启用kerberos服务步骤:
1 Kerberos部署
系统环境
1.操作系统:CentOS Linux release 7.9.2009
2.CDH6.3.2
3.采用root用户进行操作
2. KDC服务安装及配置
1). 在Cloudera Manager服务器上安装KDC服务
yum install krb5-server krb5-libs krb5-auth-dialog krb5-workstation openldap-clients -y
会生成/etc/krb5.conf、/var/kerberos/krb5kdc/kadm5.acl、/var/kerberos/krb5kdc/kdc.conf三个文件。
2). 修改/etc/krb5.conf配置
vi /etc/krb5.conf
Configuration snippets may be placed in this directory as well
includedir /etc/krb5.conf.d/
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
dns_lookup_realm = false
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = true
rdns = false
pkinit_anchors = FILE:/etc/pki/tls/certs/ca-bundle.crt
default_realm = JHT.COM
#default_ccache_name = KEYRING:persistent:%{uid}
[realms]
JHT.COM = {
kdc = cdh01
admin_server = cdh01
}
[domain_realm]
.jht.com = JHT.COM
jht.com = JHT.COM
第一部分是logging配置, 略过。 然后是libdefaults部分:
default_realm: 默认realm,例如当我们使用kinit而不指定principal时使用的就是这里配置的默认realm
dns_lookup_realm:是否可以通过DNS查找使用什么样的realm
ticket_lifetime: 设定ticket的有效期
forwardable: 用于指定ticket是否可以被转发,转发的含义是:如果一个用户已经有了一个TGT,当他登入到另一个远程系统,KDC会为他自动重新创建一个TGT,而不需要让用户重新进行身份认证
然后是[realms]部分,这一部分会列出所有的realm,kdc和admin_server两个配置是在告诉客户端哪台服务器在运行KDC以及kadmin进程。这两项配置可以在服务器上追加端口,如果不指定,则使用默认端口,KDC是88,admin server是749.
最后一部分[domain_realm]是配置DNS名称和Kerberos Realm映射的。
.http://jht.com = JHT.COM是在说:所有在jht.com域下的主机都会被映射到JHT.COM这个realm下,而jht.com = JHT.COM是说jht.com它自己也会映射到JHT.COM这个realm。
3). 修改/var/kerberos/krb5kdc/kadm5.acl配置
vim /var/kerberos/krb5kdc/kadm5.acl
*/admin@JHT.COM *
4). 修改/var/kerberos/krb5kdc/kdc.conf配置
vim /var/kerberos/krb5kdc/kdc.conf
[kdcdefaults]
kdc_ports = 88
kdc_tcp_ports = 88
[realms]
JHT.COM = {
#master_key_type = aes256-cts
max_renewable_life= 7d 0h 0m 0s
acl_file = /var/kerberos/krb5kdc/kadm5.acl
dict_file = /usr/share/dict/words
admin_keytab = /var/kerberos/krb5kdc/kadm5.keytab
supported_enctypes = aes256-cts:normal aes128-cts:normal des3-hmac-sha1:normal arcfour-hmac:normal camellia256-cts:normal camellia128-cts:normal des-hmac-sha1:normal des-cbc-md5:normal des-cbc-crc:normal
}
5). 创建Kerberos数据库
kdb5_util create –r http://JHT.COM -s
Loading random data
Initializing database ‘/var/kerberos/krb5kdc/principal’ for realm ‘JHT.COM’,
master key name ‘K/M@JHT.COM’
You will be prompted for the database Master Password.
It is important that you NOT FORGET this password.
Enter KDC database master key:【输入密码为hadoop】
Re-enter KDC database master key to verify:【输入密码为hadoop】
此处需要输入Kerberos数据库的密码,设置为hadoop。
6). 创建Kerberos的管理账号
admin/admin@JHT.COM
输入: kadmin.local
Authenticating as principal root/admin@JHT.COM with password.
kadmin.local:
kadmin.local: addprinc admin/admin@JHT.COM
WARNING: no policy specified for admin/admin@JHT.COM; defaulting to no policy
Enter password for principal “admin/admin@JHT.COM”: 【输入密码为admin】
Re-enter password for principal “admin/admin@JHT.COM”:
Principal “admin/admin@JHT.COM” created.
kadmin.local:
7).将Kerberos服务添加到自启动服务,并启动krb5kdc和kadmin服务
systemctl enable krb5kdc
systemctl enable kadmin
systemctl start krb5kdc
systemctl start kadmin
8) .测试Kerberos的管理员账号
kinit admin/admin@JHT.COM
.为集群安装所有Kerberos客户端,包括Cloudera Manager
yum -y install krb5-libs krb5-workstation
10).将KDC Server上的krb5.conf文件拷贝到所有Kerberos客户端
scp /etc/krb5.conf root@cdh02:/etc/
scp /etc/krb5.conf root@cdh03:/etc/
2. 配置KERBEROS管理员账号
1.在KDC中给Cloudera Manager添加管理员账号
cloudera-scm/admin@JHT.COM
[root@dev01 ~]# kadmin.local
Authenticating as principal root/admin@JHT.COM with password.
kadmin.local: addprinc cloudera-scm/admin@JHT.COM
WARNING: no policy specified for cloudera-scm/admin@JHT.COM; defaulting to no policy
Enter password for principal “cloudera-scm/admin@JHT.COM”: [密码:admin]
Re-enter password for principal “cloudera-scm/admin@JHT.COM”: [密码:admin]
Principal “cloudera-scm/admin@JHT.COM” created.
kadmin.local: list_principals
HTTP/cdh01@JHT.COM
HTTP/cdh02@JHT.COM
HTTP/cdh03@JHT.COM
K/M@JHT.COM
admin/admin@JHT.COM
cloudera-scm/admin@JHT.COM
hdfs/cdh01@JHT.COM
hdfs/cdh02@JHT.COM
hdfs/cdh03@JHT.COM
hdfs@JHT.COM
hive/cdh01@JHT.COM
hive/cdh03@JHT.COM
hue/cdh02@JHT.COM
hue/cdh03@JHT.COM
kadmin/admin@JHT.COM
kadmin/cdh01@JHT.COM
kadmin/changepw@JHT.COM
kiprop/cdh01@JHT.COM
krbtgt/JHT.COM@JHT.COM
mapred/cdh03@JHT.COM
service@JHT.COM
spark/cdh02@JHT.COM
yarn/cdh01@JHT.COM
yarn/cdh02@JHT.COM
yarn/cdh03@JHT.COM
zookeeper/cdh01@JHT.COM
zookeeper/cdh02@JHT.COM
zookeeper/cdh03@JHT.COM
<9>启用kerberos服务过程报错:把几个缺少的域全部加入kerberos数据库。
USERNAME-REDACTED kinit: Client 'USERNAME-REDACTED' not found in Kerberos database while getting initial credentials
这个时候需要看 cat /var/log/krb5kdc.log报错;
- 检查 KDC 日志:tail -f /var/log/krb5kdc.log
- 检查 Cloudera 日志:tail -f /var/log/cloudera-scm-server/cloudera-scm-server.log
CLIENT_NOT_FOUND: root@JHT.COM for krbtgt/JHT.COM@JHT.COM, Client not found in Kerberos database
CLIENT_NOT_FOUND: admin@JHT.COM for krbtgt/JHT.COM@JHT.COM, Client not found in Kerberos database
ISSUE: authtime 1754633676, etypes {rep=18 tkt=18 ses=18}, admin/admin@JHT.COM for krbtgt/JHT.COM@JHT.COM
ISSUE: authtime 1754633775, etypes {rep=18 tkt=18 ses=18}, admin/admin@JHT.COM for krbtgt/JHT.COM@JHT.COM
ISSUE: authtime 1754633788, etypes {rep=18 tkt=18 ses=18}, admin/admin@JHT.COM for krbtgt/JHT.COM@JHT.COM
LOOKING_UP_SERVER: authtime 0, admin/admin@JHT.COM for host/cdhb@JHT.COM, Server not found in Kerberos database
LOOKING_UP_SERVER: authtime 0, admin/admin@JHT.COM for host/cdhb@JHT.COM, Server not found in Kerberos database
LOOKING_UP_SERVER: authtime 0, admin/admin@JHT.COM for host/cdhc@JHT.COM, Server not found in Kerberos database
LOOKING_UP_SERVER: authtime 0, admin/admin@JHT.COM for host/cdhc@JHT.COM, Server not found in Kerberos database
CLIENT_NOT_FOUND: cloudera-scm@JHT.COM for krbtgt/JHT.COM@JHT.COM, Client not found in Kerberos database
CLIENT_NOT_FOUND: cloudera-scm@JHT.COM for krbtgt/JHT.COM@JHT.COM, Client not found in Kerberos database
3. CDH集群启用Kerberos
- 进入Cloudera Manager的“管理”->“安全”界面
<1>选择“启用Kerberos”,进入如下界面
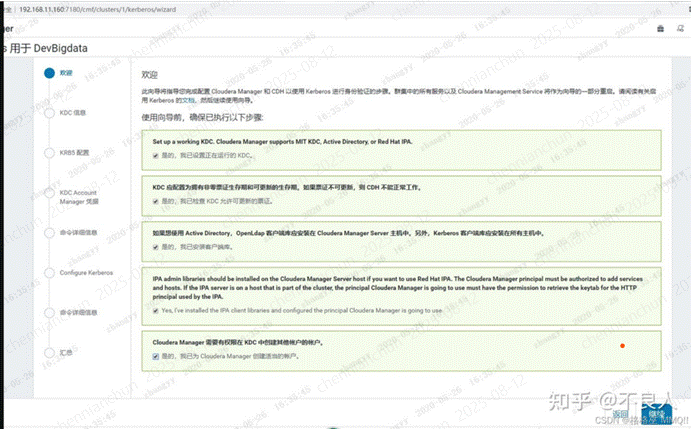
<2>启用kerberos配置过程:
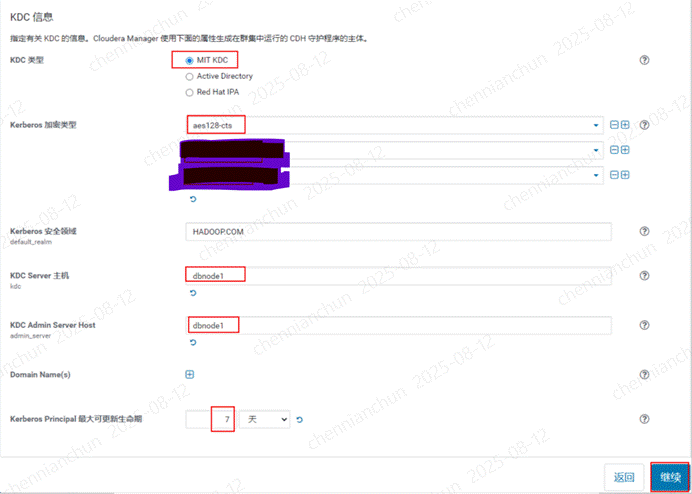
<3>配置kdc过程,只选择aes128-cts加密:域名JHT.COM
<4>
重新配置KERBEROS步骤:
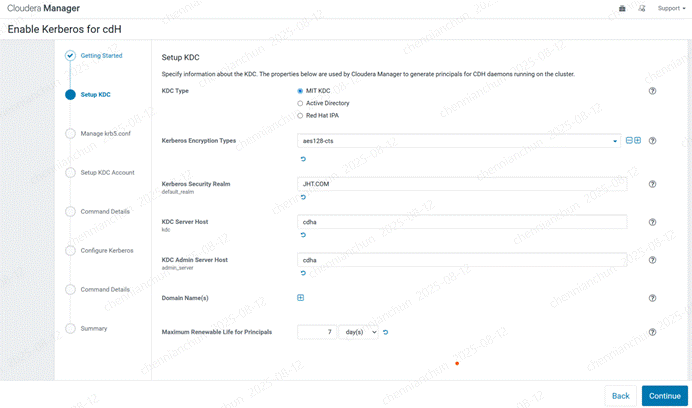
<5>不勾选
《17》设置kdc账号

《18》导入kdc管理凭证

《19》配置kerberos
《20》启用kerberos命令
《21》启用kerberos完成
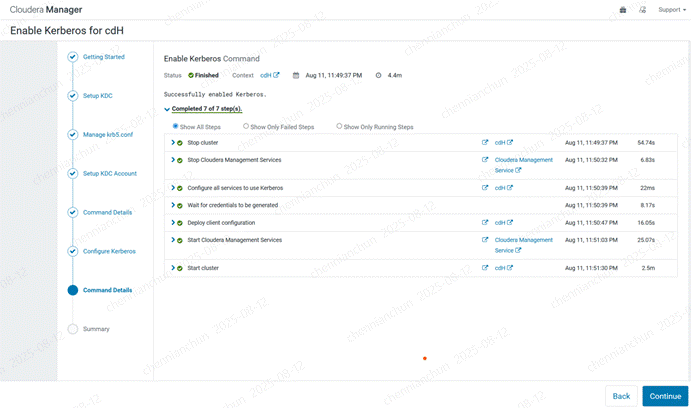
《22》完成
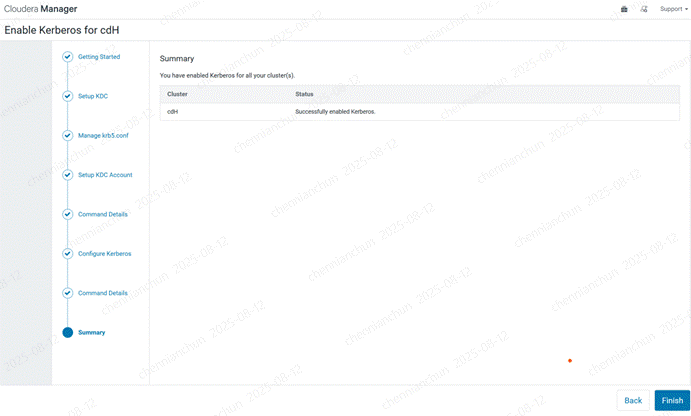
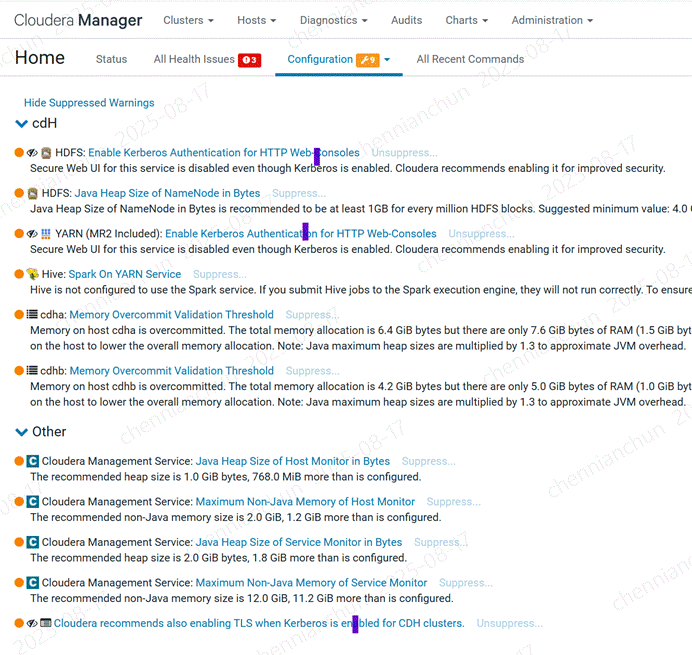
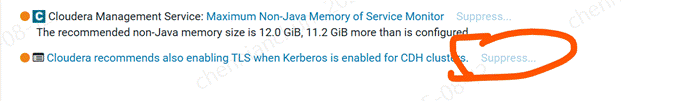
《23》完成后,配置有2个配置告警,需要启用kerberos服务。
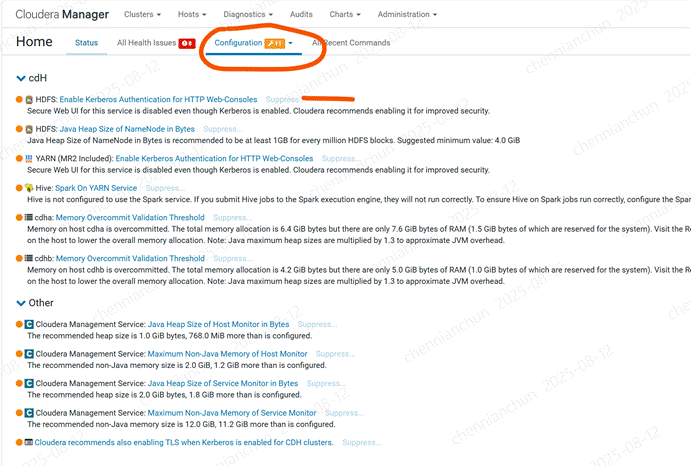
《24》hdfs启用kerberos服务【建议不启用,后面访问HTTP很麻烦】
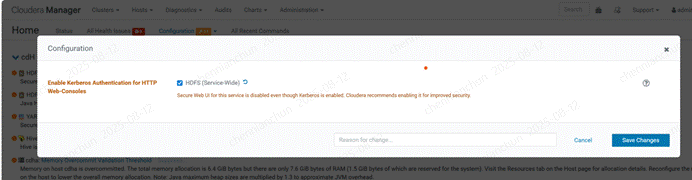
《25》yarn启用kerberos服务【建议不启用,后面访问HTTP很麻烦】
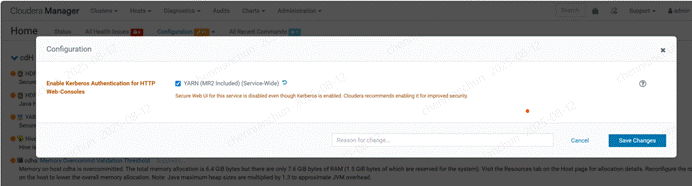
《25》不启用kerberos服务的结果;
《26》配置完成后,重启整个集群
《27》重启整个CDH服务:
《28》下面步骤省掉,suppress镇压掉;
Cloudera recommends also enabling TLS when Kerberos is enabled for CDH clusters. 介绍下配置步骤
这个步骤配置比较复杂,先不要配置;
《29》测试访问hdfs服务:
[root@cdhb ~]#
[root@cdhb ~]# hdfs dfs -ls /
25/08/12 00:47:07 WARN ipc.Client: Exception encountered while connecting to the server : org.apache.hadoop.security.AccessControlException: Client cannot authenticate via:[TOKEN, KERBEROS]
ls: Failed on local exception: java.io.IOException: org.apache.hadoop.security.AccessControlException: Client cannot authenticate via:[TOKEN, KERBEROS]; Host Details : local host is: "cdhb/192.168.118.133"; destination host is: "cdha":8020;
You have new mail in /var/spool/mail/root
[root@cdhb ~]#
[root@cdhb ~]#
通过kerberos的认证:
[root@cdh01 ~]# kinit hdfs
Password for hdfs@JHT.COM:
[root@cdhb ~]# hdfs dfs -ls /
Found 4 items
-rw-r--r-- 3 hdfs supergroup 26 2025-07-25 20:45 /aaa.txt
drwxr-xr-x - hbase hbase 0 2025-08-12 00:42 /hbase
drwxrwxrwt - hdfs supergroup 0 2025-07-25 20:25 /tmp
drwxr-xr-x - hdfs supergroup 0 2025-07-26 23:14 /user
[root@cdhb ~]#
《30》通过浏览器访问hdfs文件系统,需要验证密码;
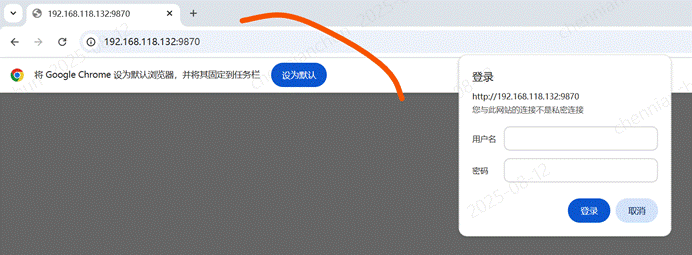
密码admin
《31》访问hive;
[root@cdhb ~]# beeline -u "jdbc:hive2://cdha:10000/default;principal=hive/cdha@JHT.COM"
WARNING: Use "yarn jar" to launch YARN applications.
SLF4J: Class path contains multiple SLF4J bindings.
SLF4J: Found binding in [jar:file:/opt/cloudera/parcels/CDH-6.3.2-1.cdh6.3.2.p0.1605554/jars/log4j-slf4j-impl-2.8.2.jar!/org/slf4j/impl/StaticLoggerBinder.class]
SLF4J: Found binding in [jar:file:/opt/cloudera/parcels/CDH-6.3.2-1.cdh6.3.2.p0.1605554/jars/slf4j-log4j12-1.7.25.jar!/org/slf4j/impl/StaticLoggerBinder.class]
SLF4J: See http://www.slf4j.org/codes.html#multiple_bindings for an explanation.
SLF4J: Actual binding is of type [org.apache.logging.slf4j.Log4jLoggerFactory]
Connecting to jdbc:hive2://cdha:10000/default;principal=hive/cdha@JHT.COM
Connected to: Apache Hive (version 2.1.1-cdh6.3.2)
Driver: Hive JDBC (version 2.1.1-cdh6.3.2)
Transaction isolation: TRANSACTION_REPEATABLE_READ
Beeline version 2.1.1-cdh6.3.2 by Apache Hive
0: jdbc:hive2://cdha:10000/default>
《32》https://web.mit.edu/kerberos/ 下载kerberos客户端工具

《33》下载对应的版本4.1的64位
《34》配置C:\ProgramData\MIT\Kerberos5\krb5.ini文件
拷贝centos7 /etc/krb5.conf 中的内容,[logging]部分不要:
[libdefaults]
dns_lookup_realm = false
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = true
rdns = false
pkinit_anchors = FILE:/etc/pki/tls/certs/ca-bundle.crt
default_realm = JHT.COM
#default_ccache_name = KEYRING:persistent:%{uid}
[realms]
JHT.COM = {
kdc = cdh01
admin_server = cdh01
}
[domain_realm]
.jht.com = JHT.COM
jht.com = JHT.COM
.cdha = JHT.COM
cdha = JHT.COM
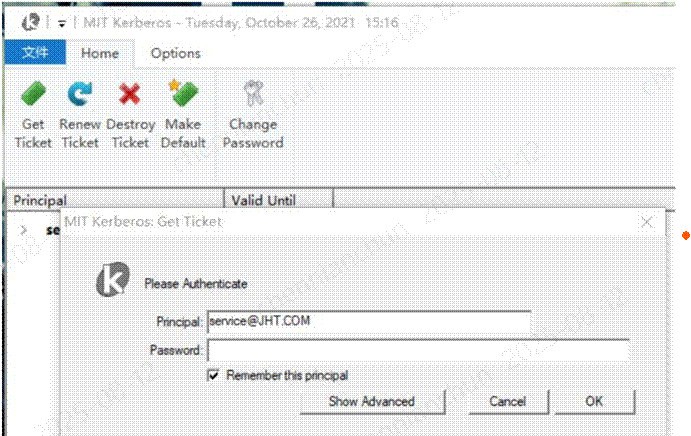
35配置完成后,启动MIT Kerberos客户端
输入centos 7上创建的用户,可以看到获取的Ticket。
36 firefox浏览器配置
- .在Firefox浏览器URL里输入:about:config
- .搜索network.negotiate-auth.trusted-uris, 配置值为域名cdha,cdhb,cdhc

- .搜索network.auth.use-sspi,双击值改为false

重启浏览器就可以正常访问hdfs了
《37》客户端正常配置后:就可以访问hdfs的文件系统;
需要通过主机名去访问hdfs:
《38》




















 925
925










