SSH带外管理
一、概述
ssh服务,一种远程管理连接工具,在CentOS7系统中默认安装并开机自启的。
SSH(Secure Shell)是一种安全通道协议,主要用来实现字符界面的远程登录,远程复制等功能。
监听tcp的22号端口。软件包名称:openssh
配置文件目录:/etc/ssh,sshd_config 服务端配置文件;ssh_config 客户端配置文件。
客户端提供:ssh、scp、sftp命令
服务端提供:sftp服务、ssh服务
二、 配置文件
服务端配置文件: sshd_config
Port 22 #监听端口 netstat -antpu
AddressFamily any #ip地址版本
ListenAddress 0.0.0.0 #监听地址,ipv4
ListenAddress :: #监听地址,ipv6
PermitRootLogin yes #是否允许root用户登录 (在安全架构里面设置成 no)
MaxAuthTries 6 #重新连接最大次数
MaxSessions 10 #建立不同用户的会话的最大个数 (最多十次连接)
PubkeyAuthentication yes #是否启用公钥对验证登录
AuthorizedKeysFile .ssh/authorized_keys #存储客户端公钥信息的文件
PasswordAuthentication yes #是否启用密码验证登录
PermitEmptyPasswords no #是否允许空白密码登录
UsePAM yes #启用系统用户及密码进行验证登录
UseDNS no #是否启用ssh内部的解析,会影响连接速度
X11Forwarding yes #是否进行图形界面转发 (消耗资源,不建议)
客户端配置文件: ssh_config,设置ssh命令连接的关键配置
Port 22 #设置ssh命令连接的默认端口
三、命令解析
###远程登录命令###
###语法:####
ssh [选项] [username@]ssh服务器的监听IP地址或者主机名(使用主机名时,保证客户端能够解析主机名)
####选项:######
-p port 指定连接服务器的监听端口
###远程拷贝命令####
###语法:####
##将本机的文件拷贝到远程主机##
scp 本机的文件路径 [username@]ssh服务器的监听IP地址或者主机名:/远程主机存储路径
##将远程主机的文件拷贝到本机##
scp [username@]ssh服务器的监听IP地址或者主机名:/远程主机存储路径 本机的文件路径
###sftp服务登录命令###
sftp [选项] [username@]ssh服务器的监听IP地址或者主机名(使用主机名时,保证客户端能够解析主机名)
sftp命令 ?:查看所有选项
sftp 登录远程主机
[root@localhost ~]# sftp root@192.168.157.129
root@192.168.157.129's password:
Connected to 192.168.157.129.
sftp>
sftp> get f1 #下载到本机
Fetching /root/f1 to f1
sftp> exit
#在本机上查看
[root@localhost ~]# ls
anaconda-ks.cfg info.sh 公共 视频 文档 音乐
f1 initial-setup-ks.cfg 模板 图片 下载 桌面
四、登录方式配置
1、用户名密码登录
默认方式,直接可以使用
2、公钥验证登录
密码学基础:
| 概念 | 解析 |
|---|---|
| 对称加密 | 双方采用相同的秘钥,安全性较低 |
| 非对称加密 | 双方采用不同的秘钥,安全性较高 |
| 公钥 | 大家都可以知道的秘钥。 |
| 私钥 | 只有自己知道的秘钥。能够证明自己的身份信息 |
注意:公钥和私钥不能相互推导!!!
公钥与私钥之间能够相互解密!!!
数据加密:
使用对端的公钥加密,接收端收到数据后,使用自己的私钥解密。作用是保证数据完整性。
数字签名:
私用自己的私钥加密,接收端收到数据后,使用发送端的公钥解密。作用是保证发送者的身份唯一性。
ssh客户端生成密钥对
###生成密钥对的命令###
ssh-keygen ,默认是交互式
放在 .ssh
###常用选项:####
-t : 指定秘钥算法
-N : 指定秘钥短语
-f : 指定秘钥存储路径
[root@s1 .ssh]# ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
###非交互生成密钥对####
[zhx1@s1 ~]$ ssh-keygen -t rsa -N '' -f ~/.ssh/id_rsa
###默认保存到当前执行该命令的用户家目录中的.ssh目录#####
[root@s1 .ssh]# ls
id_rsa id_rsa.pub
###id_rsa: 私钥;id_rsa.pub: 公钥###
###拷贝公钥命令###
ssh-copy-id
###ssh命令的特殊用法:远程执行ssh服务器的指令####
[root@s1 .ssh]# ssh 192.168.115.128 ip a
##注意:不能执行ssh-copy-id命令####
四、实操
客户端使用user1用户,并且以服务端的用户user2的身份登录,使用公钥对验证登录。
实操
一、
点击虚拟机编辑,虚拟网络编辑器,添加网络仅主机模式
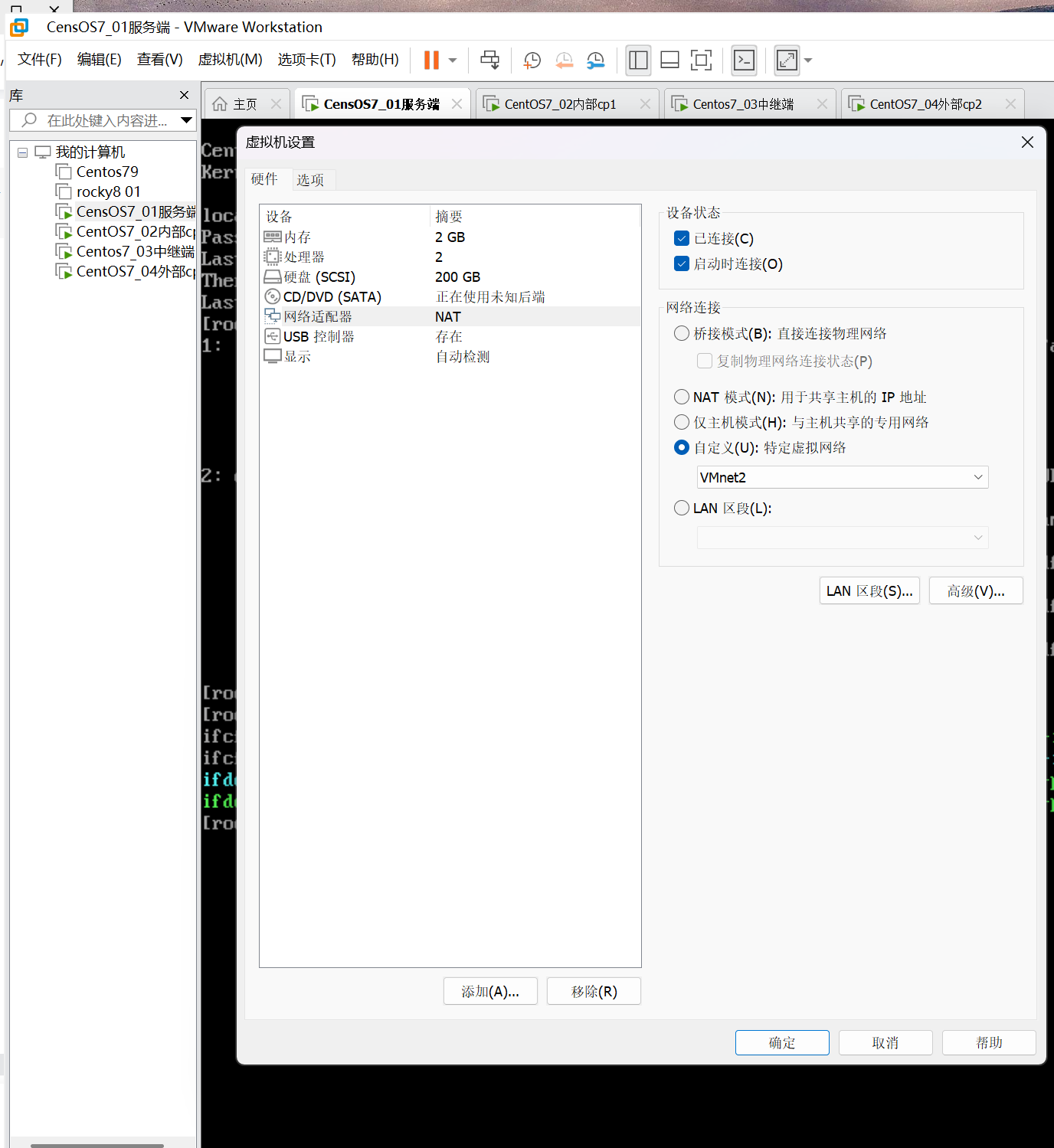
设置虚拟机01 、02,将网络配置改为仅主机模式
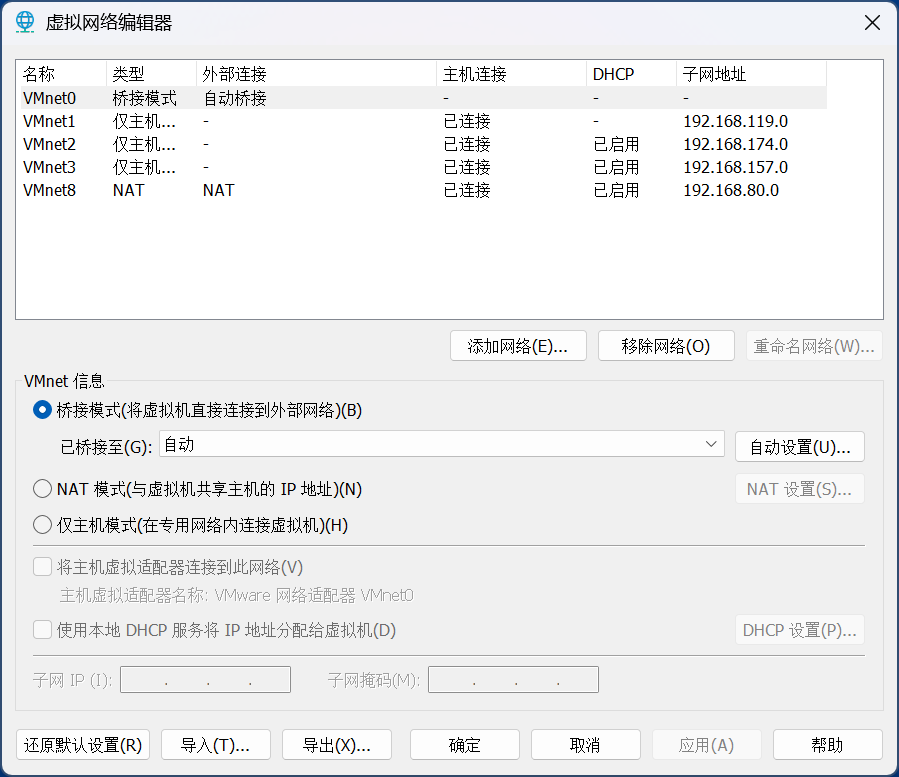
二、
1、查看虚拟机01、02的IP地址
2、在02虚拟机上抓包
#在01PC上
[root@localhost ~]# ssh root@192.168.157.129
The authenticity of host '192.168.157.129 (192.168.157.129)' can't be established.
ECDSA key fingerprint is SHA256:HY3llJ4kOLjqMKZPvGHM3EOUbald4qRn1FS/SDFLi5w.
ECDSA key fingerprint is MD5:84:71:3e:4f:27:c8:b0:0c:3e:57:2f:68:a2:81:d2:56.
Are you sure you want to continue connecting (yes/no)? y
Please type 'yes' or 'no': yes
Warning: Permanently added '192.168.157.129' (ECDSA) to the list of known hosts.
root@192.168.157.129's password:
Last failed login: Thu Jun 19 18:09:57 CST 2025 from 192.168.157.130 on ssh:notty
There was 1 failed login attempt since the last successful login.
Last login: Thu Jun 19 17:31:13 2025
#在02PC上抓包
[root@localhost ~]# tcpdump -i ens34
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on ens34, link-type EN10MB (Ethernet), capture size 262144 bytes
17:53:14.893333 ARP, Request who-has localhost.localdomain tell 192.168.157.128, length 46
17:53:14.893360 ARP, Reply localhost.localdomain is-at 00:0c:29:33:35:c1 (oui Unknown), length 28
17:53:14.893660 IP localhost.localdomain.49003 > 192.168.157.1.domain: 42155+ PTR? 128.157.168.192.in-addr.arpa. (46)
17:53:14.893720 IP 192.168.157.128.38438 > localhost.localdomain.ssh: Flags [S], seq 2657263878, win 29200, options [mss 1460,sackOK,TS val 1461371 ecr 0,nop,wscale 7], length 0
17:53:14.893755 IP localhost.localdomain.ssh > 192.168.157.128.38438: Flags [S.], seq 1864691862, ack 2657263879, win 28960, options [mss 1460,sackOK,TS val 1215226 ecr 1461371,nop,wscale 7], length 0
17:53:14.894206 IP 192.168.157.128.38438 > localhost.localdomain.ssh: Flags [.], ack 1, win 229, options [nop,nop,TS val 1461372 ecr 1215226], length 0
17:53:14.897140 IP 192.168.157.128.38438 > localhost.localdomain.ssh: Flags [P.], seq 1:22, ack 1, win 229, options [nop,nop,TS val 1461375 ecr 1215226], length 21
# 查看01PC IP地址与02CP 是否一致
[root@localhost network-scripts]# ifconfig
ens34: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.157.129 netmask 255.255.255.0 broadcast 192.168.157.255
inet6 fe80::f6a4:122b:631d:fcd5 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:33:35:c1 txqueuelen 1000 (Ethernet)
RX packets 644 bytes 61209 (59.7 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 285 bytes 58087 (56.7 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
3、执行命令返回结果,不登录
[root@localhost network-scripts]# exit
登出
Connection to 192.168.157.129 closed.
[root@localhost ~]# ssh root@192.168.157.129 ifconfig
root@192.168.157.129's password:
ens34: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.157.129 netmask 255.255.255.0 broadcast 192.168.157.255
inet6 fe80::f6a4:122b:631d:fcd5 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:33:35:c1 txqueuelen 1000 (Ethernet)
RX packets 682 bytes 66349 (64.7 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 324 bytes 65590 (64.0 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 16192 bytes 1413856 (1.3 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 16192 bytes 1413856 (1.3 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 192.168.122.1 netmask 255.255.255.0 broadcast 192.168.122.255
ether 52:54:00:35:14:f7 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
4、用scp命令远程拷贝
#在01CP上写个脚本
[root@localhost ~]# vim info.sh
#!/bin/bash
free -m
df -Th
~
[root@localhost ~]# chmod +x info.sh
#用户一定要具有权限,不一定是root :后面跟存放路径
[root@localhost ~]# scp info.sh root@192.168.157.129:/root
root@192.168.157.129's password:
info.sh
5、在02CP上查看是否存在脚本
[root@localhost ~]# ls
anaconda-ks.cfg info.sh initial-setup-ks.cfg 公共 模板 视频 图片 文档 下载 音乐
6、在01CP上通过ssh实行脚本
[root@localhost ~]# ssh root@192.168.157.129 /root/info.sh
root@192.168.157.129's password:
total used free shared buff/cache available
Mem: 1819 1049 69 13 701 591
Swap: 2047 1 2046
文件系统 类型 容量 已用 可用 已用% 挂载点
devtmpfs devtmpfs 894M 0 894M 0% /dev
tmpfs tmpfs 910M 0 910M 0% /dev/shm
tmpfs tmpfs 910M 11M 900M 2% /run
tmpfs tmpfs 910M 0 910M 0% /sys/fs/cgroup
/dev/mapper/centos-root xfs 39G 4.6G 34G 12% /
/dev/sda1 xfs 1014M 185M 830M 19% /boot
/dev/mapper/centos-home xfs 19G 38M 19G 1% /home
tmpfs tmpfs 182M 28K 182M 1% /run/user/0
7、本机拷贝远程主机文件从02CP复制到01Cp 要知道目标主机的路径
[root@localhost ~]# scp info.sh root@192.168.157.129:/root/info.sh /opt
root@192.168.157.129's password:
info.sh 100% 90 83.7KB/s 00:00
[root@localhost ~]# ls /opt/
info.sh rh
二、生成密钥对
1、服务机01创建用户zhangsan,并设置密码;远程02PC创建用户lisi
2、交互式生成,ssh-keygen
[zhangsan@localhost ~]$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/zhangsan/.ssh/id_rsa): #(当前私钥存储路径)
Created directory '/home/zhangsan/.ssh'.
Enter passphrase (empty for no passphrase): #(输入一个密码短语)
Enter same passphrase again: #(确认密码短语)
Your identification has been saved in /home/zhangsan/.ssh/id_rsa.
Your public key has been saved in /home/zhangsan/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:Q/PqrQwU8P4bmGMQWIsc0w77C4RV3ukBHyBZoZ8GcCc zhangsan@localhost.localdomain
The key's randomart image is:
+---[RSA 2048]----+
|. E=Xo. |
| ++%.B o |
| o*++ B o |
|. oo.= + o |
| . .= + S . |
| ...o + o |
| . .* + |
| .. = + |
| =.. |
+----[SHA256]-----+
[zhangsan@localhost ~]$ cd .ssh/
[zhangsan@localhost .ssh]$ ls
id_rsa id_rsa.pub
id_rsa #私钥
id_rsa.pub #公钥
3、非交互式生成
ssh-keygen -t rsa -N ' ' -f id_rsa
#生成一次改变一次 -N 生成一个新的短语
[zhangsan@localhost .ssh]$ ssh-keygen -N '' -f id_rsa
Generating public/private rsa key pair.
id_rsa already exists.
Overwrite (y/n)? y
Your identification has been saved in id_rsa.
Your public key has been saved in id_rsa.pub.
The key fingerprint is:
SHA256:e7FLfYFM79shahFHUgQWotxv7DXtfQ/Z5VAy0+XNQrY zhangsan@localhost.localdomain
The key's randomart image is:
+---[RSA 2048]----+
| . +=oo .|
| . o o. + =o|
| o . + E *|
| o+ +.* |
| S .+=o+..|
| .o=..o*o|
| . +.o.=o=|
| o o...++|
| o. . o|
+----[SHA256]-----+
#-P 指定一个密码短语
ssh-keygen -t rsa -P ' ' -f id_rsa
[zhangsan@localhost .ssh]$ ssh-keygen -P '' -f id_rsa
Generating public/private rsa key pair.
id_rsa already exists.
Overwrite (y/n)? y
Your identification has been saved in id_rsa.
Your public key has been saved in id_rsa.pub.
The key fingerprint is:
SHA256:qzFQxQKJMHuOD+4UpB0xlcszBK9gxbjgfnfMYDOgH8g zhangsan@localhost.localdomain
The key's randomart image is:
+---[RSA 2048]----+
|o.*=o+ .. |
|.+o*+ ... |
|*o*oo... |
|+E +=* |
|=.= +o* S |
|.+.o o + . |
| oo . + . |
|o + |
| . . |
+----[SHA256]-----+
4、把密钥对拷给lisi 使用ssh-copy-id
#路径不用指,默认写好了
[root@localhost ~]# su - zhangsan
上一次登录:四 6月 19 13:37:03 CST 2025pts/2 上
[zhangsan@localhost ~]$ ssh-copy-id lisi@192.168.157.129
/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/home/zhangsan/.ssh/id_rsa.pub"
The authenticity of host '192.168.157.129 (192.168.157.129)' can't be established.
ECDSA key fingerprint is SHA256:HY3llJ4kOLjqMKZPvGHM3EOUbald4qRn1FS/SDFLi5w.
ECDSA key fingerprint is MD5:84:71:3e:4f:27:c8:b0:0c:3e:57:2f:68:a2:81:d2:56.
Are you sure you want to continue connecting (yes/no)? y
Please type 'yes' or 'no': yes
/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
lisi@192.168.157.129's password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh 'lisi@192.168.157.129'"
and check to make sure that only the key(s) you wanted were added.
##用远程02PC 切换到lisi用户查看生成的文件
[root@localhost ~]# su - lisi
[lisi@localhost ~]$ cd .ssh/
[lisi@localhost .ssh]$ ls
authorized_keys
[lisi@localhost .ssh]$ cat authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDGIFH9ZKmT2MsPLGK9f1Gbe8/5b21oaH36qWe1zGYqU2ypcAoCpXAaYw4dYuqxttUrraOP7AHIwl41THMKkKm2094FbkUuu41jE1CGsr3HpHF7EHNn5W/OQi9YnnLbvwNW5mk3DOi7hPSvtkwWk8f0yUI6SM3bYnBp6F2C2gxgj6s/+MsgUHpIDQ68nj1clWBn0L1OD71oJhtYFupoSICRdCPc+48KBVlPurJL2yg0sPdYzZOhD1wrMFLVnGDXnzTR7i9ESEk+spnE3slDAdftuTPSx1rMymb0csQm224M9DYKR3Q6J7riru25MVMsF7fZKwIfSZ9Jh5PAQjiUyENB zhangsan@localhost.localdomain
5、zhangsan用户可以免密登录到lisi用户
[zhangsan@localhost ~]$ ssh lisi@192.168.157.129
Last login: Fri Jun 20 00:11:07 2025




















 3841
3841

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








