houseoforange_hitcon_2016
先检查保护

保护全开
FSOP:对于_IO_FILE_plus结构体的利用
首先,在分析这个题目之前,我们需要知道两个知识点,一个是_IO_FILE_plus,一个是FSOP
_IO_FILE_PLUS
_IO_FILE_plus是ptmalloc中定义的一种结构体,他决定了很多东西,先在gdb里面查看一眼

在此,我们就用本次题目中会使用到的_IO_list_all结构体来作为参考。
_IO_FILE_plus 主要是由两个部分组成,其中一个是_IO_FILE,另外一个是vtable。
_ I O _ F I L E _ p l u s = _ I O _ F I L E + v t a b l e \_IO\_FILE\_plus = \_IO\_FILE + vtable _IO_FILE_plus=_IO_FILE+vtable
_IO_FILE
_IO_FILE里面存了很多东西,这里有很多利用方式,比如说,
将_FLAGS = 0xfdab2887(或者说其他的值也行)
程序会将_IO_write_base = 0x80 以及 _IO_write_ptr之间的值打印出来
假设将_IO_write_base = 0x80 _IO_write_ptr = 0xa0 就会将把下图之中1到0xfffffffffff之间的值打印出来。
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-oXYTUqa3-1649341524268)(F:\MarkDownS\HEAP\houseoforange_hitcon_2016\houseoforange_hitcon_2016\微信图片_20210925003541.png)]](https://i-blog.csdnimg.cn/blog_migrate/6068b7f432f90364243d7453c322e1ca.png)
这是一种暂时与本题无关的泄露方式。
看回本题,
在_IO_FILE之中, _ chain是用来存储下一个_IO_FILE_PLUS指针的值,在malloc之中,如果产生错误,就会利用这一特性调用,最终来到 _IO_flush_all_lookup处,这个地方是用来打印错误信息的。这个地方有漏洞,对于_IO_FILE_PLUS结构体
-
_mode == 0 -
_IO_vtable_offset == 0 -
_IO_write_ptr > _IO_write_base当满足以上条件的时候,会调用 _IO_OVERFLOW函数,并且将_chain里面那个结构体作为第一个函数传入,
所以我们的利用思路,就是将**_IO_OVERFLOW**函数修改为system,将结构体的第一个位置改为"/bin/sh"这样的话就能getshell
vtable
vtable也是一个结构体

对于前文提到的_overflow就在这个地方(当然只是个人感觉)
所以这个也比较明确了,就是将vtable这一段修改为system。
函数分析
main()


add()
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-cL9nNZZX-1649341524274)(F:\MarkDownS\HEAP\houseoforange_hitcon_2016\houseoforange_hitcon_2016\image-20220406221655886.png)]](https://i-blog.csdnimg.cn/blog_migrate/a3266b67f629d202a74e46a5fe1e08be.png)
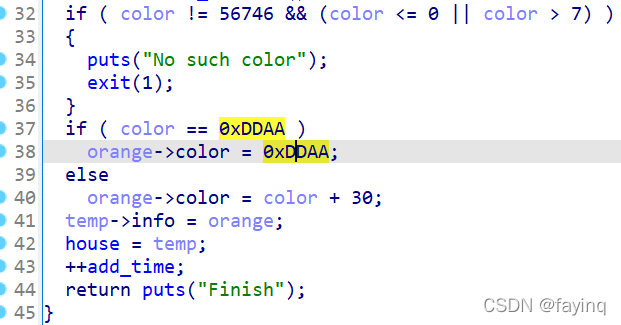
先看add函数,add函数一共malloc了3个chunk两个0x20,一个大小是自己malloc出来的。
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-9plYpU8e-1649341524275)(F:\MarkDownS\HEAP\houseoforange_hitcon_2016\houseoforange_hitcon_2016\image-20220406230140404.png)]
第一个是存了两个地址,也就是下面的两个chunk地址,
第二个存的是content
第三个是size,以及color_type
 HouseofOrange_Hitcon_2016:利用_IO_FILE_plus结构洞获取shell
HouseofOrange_Hitcon_2016:利用_IO_FILE_plus结构洞获取shell





 本文详细介绍了HouseofOrange_Hitcon_2016 CTF挑战中关于_IO_FILE_plus结构体的利用方法。通过分析_IO_FILE结构和vtable,利用堆溢出和unsorted_bin攻击,最终实现将_IO_OVERFLOW函数修改为system,以获取shell。文章详细阐述了漏洞利用的步骤和思路,包括main函数、add和edit函数的分析,以及如何通过编辑操作泄露和控制内存。
本文详细介绍了HouseofOrange_Hitcon_2016 CTF挑战中关于_IO_FILE_plus结构体的利用方法。通过分析_IO_FILE结构和vtable,利用堆溢出和unsorted_bin攻击,最终实现将_IO_OVERFLOW函数修改为system,以获取shell。文章详细阐述了漏洞利用的步骤和思路,包括main函数、add和edit函数的分析,以及如何通过编辑操作泄露和控制内存。
 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章

















 1627
1627

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








