公众号:泷羽Sec-尘宇安全
前言
oscp备考,oscp系列——DC-6:wpscan使用密码爆破,wordpress后台管道符拼接命令执行,信息收集+nmap提权
难度简单偏上
- 对于低权限shell获取涉及:wpscan使用密码爆破,wordpress后台管道符拼接命令执行
- 对于提权:信息收集+nmap提权
下载地址:
https://www.vulnhub.com/entry/dc-6,315/
有一个注意事项
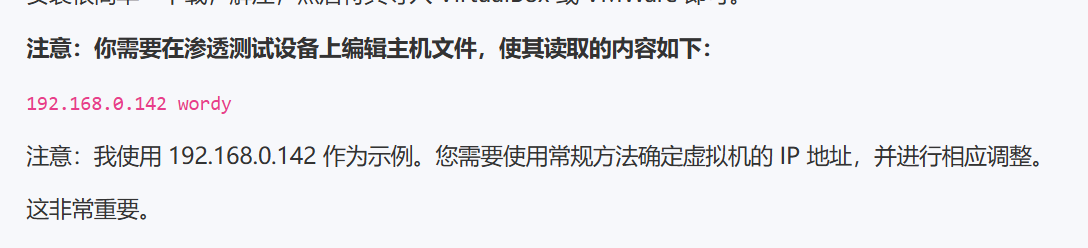
需要我们将靶机ip绑定到wordy域名上面
有一个提示
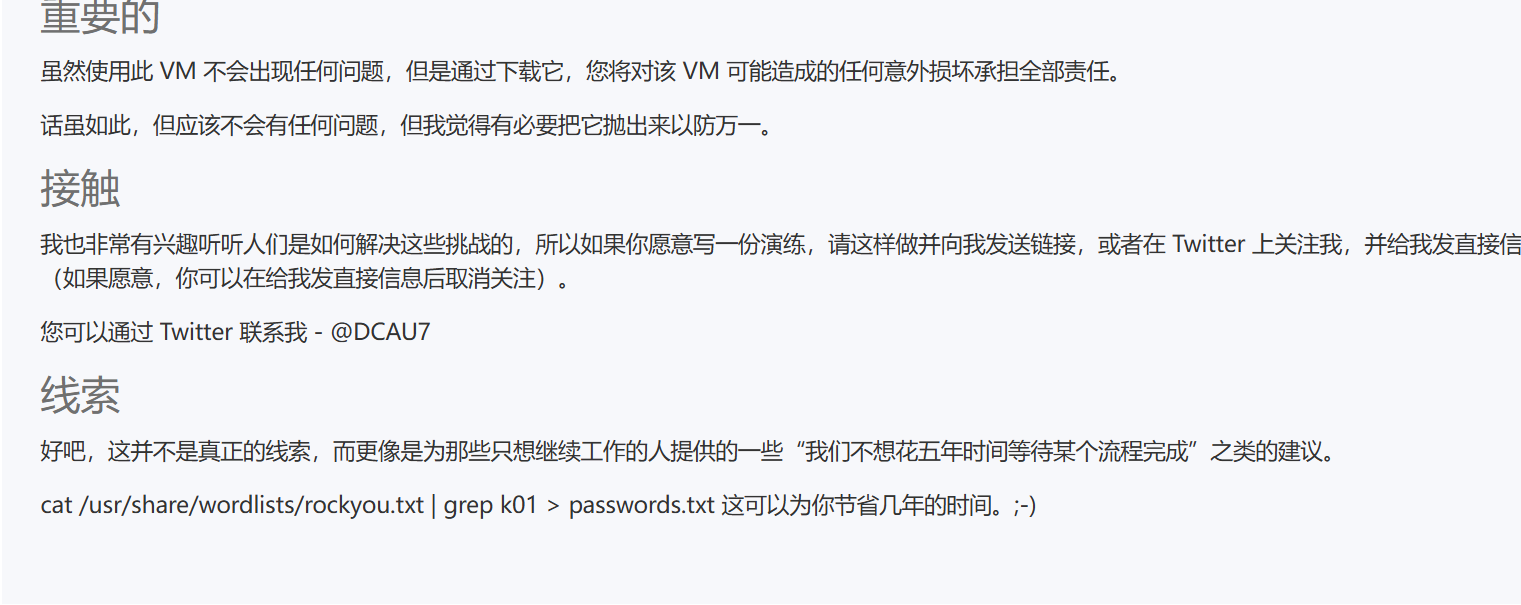
可以帮助我们节约时间,应该需要爆破密码
cat /usr/share/wordlists/rockyou.txt | grep k01 > passwords.txt
nmap
主机发现
发现靶机IP10.10.10.145
└─# nmap -sn 10.10.10.0/24
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-13 23:01 CST
Nmap scan report for 10.10.10.1
Host is up (0.0017s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 10.10.10.2
Host is up (0.00019s latency).
MAC Address: 00:50:56:F2:C6:98 (VMware)
Nmap scan report for 10.10.10.145
Host is up (0.00040s latency).
MAC Address: 00:0C:29:39:FC:04 (VMware)
Nmap scan report for 10.10.10.254
Host is up (0.00013s latency).
MAC Address: 00:50:56:EC:1C:32 (VMware)
Nmap scan report for 10.10.10.128
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 2.02 seconds
将C:\Windows\System32\drivers\etc\hosts进行修改,添加
10.10.10.145 wordy
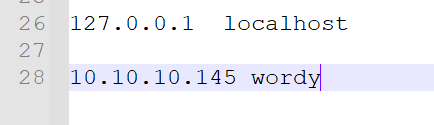
对于kali,也是直接添加到末尾即可
vim /etc/hosts
端口扫描
└─# nmap --min-rate 10000 -p- 10.10.10.145
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-13 23:02 CST
Nmap scan rep




 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章

















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








