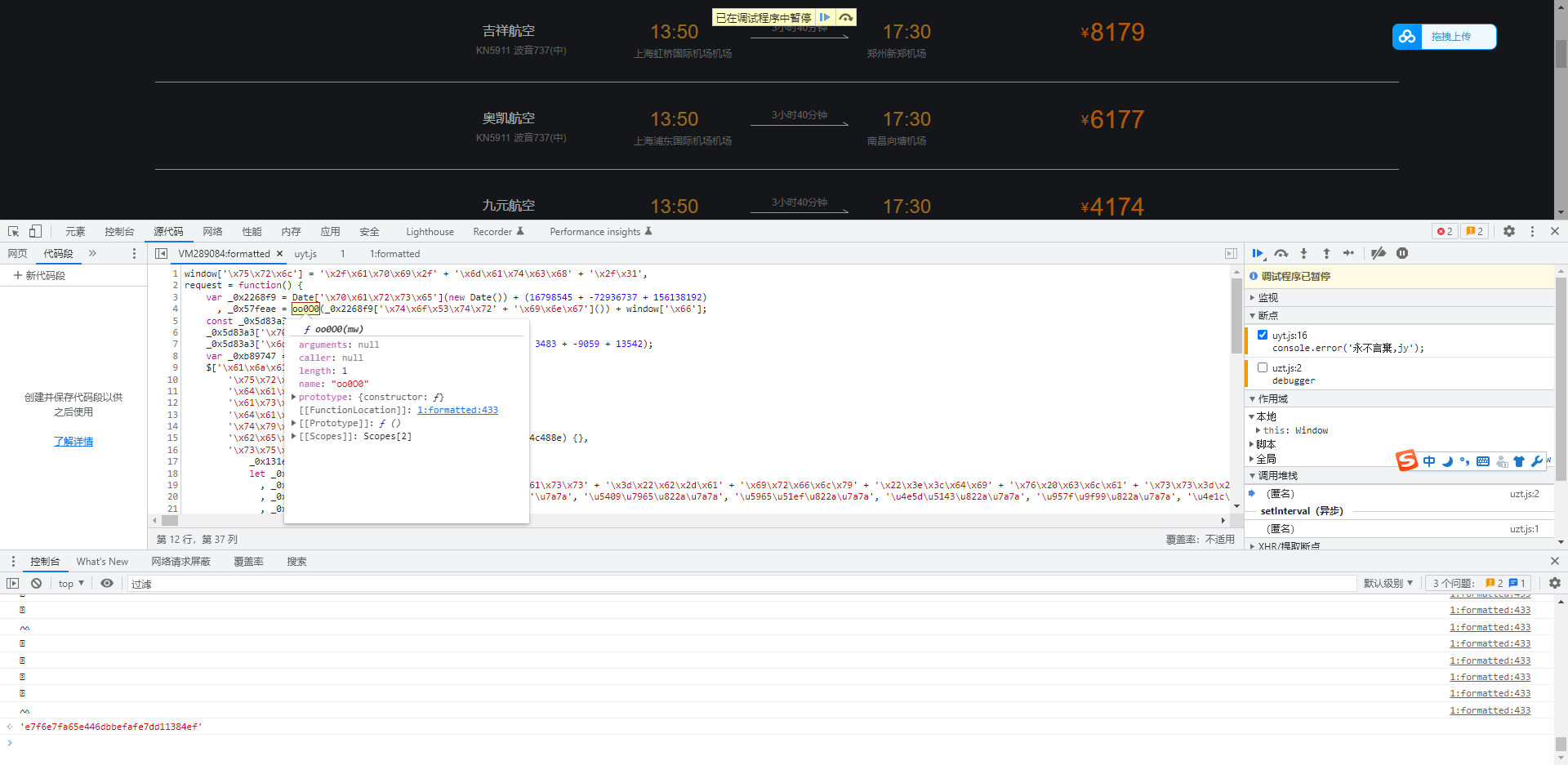
再往下看_0x57feae,里面调用了oo0O0函数,点进去看看
-
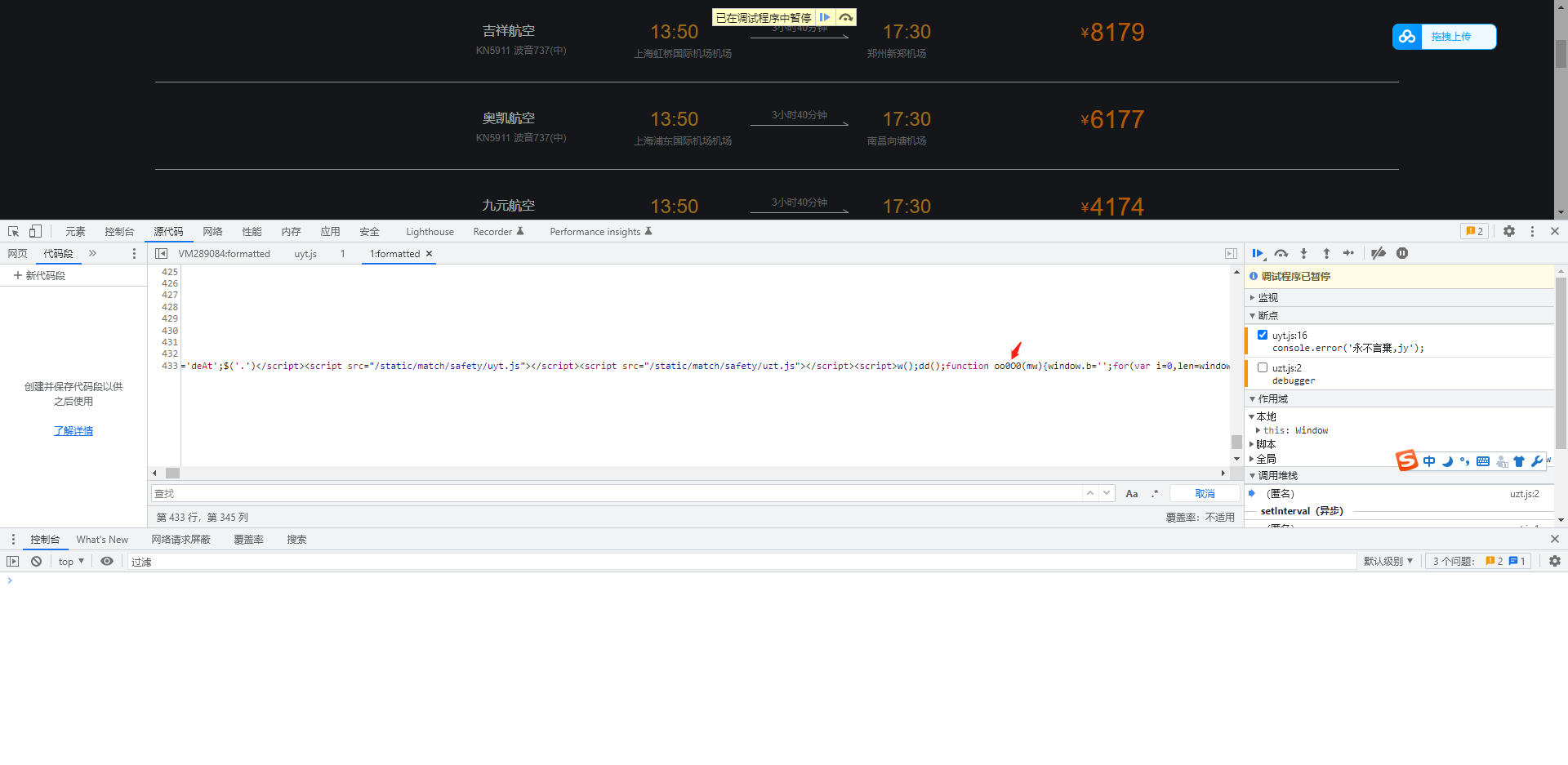
找到oo0O0函数,代码无法格式化,利用格式化工具美化一下
-
继续往下看,打印所有参数,发现_0x5d83a3[‘\x6d’]和M参数很接近,会不会就是要破解的M呢?

扣代码(心态崩)
激动的心颤抖的手,看到代码就全身发抖
接下来就是最最最关键的扣代码环节,也是很关键的部分,要是扣不好,前面白费功夫
-
上面已经找到oo0O0函数,经过美化,我们得到:
function oo0O0(mw) { window.b = ''; for (var i = 0, len = window.a.length; i < len; i++) { console.log(window.a[i]); window.b += String[document.e + document.g](window.a[i][document.f + document.h]() - i - window.c) } var U = ['W5r5W6VdIHZcT8kU', 'WQ8CWRaxWQirAW==']; var J = function(o, E) { o = o - 0x0; var N = U[o]; if (J['bSSGte'] === undefined) { var Y = function(w) { var m = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789+/=', T = String(w)['replace'](/=+$/, ''); var A = ''; for (var C = 0x0, b, W, l = 0x0; W = T['charAt'](l++);~W && (b = C % 0x4 ? b * 0x40 + W: W, C++%0x4) ? A += String['fromCharCode'](0xff & b >> ( - 0x2 * C & 0x6)) : 0x0) { W = m['indexOf'](W) } return A }; var t = function(w, m) { var T = [], A = 0x0, C, b = '', W = ''; w = Y(w); for (var R = 0x0, v = w['length']; R < v; R++) { W += '%' + ('00' + w['charCodeAt'](R)['toString'](0x10))['slice']( - 0x2) } w = decodeURIComponent(W); var l; for (l = 0x0; l < 0x100; l++) { T[l] = l } for (l = 0x0; l < 0x100; l++) { A = (A + T[l] + m['charCodeAt'](l % m['length'])) % 0x100, C = T[l], T[l] = T[A], T[A] = C } l = 0x0, A = 0x0; for (var L = 0x0; L < w['length']; L++) { l = (l + 0x1) % 0x100, A = (A + T[l]) % 0x100, C = T[l], T[l] = T[A], T[A] = C, b += String['fromCharCode'](w['charCodeAt'](L) ^ T[(T[l] + T[A]) % 0x100]) } return b }; J['luAabU'] = t, J['qlVPZg'] = {}, J['bSSGte'] = !![] } var H = J['qlVPZg'][o]; return H === undefined ? (J['TUDBIJ'] === undefined && (J['TUDBIJ'] = ![外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-Fq8jfiHN-1663230232374)(N, E)], J['qlVPZg'][o] = N) : N = H, N }; eval(atob(window['b'])[J('0x0', ']dQW')](J('0x1', 'GTu!'), '\x27' + mw + '\x27')); return '' } -
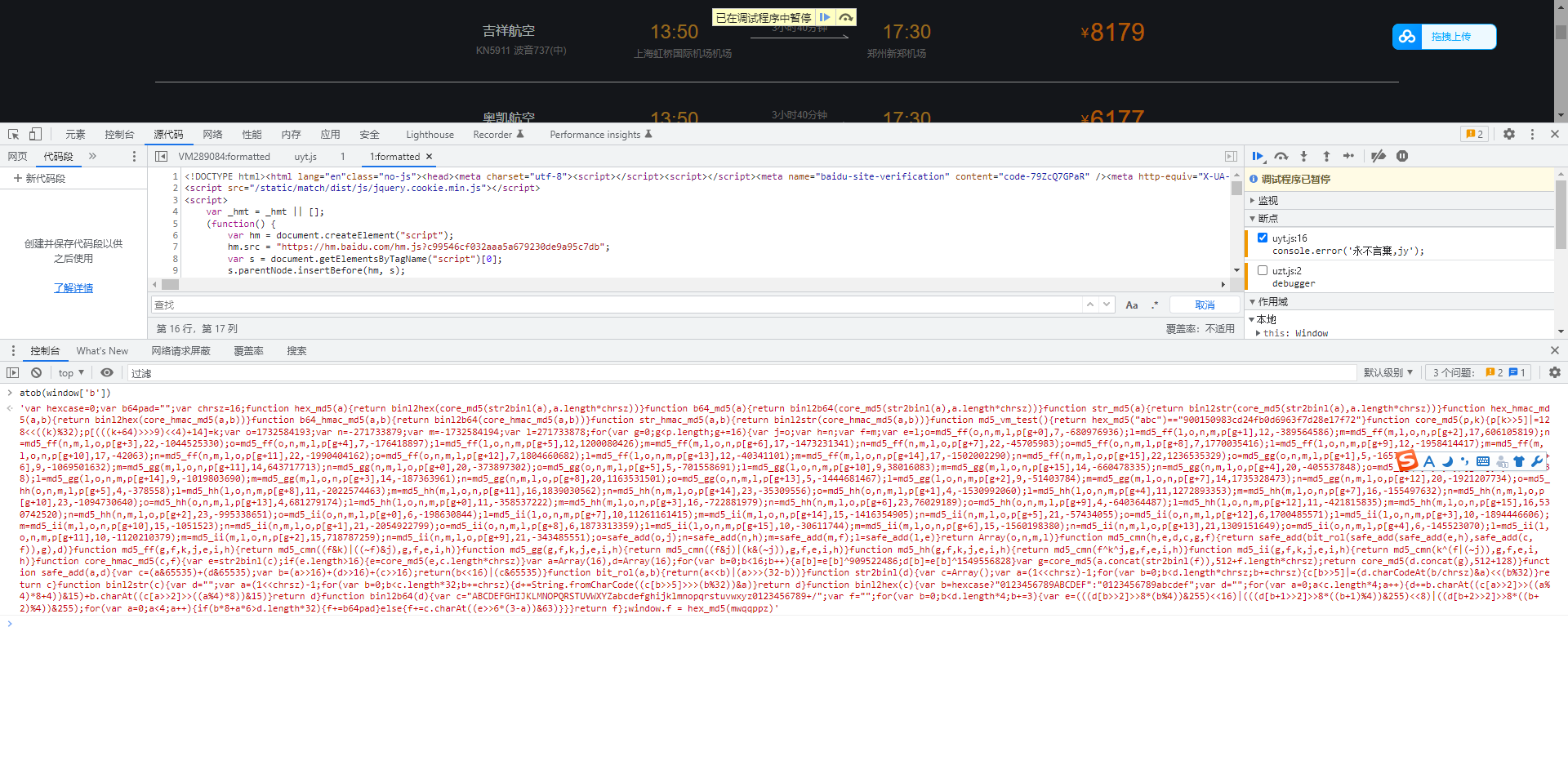
执行报错,atob未定义,控制台打印一下
-
确定是MD5加密,到这步就简单了,美化一下代码
var hexcase = 0; var b64pad = ""; var chrsz = 16; function hex_md5(a) { return binl2hex(core_md5(str2binl(a), a.length * chrsz)) } function b64_md5(a) { return binl2b64(core_md5(str2binl(a), a.length * chrsz)) } function str_md5(a) { return binl2str(core_md5(str2binl(a), a.length * chrsz)) } function hex_hmac_md5(a, b) { return binl2hex(core_hmac_md5(a, b)) } function b64_hmac_md5(a, b) { return binl2b64(core_hmac_md5(a, b)) } function str_hmac_md5(a, b) { return binl2str(core_hmac_md5(a, b)) } function md5_vm_test() { return hex_md5("abc") == "900150983cd24fb0d6963f7d28e17f72" } function core_md5(p, k) { p[k >> 5] |= 128 << ((k) % 32); p[(((k + 64) >>> 9) << 4) + 14] = k; var o = 1732584193; var n = -271733879; var m = -1732584194; var l = 271733878; for (var g = 0; g < p.length; g += 16) { var j = o; var h = n; var f = m; var e = l; o = md5_ff(o, n, m, l, p[g + 0], 7, -680976936); l = md5_ff(l, o, n, m, p[g + 1], 12, -389564586); m = md5_ff(m, l, o, n, p[g + 2], 17, 606105819); n = md5_ff(n, m, l, o, p[g + 3], 22, -1044525330); o = md5_ff(o, n, m, l, p[g + 4], 7, -176418897); l = md5_ff(l, o, n, m, p[g + 5], 12, 1200080426); m = md5_ff(m, l, o, n, p[g + 6], 17, -1473231341); n = md5_ff(n, m, l, o, p[g + 7], 22, -45705983); o = md5_ff(o, n, m, l, p[g + 8], 7, 1770035416); l = md5_ff(l, o, n, m, p[g + 9], 12, -1958414417); m = md5_ff(m, l, o, n, p[g + 10], 17, -42063); n = md5_ff(n, m, l, o, p[g + 11], 22, -1990404162); o = md5_ff(o, n, m, l, p[g + 12], 7, 1804660682); l = md5_ff(l, o, n, m, p[g + 13], 12, -40341101); m = md5_ff(m, l, o, n, p[g + 14], 17, -1502002290); n = md5_ff(n, m, l, o, p[g + 15], 22, 1236535329); o = md5_gg(o, n, m, l, p[g + 1], 5, -165796510); l = md5_gg(l, o, n, m, p[g + 6], 9, -1069501632); m = md5_gg(m, l, o, n, p[g + 11], 14, 643717713); n = md5_gg(n, m, l, o, p[g + 0], 20, -373897302); o = md5_gg(o, n, m, l, p[g + 5], 5, -701558691); l = md5_gg(l, o, n, m, p[g + 10], 9, 38016083); m = md5_gg(m, l, o, n, p[g + 15], 14, -660478335); n = md5_gg(n, m, l, o, p[g + 4], 20, -405537848); o = md5_gg(o, n, m, l, p[g + 9], 5, 568446438); l = md5_gg(l, o, n, m, p[g + 14], 9, -1019803690); m = md5_gg(m, l, o, n, p[g + 3], 14, -187363961); n = md5_gg(n, m, l, o, p[g + 8], 20, 1163531501); o = md5_gg(o, n, m, l, p[g + 13], 5, -1444681467); l = md5_gg(l, o, n, m, p[g + 2], 9, -51403784); m = md5_gg(m, l, o, n, p[g + 7], 14, 1735328473); n = md5_gg(n, m, l, o, p[g + 12], 20, -1921207734); o = md5_hh(o, n, m, l, p[g + 5], 4, -378558); l = md5_hh(l, o, n, m, p[g + 8], 11, -2022574463); m = md5_hh(m, l, o, n, p[g + 11], 16, 1839030562); n = md5_hh(n, m, l, o, p[g + 14], 23, -35309556); o = md5_hh(o, n, m, l, p[g + 1], 4, -1530992060); l = md5_hh(l, o, n, m, p[g + 4], 11, 1272893353); m = md5_hh(m, l, o, n, p[g + 7], 16, -155497632); n = md5_hh(n, m, l, o, p[g + 10], 23, -1094730640); o = md5_hh(o, n, m, l, p[g + 13], 4, 681279174); l = md5_hh(l, o, n, m, p[g + 0], 11, -358537222); m = md5_hh(m, l, o, n, p[g + 3], 16, -722881979); n = md5_hh(n, m, l, o, p[g + 6], 23, 76029189); o = md5_hh(o, n, m, l, p[g + 9], 4, -640364487); l = md5_hh(l, o, n, m, p[g + 12], 11, -421815835); m = md5_hh(m, l, o, n, p[g + 15], 16, 530742520); n = md5_hh(n, m, l, o, p[g + 2], 23, -995338651); o = md5_ii(o, n, m, l, p[g + 0], 6, -198630844); l = md5_ii(l, o, n, m, p[g + 7], 10, 11261161415); m = md5_ii(m, l, o, n, p[g + 14], 15, -1416354905); n = md5_ii(n, m, l, o, p[g + 5], 21, -57434055); o = md5_ii(o, n, m, l, p[g + 12], 6, 1700485571); l = md5_ii(l, o, n, m, p[g + 3], 10, -1894446606); m = md5_ii(m, l, o, n, p[g + 10], 15, -1051523); n = md5_ii(n, m, l, o, p[g + 1], 21, -2054922799); o = md5_ii(o, n, m, l, p[g + 8], 6, 1873313359); l = md5_ii(l, o, n, m, p[g + 15], 10, -30611744); m = md5_ii(m, l, o, n, p[g + 6], 15, -1560198380); n = md5_ii(n, m, l, o, p[g + 13], 21, 1309151649); o = md5_ii(o, n, m, l, p[g + 4], 6, -145523070); l = md5_ii(l, o, n, m, p[g + 11], 10, -1120210379); m = md5_ii(m, l, o, n, p[g + 2], 15, 718787259); n = md5_ii(n, m, l, o, p[g + 9], 21, -343485551); o = safe_add(o, j); n = safe_add(n, h); m = safe_add(m, f); l = safe_add(l, e) } return Array(o, n, m, l) } function md5_cmn(h, e, d, c, g, f) { return safe_add(bit_rol(safe_add(safe_add(e, h), safe_add(c, f)), g), d) } function md5_ff(g, f, k, j, e, i, h) { return md5_cmn((f & k) | ((~f) & j), g, f, e, i, h) } function md5_gg(g, f, k, j, e, i, h) { return md5_cmn((f & j) | (k & (~j)), g, f, e, i, h) } function md5_hh(g, f, k, j, e, i, h) { return md5_cmn(f ^ k ^ j, g, f, e, i, h) } function md5_ii(g, f, k, j, e, i, h) { return md5_cmn(k ^ (f | (~j)), g, f, e, i, h) } function core_hmac_md5(c, f) { var e = str2binl(c); if (e.length > 16) { e = core_md5(e, c.length * chrsz) } var a = Array(16), d = Array(16); for (var b = 0; b < 16; b++) { a[b] = e[b] ^ 909522486; d[b] = e[b] ^ 1549556828 } var g = core_md5(a.concat(str2binl(f)), 512 + f.length * chrsz); return core_md5(d.concat(g), 512 + 128) } function safe_add(a, d) { var c = (a & 65535) + (d & 65535); var b = (a >> 16) + (d >> 16) + (c >> 16); return (b << 16) | (c & 65535) } function bit_rol(a, b) { return (a << b) | (a >>> (32 - b)) } function str2binl(d) { var c = Array(); var a = (1 << chrsz) - 1; for (var b = 0; b < d.length * chrsz; b += chrsz) { c[b >> 5] |= (d.charCodeAt(b / chrsz) & a) << (b % 32) } return c } function binl2str(c) { var d = ""; var a = (1 << chrsz) - 1; for (var b = 0; b < c.length * 32; b += chrsz) { d += String.fromCharCode((c[b >> 5] >>> (b % 32)) & a) } return d } function binl2hex(c) { var b = hexcase ? "0123456789ABCDEF": "0123456789abcdef"; var d = ""; for (var a = 0; a < c.length * 4; a++) { d += b.charAt((c[a >> 2] >> ((a % 4) * 8 + 4)) & 15) + b.charAt((c[a >> 2] >> ((a % 4) * 8)) & 15) } return d } function binl2b64(d) { var c = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"; var f = ""; for (var b = 0; b < d.length * 4; b += 3) { var e = (((d[b >> 2] >> 8 * (b % 4)) & 255) << 16) | (((d[b + 1 >> 2] >> 8 * ((b + 1) % 4)) & 255) << 8) | ((d[b + 2 >> 2] >> 8 * ((b + 2) % 4)) & 255); for (var a = 0; a < 4; a++) { if (b * 8 + a * 6 > d.length * 32) { f += b64pad } else { f += c.charAt((e >> 6 * (3 - a)) & 63) } } } return f }; window.f = hex_md5(mwqqppz) -
很容易理解,这里就是把 mwqqppz 替换成了 mw, 通过eval执行hex_md5(mw), 最后赋值给 window.f
-
我们将window.f 稍微改一下,就能得到m了
function get_param(ts){ var timestamp = parseInt(ts) var mwqqppz = timestamp + 100000000 var m = hex_md5(mwqqppz.toString()) + '丨' + mwqqppz / 1000; return m }
成果
-
成功获取m参数,对比网页一致
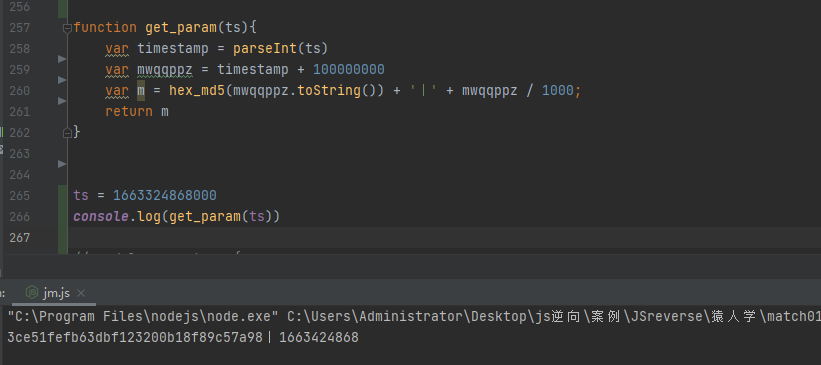
-
py中导入execjs运行Js文件
pip install execjs
import requests import time import execjs def get_param(): ts = str(int(time.time())) + "000" with open('jm.js','r',encoding='utf8') as f: js = f.read() param = execjs.compile(js).call('get_param',ts) # response = requests.get(url=self.jm_url, params=params) # param = response.text print(param) return param -
请求接口,获取数据
def get_data(page, param): headers = { "User-Agent": "yuanrenxue.project", } params = { "page": page, "m": param, } response = requests.get(url=self.base_url, params=params, headers=headers).json() if response["status"] == "1": data = response["data"] values = [i["value"] for i in data] print(values) return values -
计算结果,得到平均数
import numpy as np #导入numpy计算 mean def mean(): value = [] for i in range(1, 6): param = get_param() value = get_data(page=i, param=param) value.append(value) result = np.mean(total_value) print(result)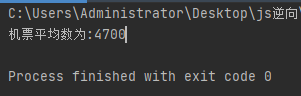
点关注不迷路,本文若对你有帮助,烦请三连支持一下 ❤️❤️❤️
各位的支持和认可就是我最大的动力❤️❤️❤️








 本文讲述了如何逆向分析并解开JavaScript混淆代码,通过逐步排查,发现并修复atob未定义问题,最终成功获取加密后的M参数。涉及MD5加密和代码美化过程。
本文讲述了如何逆向分析并解开JavaScript混淆代码,通过逐步排查,发现并修复atob未定义问题,最终成功获取加密后的M参数。涉及MD5加密和代码美化过程。


















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








