DNS集群的搭建
基本概念:DNS服务器一般在使用时,为了缓解服务器的压力,多使用一个主DNS服务器,多个副DNS服务器,这些DNS服务器就组成了一个DNS集群。
搭建DNS之前我们需要将之前在DNS的主配置文件步里做的DNS双向解析的代码删掉
##主DNS的搭建
主dns在之前作dns的正向解析,反向解析时,已经搭建好了.切记一定要将双向DNS给注释掉,还原最初始的样子,防止影响下面的实验.
##从DNS的搭建
在另一台虚拟机中安装bind的软件,然后修改其配置文件,将其变为从DNS
为了区分清楚主从DNS,我们将主DNS的虚拟机命名为dns0,将从DNS的虚拟机命名为dns1
第一步:修改主配置文件/etc/named.cmd
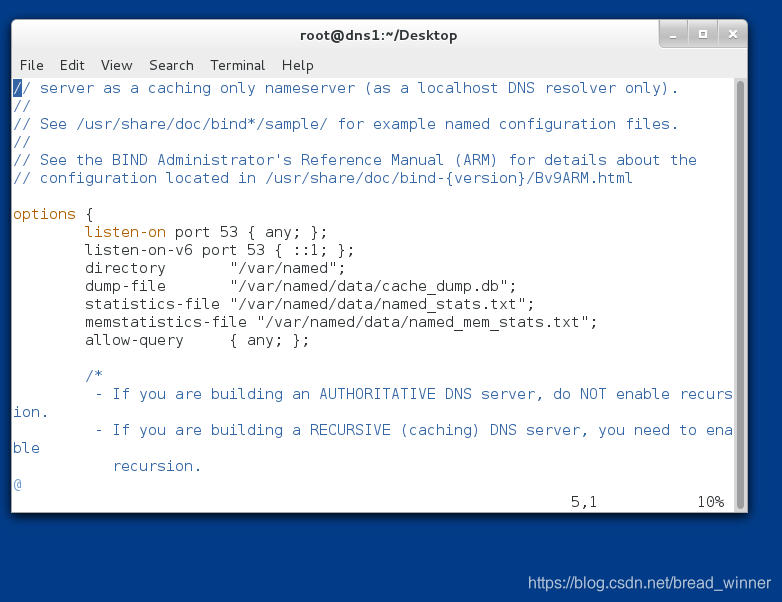
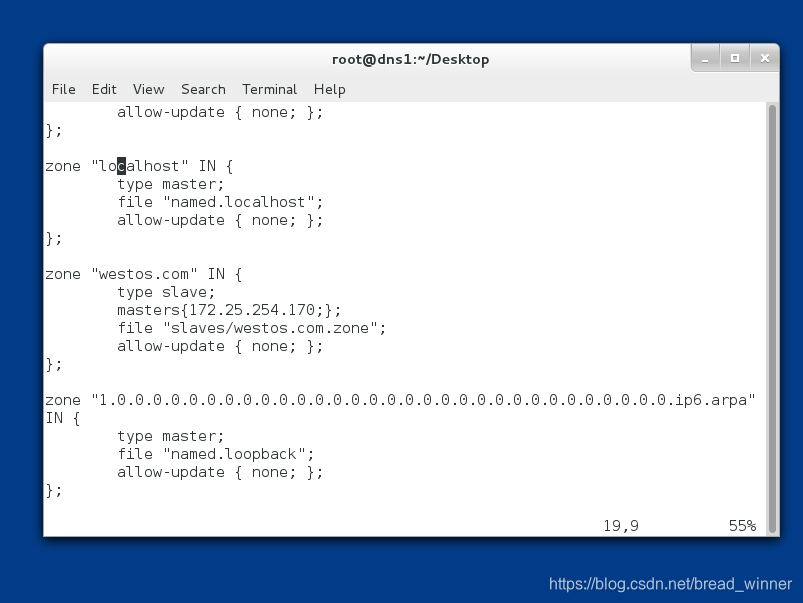
第二步:编写区域文件/etc/named.rfc1912.zones
##在副DNS中添加westos.zone的相关信息(类型和文件路径),并指明主DNS的id
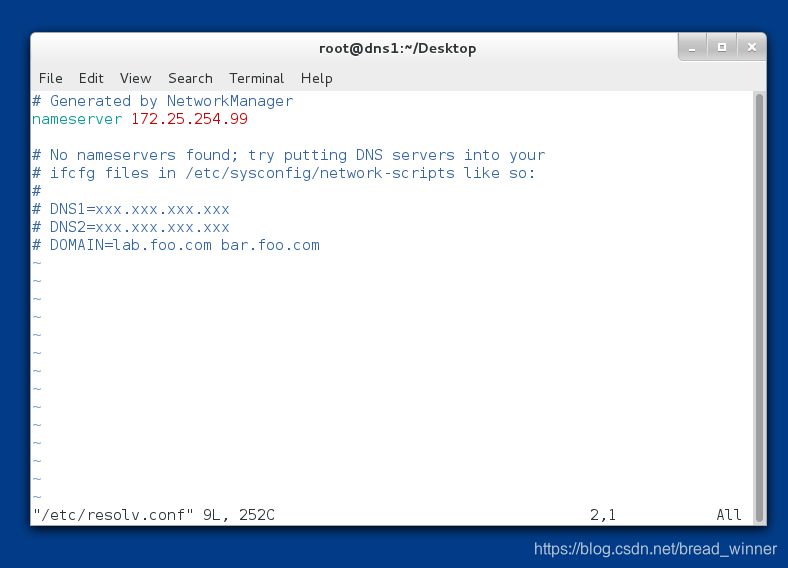
第三步:将自己的ip设置为副DNS主机
测试:在从DNS上查询主DNS的信息,单并未在从DNS上添加该网址信息,且访问的DNS为自己的ip.
若主从DNS查询结果相同,则说明DNS集群搭建完成.
主DNS上访问www.westos.com
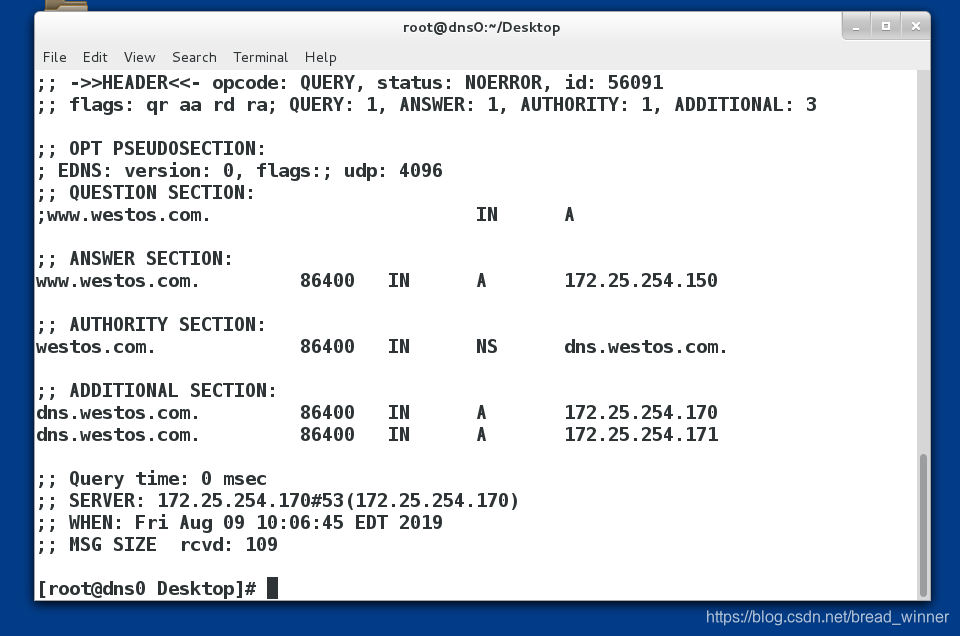
从DNS上访问www.westos.com
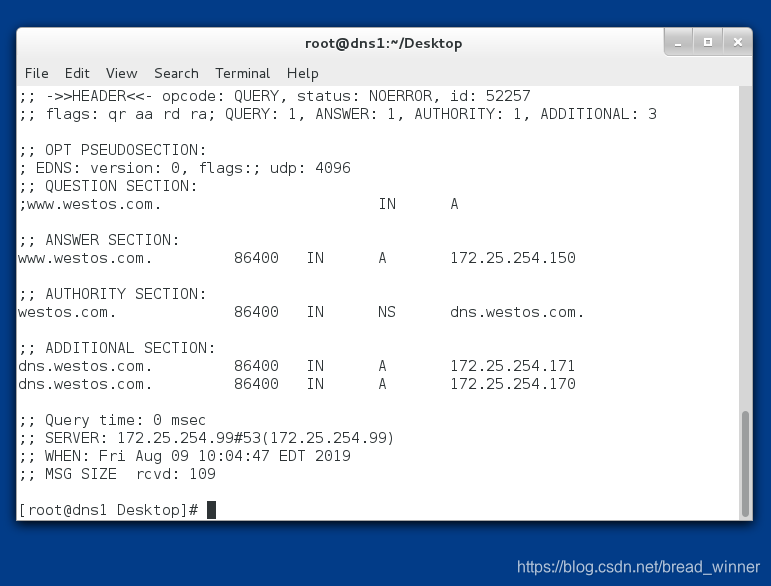
DNS同步
主DNS上对www.westos.com对应的ip进行修改,将原来的150该为250重启其服务
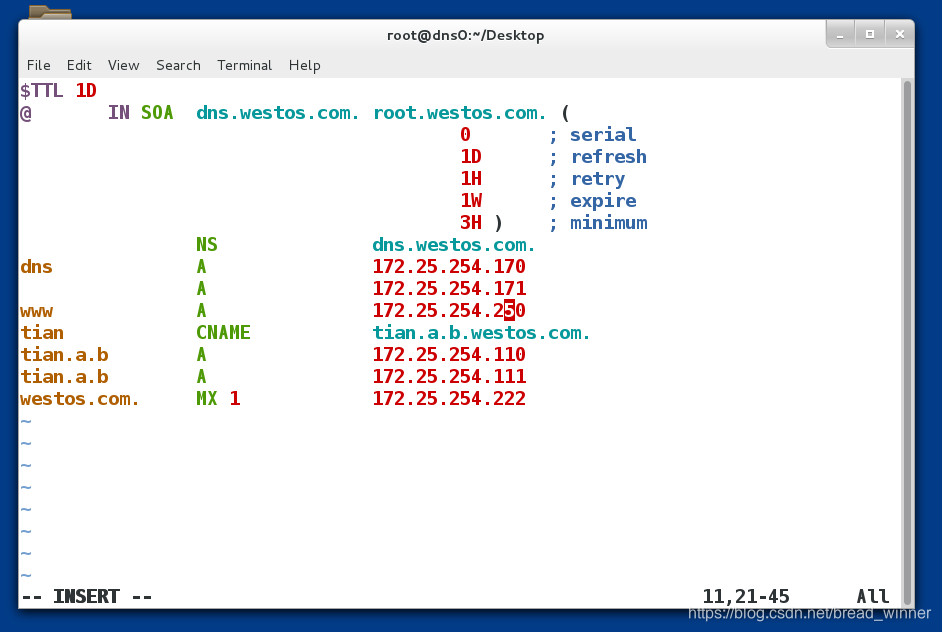
测试从DNS是否发生改变
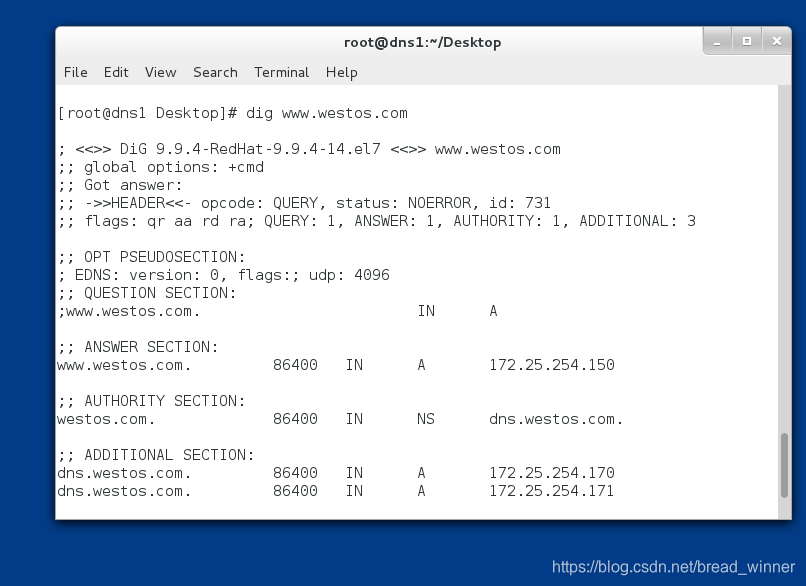
发现辅DNS是不能同步主DNS更新后的信息,这样我们需要进行主从DNS的更新
第一步:修改主DNS中的配置.
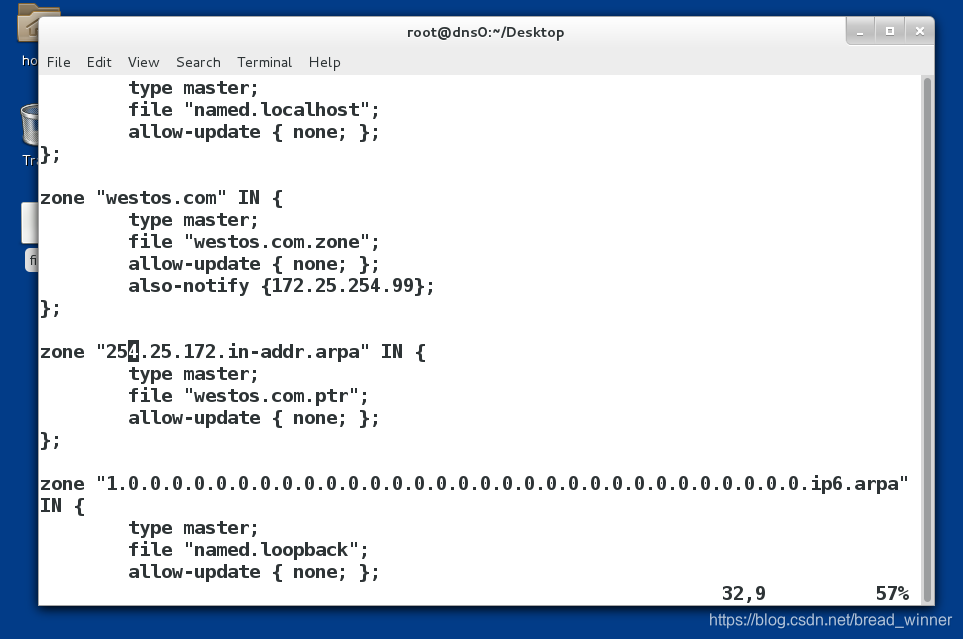
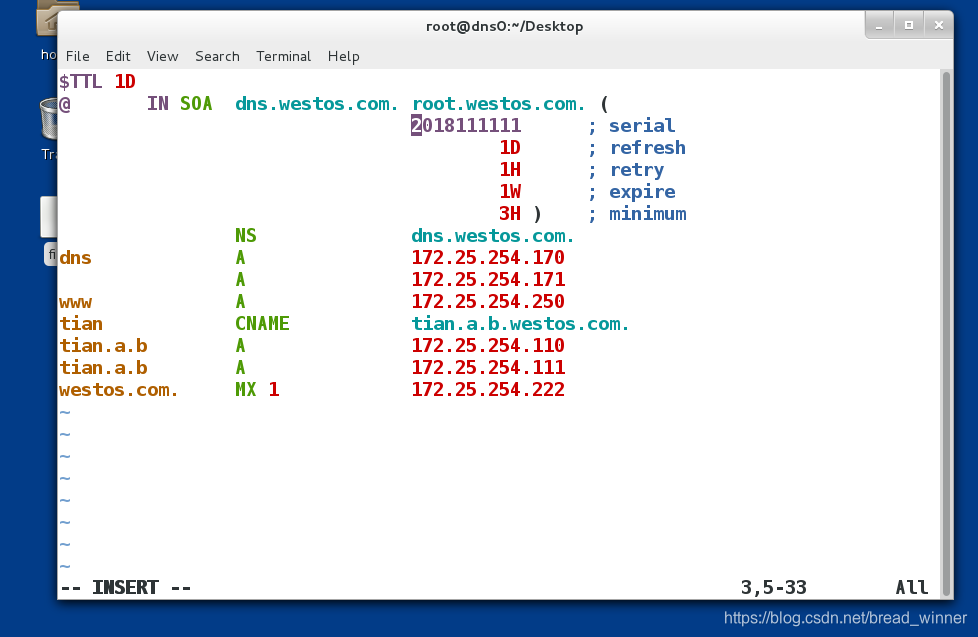
第二步:因为在两台服务器同步数据时,系统不是读取整个文件的内容,而是比较 ‘serial’前边的数字(这样比较节约时间),如果两台DNS服务器前边的数字相同,则不同步,如果不同,需要同步。所以每修改一次内容,都要修改 ‘serial’前的数字,该数字最长为10位
vim
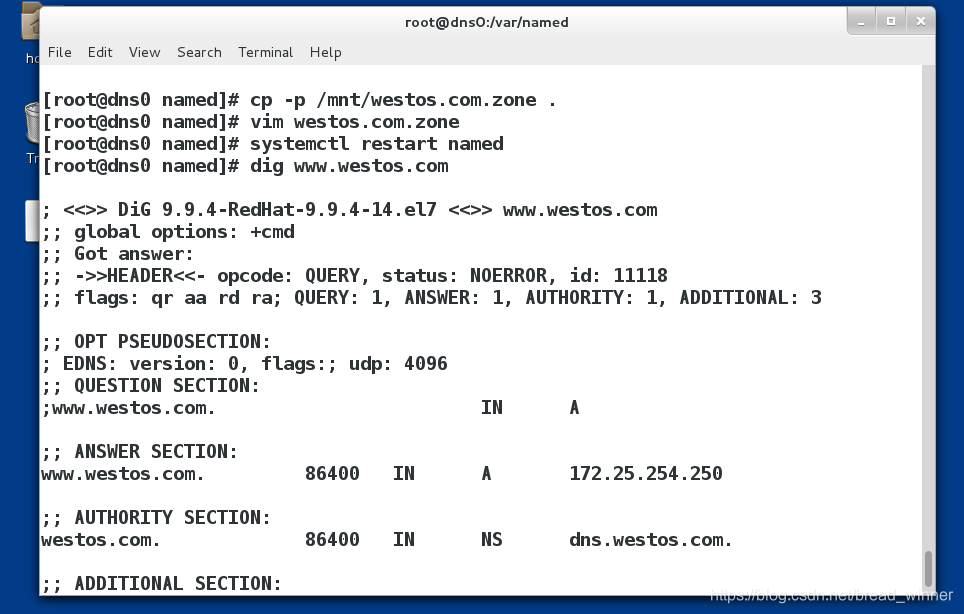
测试
主DNS测试:
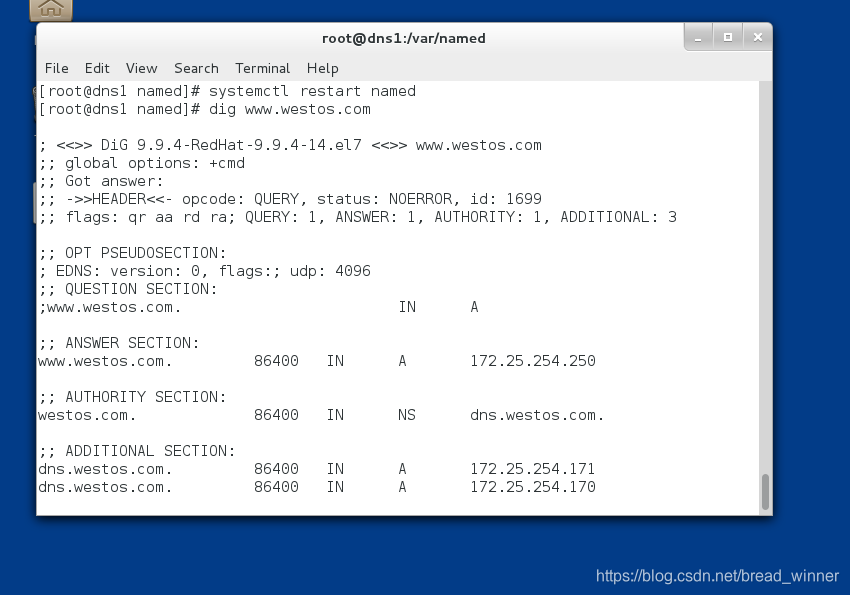
从DNS测试
普通模式 DNS 更新
第一步:在主服务器中进行配置
>##编辑配置文件
>[root@dns0 named]# /etc/named.rfc1912.zones
zone "westos.com" IN {
type master;
file "westos.com.zone";
allow-update { 172.25.254.7; };
also-notify {172.25.254.7; };
};
##修改/var/named的权限,让 “组权限” 可写,否则从属服务器无法上传信息到主服务器
[root@dns0 named]# chmod 770 /var/named
[root@dns0 named]# systemctl restart named
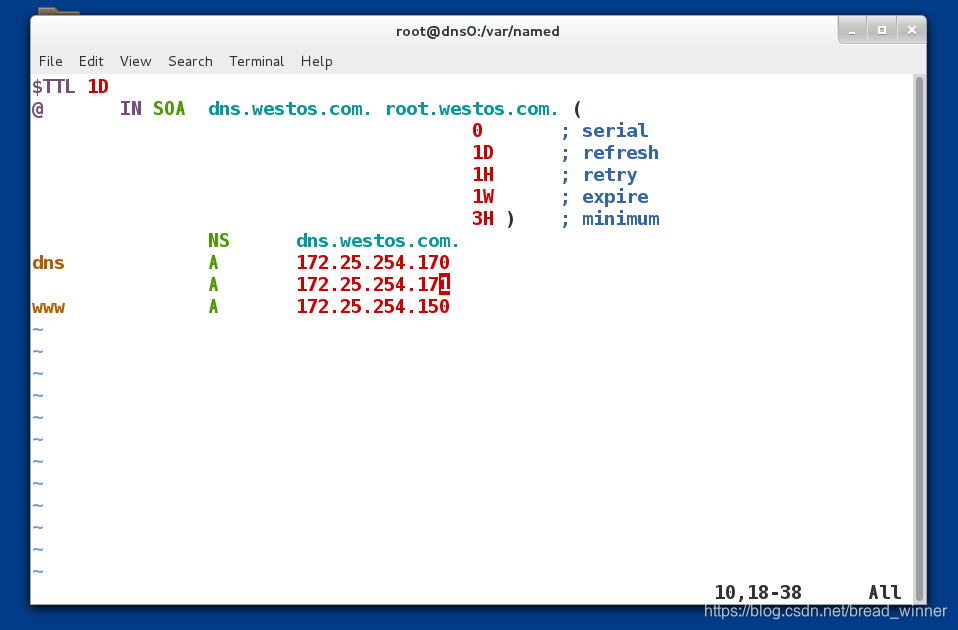
##修改www.westos.com的ip为172.25.254.150
[root@dns0 named]# vim westos.com.zone
$TTL 1D
@ IN SOA dns.westos.com. root.westos.com. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS dns.westos.com.
dns A 172.25.254.170
A 172.25.254.171
www A 172.25.254.150
[root@dns0 named]# systemctl restart named
##查询/var/named/目录下存在的文件
[root@dns0 named]# ls
data named.ca named.localhost slaves
dynamic named.empty named.loopback westos.com.zone
##查询www.westos.com的ip
[root@dns0 named]# dig www.westos.com
; <<>> DiG 9.9.4-RedHat-9.9.4-14.el7 <<>> www.westos.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 43381
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 3
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.westos.com. IN A
;; ANSWER SECTION:
www.westos.com. 86400 IN A 172.25.254.150
;; AUTHORITY SECTION:
westos.com. 86400 IN NS dns.westos.com.
;; ADDITIONAL SECTION:
dns.westos.com. 86400 IN A 172.25.254.171
dns.westos.com. 86400 IN A 172.25.254.170
;; Query time: 0 msec
;; SERVER: 127.0.0.1#53(127.0.0.1)
;; WHEN: Sun Aug 11 11:28:03 EDT 2019
;; MSG SIZE rcvd: 109
第二步:设置从服务器
##在修改前从服务器上www.westos.com的ip为172.25.254.120
[root@dns1 slaves]# dig www.westos.com
; <<>> DiG 9.9.4-RedHat-9.9.4-14.el7 <<>> www.westos.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 39078
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 3
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.westos.com. IN A
;; ANSWER SECTION:
www.westos.com. 86400 IN A 172.25.254.120
;; AUTHORITY SECTION:
westos.com. 86400 IN NS dns.westos.com.
;; ADDITIONAL SECTION:
dns.westos.com. 86400 IN A 172.25.254.171
dns.westos.com. 86400 IN A 172.25.254.170
;; Query time: 0 msec
;; SERVER: 127.0.0.1#53(127.0.0.1)
;; WHEN: Sun Aug 11 11:27:12 EDT 2019
;; MSG SIZE rcvd: 109
##进行更新
[root@dns1 slaves]# nsupdate
> server 172.25.254.170
> update add www.westos.com 86400 A 172.25.254.40
> send
> quit
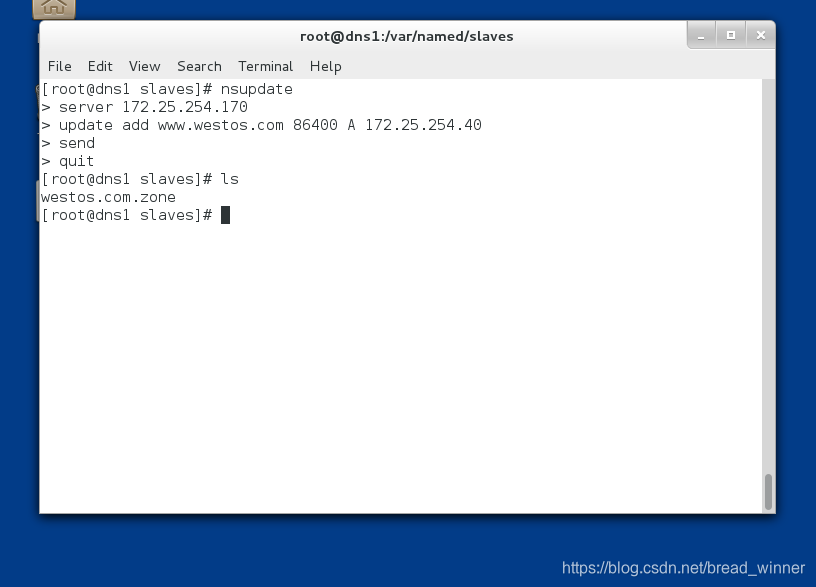
第三步:进行测试
##在主服务器上查看出现.jnl文件.证明更新成功
[root@dns0 named]# ls
data named.ca named.localhost slaves westos.com.zone.jnl
dynamic named.empty named.loopback westos.com.zone
##在从服务器上查看www.westos.com的ip,成功更新
[root@dns1 slaves]# dig www.westos.com
; <<>> DiG 9.9.4-RedHat-9.9.4-14.el7 <<>> www.westos.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 42579
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 3
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.westos.com. IN A
;; ANSWER SECTION:
www.westos.com. 86400 IN A 172.25.254.150
;; AUTHORITY SECTION:
westos.com. 86400 IN NS dns.westos.com.
;; ADDITIONAL SECTION:
dns.westos.com. 86400 IN A 172.25.254.171
dns.westos.com. 86400 IN A 172.25.254.170
;; Query time: 0 msec
;; SERVER: 127.0.0.1#53(127.0.0.1)
;; WHEN: Sun Aug 11 11:29:35 EDT 2019
;; MSG SIZE rcvd: 109
DNS的加密更新
在进行加密实验前需要还原实验内容
第一步:获取秘匙
##在那个文件下,秘匙就会生成在那
[root@dns0 named]# cd /mnt
##生成一个DNS锁跟密钥,类型是HMAC-MD5,长度是128,锁的名字是westos
[root@dns0 mnt]# dnssec-keygen -a HMAC-MD5 -b 128 -n HOST westos
Kwestos.+157+34165
##查看生成的锁和钥匙
[root@dns0 mnt]# ls
Kwestos.+157+34165.key Kwestos.+157+34165.private westos.com.zone
##查看钥匙
[root@dns0 mnt]# cat Kwestos.+157+34165.key
westos. IN KEY 512 3 157 pRh1K0//rom0B6n0JvXiGQ==
##查看锁,会发现两个相同,是因为HMAC-MD5加密为对称加密
[root@dns0 mnt]# cat Kwestos.+157+34165.private
Private-key-format: v1.3
Algorithm: 157 (HMAC_MD5)
Key: pRh1K0//rom0B6n0JvXiGQ==
Bits: AAA=
Created: 20190812115231
Publish: 20190812115231
Activate: 20190812115231
##编辑配置文件
[root@dns0 mnt]# vim /etc/named.rfc1912.zones
zone “westos.com” IN {
type master;
file “westos.com.zone”;
allow-update { key westos; }; #拥有钥匙的主机才可以更新
also-notify { 172.25.254.7; };
};
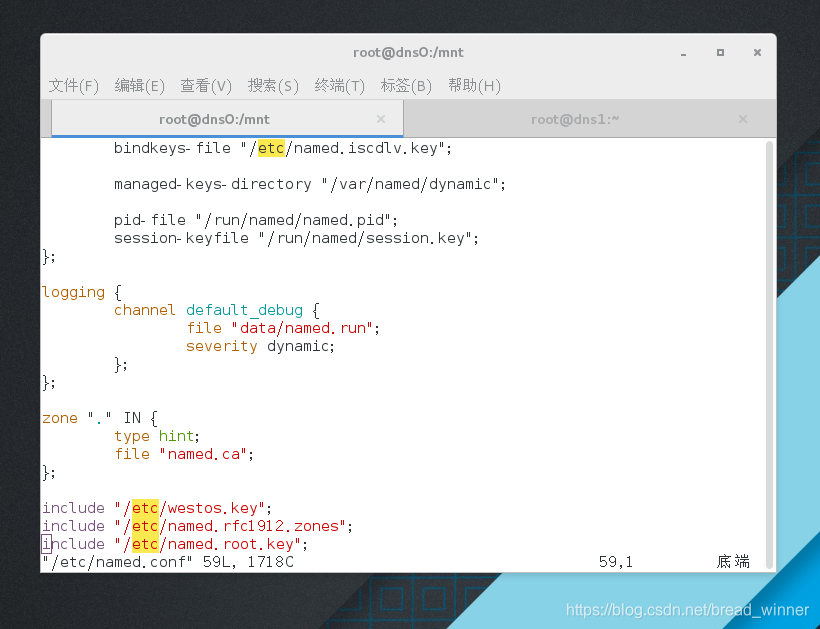
##编辑主配置文件,在最后加上包含的钥匙路径
[root@dns0 mnt]# vim /etc/named.conf
include “/etc/westos.key”;
include “/etc/named.rfc1912.zones”;
include “/etc/named.root.key”;
##将钥匙发送到/etc目录下,注意复制权限
[root@dns0 mnt]# cp -p Kwestos.+157+34165.key /etc/westos.key
##编辑钥匙文件
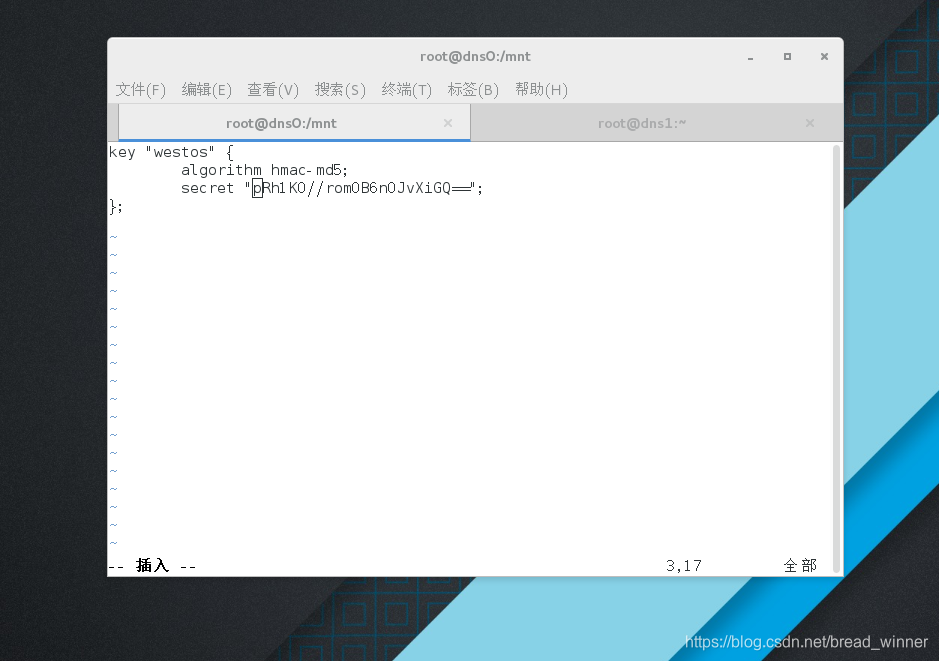
[root@dns0 mnt]# vim /etc/westos.key
key “westos” {
algorithm hmac-md5;
secret “pRh1K0//rom0B6n0JvXiGQ==”;
};
##重启服务
[root@dns0 mnt]# systemctl restart named
##将钥匙送给218这台主机到/mnt目录下
[root@dns0 mnt]# scp Kwestos.+157+34165.* root@172.25.254.7:/mnt/
root@172.25.254.218’s password:
Kwestos.+157+34165.key 100% 50 0.1KB/s 00:00
Kwestos.+157+34165.private 100% 165 0.2KB/s 00:00
##修改www.westos.com的ip地址
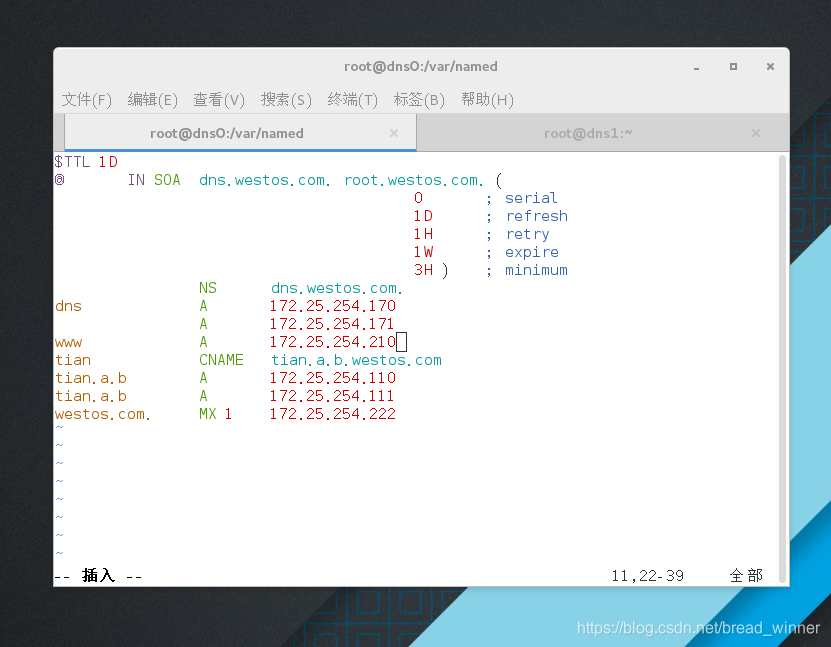
[root@dns0 named]# vim westos.com.zone
##重启服务
[root@dns0 named]# systemctl restart named
##查看是否修改完成
[root@dns0 named]# dig www.westos.com
; <<>> DiG 9.9.4-RedHat-9.9.4-14.el7 <<>> www.westos.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 36777
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 3
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.westos.com. IN A
;; ANSWER SECTION:
www.westos.com. 86400 IN A 172.25.254.210
;; AUTHORITY SECTION:
westos.com. 86400 IN NS dns.westos.com.
;; ADDITIONAL SECTION:
dns.westos.com. 86400 IN A 172.25.254.171
dns.westos.com. 86400 IN A 172.25.254.170
;; Query time: 0 msec
;; SERVER: 127.0.0.1#53(127.0.0.1)
;; WHEN: 一 8月 12 08:22:40 EDT 2019
;; MSG SIZE rcvd: 109
第二步:在从DNS服务端
##在从服务器上查看www.westos.com的ip状态
[root@dns1 mnt]# dig www.westos.com
; <<>> DiG 9.9.4-RedHat-9.9.4-14.el7 <<>> www.westos.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 58490
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 3
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.westos.com. IN A
;; ANSWER SECTION:
www.westos.com. 86400 IN A 172.25.254.150
;; AUTHORITY SECTION:
westos.com. 86400 IN NS dns.westos.com.
;; ADDITIONAL SECTION:
dns.westos.com. 86400 IN A 172.25.254.170
dns.westos.com. 86400 IN A 172.25.254.171
;; Query time: 0 msec
;; SERVER: 127.0.0.1#53(127.0.0.1)
;; WHEN: 一 8月 12 08:31:01 EDT 2019
;; MSG SIZE rcvd: 109
[root@dns1 mnt]# ls
Kwestos.+157+34165.key Kwestos.+157+34165.private
[root@dns1 mnt]# nsupdate -K /mnt/Kwestos.+157+34165.private
nsupdate: illegal option -- K
nsupdate: invalid argument -K
usage: nsupdate [-dD] [-L level] [-l][-g | -o | -y keyname:secret | -k keyfile] [-v] [filename]
[root@dns1 mnt]# nsupdate -k /mnt/Kwestos.+157+34165.private
> server 172.25.254.170
> update add www.westos.com 86400 A 172.25.254.7
> send
> quit
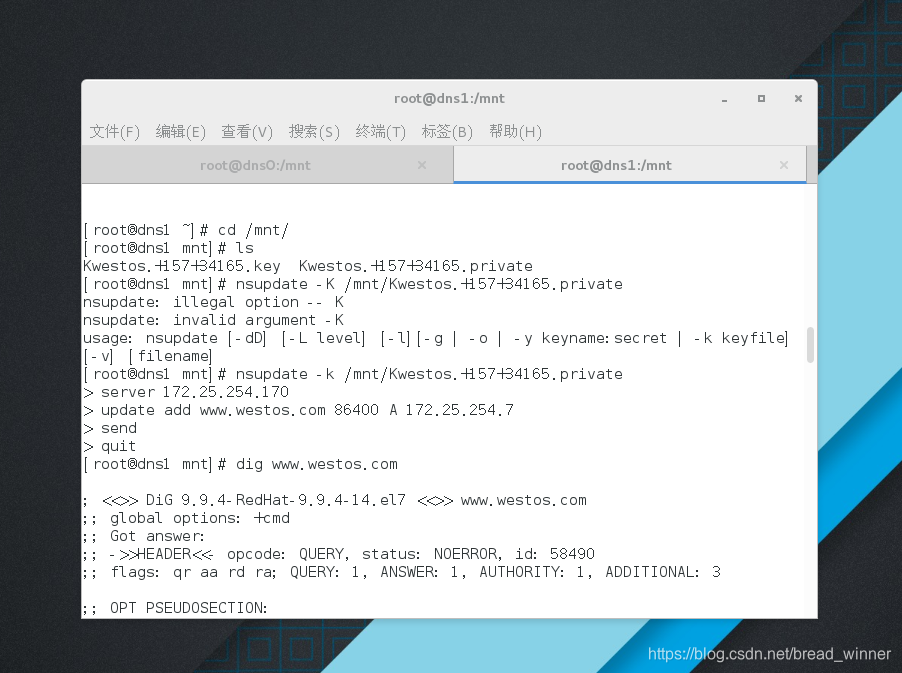
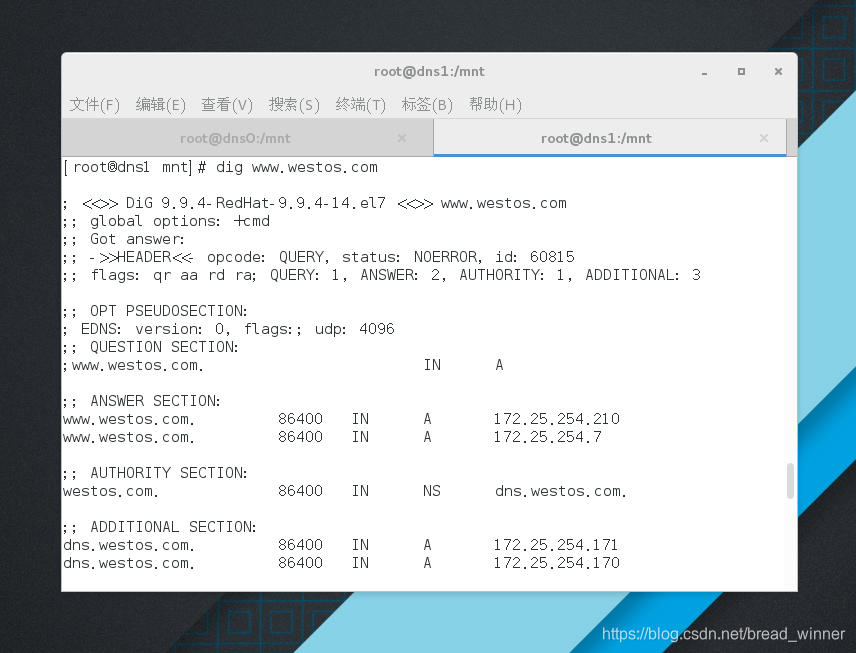
第三步:测试结果
##在有钥匙的从DNS1中进行加密并且成功
[root@dns1 mnt]# dig www.westos.com
; <<>> DiG 9.9.4-RedHat-9.9.4-14.el7 <<>> www.westos.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 52695
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 3
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.westos.com. IN A
;; ANSWER SECTION:
www.westos.com. 86400 IN A 172.25.254.150
;; AUTHORITY SECTION:
westos.com. 86400 IN NS dns.westos.com.
;; ADDITIONAL SECTION:
dns.westos.com. 86400 IN A 172.25.254.171
dns.westos.com. 86400 IN A 172.25.254.170
;; Query time: 0 msec
;; SERVER: 127.0.0.1#53(127.0.0.1)
;; WHEN: 一 8月 12 08:33:28 EDT 2019
;; MSG SIZE rcvd: 109
DHCP 更新DNS 动态域名服务部署(DDNS或者花生壳)
第一步:下载安装dhcp,并搭建dhcp
##安装dhcp服务
[root@dns0 mnt]# yum install dhcp -y
##复制dhcp模板
[>root@dns0 mnt]# cp -p /usr/share/doc/dhcp*/dhcpd.conf.example /etc/dhcp/dhcpd.conf
cp:是否覆盖"/etc/dhcp/dhcpd.conf"? y
[root@dns0 mnt]# vim /etc/dhcp/dhcpd.conf
# dhcpd.conf
#
# Sample configuration file for ISC dhcpd
#
# option definitions common to all supported networks...
option domain-name "westos.com"; ##域名
option domain-name-servers 172.25.254.170; ##系统的dns服务
default-lease-time 600;
max-lease-time 7200;
# Use this to enble / disable dynamic dns updates globally. ##使用此功能可以在全局范围内禁用/禁用动态dns更新
# ddns-update-style interim; ##启用DDNS
# If this DHCP server is the official DHCP server for the local
# network, the authoritative directive should be uncommented.
#authoritative;
# Use this to send dhcp log messages to a different log file (you also
# have to hack syslog.conf to complete the redirection).
log-facility local7;
# No service will be given on this subnet, but declaring it helps the
# DHCP server to understand the network topology.
# This is a very basic subnet declaration.
subnet 172.25.254.0 netmask 255.255.255.0 { ##设置动态分配的网段和子网掩码
range 172.25.254.70 172.25.254.90; ##地址池,分配的ip地址
option routers 172.25.254.70; ##网关
}
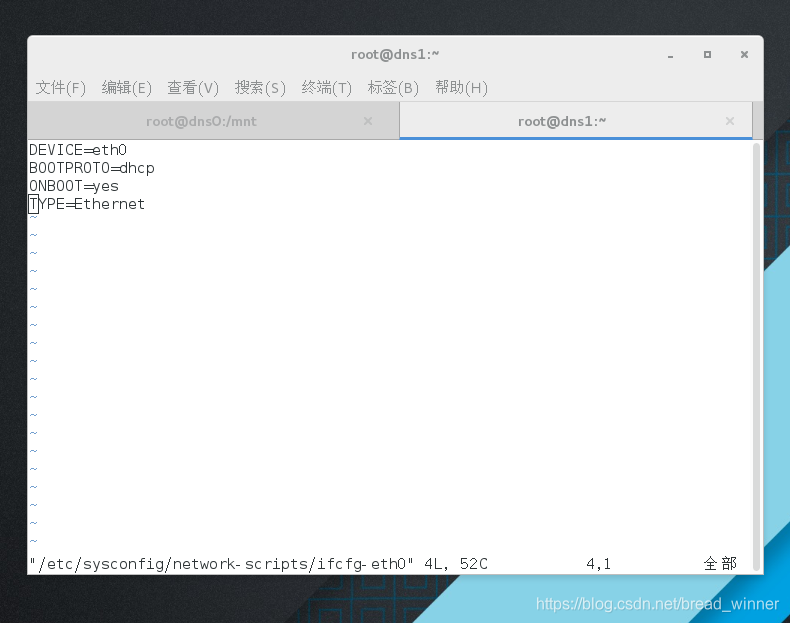
第二步:修改从DNS服务器的ip,使主DNS服务器的dhcp分配给从DNS服务器ip
##:修改从DNS服务器的ip
[root@dns1 ~]# vim /etc/sysconfig/network-scripts/ifcfg-eth0
##重启网络
[root@dns1 ~]# systemctl restart network
##显示ip
[root@dns1 ~]# ip addr show eth0
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 52:54:00:00:46:0b brd ff:ff:ff:ff:ff:ff
inet 172.25.254.71/24 brd 172.25.254.255 scope global dynamic eth0
valid_lft 590sec preferred_lft 590sec
inet6 fe80::5054:ff:fe00:460b/64 scope link
valid_lft forever preferred_lft forever
第三步:修改dhcp主配置文件,使DNS和dhcp向关联,进行动态域名解析(ddns)
##修改dhcp主配置文件
[root@dns0 mnt]# vim /etc/dhcp/dhcpd.conf
# dhcpd.conf
#
# Sample configuration file for ISC dhcpd
#
# option definitions common to all supported networks...
option domain-name "westos.com";
option domain-name-servers 172.25.254.170;
default-lease-time 600;
max-lease-time 7200;
# Use this to enble / disable dynamic dns updates globally.
ddns-update-style interim; ## 打开ddns花生壳服务
# If this DHCP server is the official DHCP server for the local
# network, the authoritative directive should be uncommented.
#authoritative;
# Use this to send dhcp log messages to a different log file (you also
# have to hack syslog.conf to complete the redirection).
log-facility local7;
# No service will be given on this subnet, but declaring it helps the
# DHCP server to understand the network topology.
# This is a very basic subnet declaration.
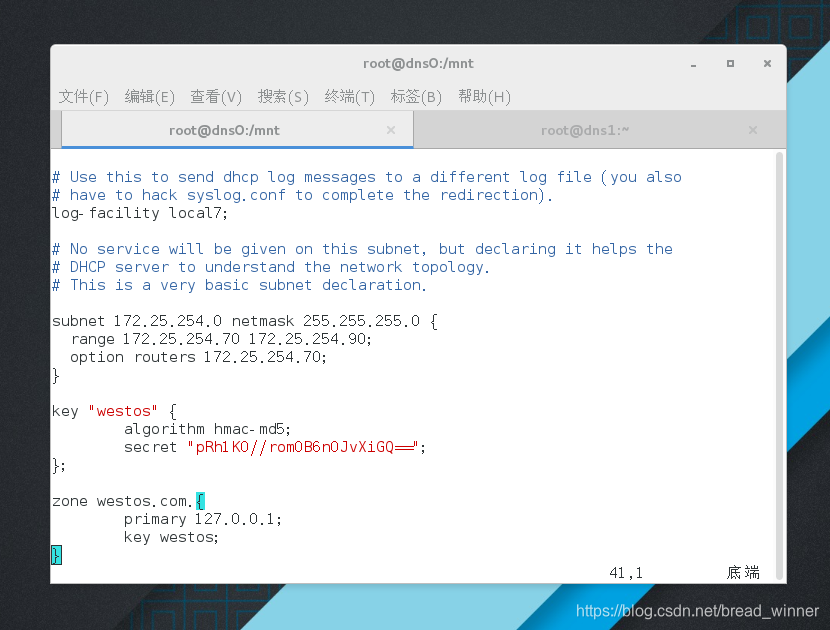
subnet 172.25.254.0 netmask 255.255.255.0 {
range 172.25.254.70 172.25.254.90;
option routers 172.25.254.70;
}
key "westos" { #dns 服务密钥,上个实验的加密密钥
algorithm hmac-md5;
secret "pRh1K0//rom0B6n0JvXiGQ==";
};
zone westos.com.{ #dns服务区域
primary 127.0. #允许哪个主机进行动态同步
key westos; #通过密钥进行
}
## 重启服务
[root@dns0 mnt]# systemctl restart dhcpd.service
第四步:进行测试
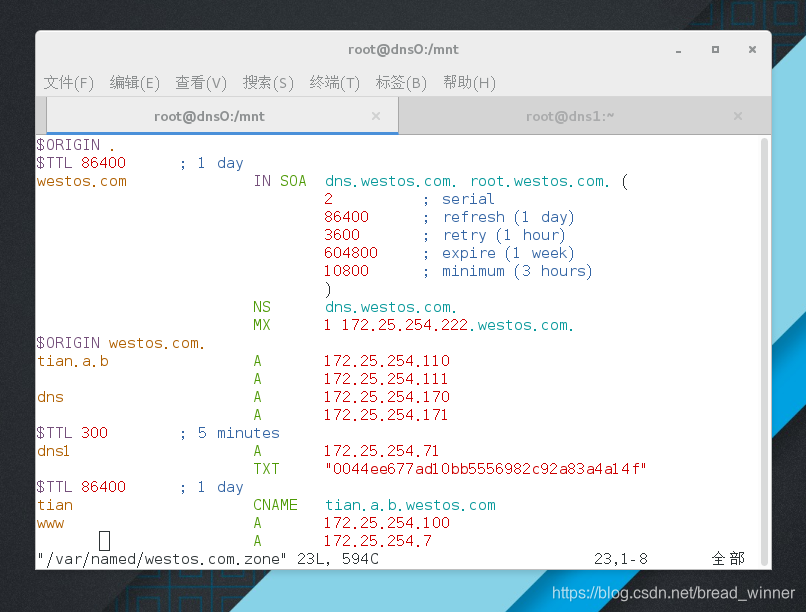
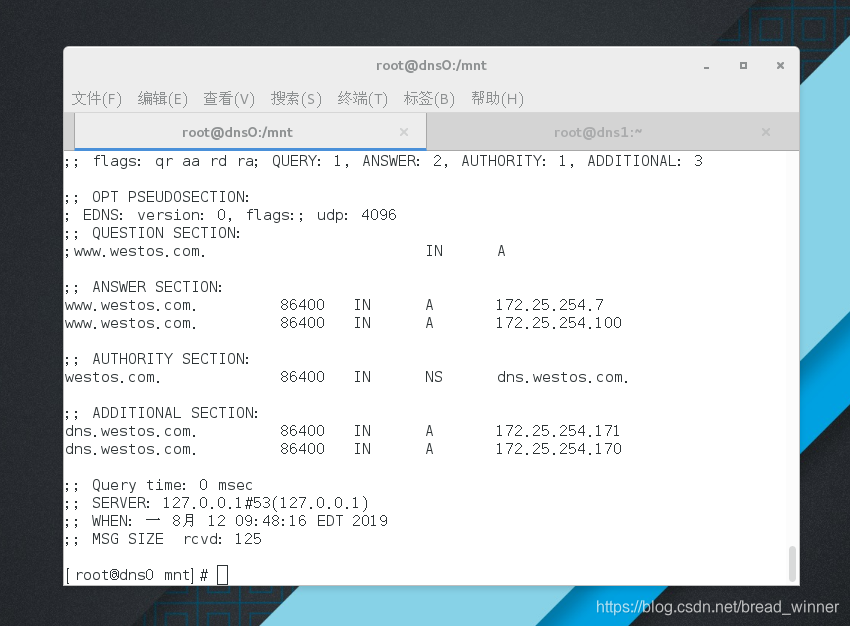
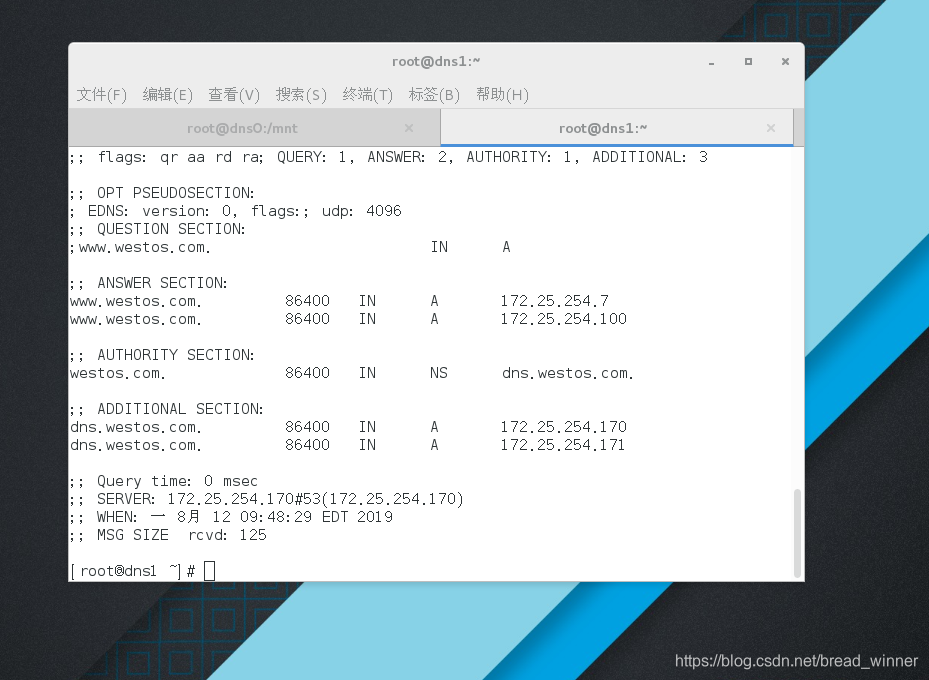
修改主dns中www.westos.com的ip地址为100
在主dns中测试www.westos.com的ip
在从dns上测试www.westos.com的ip地址





 本文详细介绍了如何在Linux系统中搭建DNS集群,包括主从DNS服务器的配置,以及DNS的普通模式更新和加密更新。此外,还讲解了DHCP更新DNS动态域名服务(DDNS)的部署过程,包括安装DHCP服务,配置DHCP以实现动态域名解析。
本文详细介绍了如何在Linux系统中搭建DNS集群,包括主从DNS服务器的配置,以及DNS的普通模式更新和加密更新。此外,还讲解了DHCP更新DNS动态域名服务(DDNS)的部署过程,包括安装DHCP服务,配置DHCP以实现动态域名解析。
















 338
338

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








