#include <iostream>
#include<Windows.h>
char* p;
int i;
void JmpTarget();
void __declspec(naked) IdtEntry() {
p = (char*)0x8003f120;
for (int i = 0; i < 64; i++) {
*p = ((char*)JmpTarget)[i];
p++;
}
__asm {
iretd
}
}
void __declspec(naked) JmpTarget() {
__asm {
push eax
mov eax,ss:[esp+4]
mov ds:[0x8003f3f0],eax
pop eax
push 0
mov word ptr [esp+2],0
push 0x8053F31D
ret
}
}
void go() {
__asm {
mov eax, 1
int 0x20
}
}
int main()
{
if ((DWORD)IdtEntry != 0x401040) {
printf("wrong addr:%p", IdtEntry);
exit(-1);
}
go();
system("pause");
}
开始Hook
#include <iostream>
#include<Windows.h>
DWORD g_num;
void __declspec(naked) IdtEntry() {
__asm {
mov eax, cr0
and eax, not 10000h
mov cr0, eax
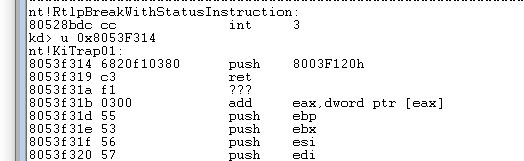
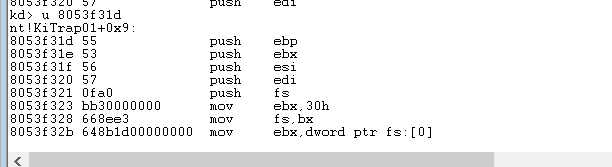
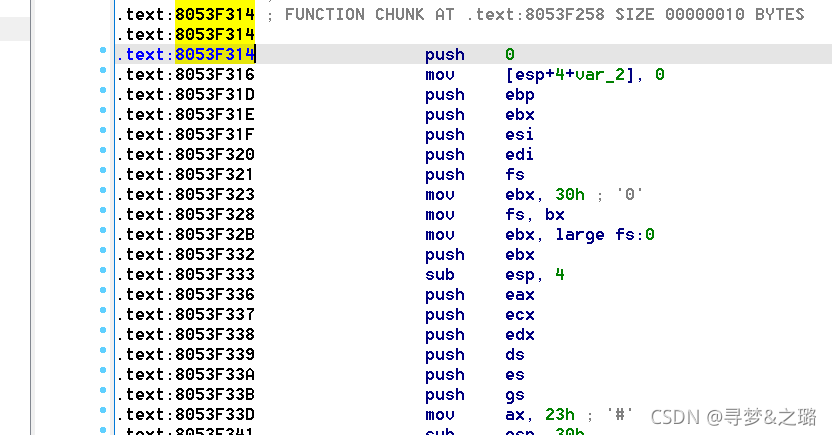
mov eax, 0x03f12068
mov ds:[0x8053F314] , eax
mov ax,0xc380
mov ds : [0x8053F318] , eax
//8053F314
mov eax, cr0
or eax, 10000h
mov cr0, eax
iretd
}
}
void go() {
__asm {
mov eax, 1
int 0x20
}
}
int main()
{
if ((DWORD)IdtEntry != 0x401040) {
printf("wrong addr:%p", IdtEntry);
exit(-1);
}
go();
system("pause");
}
#include <iostream>
#include<Windows.h>
DWORD g_num;
void __declspec(naked) IdtEntry() {
__asm {
mov eax, cr0
and eax, not 10000h
mov cr0, eax
mov eax, 0x03f12068
mov ds:[0x8053F314] , eax
mov ax,0xc380
mov ds : [0x8053F318] , eax
//8053F314
mov eax, cr0
or eax, 10000h
mov cr0, eax
iretd
}
}
void go() {
__asm {
mov eax, 1
int 0x20
}
}
int main()
{
if ((DWORD)IdtEntry != 0x401040) {
printf("wrong addr:%p", IdtEntry);
exit(-1);
}
go();
system("pause");
}
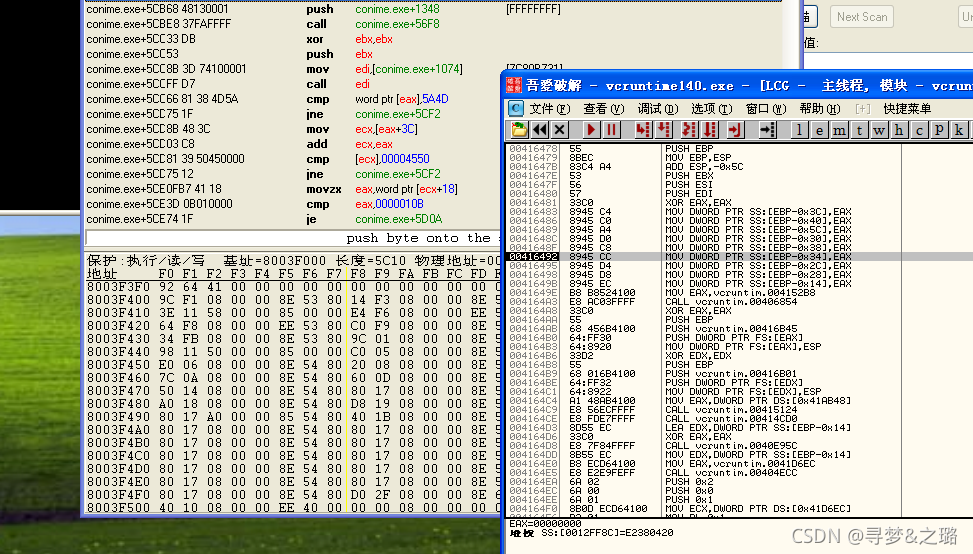
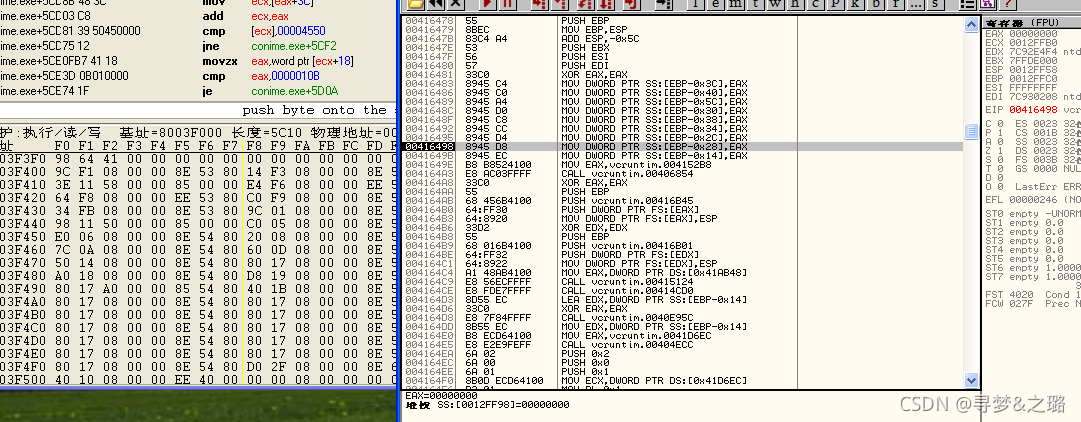
#include <iostream>
#include<Windows.h>
char* p;
int i;
void JmpTarget();
void __declspec(naked) IdtEntry() {
p = (char*)0x8003f120;
for (int i = 0; i < 64; i++) {
*p = ((char*)JmpTarget)[i];
p++;
}
__asm {
iretd
}
}
void __declspec(naked) JmpTarget() {
__asm {
push eax
mov eax, ss: [esp+4]
mov ds : [0x8003f3f0] , eax
mov eax,1
mov ds : [0x8003f3f4] , eax
pop eax
push 0
mov word ptr[esp + 2], 0
push 0x8053F31D
ret
}
}
void go() {
__asm {
mov eax, 1
int 0x20
}
}
int main()
{
if ((DWORD)IdtEntry != 0x401040) {
printf("wrong addr:%p", IdtEntry);
exit(-1);
}
go();
system("pause");
}
#include <iostream>
#include<Windows.h>
DWORD g_num;
DWORD g_enabled;
void __declspec(naked) IdtEntry() {
__asm {
mov eax,ds:[0x8003f3f0]
mov g_num,eax
mov eax, ds : [0x8003f3f4]
mov g_enabled,eax
xor eax,eax
mov ds:[8003f3f4],eax
iretd
}
}
void go() {
__asm {
mov eax, 1
int 0x20
}
}
int main()
{
if ((DWORD)IdtEntry != 0x401040) {
printf("wrong addr:%p", IdtEntry);
exit(-1);
}
while (1) {
go();
Sleep(1000);
if (g_enabled)
printf("%p\n", g_num);
}
system("pause");
}





 本文详细探讨了Windows环境下,通过IDT(Interrupt Descriptor Table)实现的Hook技术,涉及裸函数、中断处理、内存操作和系统调用的修改。作者展示了如何修改中断入口地址并监控特定中断,以及hook后的代码执行流程。
本文详细探讨了Windows环境下,通过IDT(Interrupt Descriptor Table)实现的Hook技术,涉及裸函数、中断处理、内存操作和系统调用的修改。作者展示了如何修改中断入口地址并监控特定中断,以及hook后的代码执行流程。


















 2273
2273

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










