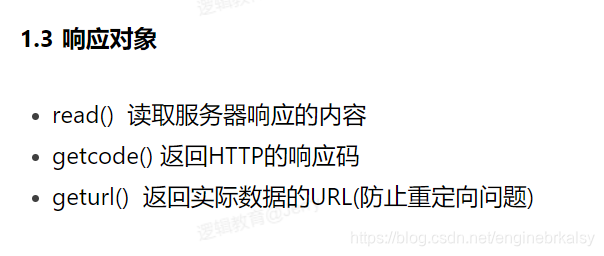
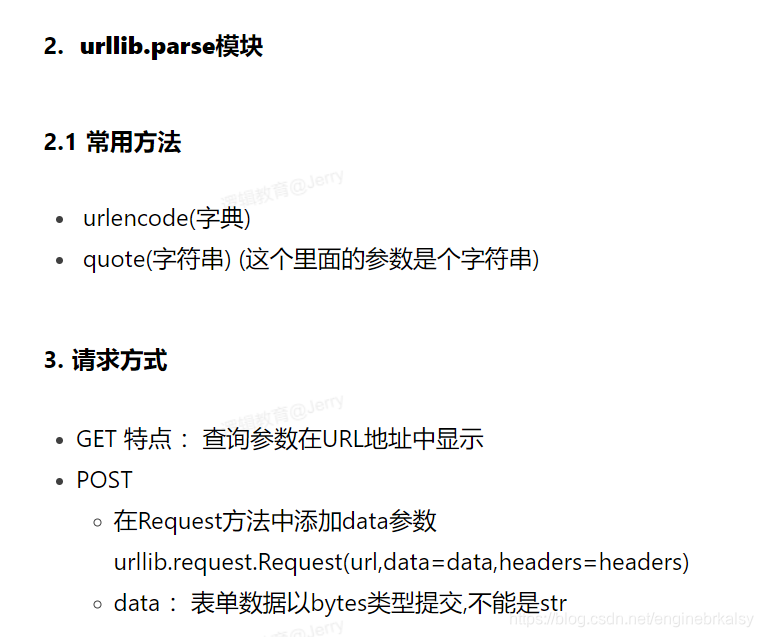
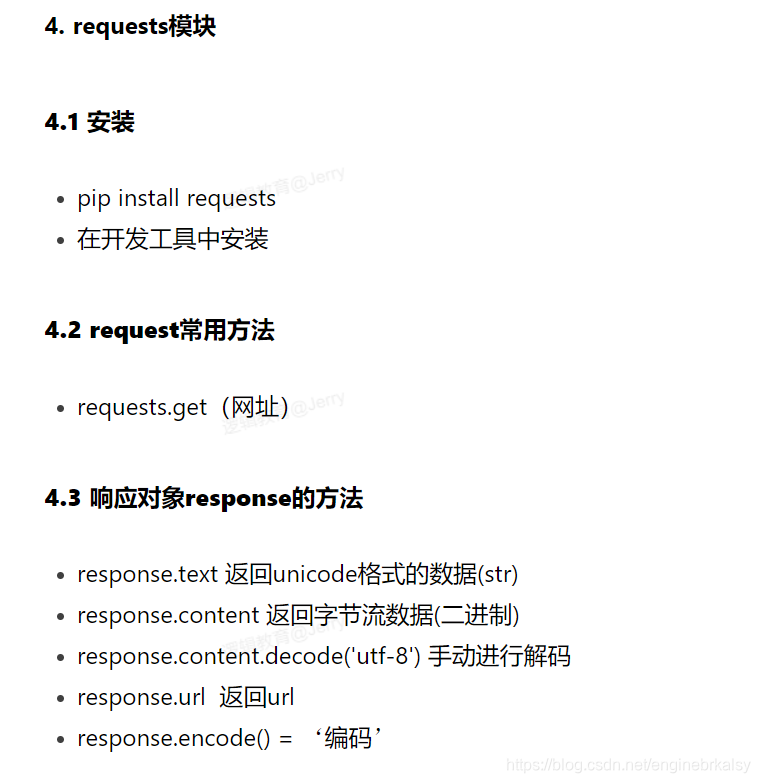
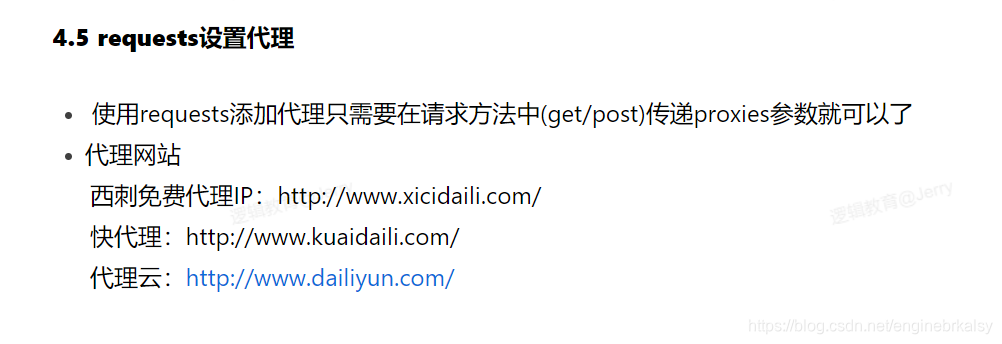
知识补充


cookie作用1:反爬案例——购票
运用了AJAX技术,不用重新加载页面也可以改变数据
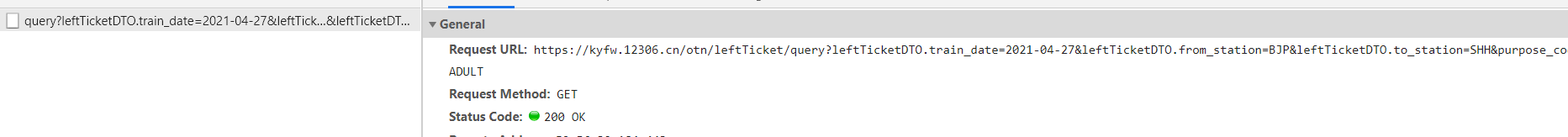
import requests
url = 'https://kyfw.12306.cn/otn/leftTicket/query?leftTicketDTO.train_date=2021-04-27&leftTicketDTO.from_station=BJP&leftTicketDTO.to_station=SHH&purpose_codes=ADULT'
headers = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.104 Safari/537.36'
}
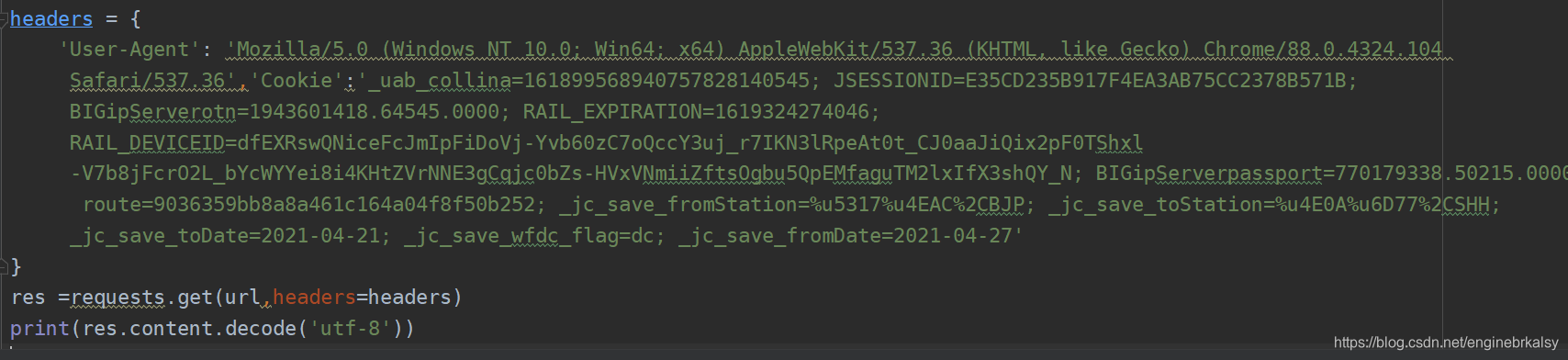
res =requests.get(url,headers=headers)
print(res.content.decode('utf-8'))
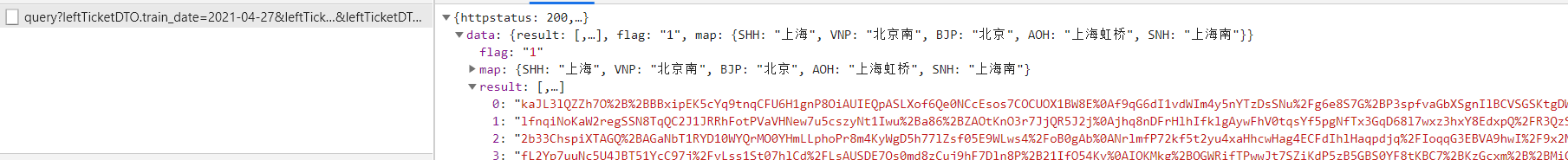
发现结果不是想要的
解决:加入cookie
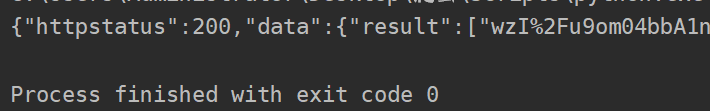
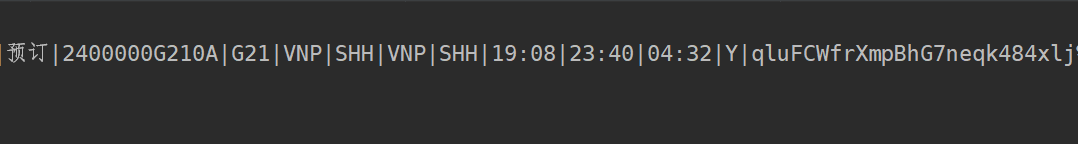
成功了
cookie作用2:模拟登录
# 模拟登录
# https://www.zhihu.com/signin?next=%2F 知乎登录界面
# https://www.zhihu.com/hot 知乎热榜界面
url = 'https://www.zhihu.com/hot'
headers = {
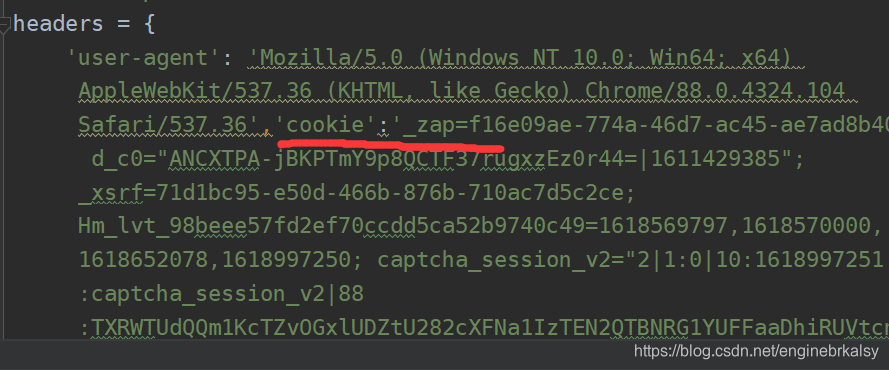
'user-agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.104 Safari/537.36'
}
res =requests.get(url,headers=headers)
print(res.text)
证明没有进入hot界面,加入cookie,成功了
session——突破图片验证码
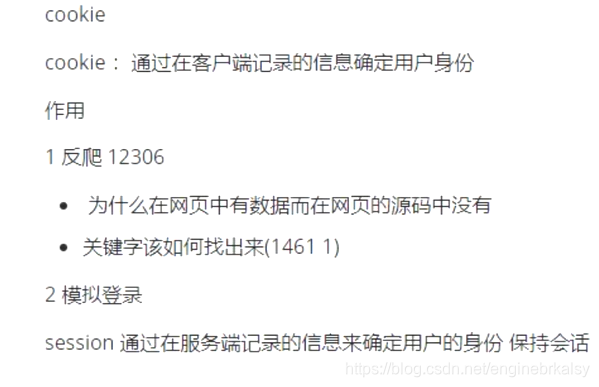

验证码失败显示:
需求:进入页面
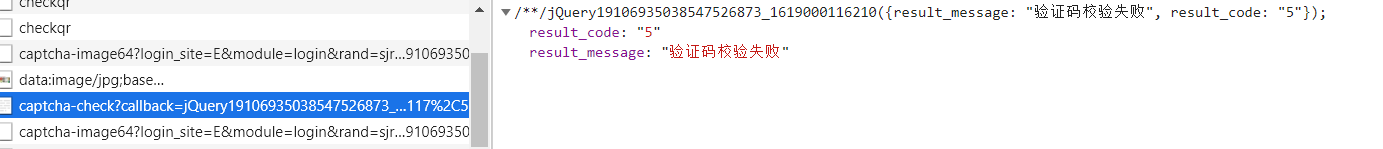
请求失败:

先要获取图片的url——运用base64转换——要把第一行删掉
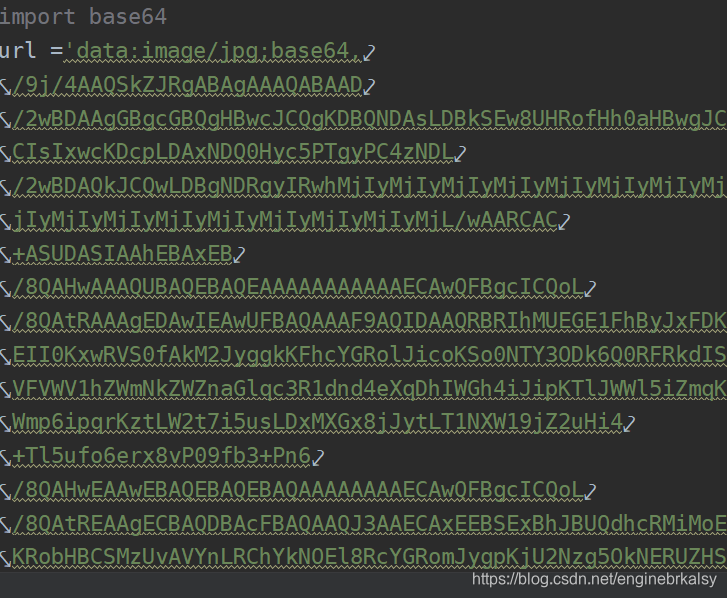
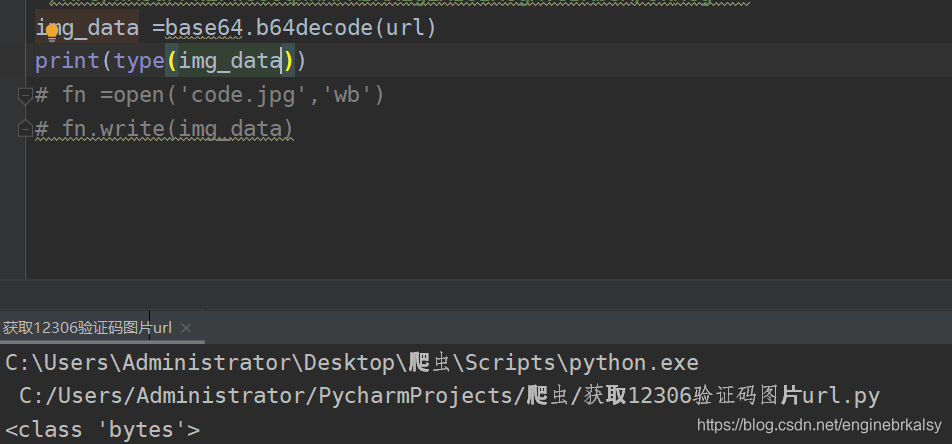
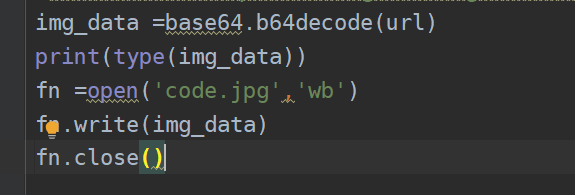
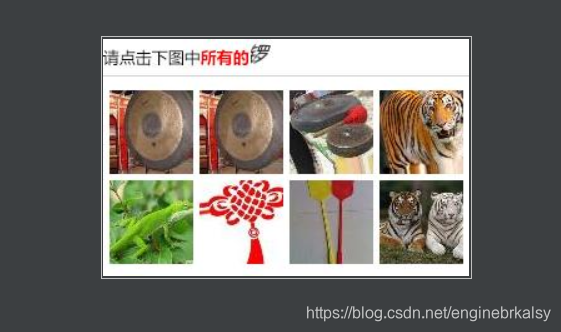
用上述方法得到图片太麻烦,用以下方式简单:
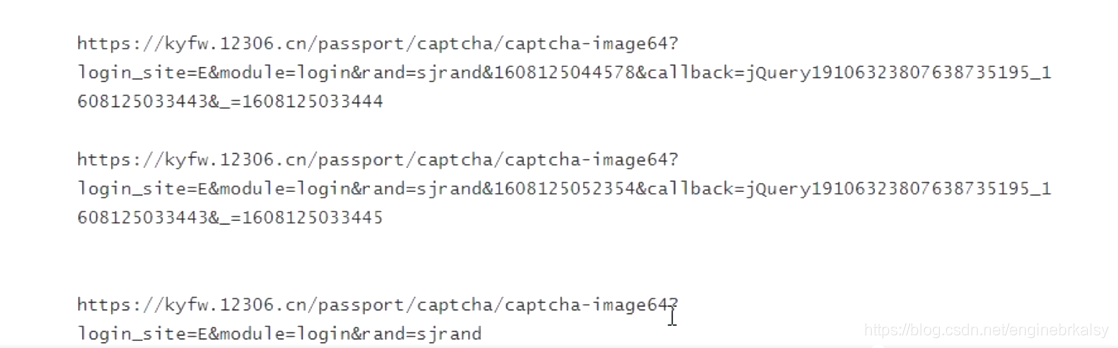
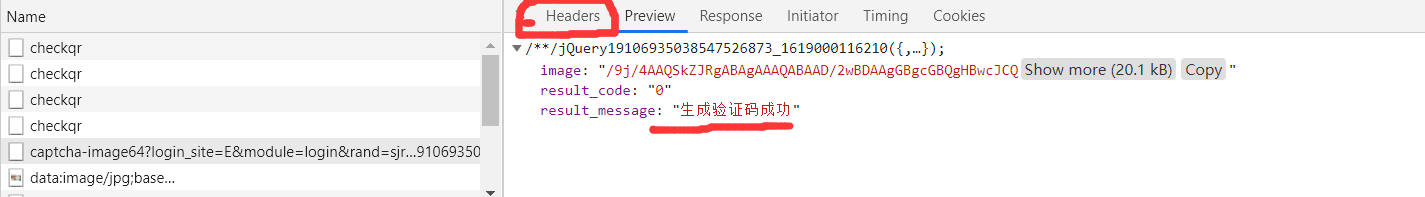
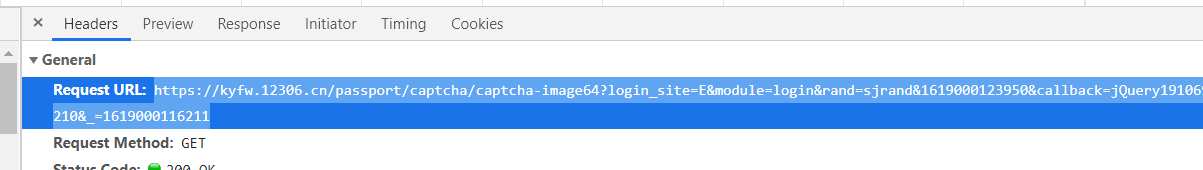
删掉image64的64结果:
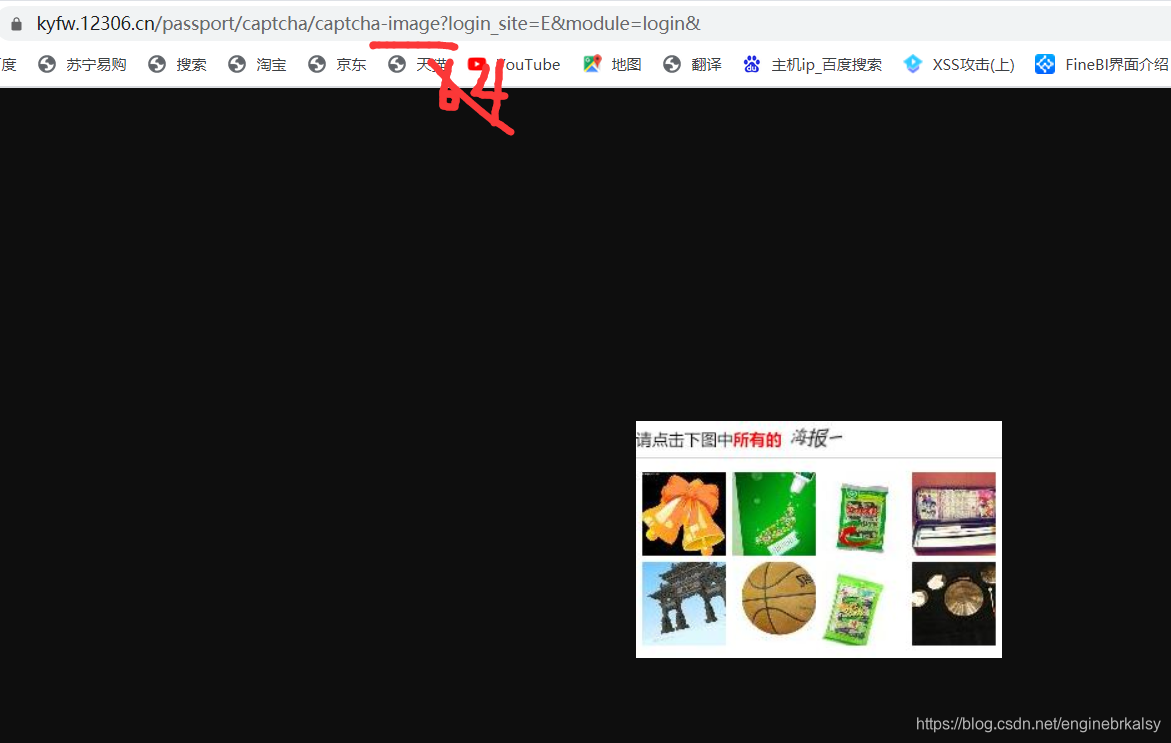
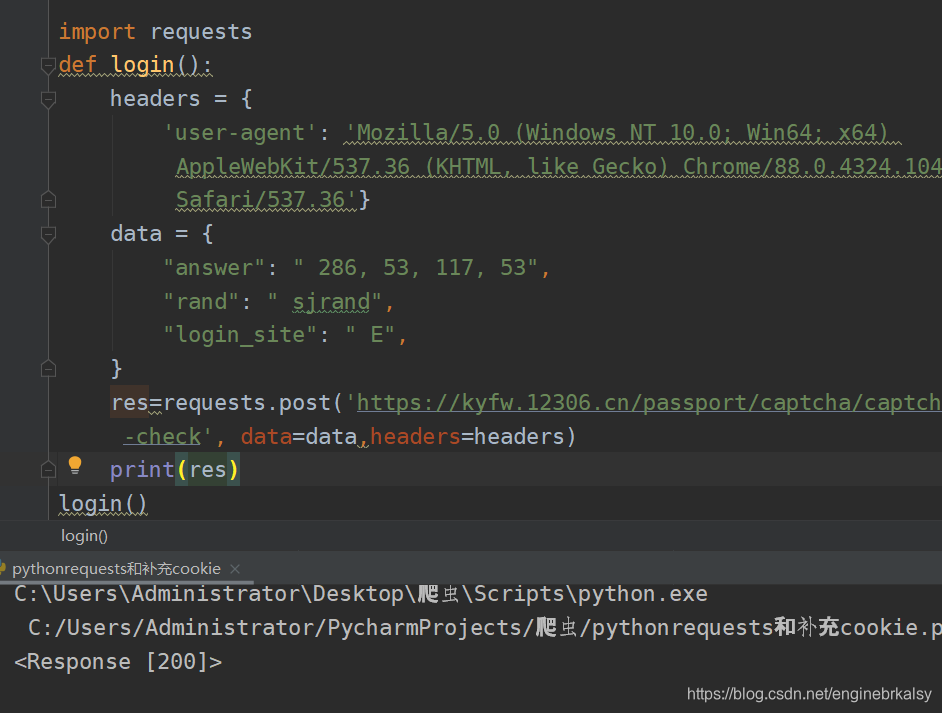
用session——保持会话
import requests
req =requests.session()
def login():
# 获取图片
pic_response =req.get('https://kyfw.12306.cn/passport/captcha/captcha-image64?login_site=E&module=login&rand=sjrand')
codeImage=pic_response.content
fn =open('code5.png','wb')
fn.write(codeImage)
fn.close()
headers = {
'user-agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.104 Safari/537.36'}
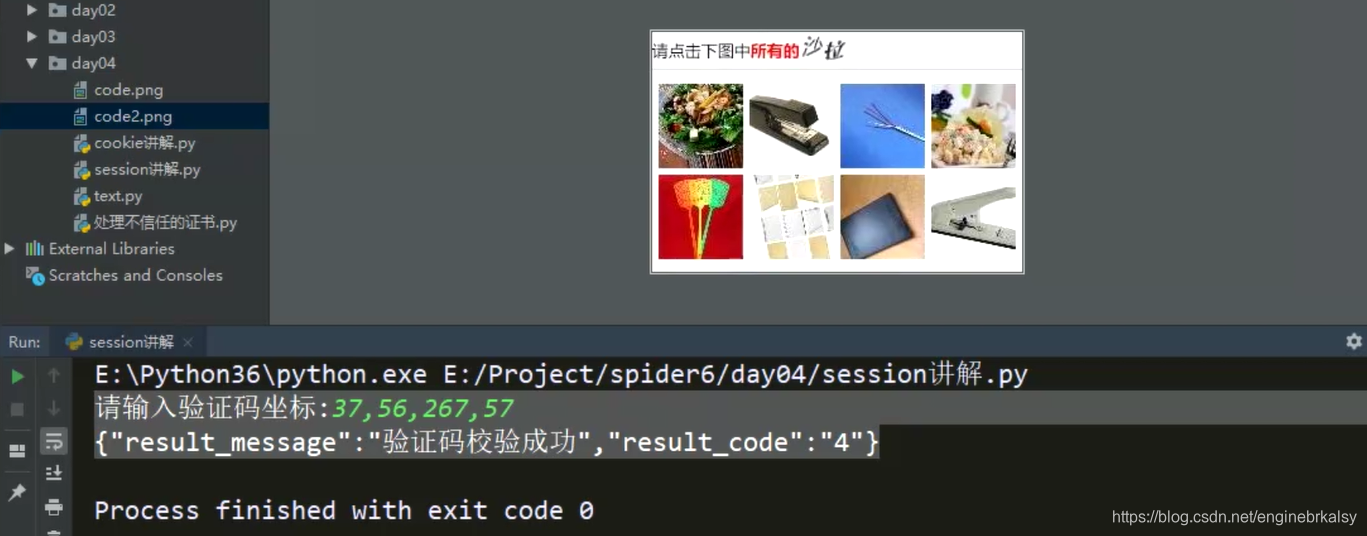
codeStr =input("请输入验证码坐标")
data = {
"answer": codeStr,
"rand": " sjrand",
"login_site": " E",
}
res=req.post('https://kyfw.12306.cn/passport/captcha/captcha-check', data=data,headers=headers)
print(res.text)
login()
图片坐标用截图来写


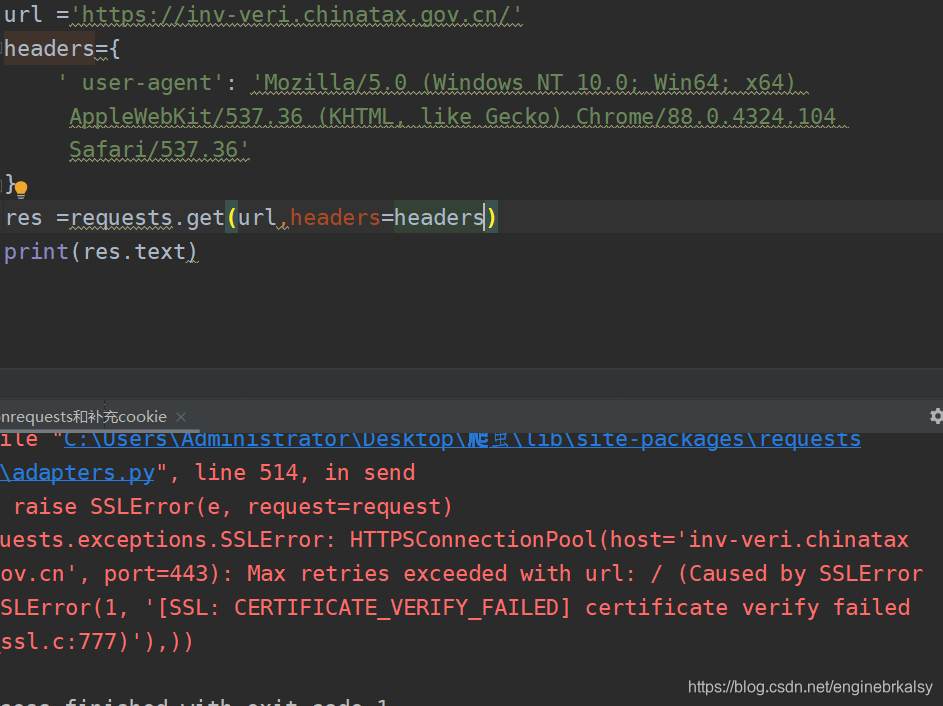
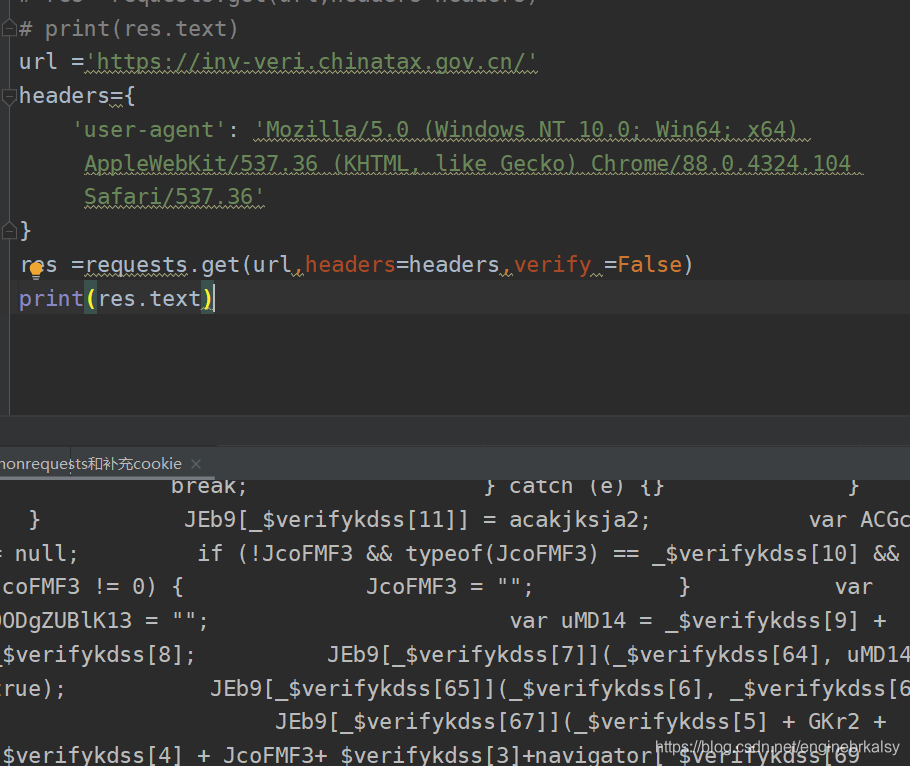
解决方法:verify =false
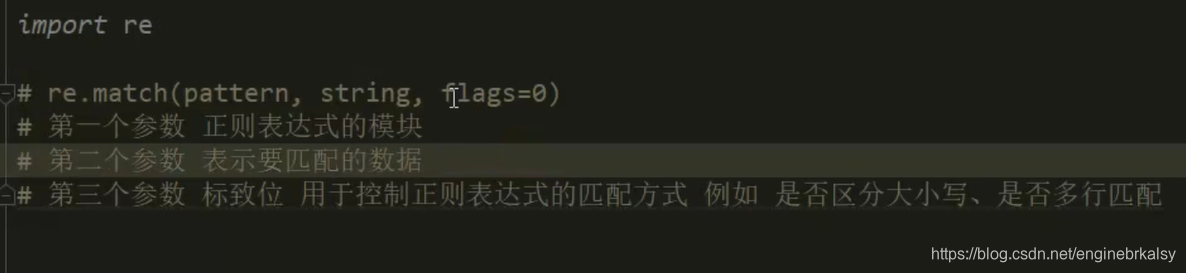
正则表达式介绍

 Cookie与Session实战:从反爬到验证码破解
Cookie与Session实战:从反爬到验证码破解





















 5834
5834

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








