CVE-2021-3129分析
- Tag: [[php phar]] | [[php deserialize]]
Env搭建
VulEnv/laravel/cve_2021_3129 at master · XuCcc/VulEnv
Source 分析
根据描述,本质上是由于 facade/ignition 引入的问题,直接查看 ignition 的 commit 记录[^1] 看到 \Facade\Ignition\Solutions\MakeViewVariableOptionalSolution 添加了一个安全过滤函数 isSafePath
// \Facade\Ignition\Solutions\MakeViewVariableOptionalSolution::makeOptional
public function makeOptional(array $parameters = []){
$originalContents = file_get_contents($parameters['viewFile']); $newContents = str_replace('$'.$parameters['variableName'], '$'.$parameters['variableName']." ?? ''", $originalContents); $originalTokens = token_get_all(Blade::compileString($originalContents)); $newTokens = token_get_all(Blade::compileString($newContents)); $expectedTokens = $this->generateExpectedTokens($originalTokens, $parameters['variableName']); if ($expectedTokens !== $newTokens) {
return false; } return $newContents;}发现危险函数 file_get_contents ,跟踪函数调用栈
- \Facade\Ignition\Solutions\MakeViewVariableOptionalSolution::makeOptional
- \Facade\Ignition\Solutions\MakeViewVariableOptionalSolution::run
- \Facade\Ignition\Http\Controllers\ExecuteSolutionController::__invoke
- \Facade\Ignition\IgnitionServiceProvider::registerHousekeepingRoutes
参数$parameters['viewFile']无过滤,通过execute-solution路由可以进行触发,结合官方文档[^2] 可知,在执行solution操作时将走到 source 处。
Poc 编写
启动环境后,就出现了一个 igition 的错误修复界面,点击 Generate app key 抓包
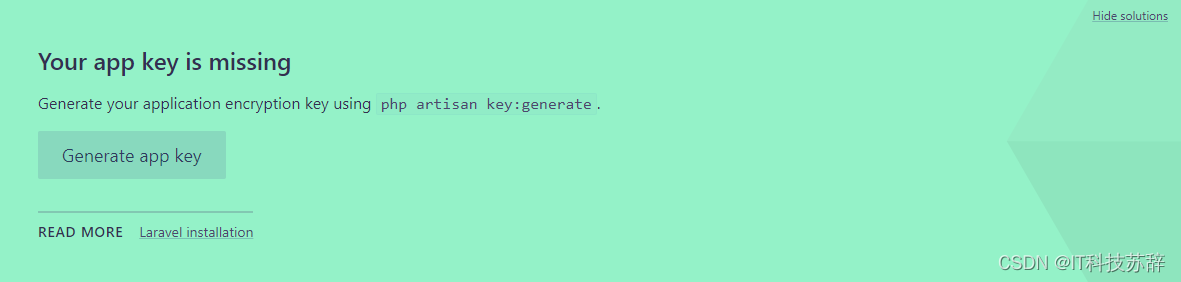
POST /_ignition/execute-solution HTTP/1.1
Host: localhost:8000Content-Length: 82Accept: application/jsonContent-Type: application/jsonUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36Origin: http://localhost:8000Referer: http://localhost:8000/Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Connection: close{
"solution":"Facade\\Ignition\\Solutions\\GenerateAppKeySolution","parameters":[]}
然后修改参数 solution 修改为 MakeViewVariableOptionalSolution 指定 solution
POST /_ignition/execute-solution HTTP/1.1
Host: localhost:8000Content-Length: 163Accept: application/jsonContent-Type: application/jsonUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36Origin: http://localhost:8000Referer: http://localhost:8000/Accept-Encoding: gzip, deflateAccept




 该博客详细分析了CVE-2021-3129漏洞,涉及PHP的phar和deserialization。内容包括环境搭建、源码分析、POC和EXP编写,以及利用思路和修复方案。通过操纵日志文件,利用phar文件结构特点实现反序列化攻击。
该博客详细分析了CVE-2021-3129漏洞,涉及PHP的phar和deserialization。内容包括环境搭建、源码分析、POC和EXP编写,以及利用思路和修复方案。通过操纵日志文件,利用phar文件结构特点实现反序列化攻击。
 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章

















 2589
2589

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








