1. ezcrypt(史)
pyinstxtractor.py解包exe,然后pycdc反编译NSSCTF.pyc
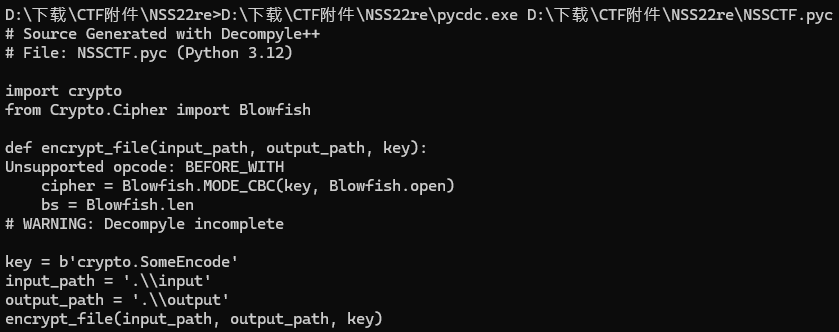
得到的源码并不完整,但是重要的部分已经有了,就是一个blowfish加密
但是密钥是crypto.SomeEncode,这并不是字面意义的字符串,而是引用的其他文件
NSSCTF.exe_extracted可以找到可疑文件crypto.cpython.pyc

是一个魔改的TEA(这里出题逻辑有问题,按给的代码逻辑SomeEncode是v加密得到的,但实际上却要我们解密得到)
#define _CRT_SECURE_NO_WARNINGS
#include<stdio.h>
int main()
{
unsigned int enc[5] =
{
1396533857,
0xCC8AE275,
0x89FB8A63,
940694833
};
unsigned int key[4] =
{
17,
34,
51,
68
};
int i, j;
for (i = 0; i < 4; i += 2)
{
unsigned int v0 = enc[i], v1 = enc[i + 1], sum = 0xC6EF3720;
unsigned int delta = 0x9e3779b9;
unsigned int k0 = key[0], k1 = key[1], k2 = key[2], k3 = key[3];
for (j = 0; j < 32; j++)
{
v1 -= ((v0 << 3) + k2 ^ v0 + sum ^ (v0 >> 4) + k3 ^ 2310) & 0xFFFFFFFF;
v0 -= ((v1 << 3) + k0 ^ v1 + sum ^ (v1 >> 4) + k1 ^ 596) & 0xFFFFFFFF;
sum -= delta & 0xFFFFFFFF;
}
enc[i] = v0; enc[i + 1] = v1;
}
for (i = 0; i < 4; i++)
{
printf("%u ", enc[i]);
}
printf("%s", enc);//sNzEveRsjorPstce
return 0;
}
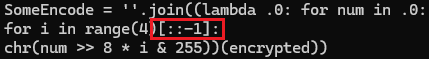
这里有个每四位一个逆序(第三行就是ASCII转字符的意思),解出来手动改一下吧,就是 EzNssRevProjects
#ezcrypt wp
from Crypto.Cipher import Blowfish
from Crypto.Util.Padding import unpad
from Crypto.Random import get_random_bytes
def decrypt_file(input_path, output_path, key):
with open(input_path, 'rb') as f:
# 读取整个文件内容,包括IV和密文
data = f.read()
# 分割IV和密文
iv = data[:Blowfish.block_size]
print(iv)
ciphertext = data[Blowfish.block_size:]
print(ciphertext)
# 验证密钥长度
#if len(key) != Blowfish.key_size:
# raise ValueError("Invalid key size for Blowfish. It must be exactly 8 bytes long.")
# 创建一个新的Blowfish cipher对象,并设置密钥和IV
cipher = Blowfish.new(key, Blowfish.MODE_CBC, iv=iv)
# 解密数据
plaintext = (cipher.decrypt(ciphertext), Blowfish.block_size)
print(plaintext[0])
# 将解密后的数据写入输出文件
with open(output_path, 'wb') as f:
f.write(plaintext[0])
key = b'EzNssRevProjects'
input_path = 'D:\\下载\\CTF附件\\NSS22re\\output'
output_path = 'D:\\下载\\CTF附件\\NSS22re\\flag'
decrypt_file(input_path, output_path, key)密钥解码得到一个二进制文件,IDA打开是个虚拟机(笑)

动调不出来(这里逻辑也莫名其妙,明明这个代码就应该能跑出flag,但实际上是要你把代码反过来写)
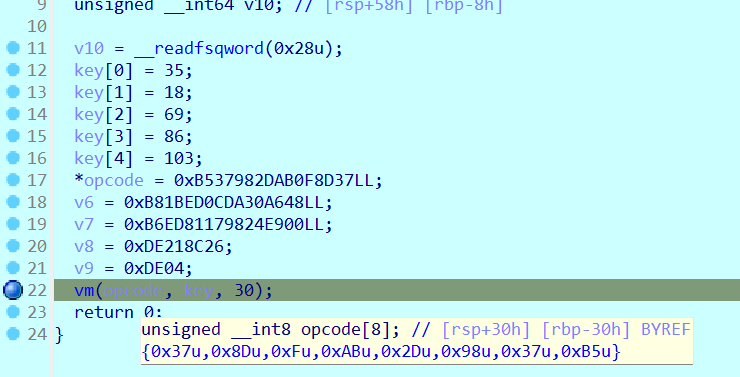
硬做,动调取出opcode,key





 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章


















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








