36380-032135642X_ak.pdf (nyit.edu)
机密性作业:
Why is it meaningless to have compartments at the UNCLASSIFIED level (such as (UNCLASSIFIED, { NUC }) and ( UNCLASSIFIED, { EUR }))?
- 为什么unclassified级别中包含类别是完全没有意义的【例如(unclassified,{NUC})】?
当某些东西未被分类时,对它的访问是不受限制的,即unclassified是公开级的文件,所有的人都可以获取到,包含某类别后,即使这个人无法获取其他类别的文件,但因为是公开级的,其他人也可与其共享这些他无法获取的文件,因此对于公开级设定类别是完全没有意义的。
原文:Compartments are used to restrict access at a particular level or levels. But when something is UNCLASSIFIED, access to it is unrestricted. Hence having compartments at the UNCLASSIFIED level serves no purpose, and is meaningless.
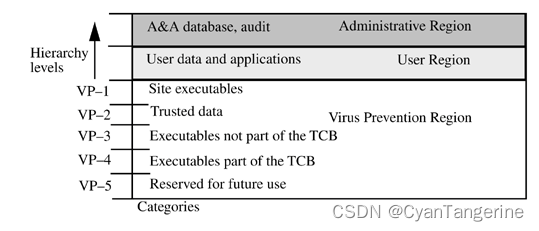
- 2.在DG/UX系统中,为什么病毒防护区低于用户区?In the DG/UX system, why is the virus prevention region below the user region?
在DG/UX系统中,病毒防护区域位于用户区域之下,是为了以防止任何用户程序在包含系统或站点可执行文件的区域中更改(写入)代码或数据。例如,如果用户在用户区域中加载并执行程序,DG/UX系统不允许用户程序写入到病毒防护区,因此用户区域的病毒无法更改病毒防护区中的可执行文件或其他文件,由于这样的禁止写操作的规则,该程序无法更改系统可执行文件。正因如此,病毒只能在用户区域内传播。
原文:In the DG/UX system, the virus prevention region is below the user region to prevent any user programs from altering (writing) code or data in a region that contains system or site executables. For example, if a user loads and executes a program in the user region, that program cannot alter system executables because of the rule forbidding writes down. Hence computer viruses can spread only within the user region. Note that the DG/UX system disallows writes up, so the computer virus at the user region could not alter executables or other files in the administrative region. (In a strict implementation of the Bell-LaPadula model, they would be able to write to information in this region.)
- 3.在DG/UX系统中,为什么管理区高于用户区?In the DG/UX system, why is the administrative region above the user region?
在DG/UX系统中,管理区域位于用户区域之上,以防止用户读取存储在该级别的信息。例如,“标识和授权”数据库包含用户不应看到的敏感信息——身份验证信息。与Bell-LaPadula模型不同的是,DG/UX系统也不允许用户在该级别的区域写入,因此用户不能在该区域中附加或更改信息,但在严格执行Bell-LaPadula模型的情况下,用户将能够写入该区域的信息。
原文:In the DG/UX system, the administrative region is above the user region to prevent the users from reading information stored at that level. For example, the Identification and Authorization database contains sensitive information, such as authentication information, that users should notbe able to see. Note that the DG/UX system also disallows writes up, so users cannot append to or alter information in this region. (In a strict implementation of the Bell-LaPadula model, they would be able to write to information in this region.)
完整性作业:
In the Clark-Wilson model, must the TPs be executed serially, or can they be executed in parallel? If the former, why; if the latter, what constraints must be placed on their execution?
- 在Clark-Wilson模型中,是否必须顺序执行TP,或者是否可以并行执行TP?如果是前者,说明原因;如果是后者,那么在执行时需要设置何种约束?
在Clark Wilson基本模型中必须顺序执行,因为对于如何处理对同一数据的并发访问,没有标准化规则,这是数据库的常见问题。但只要满足伯恩斯坦条件,TP可以并行执行。并行执行TP的唯一问题是当两个TP试图同时更新或写入相同的CDI时。伯恩斯坦条件指出,多个进程可以同时读取一个对象,但最多只能有一个进程写入一个对象。在此期间,没有进程可以读取该对象。这确保了对象中的值是一致的。类似地,如果两个TP试图同时更改CDI,则存在导致结果不确定的竞争条件;如果一个TP正在写入对象,而其他TP正在同时读取对象,则读取的值可能不一致。
因此,在大多数商务系统中, TP操作都是按顺序执行的。例如,访问操作:登录、更改金额、打印收据和注销,这些无法并行执行,而顺序执行满足商务业务的需求和一致性。但某些操作可以并行执行:例如转账:发起方金额减少,接收方金额增加。但完整性要求其必须是一个原子操作,因此在两个操作完成后,它们将被提交到数据库,否则它们不一致。
原文:The TPs can be executed in parallel, provided the Bernstein conditions are met. The only problem with executing TPs in parallel occurs when two of them try to update or write the same CDI at the same time. The Bernstein conditions state that multiple processes may read an object at the same time, but at most one process may write to an object and, during that time, no process may read the object. This ensures that the values in the object are consistent. Similarly, if two TPs try to alter a CDI simultaneously, there is a race condition rendering the result indeterminate; if one TP is writing the object and others are reading it at the same time, the vaules read may be inconsistent.
In business systems, most TP operations are executed sequentially. For example, access operations: log in, change the amount of money, print receipts, and log out. Cannot be executed in parallel. Sequential execution meets business requirements and meets consistency.
Some operations can be performed in parallel. For example, transfer: one process reduces the amount of money, and one process increases the amount of money. The integrity requirement must be an atomic operation, so after the two operations are completed, they are submitted to the database, otherwise they are not consistent.
参考:Foundations of Computer Security - Lecture 24: The Clark-Wilson Model (utexas.edu)(https://www.cs.utexas.edu/~byoung/cs361/lecture24-4up.pdf)
http://en.wikipedia.org/wiki/Isolation_database_systemsComputer System Security 2018【5】Chapter 9: Integrity - Katastroshttp://en.wikipedia.org/wiki/Isolation_database_systems
2、可以将ER1和ER2压缩为一个关系。为什么Clark-Wilson模型不这么做?
The relations certified (see ER1) and allowed (see ER2) can be collapsed into a single relation. Please do so and state the new relation. Why doesn't the Clark-Wilson model do this?
实施规则ER1:系统必须维护所有的证明关系,且必须保证只有经过证明可以运行该CDI的TP才能操作该CDI。
实施规则ER2:系统必须将用户与每个TP及一组相关的CDI关联起来。TP可以代表相关用户来访问这些CDI。如果没有与特定的TP及CDI相关联,那么这个TP将不能代表那个用户对CDI进行访问。
这两者不能结合,因为它是两步关系,即TP操作CDI,用户使用TP操作自己的CDI。如果结合在一起,意味着一步到位的操作,有些内涵没有明确表达:新关系将包含形式(user,TP,{CDI1,…,CDIn})的元组,这意味着用户用户可以对受约束的数据项CDI1、…,CDIn执行事务过程TP。一个问题是如何处理TP可以操作的CDI,但不允许任何用户在这些CDI上执行该TP。一种方法是定义一个名为“nobody”的伪用户,并将这些CDI放入一个元组中,用户名为“none”。
“允许”和“认证”的关系根本不同。ER1定义了事务过程可以对哪些(类型)实体进行操作,ER2定义了谁可以将事务过程应用于特定的受约束数据项。如果它们合二为一,则需要两种不同的机制来执行该规则。因此,将它们分离可以使模型保持简单和干净。
原文:The new relation would contain tuples of the form (user, TP, { CDI1, …, CDIn } ), meaning that the user user could execute the transaction procedure TP on the constrained data items CDI1, …, CDIn. One problem is how to handle the CDIs that the TP could operate on, but that no user is allowed to perform that TP on those CDIs. One way is to define a pseudo-user called “nobody” and put these CDIs into a tuple with the user as “nobody”. The “allowed” and “certified” relations are fundamentally different. ER1 defines what (type of) entities the transaction procedure can operate on, and ER2 defines who can apply the transaction procedure to specific constrained data items. If they were collapsed into one, two different mechanism would be needed to enforce the rule. Hence separating them keeps the model simple and clean.
ER1: The system must maintain the association relationship to ensure that the verified TP operates the corresponding CDI, that is, there is a one-to-one association relationship between TP and CDI. ER2: When TP operates CDI, it is guaranteed that the operating user has the right to operate the corresponding CDI. The user represented by TP is the real user of CDI , and there is a one-to-one correspondence between the triples { user, TP, {CDI set} }. The two cannot be combined because it is a two-step relationship, that is, TP operates CDI, and users use TP to operate their own CDI. If combined, it means a one-step operation, and some connotations are not clearly expressed.
参考:http://wwwusers.di.uniroma1.it/~parisi/Risorse/Integrityx2.pdf
Computer System Security 2018【5】Chapter 9: Integrity - Katastros





















 1023
1023


 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?







