签到
flag{buu_ctf}这是一个不能说的题目
下载文件后发现闪过几张图片
他们分别是:



即如下flag
flag{he11ohongke}二维码
下载图片,扫描发现二维码不存在flag
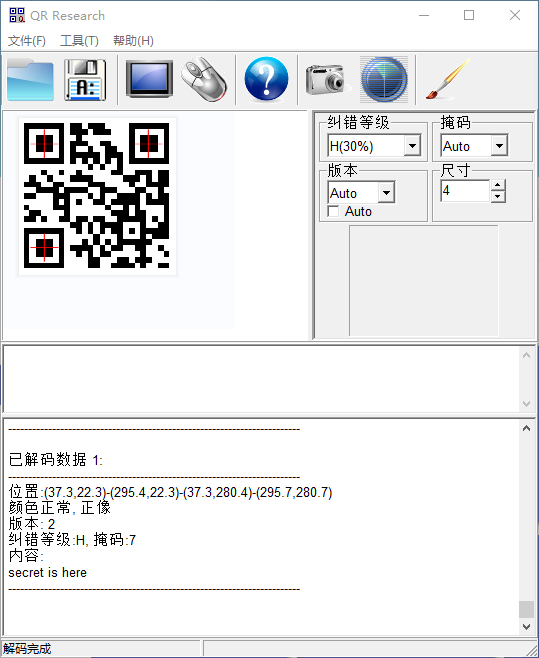
丢进010
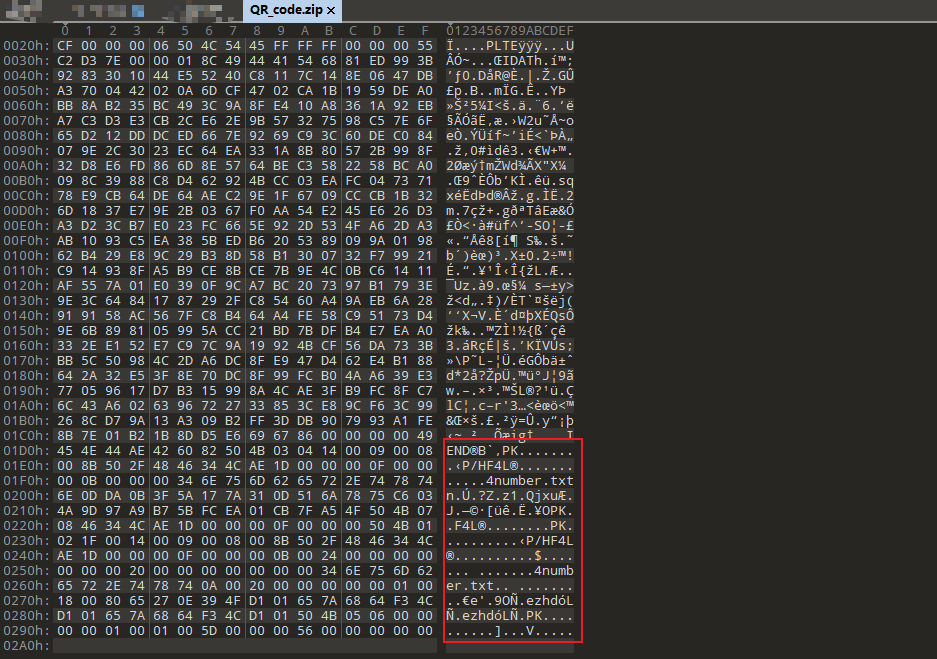
发现如图PK字样,猜测为zip压缩包,将后缀改为压缩包进行识别,发现有密码

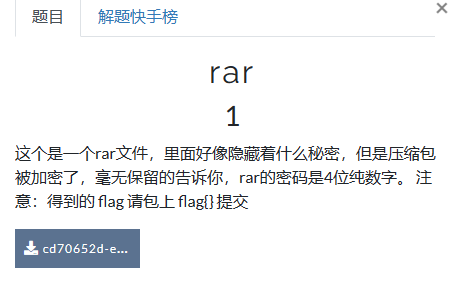
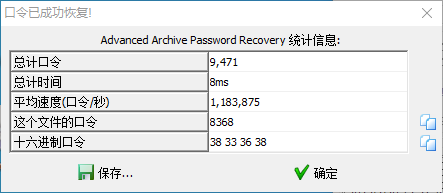
提示为四位数密码 使用ARCHPR查看
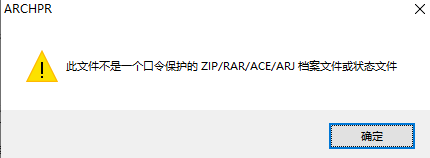
发现这里踩到一个大坑,bandizip可以识别压缩包内容而ARCHPR则必须提取为纯净ZIP才可以爆破
提取后再次爆破
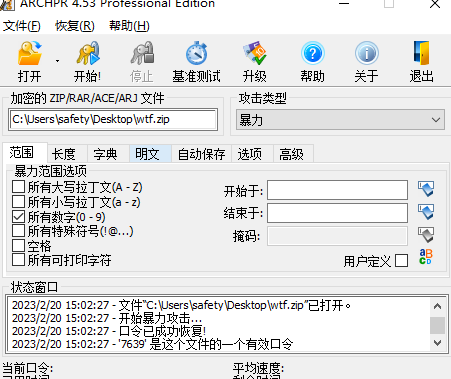
密码为7639 解压后拿到flag
文本内容:
CTF{vjpw_wnoei}
实际Flag应当为
flag{vjpw_wnoei}你竟然赶我走
下图 丢进010 看文件末尾
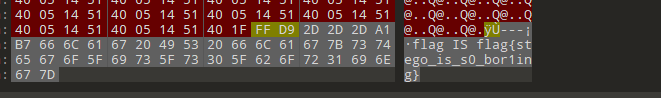
(可以看的出来之里出题人在嘲讽拿LSB扫的笨比)
flag{stego_is_s0_bor1ing}大白
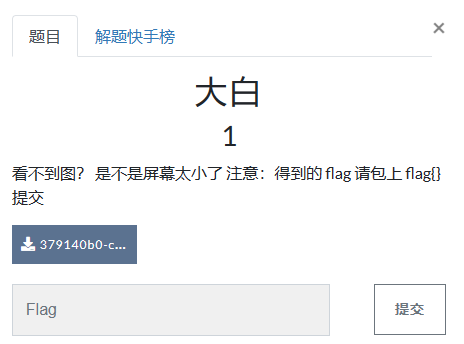
题目提示的很明显了,图片尺寸有问题
直接丢近tweakpng
正确做法应该是拿py脚本修复图片尺寸 这里图方便直接改了

flag{He1l0_d4_ba1}N种方法解决
下了是个exe 没法运行
丢010
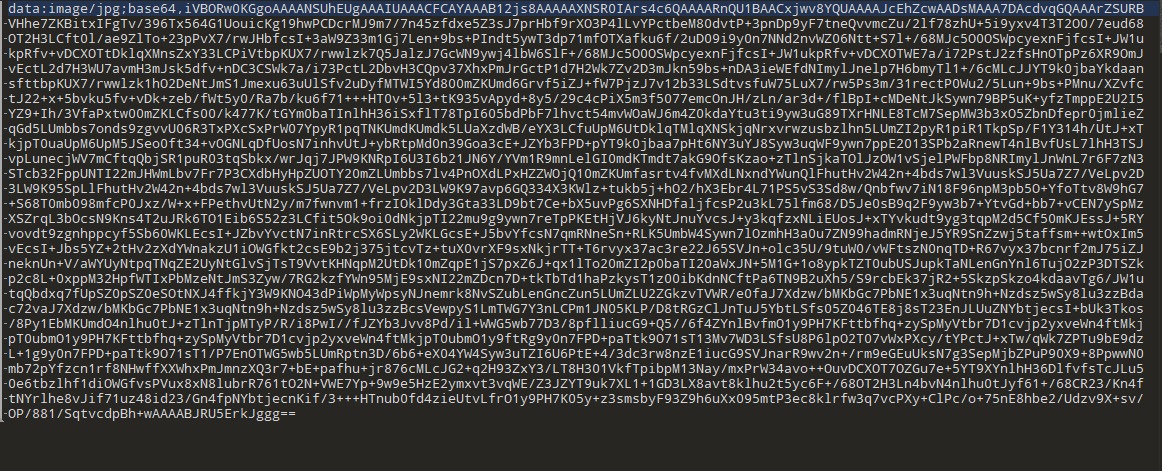
老熟悉了 base64形式图片

二维码 扫
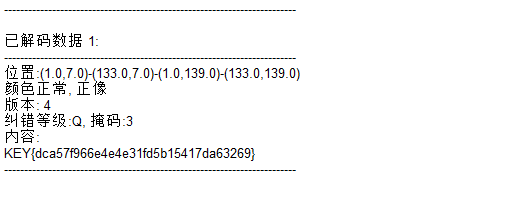
flag{dca57f966e4e4e31fd5b15417da63269}乌镇峰会种图
同”你竟然赶我走“
flag{97314e7864a8f62627b26f3f998c37f1}基础破解

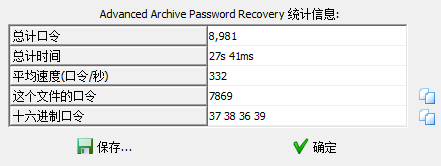
四位密码 嗯扫就完了
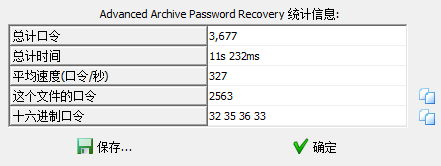
密码为"2563"
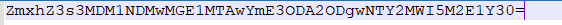
内容一眼base64
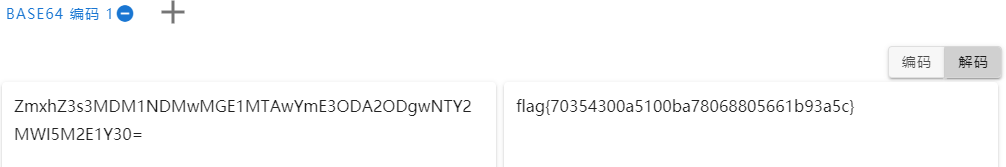
flag{70354300a5100ba78068805661b93a5c}wireshark
不会流量取证 下一个
文件中的秘密
方法与“你竟然赶我走”类似,翻两下就看到了
flag{870c5a72806115cb5439345d8b014396}LSB
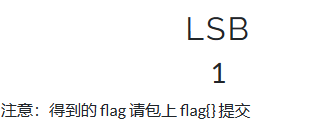
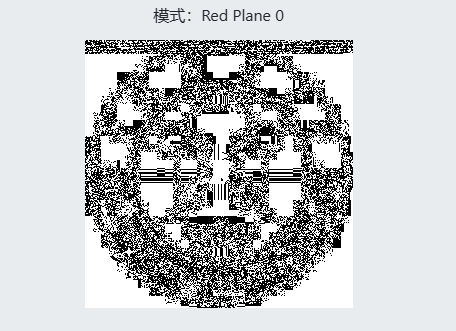
可以看到这个频道上藏了一条奇怪的东西
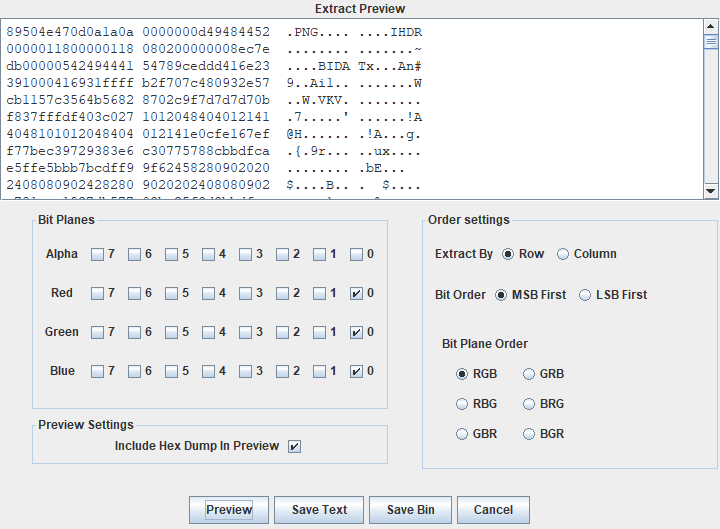
这样子dump就会得到一个二维码
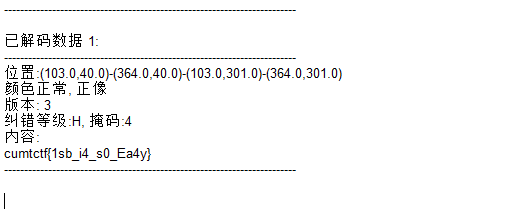
flag{1sb_i4_s0_Ea4y}zip伪加密
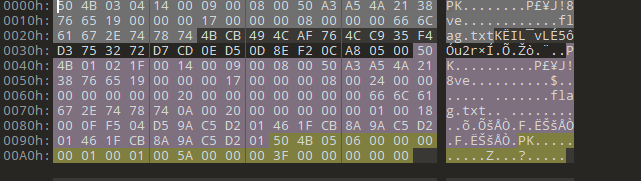
010发现头尾都真有加密
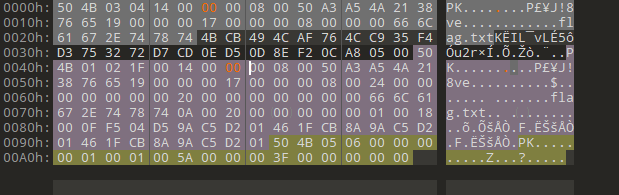
头尾都去掉就好了
flag{Adm1N-B2G-kU-SZIP}rar
扫就做完了
flag{1773c5da790bd3caff38e3decd180eb7}被嗅探的流量
同wireshark不会做
qr
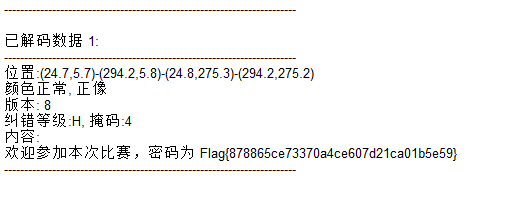
flag{878865ce73370a4ce607d21ca01b5e59}镜子里面的世界
LSB一圈啥也没有
丢zsteg看看
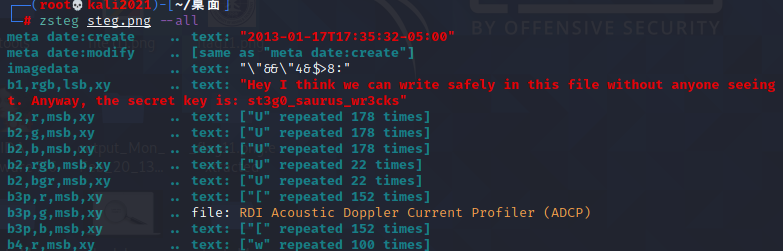
flag{st3g0_saurus_wr3cks}ningen

依然是就差把答案糊脸上的题
010末端有个压缩包数据直接提取
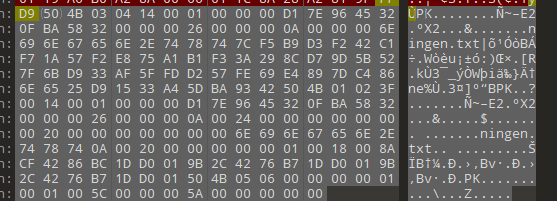
flag{b025fc9ca797a67d2103bfbc407a6d5f}小明的保险箱
同上
flag{75a3d68bf071ee188c418ea6cf0bb043}爱因斯坦
同上但是密码藏图exif里
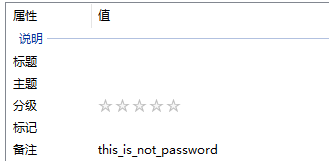
flag{dd22a92bf2cceb6c0cd0d6b83ff51606}easycap
同wireshark不会
隐藏的钥匙
丢010翻出这么个东西
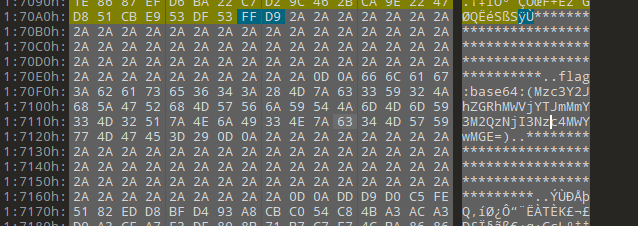
flag:base64:(Mzc3Y2JhZGRhMWVjYTJmMmY3M2QzNjI3Nzc4MWYwMGE=)
也就是说这是base64格式的密钥
flag{377cbadda1eca2f2f73d36277781f00a}monster
还是丢010翻出个
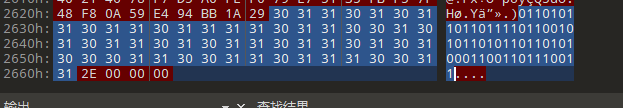
01101011011011110110010101101011011010100011001101110011
第一印象是莫斯电码,但是后面觉得不太对,就试着用ascii码了
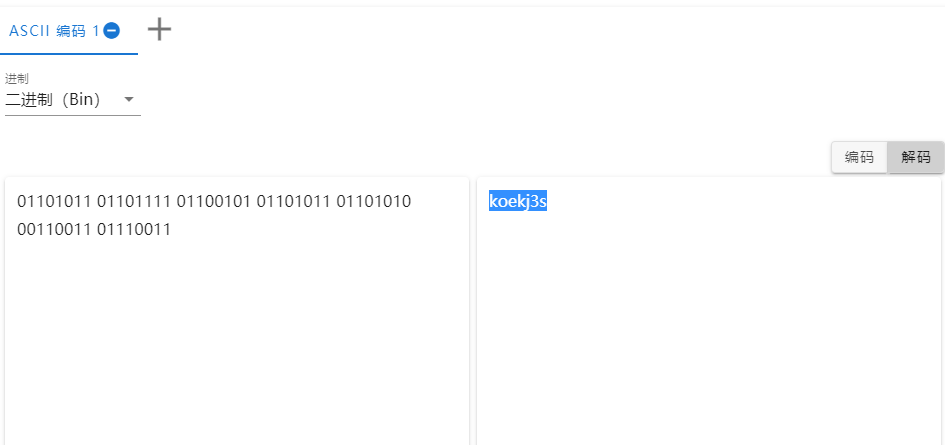
flag{koekj3s}FLAG
没思路就一把梭
看到有个zip
 CTF挑战:解密与隐藏信息
CTF挑战:解密与隐藏信息





 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章

















 1084
1084

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








